当前位置:网站首页>2022DASCTF Apr X FATE 防疫挑战赛 CRYPTO easy_real
2022DASCTF Apr X FATE 防疫挑战赛 CRYPTO easy_real
2022-04-23 20:21:00 【雨后初霁&】
逆向一道都不会,寄了。只做了密码的签到题
题目描述
import random
import hashlibflag = 'xxxxxxxxxxxxxxxxxxxx'
key = random.randint(1,10)
for i in range(len(flag)):
crypto += chr(ord(flag[i])^key)
m = crypto的ascii十六进制
e = random.randint(1,100)
print(hashlib.md5(e))
p = 64310413306776406422334034047152581900365687374336418863191177338901198608319
q = xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
n = p*q
c = pow(m,e,n)
print(n)
print(c)
#37693cfc748049e45d87b8c7d8b9aacd
#4197356622576696564490569060686240088884187113566430134461945130770906825187894394672841467350797015940721560434743086405821584185286177962353341322088523
#3298176862697175389935722420143867000970906723110625484802850810634814647827572034913391972640399446415991848730984820839735665233943600223288991148186397
从代码中不难看出
#37693cfc748049e45d87b8c7d8b9aacd 对应相应的e的md5值
到相应的网站解密
e=23
其他的分别定义
n=4197356622576696564490569060686240088884187113566430134461945130770906825187894394672841467350797015940721560434743086405821584185286177962353341322088523
c=3298176862697175389935722420143867000970906723110625484802850810634814647827572034913391972640399446415991848730984820839735665233943600223288991148186397
p = 64310413306776406422334034047152581900365687374336418863191177338901198608319根据代码,我们不难看出,这是典型的rsa加密
直接求出明文的数值
from Crypto.Util.number import inverse,long_to_bytes
n=4197356622576696564490569060686240088884187113566430134461945130770906825187894394672841467350797015940721560434743086405821584185286177962353341322088523
c=3298176862697175389935722420143867000970906723110625484802850810634814647827572034913391972640399446415991848730984820839735665233943600223288991148186397
p = 64310413306776406422334034047152581900365687374336418863191177338901198608319
q=n//p
e=23
phi=(q-1)*(p-1)
d=inverse(e,phi)
m = pow(c, d, n)
print(m);
//m=2976168736142380455841784134407431434784057911773423743751382131043957
//m="ndios_;9kgE;WK8e;W?gWn<\;k|nu"我们接着观察
key是一个随机值
但是有范围的
我们直接暴力枚举
import random
import hashlib
import math
from Crypto.Util.number import inverse,long_to_bytes
n=4197356622576696564490569060686240088884187113566430134461945130770906825187894394672841467350797015940721560434743086405821584185286177962353341322088523
c=3298176862697175389935722420143867000970906723110625484802850810634814647827572034913391972640399446415991848730984820839735665233943600223288991148186397
p = 64310413306776406422334034047152581900365687374336418863191177338901198608319
q=n//p
e=23
phi=(q-1)*(p-1)
d=inverse(e,phi)
m = pow(c, d, n)
print(m);
m="ndios_;9kgE;WK8e;W?gWn<\;k|nu"
for key in range(11):
flag=""
for i in range(len(m)):
flag+=chr(ord(m[i])^key)
print(flag)

直接出flag
打了这么多比赛,还是菜。
很多题目赛后根本没复现,真是失败的菜鸡,呜呜呜。
校内可以交流的师傅太少,听说最近联合战队在招新,准备去试试。
版权声明
本文为[雨后初霁&]所创,转载请带上原文链接,感谢
https://blog.csdn.net/a257131460266666/article/details/124368463
边栏推荐
- WordPress插件:WP-China-Yes解决国内访问官网慢的方法
- 使用 WPAD/PAC 和 JScript在win11中进行远程代码执行
- PostgreSQL basic functions
- Click an EL checkbox to select all questions
- 论文写作 19: 会议论文与期刊论文的区别
- . Ren -- the intimate artifact in the field of vertical Recruitment!
- nc基础用法
- Redis installation (centos7 command line installation)
- Mysql database backup scheme
- 【PTA】L1-002 打印沙漏
猜你喜欢
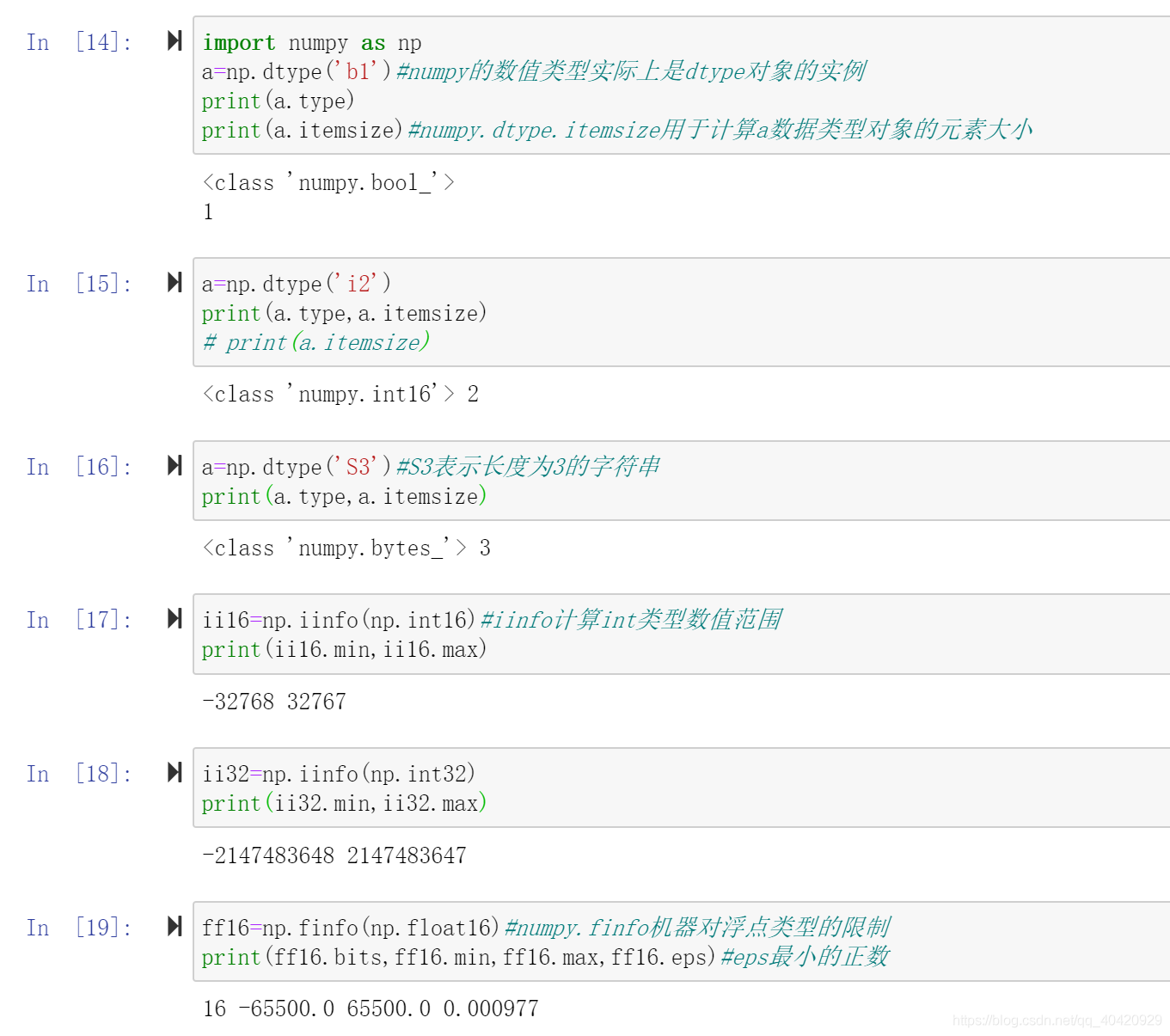
Numpy - creation of data type and array

Building the tide, building the foundation and winning the future -- the successful holding of zdns Partner Conference
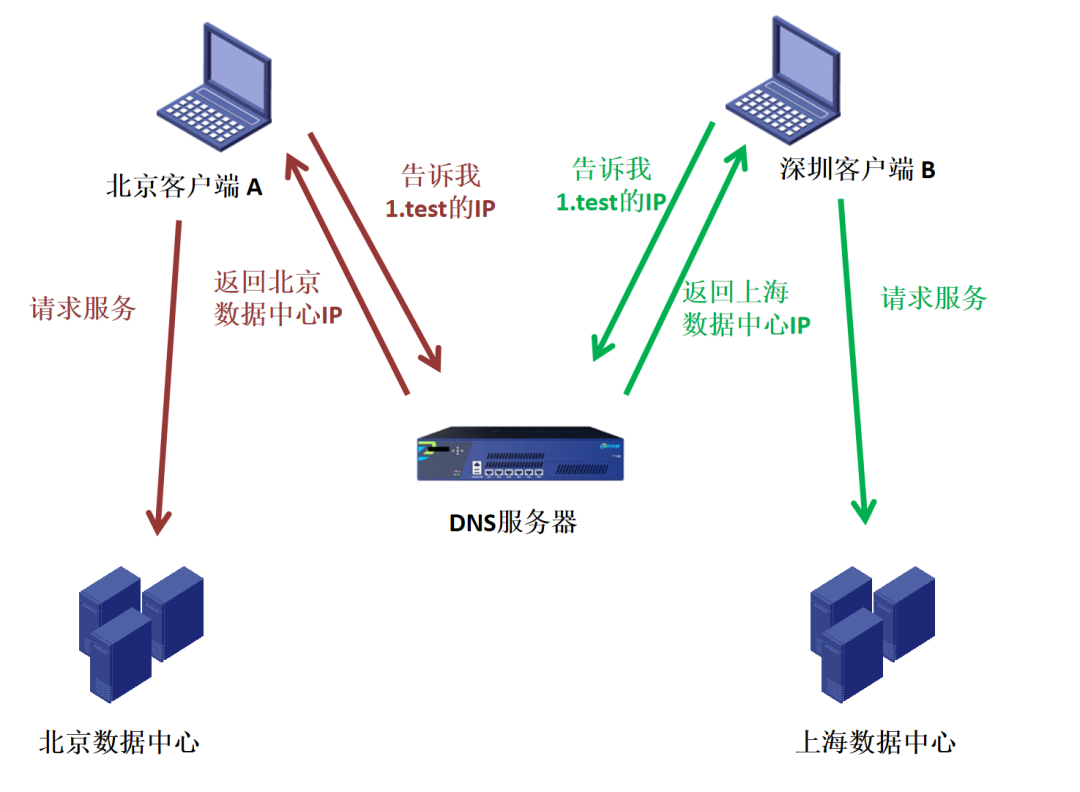
DNS cloud school rising posture! Three advanced uses of authoritative DNS
Identification of bolt points in aerial photography based on perception
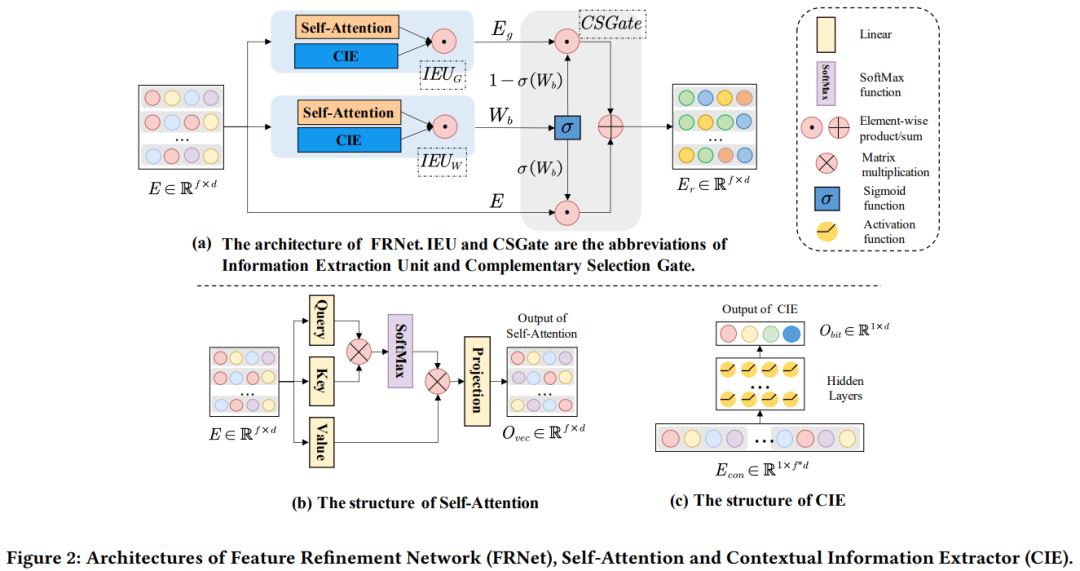
SIGIR'22「微软」CTR估计:利用上下文信息促进特征表征学习
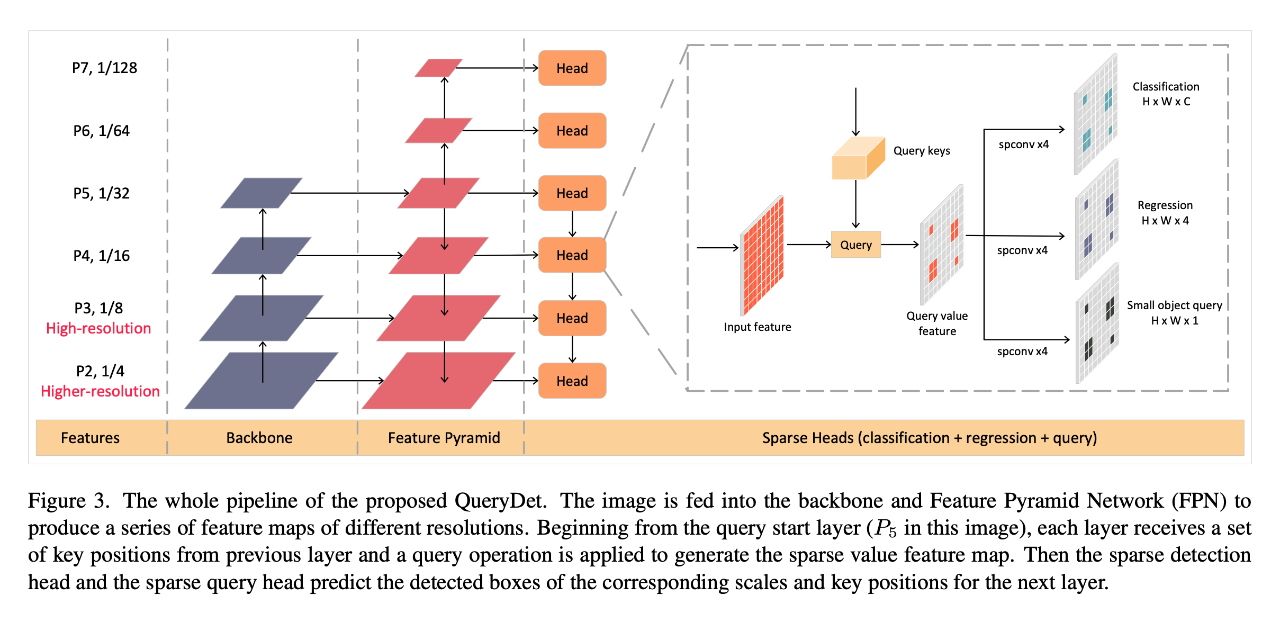
CVPR 2022 | querydet: use cascaded sparse query to accelerate small target detection under high resolution

Openharmony open source developer growth plan, looking for new open source forces that change the world!
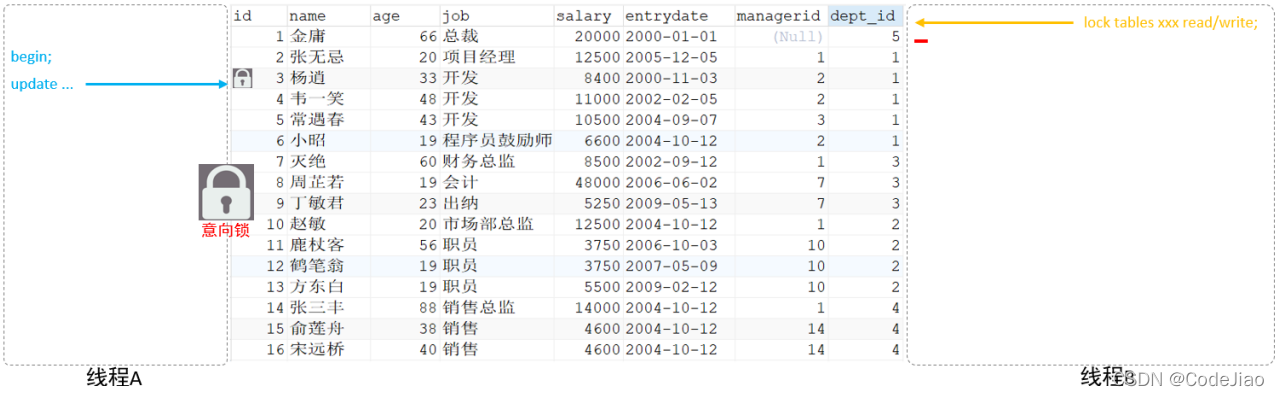
MySQL advanced lock - overview of MySQL locks and classification of MySQL locks: global lock (data backup), table level lock (table shared read lock, table exclusive write lock, metadata lock and inte

. Ren -- the intimate artifact in the field of vertical Recruitment!
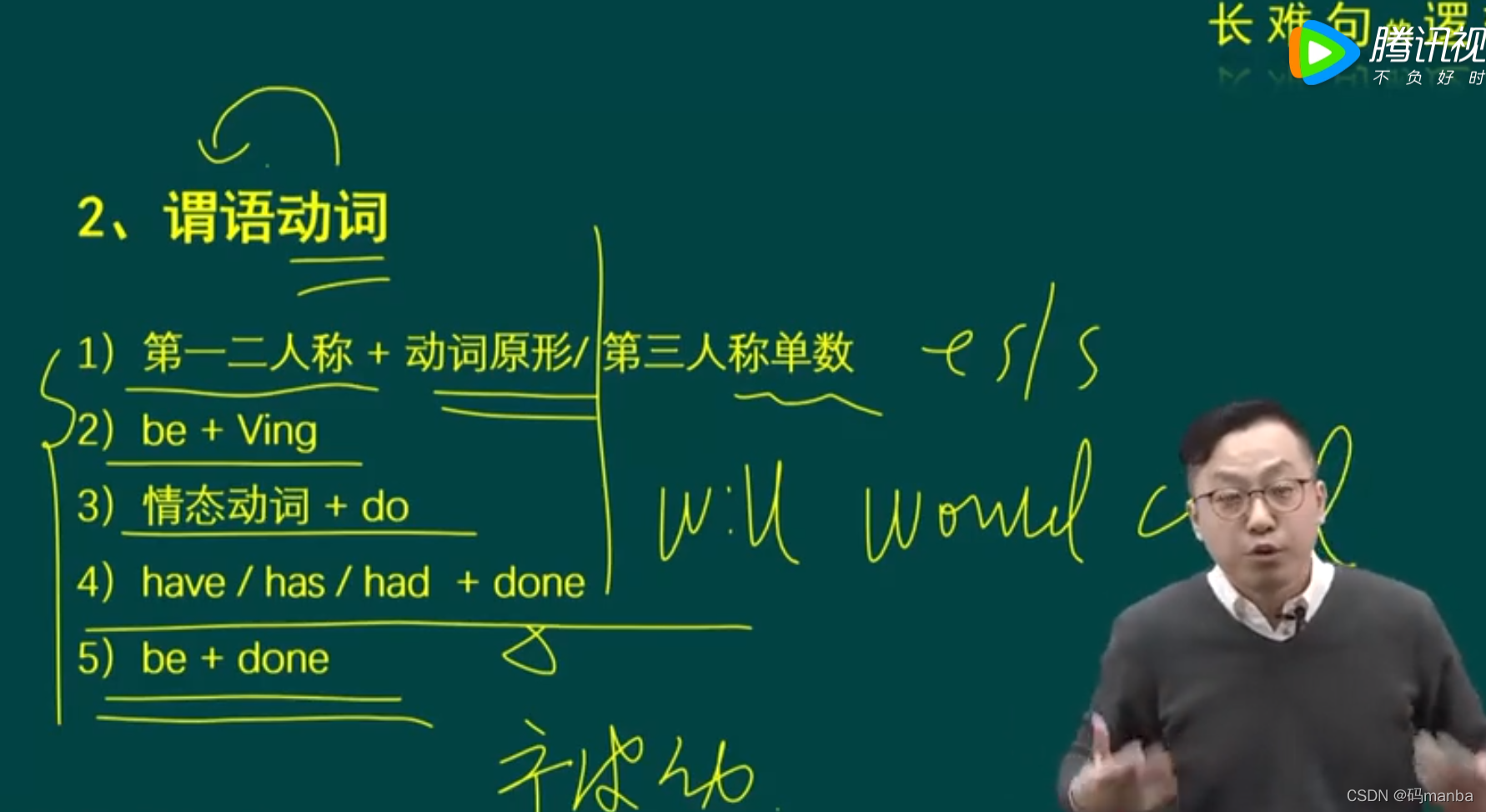
考研英语唐叔的语法课笔记
随机推荐
NC basic usage 4
Historical track data reading of Holux m1200-e Bluetooth GPS track recorder
WordPress plug-in: WP CHINA Yes solution to slow domestic access to the official website
Zdns was invited to attend the annual conference of Tencent cloud basic resources and share the 2020 domain name industry development report
SQL Server connectors by thread pool 𞓜 instructions for dtsqlservertp plug-in
What is the difference between a host and a server?
CVPR 2022 | querydet: use cascaded sparse query to accelerate small target detection under high resolution
NC basic usage 3
PIP installation package reports an error. Could not find a version that satisfies the requirement pymysql (from versions: none)
Handwritten Google's first generation distributed computing framework MapReduce
SQL Server Connectors By Thread Pool | DTSQLServerTP plugin instructions
[graph theory brush question-4] force deduction 778 Swimming in a rising pool
star
redis 分布式锁
Is the wechat CICC wealth high-end zone safe? How to open an account for securities
Sqoop imports data from Mysql to HDFS using lzop compression format and reports NullPointerException
JDBC tool class jdbcfiledateutil uploads files and date format conversion, including the latest, simplest and easiest way to upload single files and multiple files
CVPR 2022 | QueryDet:使用级联稀疏query加速高分辨率下的小目标检测
16MySQL之DCL 中 COMMIT和ROllBACK
Redis distributed lock