当前位置:网站首页>JMM model of concurrent programming and three characteristics of concurrency
JMM model of concurrent programming and three characteristics of concurrency
2022-04-21 13:49:00 【bingtanghulu_ six】
Catalog
2. Concurrency and parallelism
3. Three features of concurrency
4. java Concurrent knowledge system
6. CPU Three level cache architecture
7. Cache consistency mechanism
1. JMM Model
JMM The memory model is java A specification proposed by virtual machine , Used to coordinate the differences between the operating system and hardware , Achieve concurrency .
Among them is 8 An atomic instruction :
1.lock: Lock variable
2.unlock: Unlock locked variables , When locking multiple times, you need to unlock the same number of times , Locking and unlocking must occur in pairs
3. read,load: Read the variable value from main memory and load it into local memory , Two atomic instructions must be executed sequentially
4. use: Give the variable value in local memory to the execution engine , Ready for thread use
5. assign: Assign the value of the execution engine to the local memory
6. store,write: Store variable values from local memory and write them to main memory , Two atomic instructions must be executed sequentially

2. Concurrency and parallelism
Concurrent : Only one instruction can be executed at a time , And the switching time between accompanying instructions is very short .
parallel : Multiple instructions are executed at the same time
3. Three features of concurrency
Atomicity : A single instruction is indivisible
visibility : Write to variable , The last written value can be seen in the task thread
Orderliness : The programming sequence is consistent with the execution sequence , Keep this order consistent even in multithreading
Operations to ensure visibility :
1. Memory barrier :
volatile, Memory barrier (jdk8 in UnsafeFactory.getUnsafe().storeFence(); Call the memory barrier )
synchronized,lock,final
2. Context switch :Thread.yieled
Actually at the bottom C++ It is to call the assembly instruction to call the memory barrier , If you need to view the assembly instructions, you can view them in VM Add
-XX:+UnlockDiagnosticVMOptions -XX:+PrintAssembly -XcompIf there is a lack of hsdis-amd64.dll Files need to be downloaded, and assembly instructions can be printed on the console , By searching lock keyword .
4. java Concurrent knowledge system
1. Thread basis
2. Thread safety : Sync , Mutually exclusive , Division of labor
3. Concurrent tool class
4. Concurrent design patterns
5. Computer architecture

6. CPU Three level cache architecture
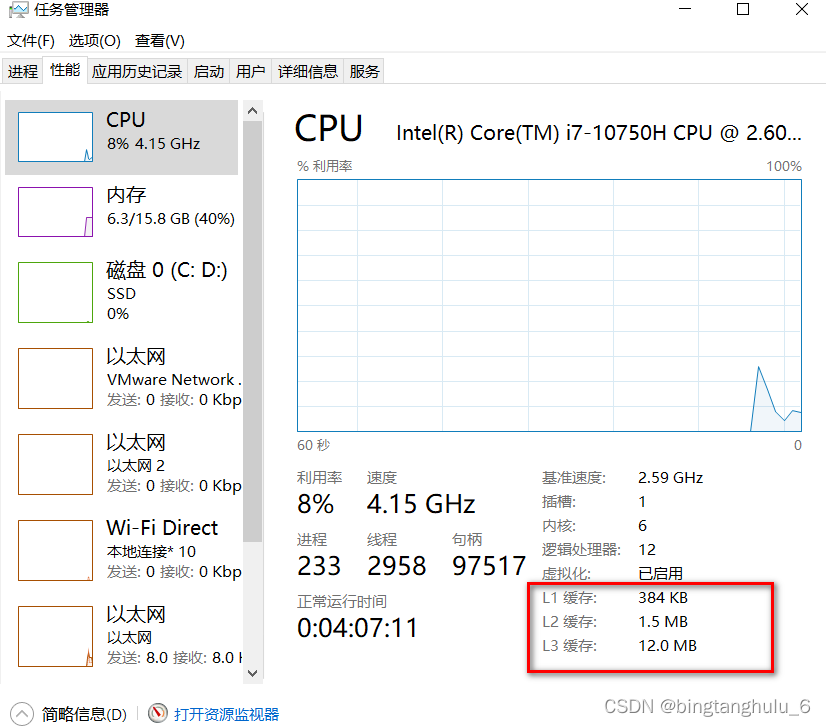
CPU Now there is generally a three-level cache architecture : Two L1Cache, One L2 Cache, A shared L3 Cache

7. Cache consistency mechanism
There is now a mechanism in the computer to ensure cache consistency : Snooping mechanism and directory based mechanism .
Snooping mechanism : Every request must be broadcast to all nodes in the system , fast , But it takes a lot of bandwidth .
Directory based mechanism : Longer delay , Bandwidth usage is minimal .
Locality principle : stay CPU When accessing a storage device , Whether stored data or instructions tend to gather in a continuous area . Divided into two : Time locality and space locality .
Temporal locality : A message is accessed , Then it may be visited in the near future .
Spatial locality : If a memory location is referenced , Then the location near it will also be referenced .
8.java Visibility assurance
Single threaded programs cannot guarantee memory visibility problems .
Using synchronized programs correctly can ensure memory visibility by prohibiting compiler and processor reordering .
Multithreading that is not synchronized correctly cannot guarantee .
There are four kinds of memory barriers at the assembly instruction level :LoadLoad,LoadStore,StoreStore,StoreLoad, but X86 There is only one processor stroeLoad It works , The other three are null operations .
JVM Hierarchical memory barrier :UnSafeFactory.getUnSafe().storeFence(); This way of calling the memory barrier jdk8 May be abandoned later , In general use volatile Ensure memory visibility .
volatile Memory semantics :
1. visibility : To a volatile Decorated variable , You can always see the last written variable value in multiple threads .
2. Orderliness : Through to volatile Various specific memory barriers are added before and after modified variable reading and writing operations to prohibit instruction rearrangement .
3. Atomicity : Atomicity is not guaranteed
版权声明
本文为[bingtanghulu_ six]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211346550037.html
边栏推荐
- MySQL slow query log and index merge analysis
- Oracle 备份失败报错ORA-04063: view SYS.KU_RADM_FPTM_VIEW has errors
- 机器学习笔记 - Moore-Penrose 伪逆
- 并发编程之CAS和Atomic原子操作类
- Servlet中关于web.xml的测试
- 滚动条样式修改
- String - 1 String length (10 points) the C language standard function library includes the strlen function, which is used to calculate the length of the string. As an exercise, we write a function wit
- OpenLDAP使用ldapadd手动添加用户
- Use of JSON server
- Unittest unit test (V)
猜你喜欢
机器学习笔记 - SVD奇异值分解(3) 在图像上应用 SVD

POI与EasyExcel读写测试

JVM内存模型深度剖析与优化

Chapter 4 - hierarchical query of SQL query

【leetcode】516.最长回文子序列

Peking University ACM problems 1009: edge detection

JVM内存分配机制详解
Markdown grammar and test

Machine learning notes - SVD singular value decomposition (3) applying SVD to images

MySQL Samsung index and cost calculation
随机推荐
Unittest单元测试(三)
Peking University ACM problems 1009: edge detection
Synchronized of concurrent locking mechanism
软件工程-基础篇刷题
Basic training process of image classification -- Based on mobilenet_ V3 as an example
字符串中字符排序 (10 分)请编写函数fun对长度为8个字符的字符串按降序排列。
Scroll bar style modification
npm---npm配置文件
Oracle 备份失败报错ORA-04063: view SYS.KU_RADM_FPTM_VIEW has errors
Common configuration items of echart (line, area, text)
深度学习与图像识别:原理与实践 笔记Day_16
The sales attribute values in sku must be filled in in pairs. Why
深度学习与图像识别:原理与实践 笔记Day_12
深度学习与图像识别:原理与实践 笔记Day_10
String - 1 String length (10 points) the C language standard function library includes the strlen function, which is used to calculate the length of the string. As an exercise, we write a function wit
[special topic of stack and queue] - Dual queue simulation stack
【leetcode】144.二叉树的前序遍历
Nmap usage
关于`Object.clone()`子类不能调用的思考
npm---环境