当前位置:网站首页>[Code Audit] - PHP project class RCE and files include download and delete
[Code Audit] - PHP project class RCE and files include download and delete
2022-08-09 19:32:00 【haoaaao】
[Xiaodi Security] Day52 Code Audit-PHP project RCE and filesIncluding download and delete - BilibiliClick to view the full text> https://www.bilibili.com/read/cv15169189?spm_id_from=333.999.0.0
https://www.bilibili.com/read/cv15169189?spm_id_from=333.999.0.0
0x00 knowledge point
1. Vulnerability keywords
#SQL Injection:
---select insert update mysql_query mysqli etc.
#File upload:
---$_FILES, type="file", upload, move_uploaded_file(), etc.
#XSS Cross-Site:
---print print_r echo sprintf die var_dump var_export etc.
#The file contains:
---include include_once require require_once etc.
#Code execution:
---eval assert preg_replace call_user_func call_user_func_array etc.
#Command execution:
---system exec shell_exec `` passthru pcntl_exec popen proc_open
#Variable override:
---extract() parse_str() importrequestvariables() $$ etc.
#Deserialization:
---serialize() unserialize() __construct __destruct etc.
#Other vulnerabilities:
---unlink() file_get_contents() show_source() file() fopen() etc.
2. General keywords
---$_GET,$_POST,$_REQUEST,$_FILES,$_SERVER etc.
---There may be loopholes in function point or keyword analysis
---Capture the package or search for keywords to find the source of the code and the corresponding file
---Track the filtered or accepted data function, and find the place where this function or code is triggered to trigger the test
http://192.168.0.102:91/?r=../../index.txt%00
http://192.168.0.102:94/admin/save.php?act=delfile
path=/upload/../install/install.lock
0x01 Case Ideas
1, xhcms-frameless-file includes cross-site-search or application-include
Overall ideas
///Analysis of general applications and url addresses may contain xss and security vulnerabilities
Capture the package to find the xss unfiltered code block and the file contains a suffix to bypass the code block
(See the link for the specific analysis process [Xiaodi Security] Day52 code audit - PHP project class RCE and file contains download and delete - Bilibili)
2, earmusic-frameless-file download-search or application function-down, etc.
Overall ideas
---Judging by application analysis or search that there may be file download operations
---Capture and analyze the download address to find the corresponding code block, the file download address is controlled by $file
---$file is known from the database query statement, tracking where such data can be updated or changed
---Try to modify the discovery filter, track the filter mechanism to analyze and bypass, and use the full path address to bypass
Analysis steps:
Enter the shooting range and observe the function
---Here is a possible loophole from the function of the member center:
There is a file download vulnerability in music download;
There is a file upload vulnerability in avatar and music upload;
Personal information modification may have SQL injection vulnerabilities;
Logs, footers may have XSS vulnerabilities;
There may be some other loopholes in the api to view the call;
View the packet transmission format, etc.
---According to the function of the website, take guesses about possible loopholes: biased towards social networking, injection, XSS more; music download, file download, upload loopholes more;
---Two ideas for file download vulnerability mining here:
(1) Functional test based on file download
(2) Search for related functions and keywords of file download and then capture and analyze the package
(3) Track the filtered or accepted data function, and find the place where this function or code is triggered to trigger the test
3, zzzcms-frameless-file delete RCE-search or apply-unlink,eval
Overall ideas
---File delete search keyword unlink, corresponding to the function del_file, see where this is called
---Background delfile function call, how to punish the delfile function, controlled by parameters, test
---The code executes the search keyword eval, the corresponding configuration template parses the file, and sees where this is called
---It is judged that the template file can be modified in the background, the template file is triggered in the foreground, and the payload is constructed for testing
Analysis steps:
---File deletion is generally used for white box auditing, you can delete the install.lock file
(For specific steps, see the link [Xiaodi Security] Day52 code audit - PHP project class RCE and file contains download and delete - Bilibili)
边栏推荐
猜你喜欢
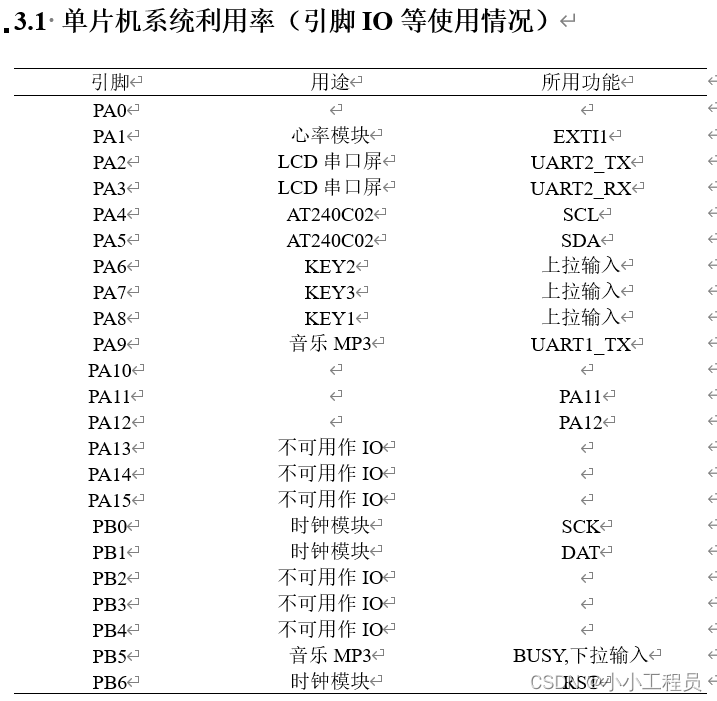
B46 - STM32太阳能充电智能心率监测骑行仪
单片机的优点和单片机开发的流程

快捷键修改typora字体----自制脚本
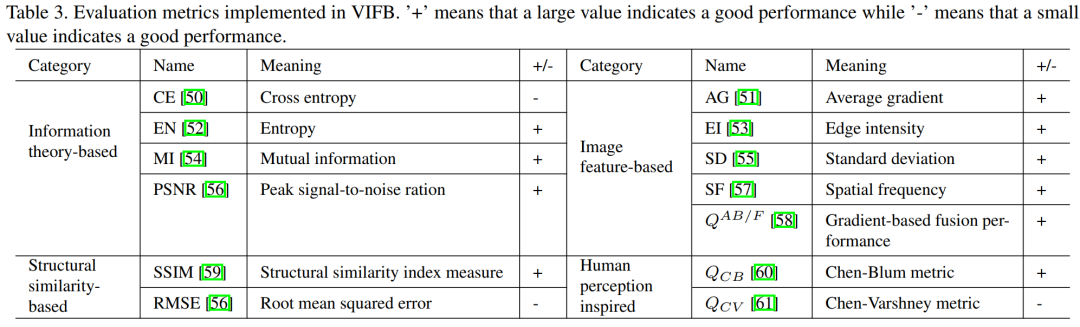
1.1、VIFB: A Visible and Infrared Image Fusion Benchmark(一个可见光与红外图像融合Benchmark)文章阅读

Lagrange插值公式matlab实现

2.1, pay attention to the network based on parallel context scenario text image super-resolution
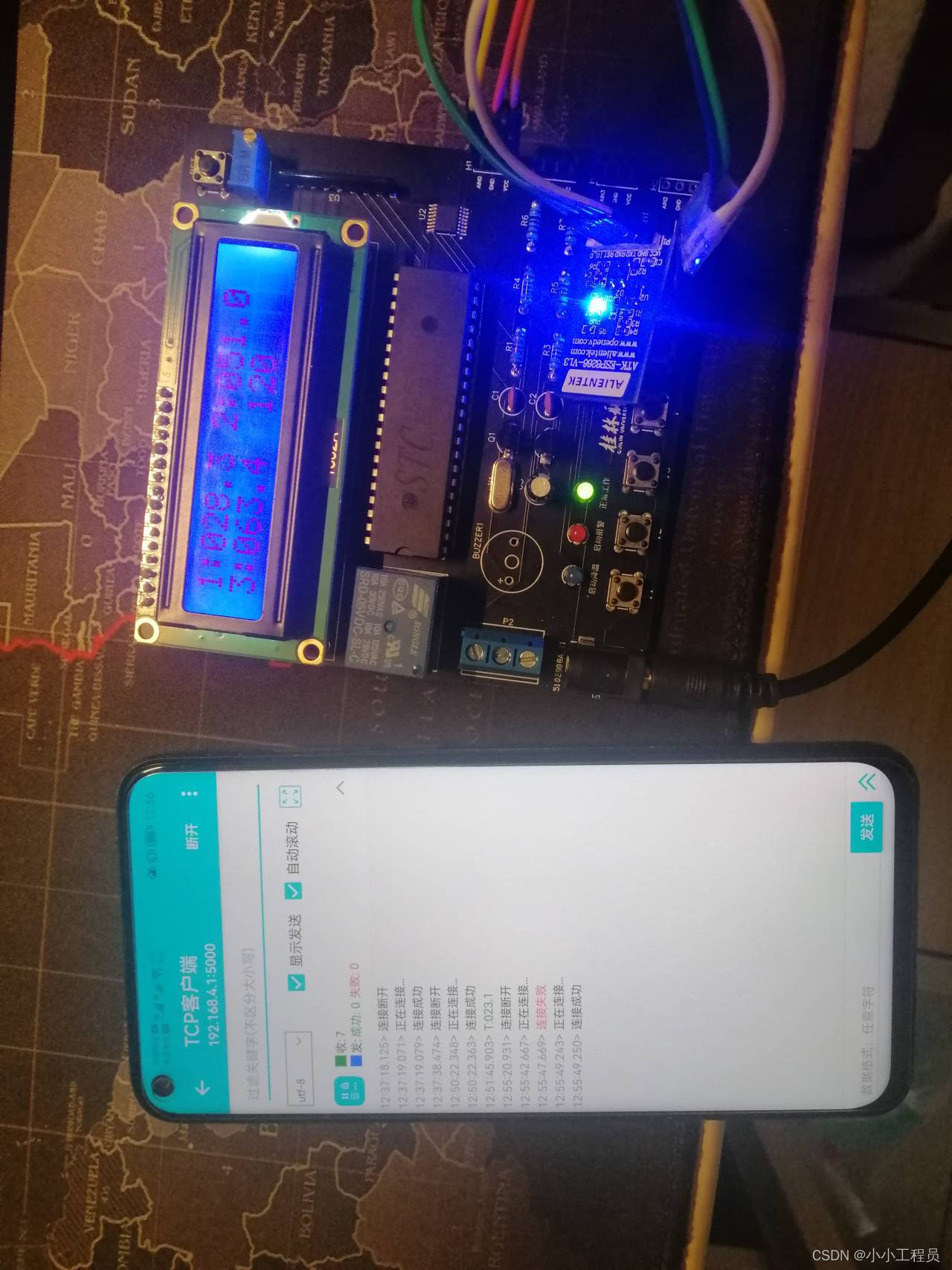
A49 - ESP8266建立AP传输XPT2046AD数据WIFI模块

WPF效果第一百九十四篇之伸缩面板

HR获取入职日期 RP_GET_HIRE_DATE

QT工程编译过程学习
随机推荐
Insert a number and sort "Suggested Favorites"
B44 - 基于stm32蓝牙智能语音识别分类播报垃圾桶
SkiaSharp 之 WPF 自绘 粒子花园(案例版)
Apache Doris 社区 PMC 杨政国:开源项目如何在自身和社区的需求中取得平衡?
SkiaSharp 之 WPF 自绘 投篮小游戏(案例版)
What is hardware integrated development?What are the cores of hardware integrated development?
PADS生成位号图
What is control board custom development?
WPF 实现柱形统计图
crm系统哪家好?好用的crm管理系统推荐
一键生成 API 文档的妙招
关于聊天机器人,跨境电商人必须知道这些…
单片机的优点和单片机开发的流程
Axure实现表格带滚动条
.NET 6 study notes (4) - Solve the Nullable warning in VS2022
The article details of the qiucode.cn website realize the code block can be copied by clicking the button
元宇宙虚拟场景互动获得生活、工作、学习新鲜体验
WPF效果第一百九十四篇之伸缩面板
Jenkins使用pipeline部署服务到远程服务器
【开源教程4】疯壳·开源编队无人机-OPENMV 脚本烧写