当前位置:网站首页>VMware virtual machines export hard disk vmdk files using esxi
VMware virtual machines export hard disk vmdk files using esxi
2022-04-23 11:53:00 【wx5a98a78793203】
1. scene ,esxi The server is down , Back up vmdk file , I want to find a machine to replace , Or move to another esxi machine .( It is suggested to build a shared storage cluster , This situation can be avoided )
2. Create a new virtual machine , The hard disk needs to be as big as or larger than the original machine ,
After adding the original hard disk to the virtual machine .
- Prepare one pe iso file , Give virtual cd Use , Set up a virtual cd The first to start , Boot to PE Environmental Science
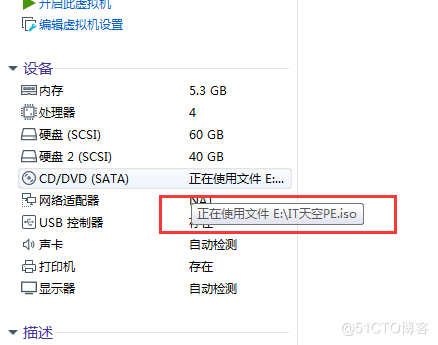
 Pop up and select allow
Pop up and select allow
4. Generally, the old hard disk loaded is unreadable

You need to use the partition tool to migrate the old hard disk data to the new hard disk


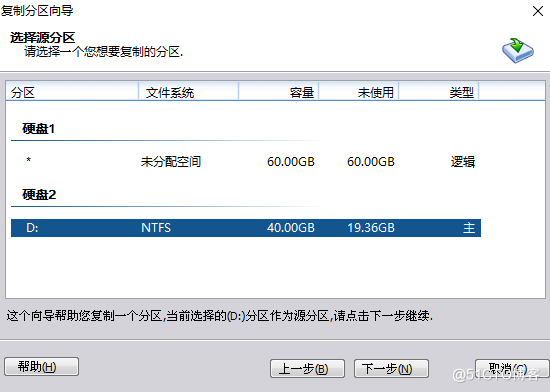
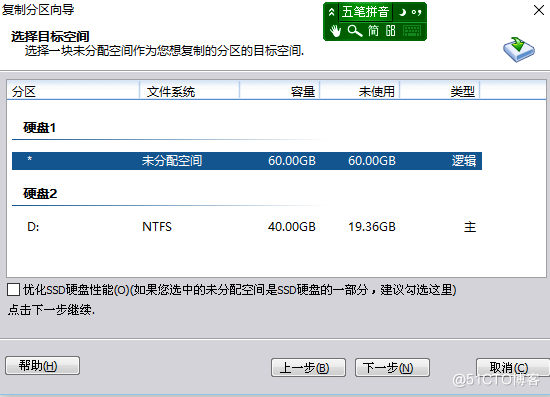


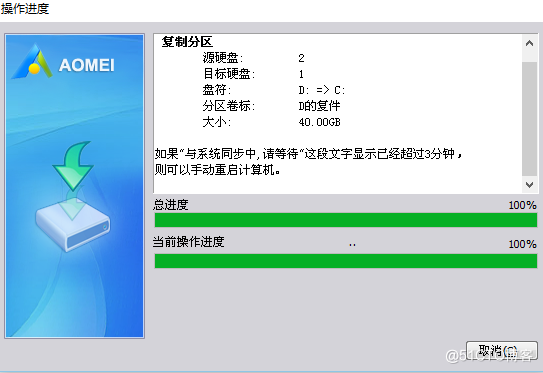
5. After the partition replication is completed , Need to fix the boot


6. After repair, restart the system

7.esxi The principle of migration is the same , load PE stay PE Environment operation repair .
版权声明
本文为[wx5a98a78793203]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231045057012.html
边栏推荐
- 力扣-70.爬楼梯
- How Im expressions work (5.3)
- 少儿编程结构的改变之路
- 欣旺达宣布电池产品涨价 此前获“蔚小理”投资超10亿
- 使用连接组优化连接 (IM 6)
- Maker education for primary and middle school students to learn in happiness
- 数据库如何填充IM表达式(IM 5.4)
- qt5. 8. You want to use SQLite in the 64 bit static library, but the static library has no method to compile the supporting library
- 什么是网关
- Laravel adds custom helper functions
猜你喜欢

Significance of actively participating in middle school robot competition

解决由于找不到amd_ags_x64.dll,无法继续执行代码。重新安装程序可能会解决此问题,地平线(Forza Horizon 5)

解析社交性机器人对基础科学的作用
Share two practical shell scripts

云呐|固定资产盘点中,支持多种盘点方式(资产清查盘点)

Interpreting the art created by robots

解读机器人编程课程的生物认知度

Laravel adds custom helper functions

Use kettle to copy records to and get records from results

Nacos Foundation (9): Nacos configuration management from single architecture to microservices
随机推荐
Relu function of activation function
初探 Lambda Powertools TypeScript
解读机器人编程课程的生物认知度
[web daily practice] eight color puzzle (float)
项目实训-火爆辣椒
获取钉钉考勤机打卡记录
Step function of activation function
ES6 learning notes II
解读机器人创造出来的艺术
RebbitMQ的初步了解
Practical data Lake iceberg lesson 30 MySQL - > iceberg, time zone problems of different clients
零钱兑换II——【LeetCode】
解决由于找不到amd_ags_x64.dll,无法继续执行代码。重新安装程序可能会解决此问题,地平线(Forza Horizon 5)
Maker education for primary and middle school students to learn in happiness
rebbitMQ的简单搭建
《通用数据保护条例》(GDPR)系列解读三:欧洲子公司如何向国内母公司回传数据?
解析社交性机器人对基础科学的作用
User interface and im expression (IM 5.6)
Database design of simple voting system
Laravel admin time range selector daterange default value problem