当前位置:网站首页>Fedora 36 dnf 安装ModSecurity和 OWASP 核心规则集
Fedora 36 dnf 安装ModSecurity和 OWASP 核心规则集
2022-08-09 23:58:00 【allway2】
dnf install httpd
dnf install mod_security
dnf install mod_security_crs
systemctl enable httpd
systemctl start httpd
more /etc/httpd/conf.d/mod_security.conf
测试:
more /var/log/httpd/modsec_audit.log
--64aa8f03-H--
Message: Warning. Pattern match "^[\\d.:]+$" at REQUEST_HEADERS:Host. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf"] [line "735"] [id "920350"] [msg "Host header is a numeric IP address"] [data "192.168.50.131"] [severity "WARNING"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-protocol"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/210/272"] [tag "PCI/6.5.10"]
Message: Warning. Matched phrase "bin/bash" at ARGS:exec. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf"] [line "500"] [id "932160"] [msg "Remote Command Execution: Unix Shell Code Found"] [data "Matched Data: bin/bash found within ARGS:exec: /bin/bash"] [severity "CRITICAL"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-shell"] [tag "platform-unix"] [tag "attack-rce"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/152/248/88"] [tag "PCI/6.5.2"]
Message: Access denied with code 403 (phase 2). Operator GE matched 5 at TX:anomaly_score. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "93"] [id "949110"] [msg "Inbound Anomaly Score Exceeded (Total Score: 8)"] [severity "CRITICAL"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"]
Message: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/etc/httpd/modsecurity.d/activated_rules/RESPONSE-980-CORRELATION.conf"] [line "91"] [id "980130"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 8 - SQLI=0,XSS=0,RFI=0,LFI=0,RCE=5,PHPI=0,HTTP=0,SESS=0): individual paranoia level scores: 8, 0, 0, 0"] [ver "OWASP_CRS/3.3.0"] [tag "event-correlation"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.50.1] ModSecurity: Warning. Pattern match "^[\\\\\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf"] [line "735"] [id "920350"] [msg "Host header is a numeric IP address"] [data "192.168.50.131"] [severity "WARNING"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-protocol"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/210/272"] [tag "PCI/6.5.10"] [hostname "192.168.50.131"] [uri "/index.html"] [unique_id "YvJa-GThw6cKMirYI40waQAAAMQ"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.50.1] ModSecurity: Warning. Matched phrase "bin/bash" at ARGS:exec. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf"] [line "500"] [id "932160"] [msg "Remote Command Execution: Unix Shell Code Found"] [data "Matched Data: bin/bash found within ARGS:exec: /bin/bash"] [severity "CRITICAL"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-shell"] [tag "platform-unix"] [tag "attack-rce"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/152/248/88"] [tag "PCI/6.5.2"] [hostname "192.168.50.131"] [uri "/index.html"] [unique_id "YvJa-GThw6cKMirYI40waQAAAMQ"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.50.1] ModSecurity: Access denied with code 403 (phase 2). Operator GE matched 5 at TX:anomaly_score. [file "/etc/httpd/modsecurity.d/activated_rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "93"] [id "949110"] [msg "Inbound Anomaly Score Exceeded (Total Score: 8)"] [severity "CRITICAL"] [ver "OWASP_CRS/3.3.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"] [hostname "192.168.50.131"] [uri "/index.html"] [unique_id "YvJa-GThw6cKMirYI40waQAAAMQ"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.50.1] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/etc/httpd/modsecurity.d/activated_rules/RESPONSE-980-CORRELATION.conf"] [line "91"] [id "980130"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 8 - SQLI=0,XSS=0,RFI=0,LFI=0,RCE=5,PHPI=0,HTTP=0,SESS=0): individual paranoia level scores: 8, 0, 0, 0"] [ver "OWASP_CRS/3.3.0"] [tag "event-correlation"] [hostname "192.168.50.131"] [uri "/index.html"] [unique_id "YvJa-GThw6cKMirYI40waQAAAMQ"]
Action: Intercepted (phase 2)
Stopwatch: 1660050168524288 8313 (- - -)
Stopwatch2: 1660050168524288 8313; combined=3896, p1=1951, p2=1729, p3=0, p4=0, p5=216, sr=533, sw=0, l=0, gc=0
Response-Body-Transformed: Dechunked
Producer: ModSecurity for Apache/2.9.4 (http://www.modsecurity.org/); OWASP_CRS/3.3.0.
Server: Apache/2.4.54 (Fedora Linux)
Engine-Mode: "ENABLED"
--64aa8f03-Z--dnf install php
cd /var/www/html/
vi index.php
<?php
phpinfo();systemctl restart httpd

边栏推荐
猜你喜欢
最高月薪15K,谁有历经千辛万苦的意志,谁就能收获属于自己的成功~
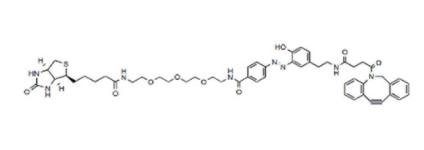
FITC标记生物素(FITC-生物素|CAS:134759-22-1)有哪些知识了?

Biotin-Cy2 Conjugate, Biotin-Cy2 Conjugate_Cy2 Biotin Conjugate
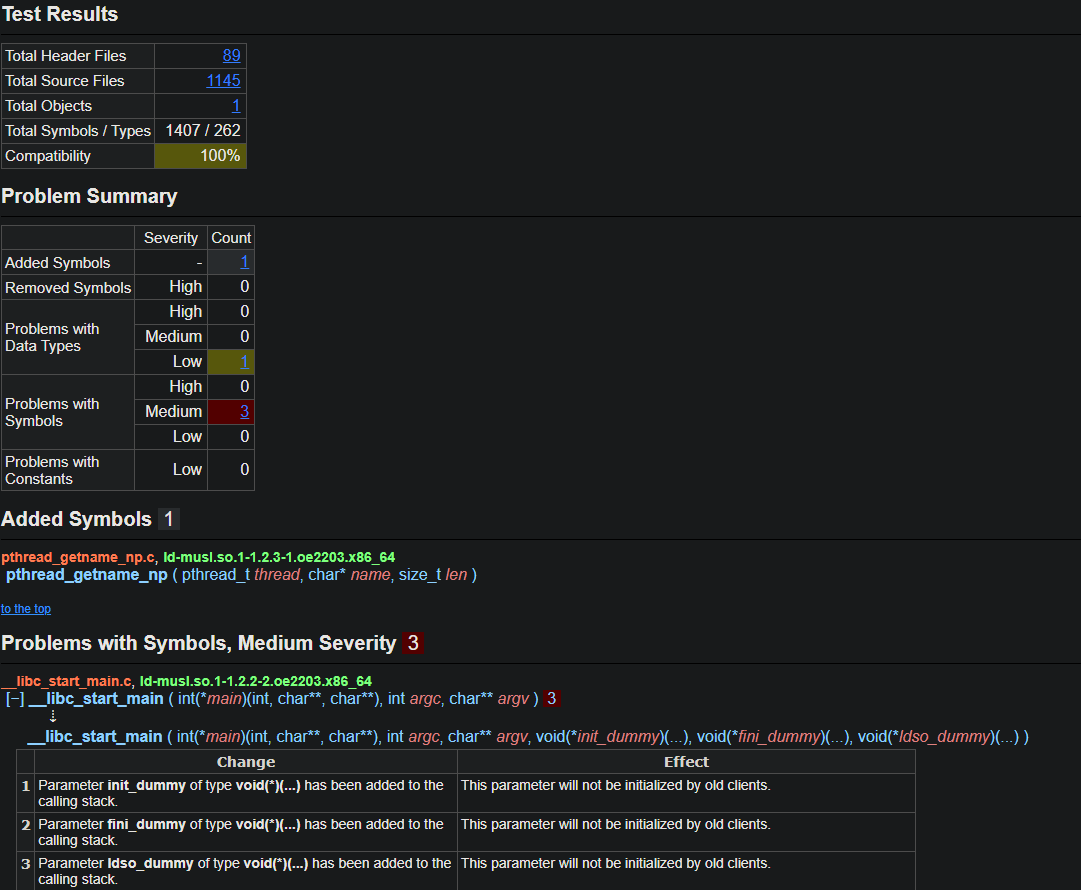
openEuler 知:abi 检测
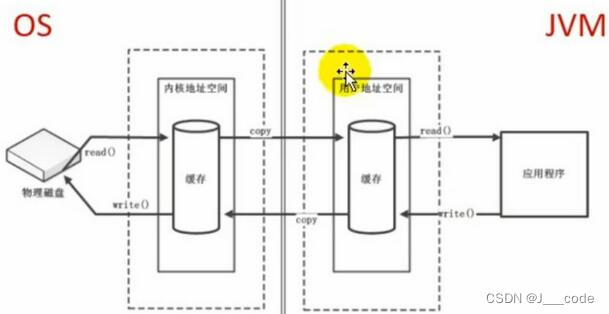
JVM Memory and Garbage Collection - 10. Direct Memory
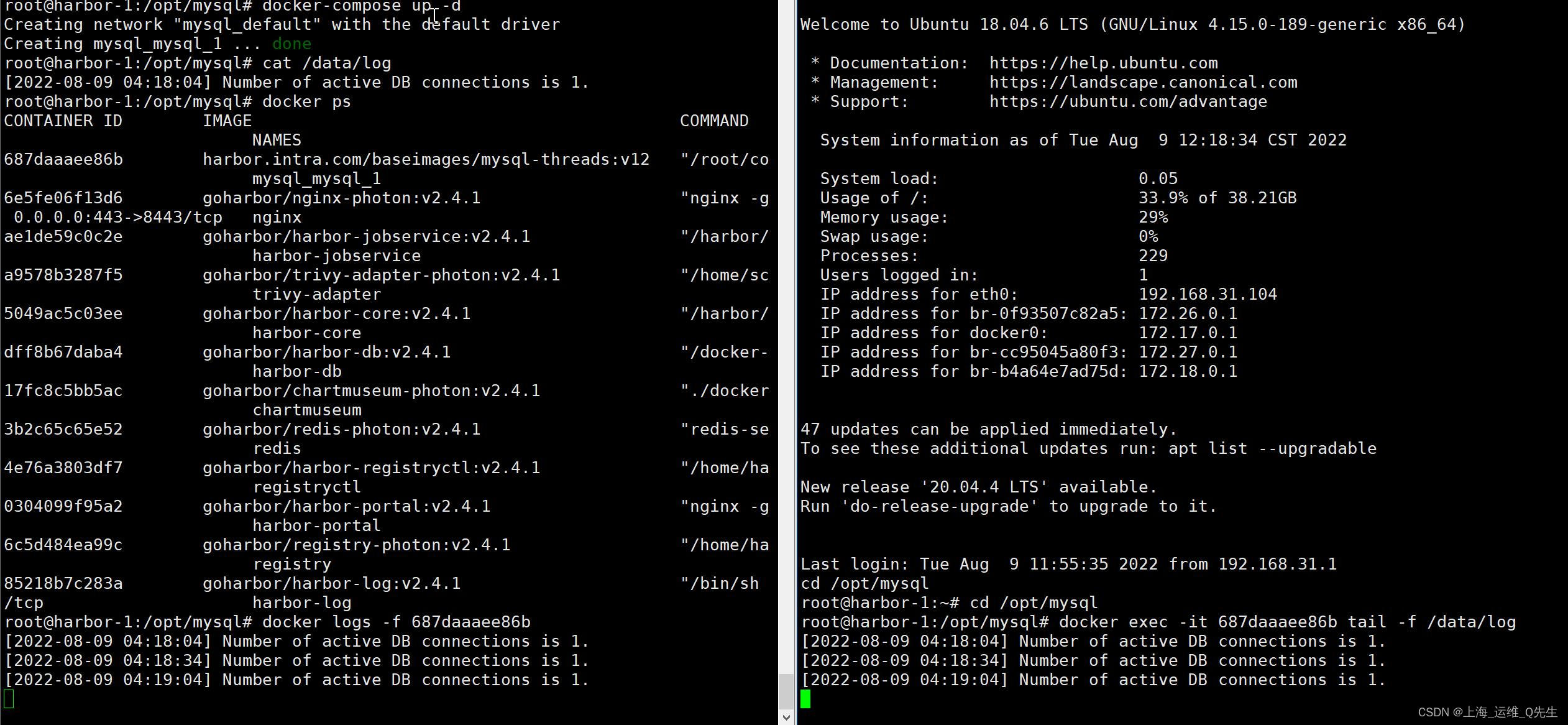
Docker interview question 2--get the number of database connections and docker-compose
【CAS:41994-02-9 |Biotinyl tyramide】生物素基酪氨酰胺价格
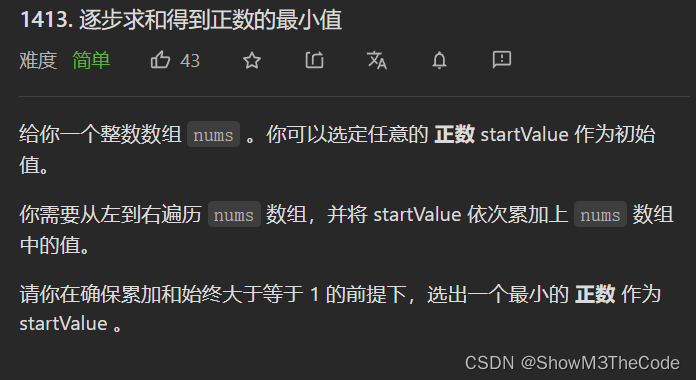
365天挑战LeetCode1000题——Day 052 逐步求和得到正数的最小值 贪心
Xi'an biotin-tetrapolyethylene glycol-amide-4phenol light yellow semi-solid
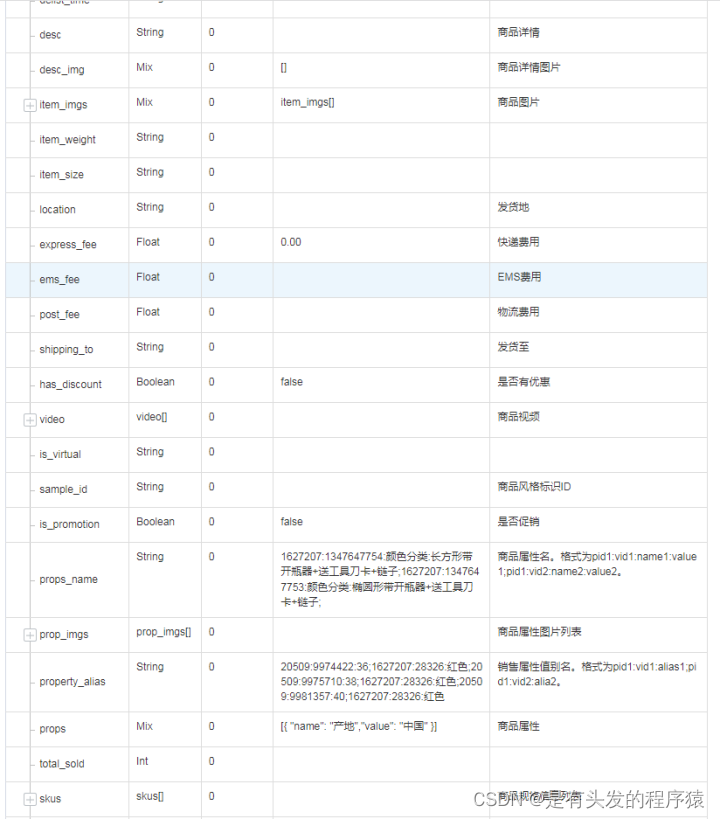
天猫全网商品详情封装接口
随机推荐
聚焦热点 | ISC 2022软件供应链安全治理与运营论坛圆满落幕
Kubernetes 开发环境比对
阿里云混合云管理平台多Region架构
-Vector Dot Product-
-红与黑-
Xi'an biotin-tetrapolyethylene glycol-amide-4phenol light yellow semi-solid
router路由
Next.js获取路由参数及styled-jsx 的使用
Leetcode81. 搜索旋转排序数组 II
-采花生-
手把手教你编写性能测试用例
How to turn off system protection in Win11?How to turn off the system protection restore function?
Solidity 智能合约入门
02|运算符
深入理解Aarch64内存管理
今日睡眠质量记录61分
知行合一的时候
天猫全网商品详情封装接口
Quick responsiveness intelligent/smart responsiveness of polyethylene glycol type nano/reduction response hydrogels research and preparation
线程的同步与互斥
