当前位置:网站首页>[HCIP Continuous Update] Principle and Configuration of IS-IS Protocol
[HCIP Continuous Update] Principle and Configuration of IS-IS Protocol
2022-08-09 13:27:00 【Chuan Dome 2001】
IS-IS protocol principle and configuration
The source of the routing entry
Direct Routing
Indirect routing
Static Routing
Dynamic Routing
IGP Interior Gateway Protocol
Distance vector: RIP
Link Status: OSPF ISIS
EGP Exterior Gateway Protocol: BGP
ISIS Intermediate System to Intermediate System
ISIS protocol is a dynamic routing protocol developed by the ISO national standardization organization for the CLNP protocol in the OSI model. Due to the strong scalability of ISIS, it supports both CLNP and IP protocols.So what is now called ISIS is called Integrated ISIS
ospf----TCP/IP----IP
ISIS----OSI/TCP/IP----IP/CLNP
Scenario application
OSPF - Campus Network - Application Protocol
ISIS—Backbone—Service-Based Protocol
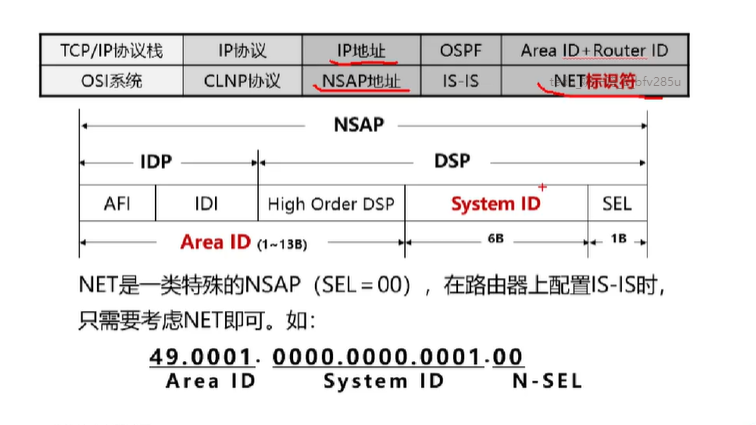
Address Structure
NSAP address: main network + subnet + host + SEL (protocol type)
NET identifier: is a special NSAP address, when SEL=00, the NSAP address becomes the NET identifier
How Dynamic Routing Works
1. Establish neighbor relationship
2. Synchronize the database
3. Calculate the routing table
Router classification
level-1 router ----- quite a special area of OSPF
level-2 router-----equivalent to the backbone area of OSPF
level-1-2 router ---- equivalent to OSPF ABR area border router
level-1 neighbor relationship
Same area: level-1 router and level-1 router or level-1-2 router
level-2 neighbor relationship
Same area: level-2 router and level-2 router or level-1-2 router
Different regions: establishing level-2 relationships
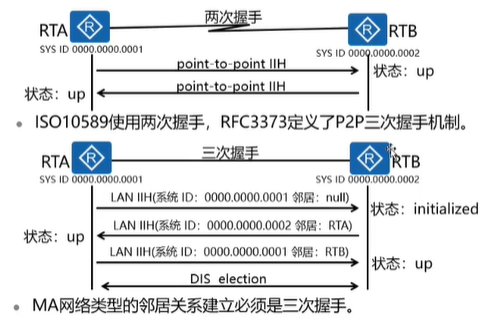
Neighbor HELLO message
Establishing neighbor relationships
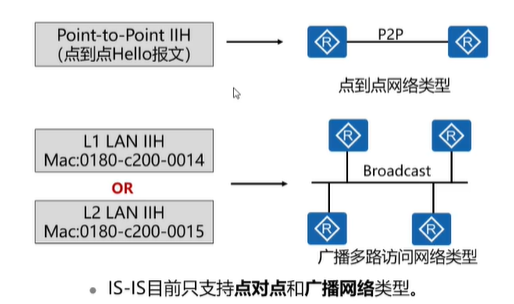
Network Type
1. Point-to-point network: P2P IIH (mac: 0180-C200-0014)
2. Broadcast network L1 lan IIH (mac: 0180-C200-0015)
State Mechanism
1, down
2, init
3, up
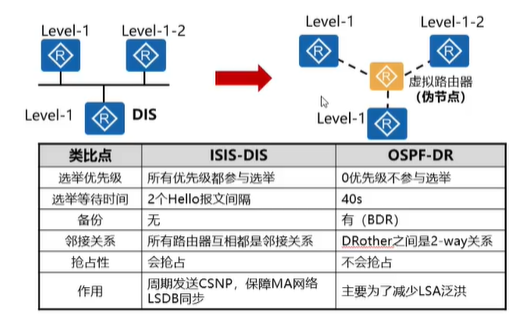
DIS and the analogy between DIS and DR
Barrier of link state information
Establishing neighbor relationships—IIH
Information
—SNP (Sequence Number Message)
—CSNP (Complete Sequence Number Message) ----equivalent to DD in OSPF
—PSNP (Partial Sequence Number Packet) ----equivalent to LSR/LSACK in OSPF
Inter-area routing
1. The layer where the L2 neighbor relationship is located - with detailed routing
2. The layer where the L1 neighbor relationship is located - with a default route pointing to the L1/2 router for external access
3. The L1/2 router sets the ATT field to 1, and the L1 router receives the information with the position 1, and generates a default route pointing to the L1/2 router
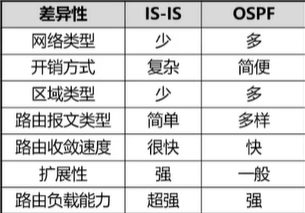
The difference between IS-IS and OSPF
IS-IS configuration
1. Configure basic IP information
2. Configure ISIS
- start ISIS
— configure the NET identifier
——Configure the router type
3. The interface participating in the ISIS calculation starts the ISIS process
4. Verify
Configuring ISIS
isis 100network-enytity 49.0012.0000.0001.00//Configure the net identityis-level level-1//Configure the router typeThe interface participating in the ISIS calculation starts the ISIS process
interface g0/0/0isis enable 100interface LoopBack 0isis enable 100Test View
dis isis peer//View neighbor relationship informationdis isis route // View ISIS routedis ip routing-tableprotocol isisRoute leak
When there are more than two L1/2 routers (ABRs) in the non-backbone area, since the area inside the area accesses the external area through the default route pointing to the L1/2 router, the optimal route calculated internally is in the entire network.The path selection may not be optimal, and there may be sub-optimal paths.Therefore, through route leakage, the detailed route of the backbone area is leaked to the sub-area, and the detailed route of the whole network is obtained.With accurate calculation, sub-routing problems are avoided.- Leaked on ABR
isis 100import-route isis level-2 into level-1边栏推荐
- WeChat payment development process
- 超越CLIP的多模态模型,只需不到1%的训练数据!南加大最新研究来了
- 基于STM32+铂电阻设计的测温仪
- 水能自发变成“消毒水”,83岁斯坦福教授:揭示冬天容易得流感的部分原因...
- Data Mining-05
- AQS同步组件-FutureTask解析和用例
- FFmpeg库在win10上配置使用(不配置libx264)
- 合并两个有序列表
- Report: The number of students who want to learn AI has increased by 200%, and there are not enough teachers
- The FFmpeg library is configured and used on win10 (libx264 is not configured)
猜你喜欢
![[Microservice ~ Remote Call] Integrate RestTemplate, WebClient, Feign](/img/8a/a0d1cf3586b7c33b7bcddf9ffede25.png)
[Microservice ~ Remote Call] Integrate RestTemplate, WebClient, Feign

非科班AI小哥火了:他没有ML学位,却拿到DeepMind的offer

两分钟录音就可秒变语言通!火山语音音色复刻技术如何修炼而成?
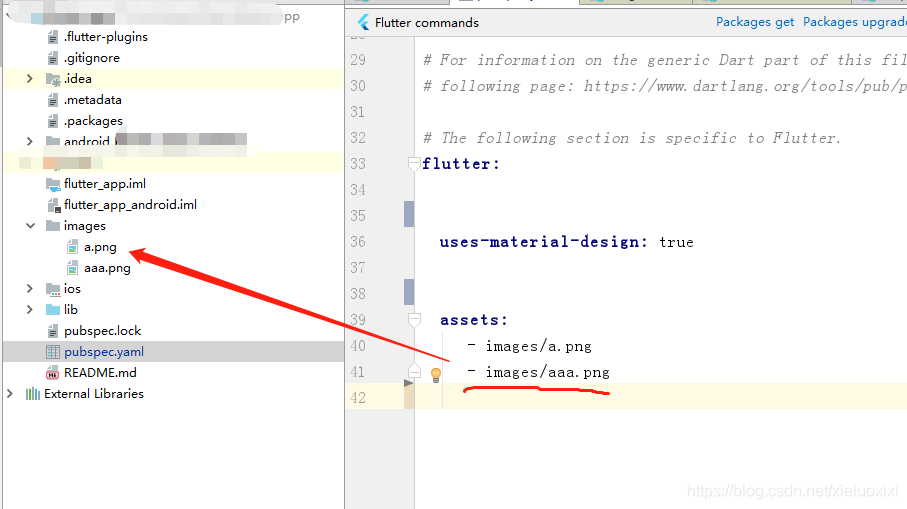
Flutter入门进阶之旅(五)Image Widget
Flutter入门进阶之旅(四)文本输入Widget TextField
win10编译x264库(也有生成好的lib文件)
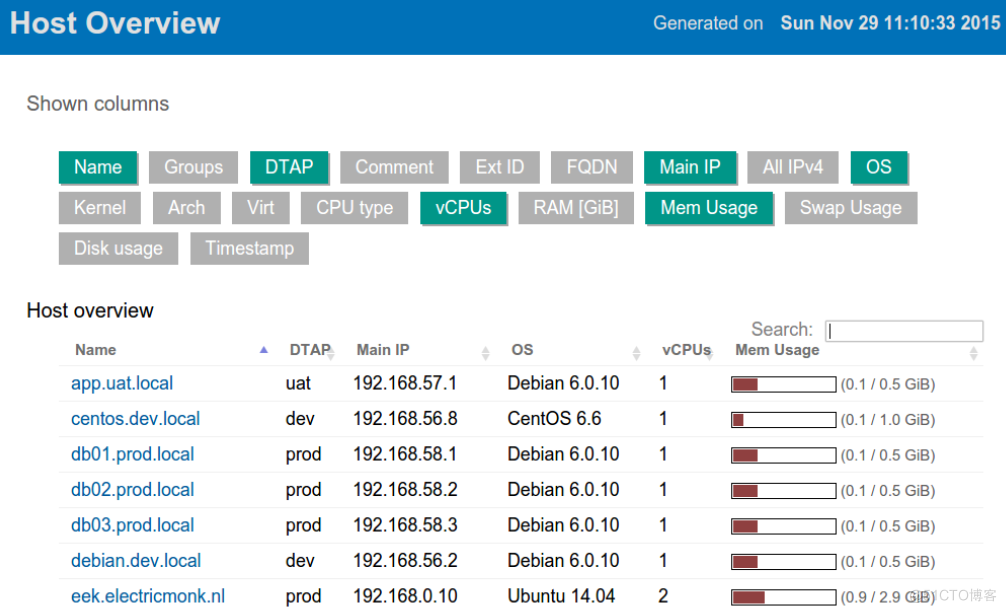
ansible-cmdb友好展示ansible收集主机信息
Go 事,如何成为一个Gopher ,并在7天找到 Go 语言相关工作,第1篇

中科院打脸谷歌:普通电脑追上量子优越性,几小时搞定原本要一万年的计算...
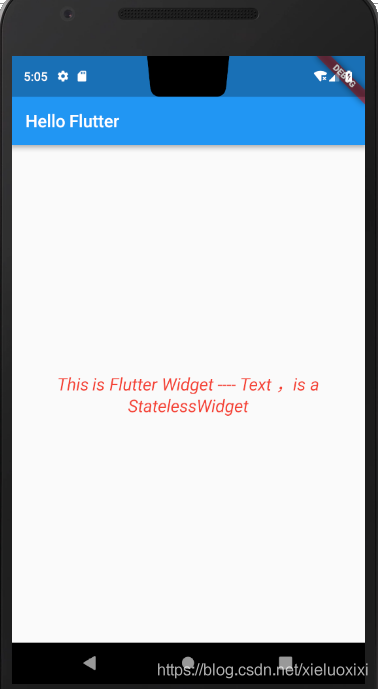
Flutter入门进阶之旅(三)Text Widgets
随机推荐
报告:想学AI的学生数量已涨200%,老师都不够用了
ABP中的数据过滤器 (转载非原创)
AI basketball referee, walking is special, ask harden care don't care
Flutter Getting Started and Advanced Tour (3) Text Widgets
Adalvo收购其首个品牌产品Onsolis
【HCIP持续更新】IS-IS协议原理与配置
张朝阳对话俞敏洪:一边是手推物理公式,一边是古诗信手拈来
ABAP interview questions: how to use the System CALL interface of the ABAP programming language, direct execution ABAP server operating System's shell command?
十分钟教会你如何使用VitePress搭建及部署个人博客站点
WebView injects Js code to realize large image adaptive screen click image preview details
MySQL principle and optimization of Group By optimization techniques
The batch size does not have to be a power of 2!The latest conclusions of senior ML scholars
Reading and writing after separation, performance were up 100%
发明时代,「幂集创新」事关你我
微服务架构的核心关键点
工作任务统计
生成上传密钥和密钥库
[Microservice ~ Remote Call] Integrate RestTemplate, WebClient, Feign
非科班AI小哥火了:他没有ML学位,却拿到DeepMind的offer
LeetCode #101. Symmetric Binary Tree