当前位置:网站首页>Redis deployment of cloud native kubesphere
Redis deployment of cloud native kubesphere
2022-04-23 12:39:00 【Love pocket sky】
1、 Reference use docker Deploy redis Steps for
1.1、 Prepare out of container persistence redis The path to the configuration file
mkdir -p /mydata/redis/conf
1.2、 Get ready redis Profile contents ,vim /mydata/redis/conf/redis.conf
## Configuration example appendonly yes port 6379 bind 0.0.0.01.3、docker start-up redis
docker run -d -p 6379:6379 --restart=always \ -v /mydata/redis/conf/redis.conf:/etc/redis/redis.conf \ -v /mydata/redis-01/data:/data \ --name redis-01 redis:6.2.5 \ redis-server /etc/redis/redis.conf
2、kubesphere Yes redis Deployment Analysis
1、 Deployment Analysis
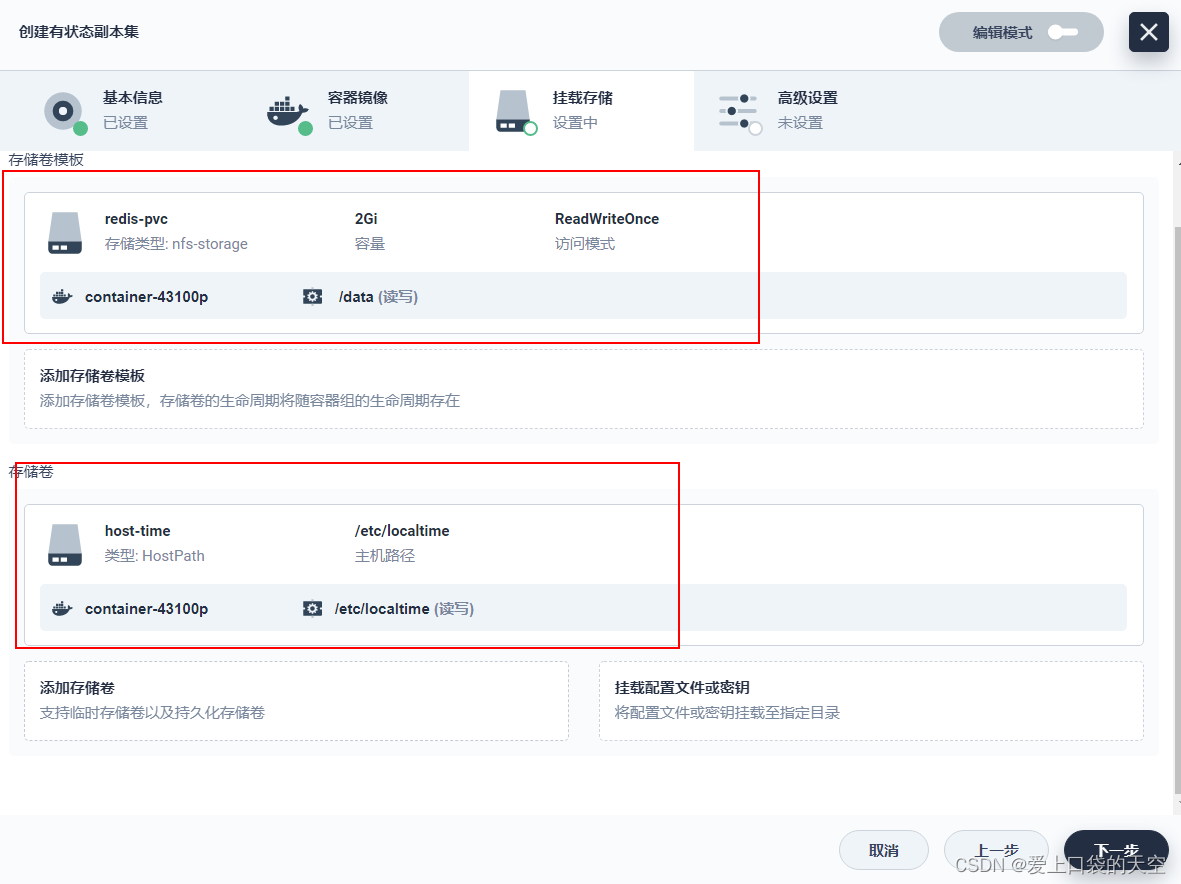
/data: take redis Persistent data files to pvc Resources
/etc/redis: Put... In this directory redis.conf The file is mapped to ConfigMap in
redis-server /etc/redis/redis.conf: Execute... With this command redis Start command
3、 Start deployment ConfigMap To map redis.conf Configuration information
1、 Enter the configuration center -》 To configure
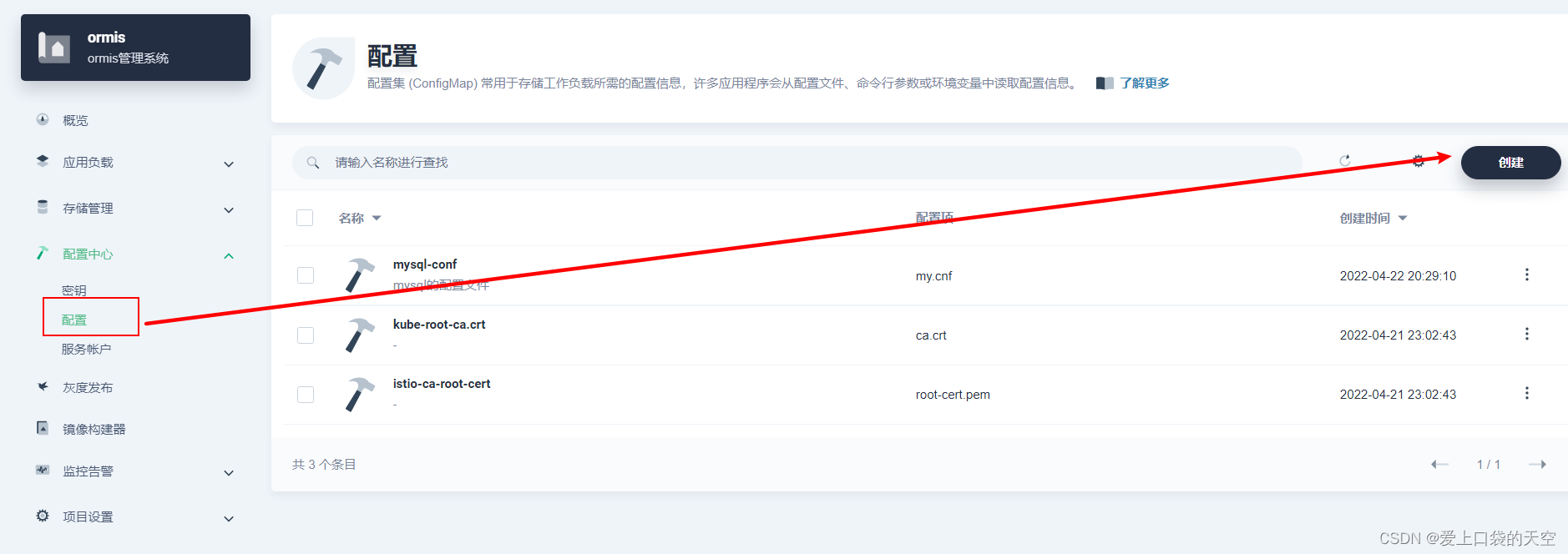
2、 Start creating configuration file
Click Create :
ok, The configuration file is mounted !
4、 Now let's start creating redis Stateful replica set of
1、 Enter the path to create a stateful replica set
2、 Start to create
Click next :
Continue setting down redis Resources for :
Next, configure the startup command :
Click synchronize host time zone :
preservation , And then click next :
Click next :

Here we want to add Volume template , Because we didn't create the storage volume in advance :
Click save :
Next, click mount configuration file :
Click save :
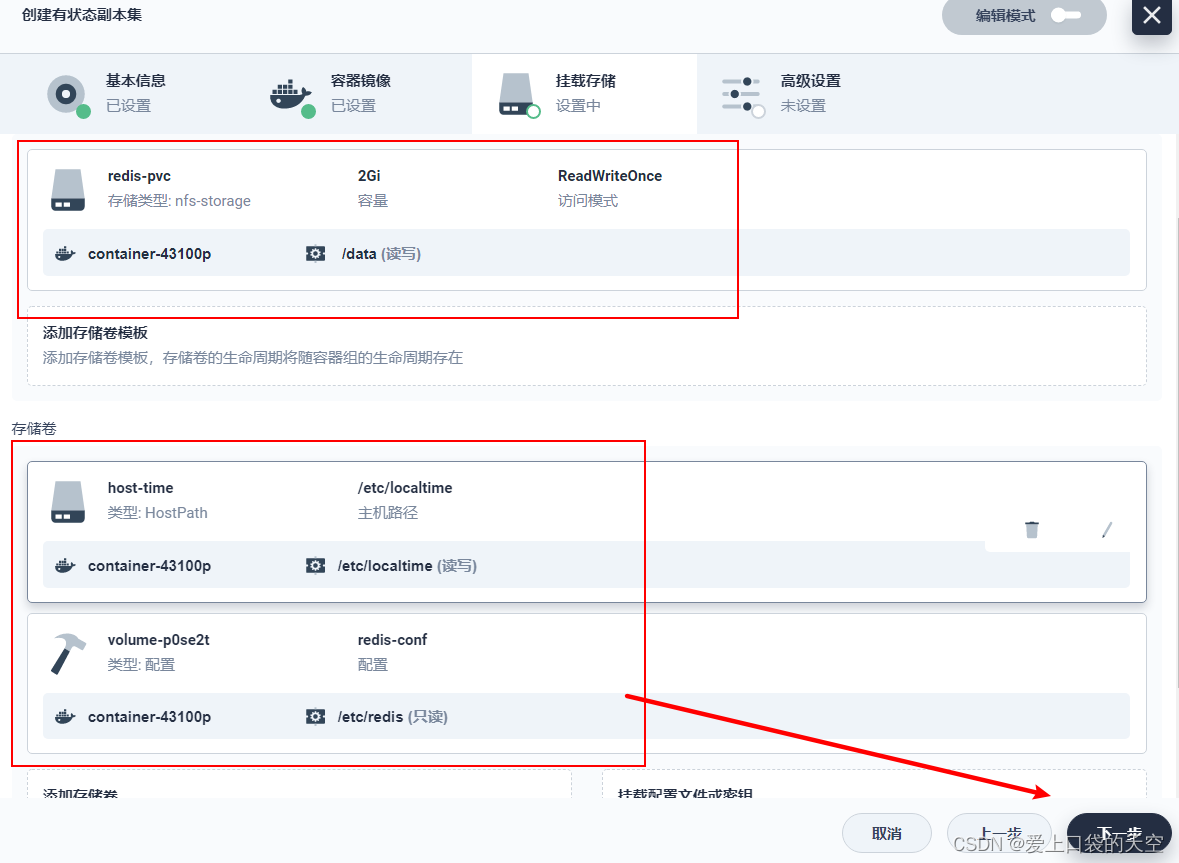
Click Create :
The final result :
5、 visit redis
1、 The default is intranet access
First, let's access and view through the terminal intranet :
2、 You can see that we use the mount volume template ,kubesphere By default, we created pvc
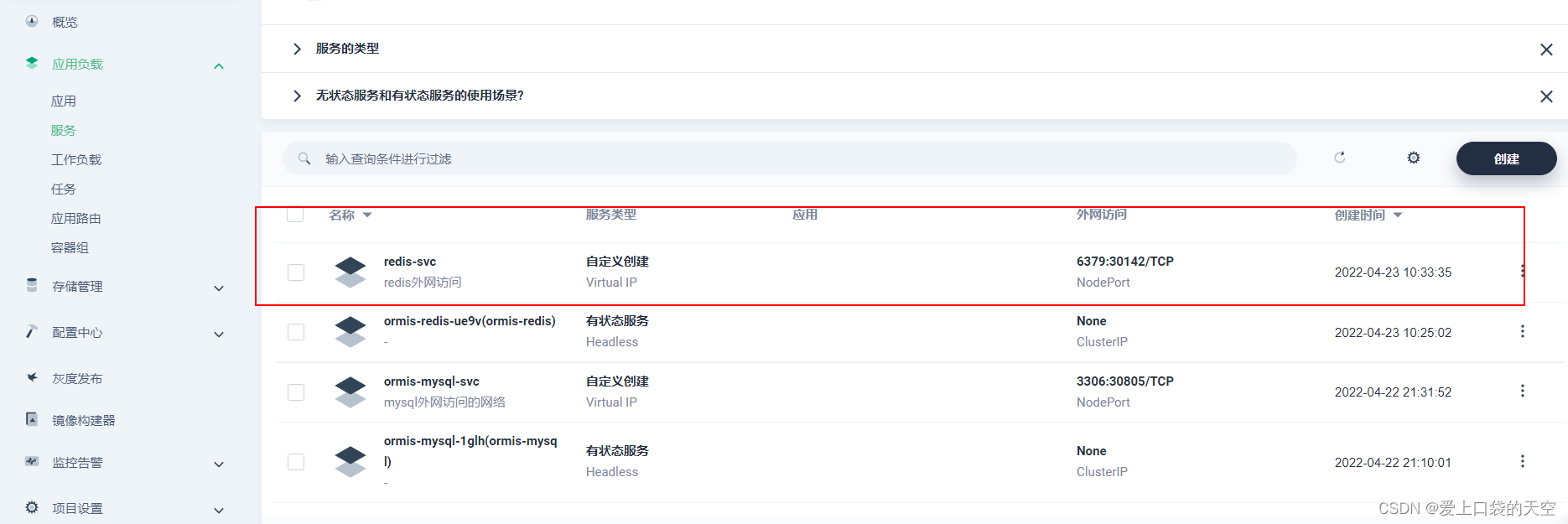
3、 Create out of cluster access

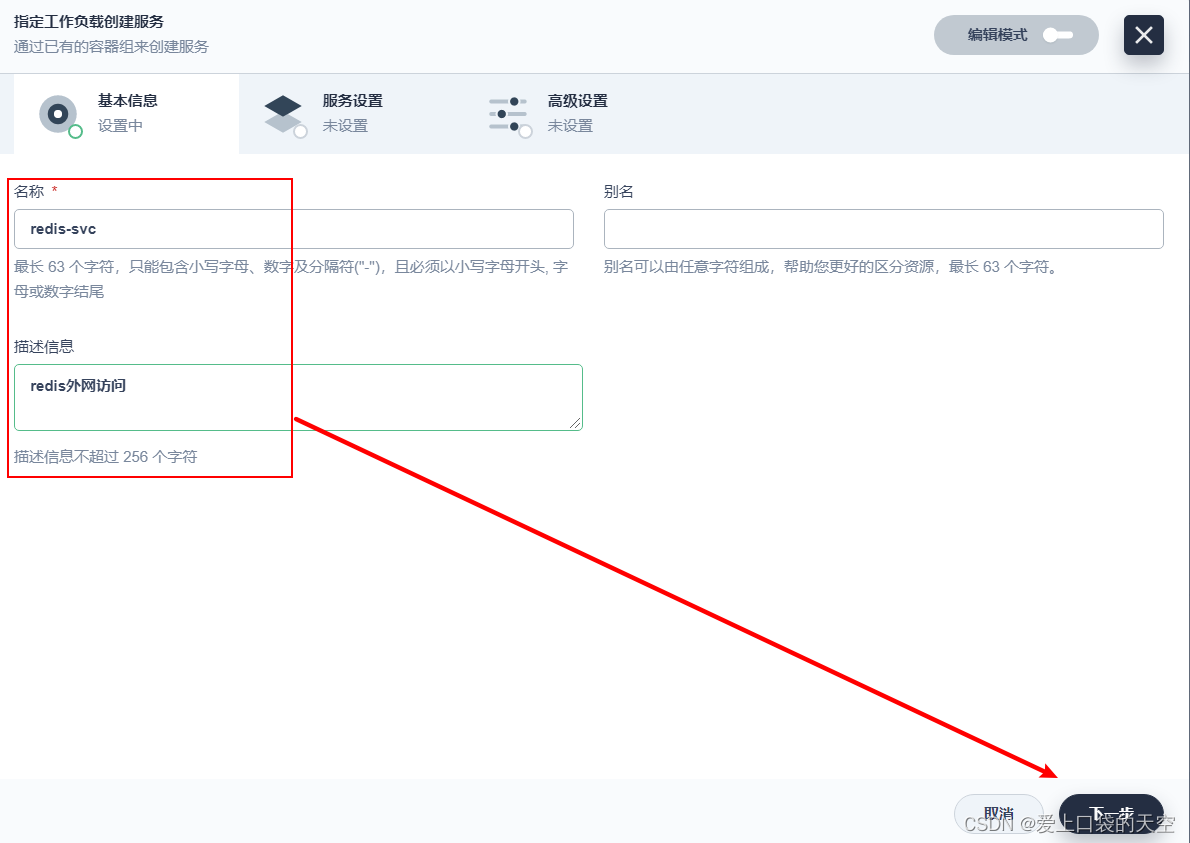

The creation is complete :
Use client access on the Internet redis, You can see that the exposed ports above are 30142:
6、 It can be adjusted dynamically with one key redis replications
For example, we choose 3 individual :

版权声明
本文为[Love pocket sky]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231236522970.html
边栏推荐
- Pagoda panel command line help tutorial (including resetting password)
- 网站首页文件被攻击篡改的形式有哪些
- Outsourcing for five years, abandoned
- Message queuing overview
- 力扣刷题之完全二叉树的节点个数
- What are the forms of attack and tampering on the home page of the website
- STM32 control stepper motor (ULN2003 + 28byj)
- BUUCTF WEB [BJDCTF2020]The mystery of ip
- Labels and paths
- 使用Source Insight查看编辑源代码
猜你喜欢
Pre competition practice of TIANTI competition

Image attribute of input: type attribute of fashion cloud learning -h5

NPDP|产品经理如何做到不会被程序员排斥?

没有空闲服务器?导入 OVF 镜像快速体验 SmartX 超融合社区版

Basic software testing Day2 - Case Execution

力扣刷题之完全二叉树的节点个数

Qt进程间通信

QT one process runs another
Xinwangda announced that the price of battery products had been increased, and the investment of "weixiaoli" exceeded 1 billion

XinChaCha Trust SSL Organization Validated
随机推荐
Qt重绘事件与剪切
万事有你 未来可期 | ONES 2022校园招聘正式开启
uni-app 原生APP-本地打包集成极光推送(JG-JPUSH)详细教程
A graphic designer's fantasy world | ones characters
Zero trust in network information security
Message queuing overview
Source code analysis of synchronousqueue
A graphic designer's fantasy world | ones characters
Analysis of InnoDB execution process in MySQL
Plato farm - a game of farm metauniverse with Plato as the goal
S2-062 remote command execution vulnerability recurrence (cve-2021-31805)
Kubernets Getting started tutoriel
Labels and paths
How much does software testing help reduce program bugs?
QT one process runs another
Worder font page font comparison table
Web17 -- use of El and JSTL
SQLserver怎么插入或更新当天的星期数,bit而不是文本
C set Logo Icon and shortcut icon
电脑系统卡如何解决?