当前位置:网站首页>Canary publishing using ingress
Canary publishing using ingress
2022-04-23 09:18:00 【May the waves make the ends of the world】
Use Ingress Implement Canary release
One 、 Basic introduction
Service It is based on four layer protocol to realize routing and forwarding , Commonly used in NodePort Way to provide external services , however When we have many business modules , Use NodePort The way is not conducive to management . therefore , We can use Ingress Controller By matching URL The way to achieve HTTP/HTTPS agent .
Ingress characteristic :
- By configuring Ingress, It can provide accessible services to internal services URL、 Load balancing 、 End SSL/TLS, And it can provide virtual host based on domain name .
Ingress Supported scheduling methods :
- URL Path mapping scheduling : By configuring Ingress Medium
pathRealization . - Host scheduling : By configuring Ingress Medium
hostRealization .
Ingress Common configuration methods : Users access the domain name , Domain name resolves to SLB Of IP Address , next SLB Proxy the request to the port currently listening , What we bind here is Ingress Mapped port number .Ingress By matching the URL Find the bound Service, Last Service Forward the request to the back end Pod Application .

Two 、Ingress Introduction
1. install
[root@k8s-master01 ~]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v0.48.1/deploy/static/provider/cloud/deploy.yaml
[root@k8s-master01 ~]# sed -i 's/LoadBalancer/NodePort/' deploy.yaml # Ingress The way of providing services
[root@k8s-master01 ~]# sed -i 's/Deployment/DaemonSet/' deploy.yaml # Ingress Deployment way
[root@k8s-master01 ~]# sed -i '/k8s.gcr.io/s/image:.*/image: registry.aliyuncs.com\/google_containers\/nginx-ingress-controller:v0.48.1/' deploy.yaml
[root@k8s-master01 ~]# kubectl apply -f deploy.yaml
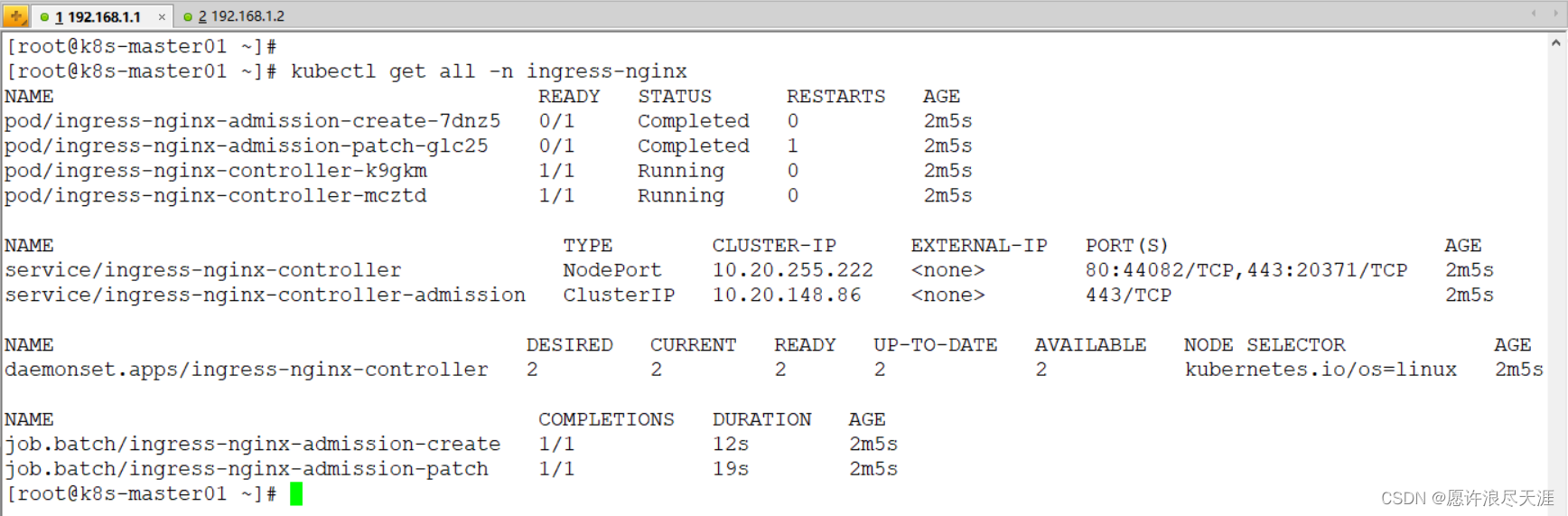
[root@k8s-master01 ~]# kubectl get all -n ingress-nginx
2. Basic use
1) establish Pod and Service
[root@k8s-master01 ~]# vim test-web-server.yaml
apiVersion: v1
kind: Pod
metadata:
name: test-web-server
labels:
app: test-web-server
spec:
containers:
- name: test-web-server
image: registry.cn-hangzhou.aliyuncs.com/zhuang_zz/test:web-v1
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: test-web-server
spec:
ports:
- name: test-web-server
port: 8080
targetPort: 8080
selector:
app: test-web-server
[root@k8s-master01 ~]# kubectl apply -f test-web-server.yaml
2) establish Ingress
[root@k8s-master01 ~]# vim test-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: test-web-server
servicePort: 8080
path: /
[root@k8s-master01 ~]# kubectl apply -f test-ingress.yaml
Because our domain name is custom configured , So you need to configure Hosts analysis ( Local parsing )
Linux:/etc/hosts
Windows:C:\Windows\System32\drivers\etc\hosts
3) verification

1) adopt Ingress Realization HTTPS agent
[root@k8s-master01 ~]# openssl req -x509 -nodes -days 365 \
-newkey rsa:2048 -keyout server.key -out server.crt -subj "/CN=*.tianya.com/O=*.tianya.com"
[root@k8s-master01 ~]# kubectl create secret tls www.tianya.com --key server.key --cert server.crt
[root@k8s-master01 ~]# vim test-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: test-web-server
servicePort: 8080
path: /
tls:
- hosts:
- www.tianya.com
secretName: www.tianya.com
2) verification

- Because the certificate configured above is self signed , did not CA authentication , So there will be a certificate error ( This is normal )
1) Realization HTTP Do not automatically jump to HTTPS
When we Ingress The configuration of contains tls when ,HTTP Will automatically jump to HTTPS On . So we can pass ssl-redirect: 'false' To turn off auto jump .
[root@k8s-master01 ~]# vim test-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: 'false'
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: test-web-server
servicePort: 8080
path: /
tls:
- hosts:
- www.tianya.com
secretName: www.tianya.com
[root@k8s-master01 ~]# kubectl apply -f test-ingress.yaml
2) verification

1) adopt Service + Endpoints Implement agent to external application
Let's start using container mode Nginx application , The reason is because it's simple , Easy to verify . If it's physically installed Nginx Direct configuration Endpoints that will do .
[root@k8s-master01 ~]# vim external-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
nodeName: k8s-master01
containers:
- name: nginx
image: nginx:1.21.0
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
hostPort: 8080
volumeMounts:
- mountPath: /usr/share/nginx/html/zhangsan
name: nginx-html
volumes:
- hostPath:
path: /root/zhangsan
name: nginx-html
---
apiVersion: v1
kind: Endpoints
metadata:
name: nginx
subsets:
- addresses:
- ip: 192.168.1.1
ports:
- port: 8080
---
apiVersion: v1
kind: Service
metadata:
name: nginx
spec:
ports:
- port: 80
targetPort: 8080
[root@k8s-master01 ~]# kubectl apply -f external-nginx.yaml
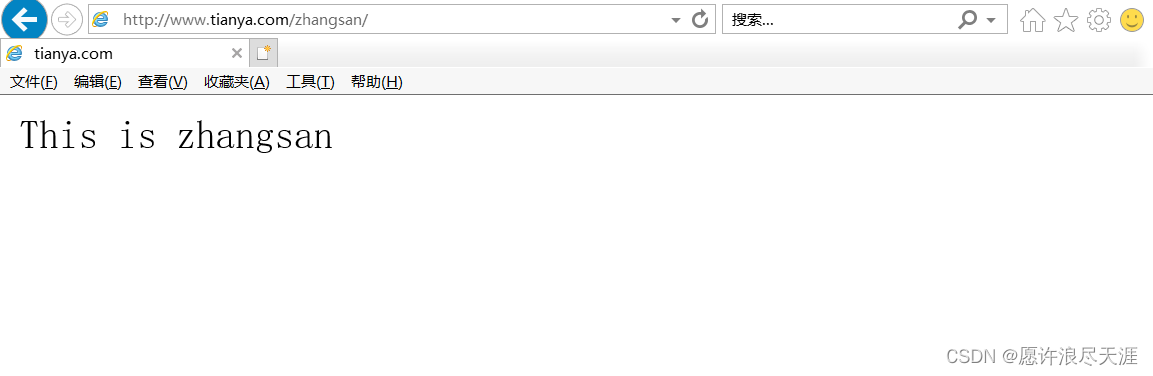
[root@k8s-master01 ~]# echo "This is zhangsan" > /root/zhangsan/index.html
2) modify Ingress To configure
[root@k8s-master01 ~]# vim test-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: 'false'
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: test-web-server
servicePort: 8080
path: /
- backend:
serviceName: nginx
servicePort: 80
path: /zhangsan/
tls:
- hosts:
- www.tianya.com
secretName: www.tianya.com
[root@k8s-master01 ~]# kubectl apply -f test-ingress.yaml
3) verification
3. Implement Canary release
Release of canary , Also known as grayscale publishing , Simply put, it means switching between two versions , We can allocate a small amount of traffic to new applications first , For functional verification . When the verification passes , We can fully allocate traffic to new applications . Even if there is a problem in the verification , You can also quickly switch the traffic back to the old application .
Ingress Mainly through configuration annotations To achieve Canary release : The official introduction
1) be based on Weight Implement Canary release
[root@k8s-master01 ~]# vim uat-web-server.yaml
apiVersion: v1
kind: Namespace
metadata:
name: uat
---
apiVersion: v1
kind: Pod
metadata:
name: uat-web-server
namespace: uat
labels:
app: uat-web-server
spec:
containers:
- name: uat-web-server
image: registry.cn-hangzhou.aliyuncs.com/zhuang_zz/test:web-v2
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: uat-web-server
namespace: uat
spec:
ports:
- name: uat-web-server
port: 8080
targetPort: 8080
selector:
app: uat-web-server
[root@k8s-master01 ~]# kubectl apply -f uat-web-server.yaml
2) modify Ingress To configure
[root@k8s-master01 ~]# vim canary-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: test-web-server
servicePort: 8080
path: /
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: uat-ingress
namespace: uat
annotations:
nginx.ingress.kubernetes.io/canary: "true"
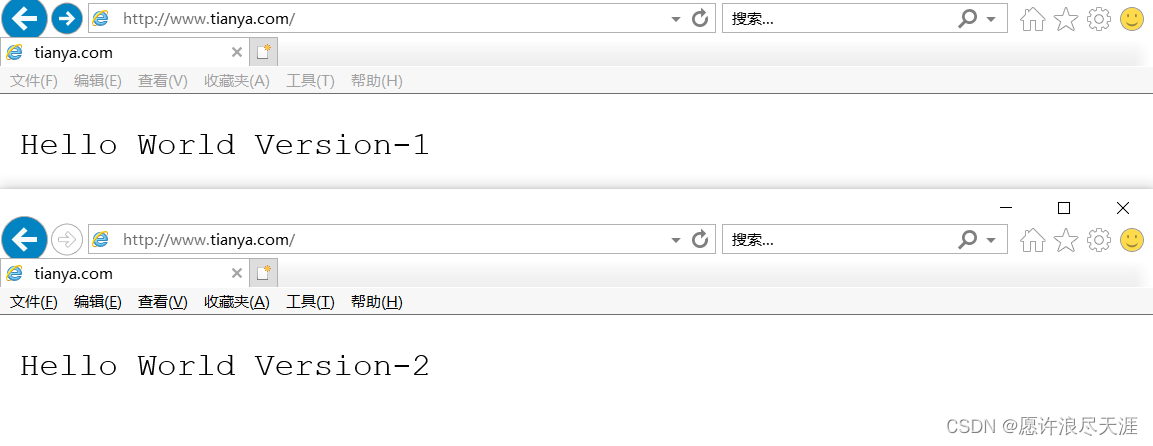
nginx.ingress.kubernetes.io/canary-weight: "30"
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: uat-web-server
servicePort: 8080
path: /
[root@k8s-master01 ~]# kubectl apply -f canary-ingress.yaml
3) verification
1) be based on Cookie Implement Canary release
[root@k8s-master01 ~]# vim canary-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: uat-ingress
namespace: uat
annotations:
nginx.ingress.kubernetes.io/canary: "true"
nginx.ingress.kubernetes.io/canary-by-cookie: "uat-web-canary"
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: uat-web-server
servicePort: 8080
path: /
[root@k8s-master01 ~]# kubectl apply -f canary-ingress.yaml
2) verification

1) be based on Header Implement Canary release
[root@k8s-master01 ~]# vim canary-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: uat-ingress
namespace: uat
annotations:
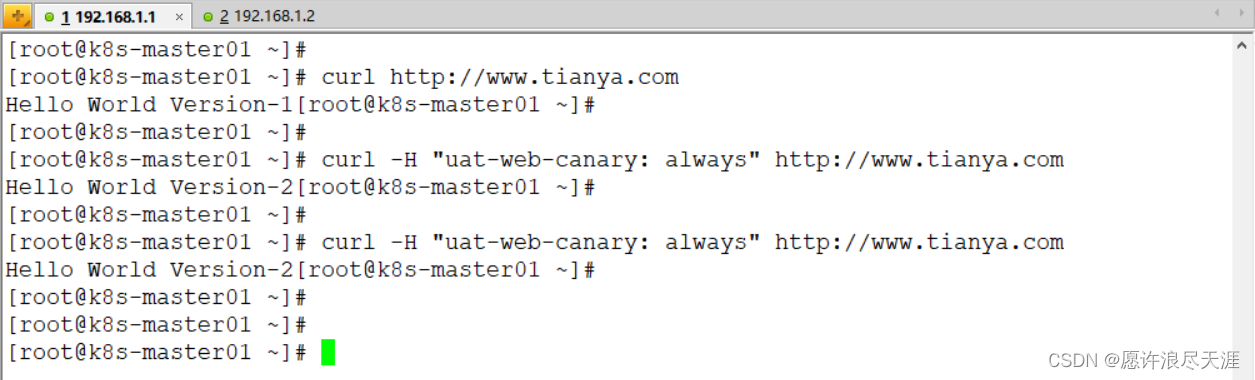
nginx.ingress.kubernetes.io/canary: "true"
nginx.ingress.kubernetes.io/canary-by-header: "uat-web-canary"
spec:
rules:
- host: www.tianya.com
http:
paths:
- backend:
serviceName: uat-web-server
servicePort: 8080
path: /
[root@k8s-master01 ~]# kubectl apply -f canary-ingress.yaml
2) verification
版权声明
本文为[May the waves make the ends of the world]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230633358519.html
边栏推荐
- Kettle实验 (三)
- tsdf +mvs
- Applet in wechat and app get current ()
- Go language self-study series | golang nested structure
- Technological innovation in government affairs in the construction of Digital Government
- Cross domain configuration error: when allowcredentials is true, allowedorigins cannot contain the special value "*“
- What is augmented reality technology? Where can it be used?
- Pctp test experience sharing
- Flink reads MySQL and PgSQL at the same time, and the program will get stuck without logs
- OpenCV中的图像处理 —— 轮廓入门+轮廓特征
猜你喜欢
![[58] length of the last word [leetcode]](/img/c5/3ba1fe5a81593d9576bb597f0d5f45.png)
[58] length of the last word [leetcode]
Kettle实验

Strength comparison vulnerability of PHP based on hash algorithm

MySQL小练习(仅适合初学者,非初学者勿进)

Pctp test experience sharing

Experimental report on analysis of overflow vulnerability of assembly language and reverse engineering stack

Data visualization: use Excel to make radar chart

Matlab draw five-star red flag

Kettle实验 (三)
![[in-depth good article] detailed explanation of Flink SQL streaming batch integration technology (I)](/img/c9/43a63f526068ef6a3e4964a22c5a1f.png)
[in-depth good article] detailed explanation of Flink SQL streaming batch integration technology (I)
随机推荐
Flink SQL realizes the integration of stream and batch
Kettle experiment conversion case
Vivo, hardware safe love and thunder
MYCAT configuration
npm报错 :operation not permitted, mkdir ‘C: \Program Files \node js \node_ cache _ cacache’
112. 路径总和
NPM reports an error: operation not allowed, MKDIR 'C: \ program files \ node JS \ node_ cache _ cacache’
2021 Li Hongyi's adaptive learning rate of machine learning
Base de la technologie électronique numérique 3.1 aperçu du circuit de porte, 3.2 circuit de porte à diode semi - conductrice
501. Mode in binary search tree
LeetCode_DFS_中等_1254. 统计封闭岛屿的数目
[58] length of the last word [leetcode]
数字政府建设中政务中台中的技术创新点
Chapter VIII project stakeholder management of information system project manager summary
The crawler returns null when parsing with XPath. The reason why the crawler cannot get the corresponding element and the solution
Leetcode-199 - right view of binary tree
653. Sum of two IV - input BST
On array replication
小程序报错:Cannot read property 'currentTarget' of undefined
[boutique] using dynamic agent to realize unified transaction management II