当前位置:网站首页>Airtrack cracking wireless network password (Dictionary running method)
Airtrack cracking wireless network password (Dictionary running method)
2022-04-23 02:45:00 【Mechanical bucket running】
This tutorial is an exercise , Do not commit any illegal or criminal acts .
What is? Aircrack-ng
Aircrack-ng It is used to crack Wireless 802.11WEP And WPA-PSK Encryption tools , The tool is in 2005 year 11 Months ago, the name was Aircrack, In its 2.41 It was renamed after the version Aircrack-ng.
Aircrack-ng Two main attack methods are used to wap Crack : One is FMS attack , The way to attack is to discover the WEP The name of the vulnerability researcher (Scott Fluhrer、Itsik Mantin And Adi Shamir) Named ; The other is KoreK attack , Statistics , The attack efficiency of this attack method is much higher than FMS attack . Of course , The latest version integrates more types of attacks . For wireless hackers ,Aircrack-ng It is an indispensable wireless attack tool , It can be said that a large part of wireless attacks rely on it to complete ; For wireless security personnel ,Aircrack-ng It is also a necessary wireless security detection tool , It can help administrators check the vulnerability of wireless network passwords and understand the distribution of wireless network signals , It is very suitable for wireless security audit of enterprises .
◆ Use Aircrack-ng Crack WEP Encrypted wireless network
First of all, let's talk about how to crack WEP Encrypted content , Wireless networks that enable this type of encryption are often listed as one of the most insecure network environments . and Aircrack-ng It is the first choice of powerful weapons to crack such encryption , About use Aircrack-ng Suit cracking WEP The specific steps of encryption are as follows .
step 1: Load wireless network card .
In fact, many newcomers always have some doubts when they start loading network cards , So let's take a closer look at this basic operation . First, check which network cards have been loaded , Enter the command as follows :
Make sure you have inserted it correctly USB perhaps PCMCIA Wireless network card
ifconfig

step 2: Activate the wireless network card to monitor Monitoring mode .
For many little black , We should have used all kinds of sniffing tools to grab data packets such as passwords . that , You know that , The network card used for sniffing must be in monitor Listening mode . The same is true for sniffing wireless networks .
stay Linux Next , We use Aircrack-ng In the suit airmon-ng Tools to implement , The specific command is as follows :
In the picture sudo Yes, it is root Permissions to perform
airmon-ng start wlan0

Input steps 3: Detect wireless networks , Grab wireless packets .
After activating the wireless network card , We can start the wireless packet capture tool , Here we use Aircrack-ng In the suit airmon-ng Tools to implement , The specific command is as follows :
Use ifconfig Check the name of the active network card

But before the official capture , Generally, pre detection is carried out first , To get an overview of the current wireless network , Include AP Of SSID、MAC Address 、 Work channel 、 Wireless client MAC And quantity, etc . Just open one Shell, Enter the specific command as follows :
airodump-ng wlan0mon
Current network conditions

chart 9
Now that we see the target of this test , That's it. SSID be known as TP-LINK Wireless router , Next, enter the following command :
Pay attention to writing in this format
airodump-ng wlan0mon -c 5 --bssid 18:F0:E4:0D:3A:F4 -w file9.cap
# Specify the channel 、AP—MAC 、 Save data package
Parameter interpretation :
–ivs The settings here are filtered by setting , No longer save all wireless data , But just save what can be used to crack IVS The data packet , This can effectively reduce the saved packet size ;
-c Here we set goals AP Working channel , Through the observation just now , The working channel of the wireless router we want to test is 6;
–bssid Channeled mac Address
-w Followed by the file name to save , here w Namely “write Write ” It means , So enter the file name you want to keep , Here's the picture 10 I'll write here as longas. that , What little black people must pay attention to is : Here, although we set the saved file name to longas, But the generated file is not longase.ivs, It is longas-01.ivs.
This page is about to grab the handshake package

Here, in order to get what you need to crack WPA2 Handshake verification of the entire complete packet , We will send a message called “Deauth” To forcibly disconnect the legal wireless client connected to the wireless router , here , The client will automatically reconnect to the wireless router , We also have the opportunity to capture WPA2 Handshake verification of the complete packet .
Because it must be disconnected, the handshake bag will be generated in practice
STATION It's the client on our mobile phone mac Address We need to disconnect him
There is a problem with the following code , I've tried all the online tutorials , Can't even execute , I still took another device , Just got the handshake bag .
aireplay-ng -0 0 -a 44:4B:7E:8A:45:FD -c A6:85:62:CD:84:A3 wlan0mon
// This format
-0 use deauth Attack mode , Keep up with the number of attacks , Here I set it to 1, You can set it to... According to the actual situation 10 Unequal
-a Followed by the router mac Address
-c Followed by the client mac Address
aireplay-ng -3 -b AP Of mac -h Client's mac mon0
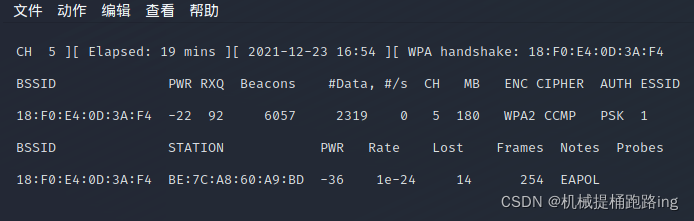
appear handshake It's a successful crack
Now start using your own dictionary Match the package .
aircrack-ng -w /root/wifi.txt /root/test-01.cap( To use absolute paths )
wifi.txt It's a blasting dictionary ,test-01.ivs It's the file of the grabbed package

Get the password perfectly !
summary
The above code that kicks out others cannot run .
I got the handshake package immediately after I connected it with another device
版权声明
本文为[Mechanical bucket running]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220745203497.html
边栏推荐
- SQL server2019无法下载所需文件,这可能表示安装程序的版本不再受支持,怎么办了
- 机器学习(周志华) 第十四章概率图模型
- 牛客手速月赛 48 C(差分都玩不明白了属于是)
- 能做多大的单片机项目程序开发,就代表了你的敲代码的水平
- JDBC JDBC
- Download the genuine origin Pro 2022 tutorial and how to activate it
- Global, exclusive and local routing guard
- Rhcsa second day operation
- JZ35 replication of complex linked list
- 基于Torchserve部署SBERT模型<语义相似度任务>
猜你喜欢
基于Scrum进行创新和管理
ROP Emporium x86_64 7~8题
【Hcip】OSPF常用的6种LSA详解

Modification du contenu de la recherche dans la boîte déroulante par PHP + MySQL

1215_ Hello world used by scons

How big the program development of single chip microcomputer project can be, it represents your level of knocking code

认识进程(多线程_初阶)

魔王冷饭||#078 魔王答上海、南京行情;沟通指导;得国和打杀筛选;赚钱的目的;改变别人看法

Global, exclusive, local Routing Guard

高效音乐格式转换工具Music Converter Pro
随机推荐
Les derniers noeuds K de la liste jz22
Windows MySQL 8 zip installation
Learn regular expression options, assertions
Actual combat of industrial defect detection project (IV) -- ceramic defect detection based on hrnet
Talk about current limiting
Machine learning (Zhou Zhihua) Chapter 14 probability graph model
基于Torchserve部署SBERT模型<语义相似度任务>
一个国产图像分割项目重磅开源!
JZ35 replication of complex linked list
Looking for a job, writing a resume to an interview, this set of information is enough!
MySQL / SQL Server判断表或临时表存在则删除
Global, exclusive and local routing guard
LeetCode 1450 - 1453
How to solve the complexity of project document management?
C language 171 Number of recent palindromes
How big the program development of single chip microcomputer project can be, it represents your level of knocking code
程序设计天梯赛 L1-49 天梯赛分配座位(模拟),布响丸辣
基于Scrum进行创新和管理
Push data from onenet cloud platform to database
【工欲善其事必先利其器】论文编辑及文献管理(Endnote,Latex,JabRef ,overleaf)资源下载及使用指南