当前位置:网站首页>Logic unauthorized and horizontal and vertical unauthorized payment tampering, verification code bypass, interface
Logic unauthorized and horizontal and vertical unauthorized payment tampering, verification code bypass, interface
2022-08-09 19:42:00 【a Traveler】
参考:内容来源00实验室笔记;
Ultraviolet loopholes are divided into horizontal and vertical unauthorized access;
水平越权:
比如说,users of the same level,用户APermissions can go to have usersB的权限;
垂直越权:
Permission acquisition for users of different levels;
水平越权:by replacing aID之类的身份标识,从而使AAccount acquisition and modificationB账号数据;垂直越权:使用低权限身份的账号,发送高权限账号才能有的请求,Get its higher-privileged action;通过删除请求中的认证信息后重放该请求,依旧可以访问或者完成操作

原理:
front-end security;
After the interface judges the user level,Filter the displayed content,(比如,Administrator user than the average user interface,ordinary users do not,Not that this feature isn't just hidden.)
If the user's number appears in the packet,User group number or type number,You can try to modify and see if there is a loophole
靶场举例:
水平越权
pikachuLogical level unauthorized login in the shooting rangekobe相关信息,登录,Capture personal information when viewing it,

Capture personal information when viewing it,可以得到

将username更改为lucy,便可得到lucy的相关信息

垂直越权
在登录admin(higher level administrator)的情况下,Capture its operation,在登录pikachu(lower level users)时,You can call out the higher-level package,更改cookiePHPSESSID=的值,可以条件:需要有admin的数据包
change relateduser值,to add it

条件:可以抓到admin的数据包
1、普通用户前端有操作界面可以抓取数据包
2、盲猜
3、Build your own through the source code of the website to get it
墨者靶场
capture two packets,see a packagecard_id的值,我们考虑用burp suite的thunderfunction to blast it,排序相关的lengthCheck for larger values,Source address or view images,You can see Ma Chunsheng's relatedcaid_id账号,View account and password in this package(may require decryption),登录,得到其flag;

第二部分: Logical unauthorized login vulnerable payment tampering
登录界面:
http 和https :其中登录 的密码;httpUsually transmitted in clear text;而HTTPS是加密过的;httpCan be cracked by blasting;And to identify the encryption way of encryption;
密码爆破:httpThe password is transmitted in clear text,在burpdirect dictionary blasting;
HTTPS的话,To judge the password encryption,Then set the password to encrypt;
Such an attack would bemd5The encryption method to blast the password;
HTTPS cookie Weak crack;
Usually requires source code for code audit discovery,有的cookie里面包含了username,Then check it with or without value,通过对usernameForgery can be bypassed to jump to the relevant page;

Then there is the issue of order modification:
1. 抓包,修改相关值(ID,price,num,statu等),quantity can be changed to-1

或者是,To grab the order Numbers for first10Yuan of packets,then buy and add1000When yuan,Change the package order number to10元的,then just pay10元
2、Or capture the package to modify the information of related products,id值和name值.


3、修改支付状态
找回重置机制:客户端回显,response状态值,验证码爆破(Number of verification codes,时间),Back flow bypass interface, etc
第三部分 SMS email verification code verification bypass;

找回重置机制:
客户端回显,response状态值,验证码爆破(Number of verification codes,时间),找回流程绕过等
接口调用乱用:短信轰炸,call bombing
第一:墨者靶场,Some reset password operations will put the verification code and reset password on the same page,This can lead to vulnerabilities,The normal page is,The first page is the verification verification code,After successfully into the second page to reset your password;
In the former case, we can use the registered account to accept the verification code first.,Then grab the package and change the phone number to the target phone number,So that you can achieve change a phone number of the password;
第二 Client echo validation,Some websites will attach the verification code to the data packet;For example, in Hanchuan Recruitment Network:

手机邮箱验证码逻辑-客户端回显-实例抓包,在数据包里面,You can directly see the verification code and just enter a verification code,抓包,Then take over the whole process,change the status code,例如将3改为1,It makes sense to modify with the current reply value,If the server is used to verify,就不行,It means that the front-end verification can be,But if the verification code is placed on the backend server,No matter what you do, you can't change;
responseEcho Status Vulnerability: When changing or resetting the password,We can use our account verification code to pass the verification code,By getting the right response package status code,Then can be modified by entering the wrong captcha response package status code to achieve the effect of the change the password;
Intercept response packet operation

In addition, if the verification code has no number of operations, it can be blasted;
第四部分 token,验证码,接口

图片验证码的识别:
插件和工具
图形验证码绕过,分为前端和后端;How to distinguish between front end and back end?
查看源代码,If there is obvious code in the source code to check that the captcha is correct,一般为js 代码,那么就是 前端,很好绕过,Directly after the first input correct verification code inside the tool;
If it is backend validation,First of all, there are some websites' verification code verification verification for the first time,We can capture the package and use the first verification code.,Why is there such a loophole??The principle is that each verification code is not eliminated after verification;
if strong,就使用使用burp插件captcha-killer识别图片验证码;
再进行爆破;
captcha-killer 使用方法:
1.复制图片地址,Capture the packet and send it here;’

2.接口利用,(Temporarily didn't find good paying interface)
在Intruder模块调用
After configuring,可以点击锁定lock the current configuration,Prevents being modified to cause blasting failure!Then install the following steps to configure

设置Intruderblasting mode andpayload位置

验证码payloadChoose to have plugins to generate

token
token就是令牌,An effective form of front-end and back-end authentication,比传统的 session Authentication is more convenient,简单来说:When the user logs in for the first time,The website will give you a“门卡”,In the future, you can enter directly with the key card,Without the need to apply for again.But after a while the door card,You need to go to the front desk to magnetize,The key card here is token
可以防止重放攻击; crsf
token 的绕过
General won't bypass,但是如果tokenwill be echoed in the packet,就可以绕过,使用burp,The range is in Pikachu;
When the echo in the packet containstoken的时候,how to grabtokenAnd the incoming blasting?
1.set load;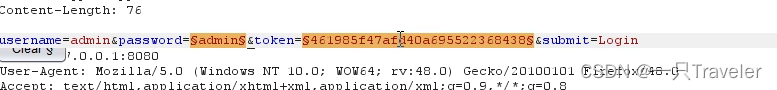
2.Mode selection tuning forkpitchar模式
3.在option设置线程为1,because each packettokenvalue will change,If there are too many threads, I don't know which one to choose;
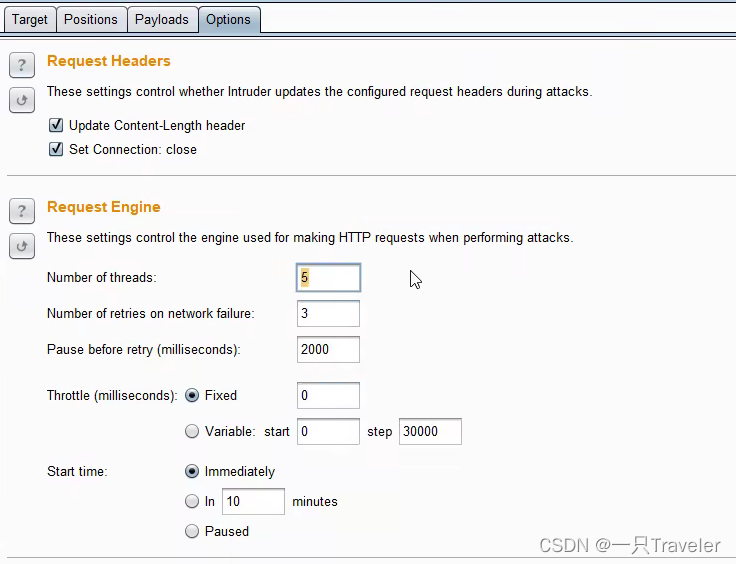
4.往下翻,find redirect selectionalways

5.在Grep-Extract里面添加,选中token的值,点OK


6.在tokenThe load location for example here is2,模式选择Recursive grep 递归搜索;
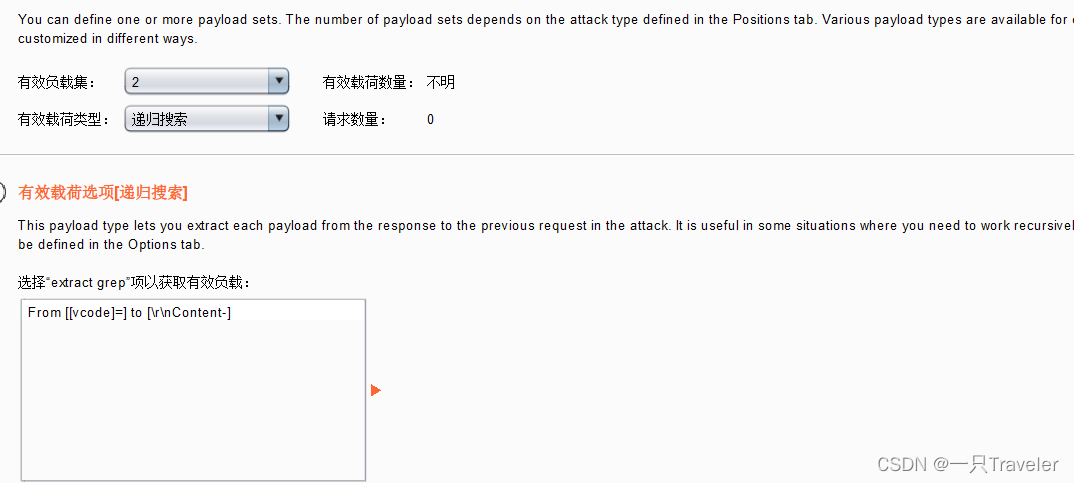
callback The echo interface may have a cross-site vulnerability,就是说,The echo will have a string of addresses and access,If this address is changed, there may be a cross-site vulnerability;

边栏推荐
猜你喜欢

.NET 6学习笔记(4)——解决VS2022中Nullable警告

小家电控制板开发——未来小家电行业的发展方向

How to choose a good SaaS knowledge base tool?
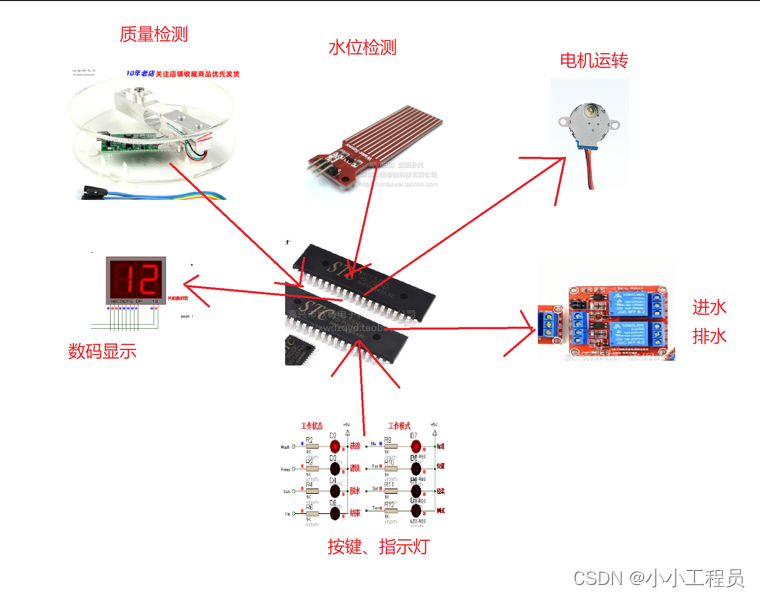
A42 - 基于51单片机的洗衣机设计

AlphaControls 控件 TsPanel TsGroupBox 块与组的结合

What is hardware integrated development?What are the cores of hardware integrated development?

测试/开发程序员喜欢跳槽?跳了就能涨工资吗?

110+ public professional datasets summarized

MASA Stack 第三期社区例会
安装MySQL的最后一步第四个红叉怎么解决
随机推荐
TMin - whether TMin overflows
一键生成 API 文档的妙招
央企施工企业数字化转型的灵魂是什么
How to adjust futures account opening process and handling fee
【解决】虚拟机VMware通过局域网连接机器人no route to host
面试中老生常谈的MySQL问答集锦夯实基础
B019 - 甲醛甲烷煤气温湿度时间测试仪
ABP详细教程——模块类
最新!2022版新员工基础安全知识教育培训PPT,企业拿去直接用
B024 – STM32温湿度控制体温检测烟雾报警系统
Substrate 源码更新导读八月第1周: 新版事务化存储层启用默认模式, Polkadot v0.9.27发布
ceph部署
@AllArgsConstructor and @NoArgsConstructor
微服务:事务管理
Functions and Features of Smart Home Control System
《.NET物联网从零开始》系列
SimpleDateFormat线程安全问题和解决方案
dotnet 6 为什么网络请求不跟随系统网络代理变化而动态切换代理
Arrow parquet 之 String Reader
【燃】是时候展现真正的实力了!一文看懂2022华为开发者大赛技术亮点