当前位置:网站首页>Some of the topics in VNCTF2021 are reproduced
Some of the topics in VNCTF2021 are reproduced
2022-08-09 08:40:00 【z.volcano】
Web
[VNCTF 2021]Ez_game
A very magical little game,Check the source code to see threejs文件,main reviewgame.js
My idea is to execute the code in the console,Change the character's parameters,Violent clearance
看到如下代码,Obviously the initial value of the character,从上到下分别对应血量、血量上限、Number of small boomerangs、Number of big boomerangs、金币数量
A small change in the console,Then have fun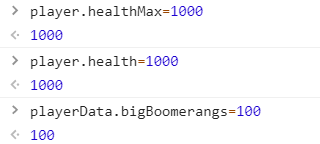
之后看到mumuzi师傅(套神)Provides a faster way of thinking,When a player is found to be victorious,执行了一次winTimer.Set();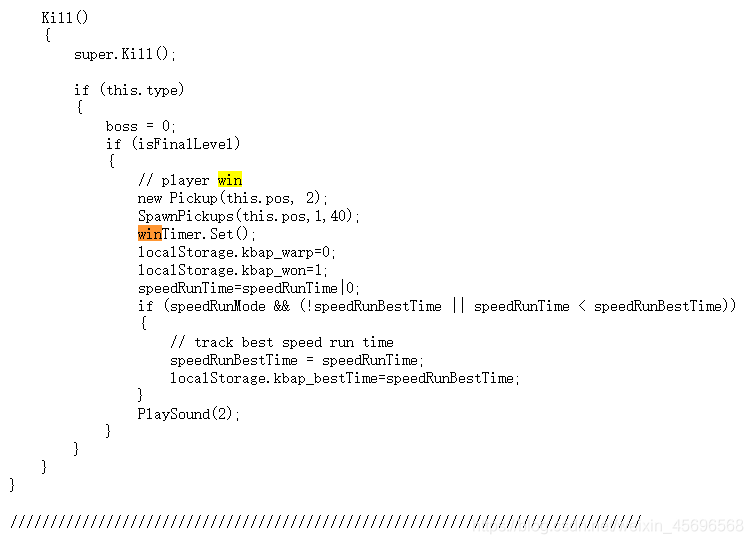
The console executes this code,拿到flag
Misc
Bingbing seems to be hiding a secret
打开压缩包,报错,但是我的rarThe image file can be taken out normally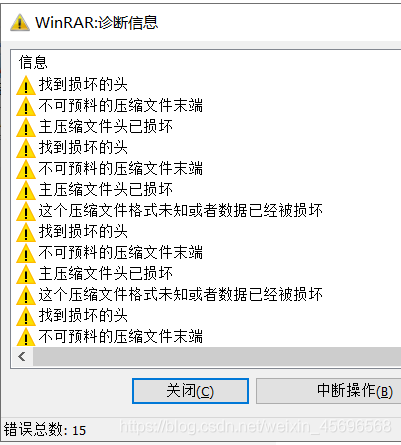
拿到FFT.png
FFT是提示傅里叶变换,跑脚本(Here is the official script)
import cv2 as cv
import numpy as np
import matplotlib.pyplot as plt
img = cv.imread('FFT.png', 0) #直接读为灰度图像
f = np.fft.fft2(img) #做频率变换
fshift = np.fft.fftshift(f) #Transfer the pixels to do the magnitude spectrum
s1 = np.log(np.abs(fshift))#取绝对值:Converting complex numbers to real numbers is logarithmic⽬in order to change the data to 0-255
plt.subplot(121)
plt.imshow(img, 'gray')
plt.title('original')
plt.subplot(122)
plt.imshow(s1,'gray')
plt.title('center')
plt.show()
The result of running out can be seen vaguelyflag,Save to local zoom picture to seeflag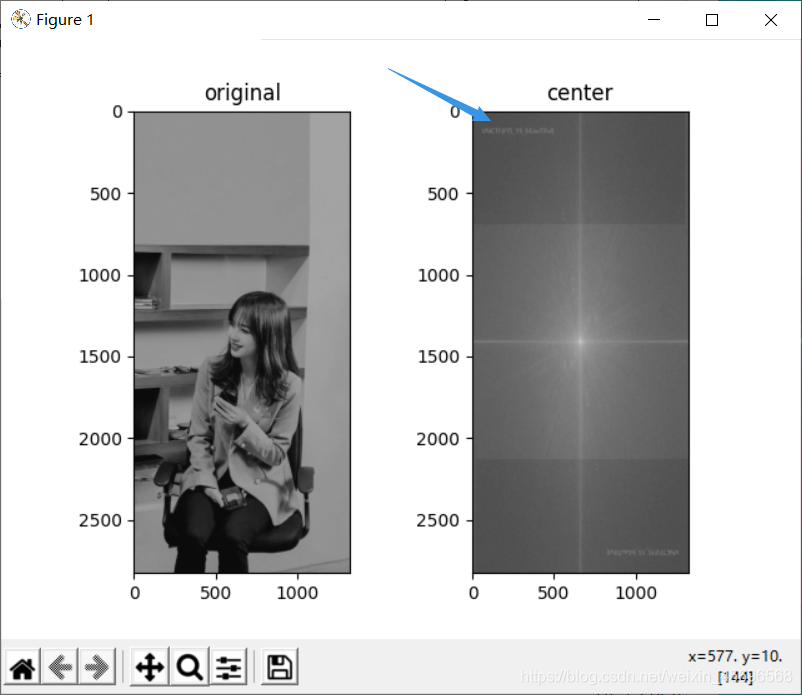
看wp才知道,The reason for the error when opening the compressed package,Because this is the test point–RAR伪加密
确实,It's what you usually seezip伪加密,RARFake encryption is really rare
Repair words andzipPseudo encryption is similar,改一个数字就行,或者直接binwalk分离出来
interesting_fishing
The attachment and the picture are each hidden in halfflag
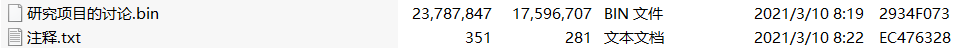
打开第一个bin文件,found likeqq邮件
把文件后缀改成eml,打开得到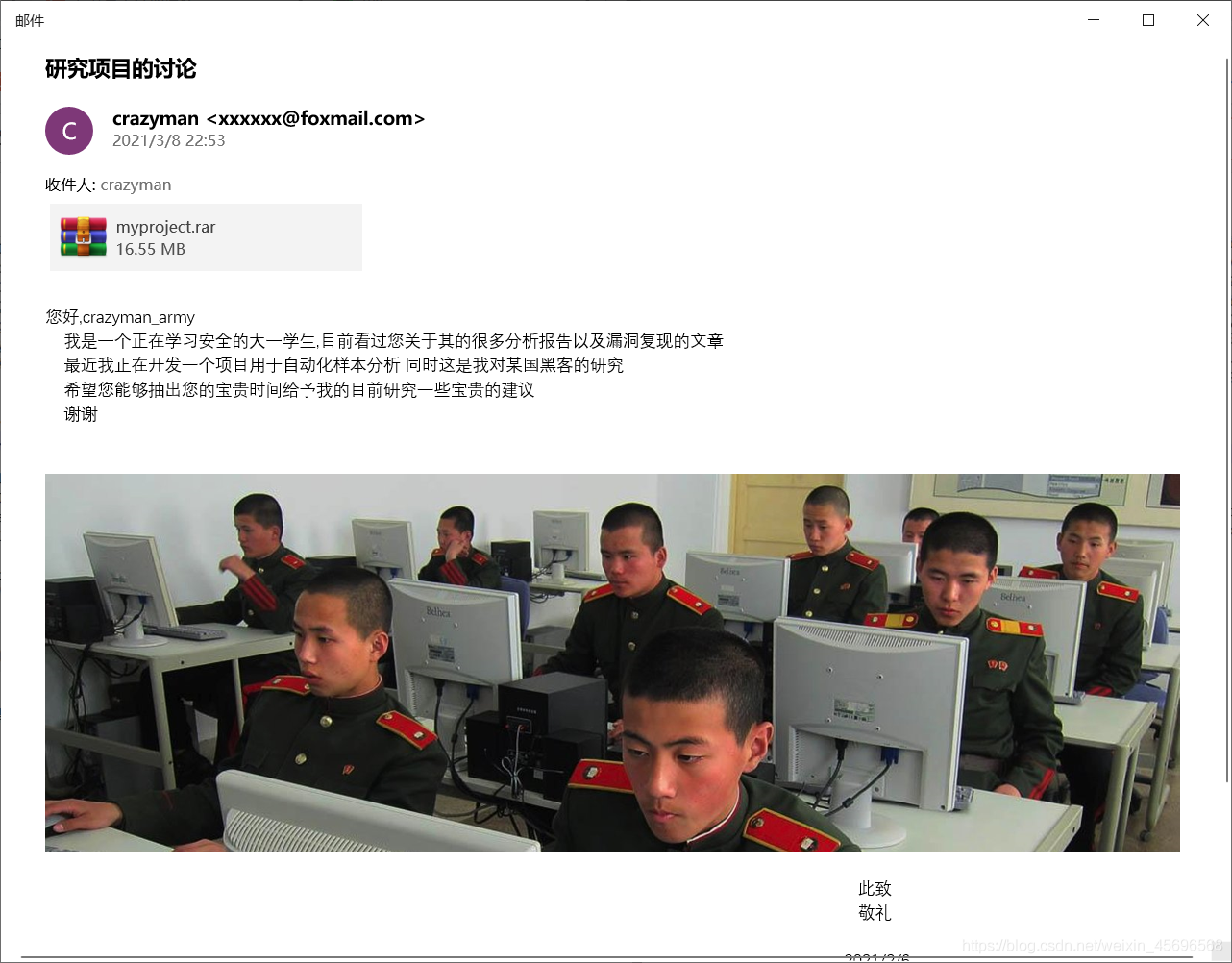
图片的名字是ThisIsSecret.jpg,提示使用our secret解密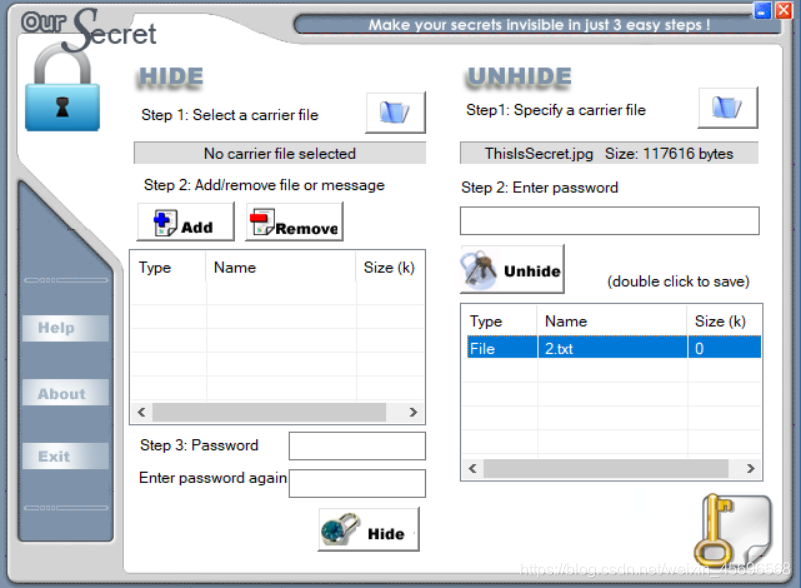
拿到[email protected]@RuS}
Look at another attachment in the email,是一个vs工程文件,用notepad++打开Browse.VC.db,看到一串base64加密的字符串,解密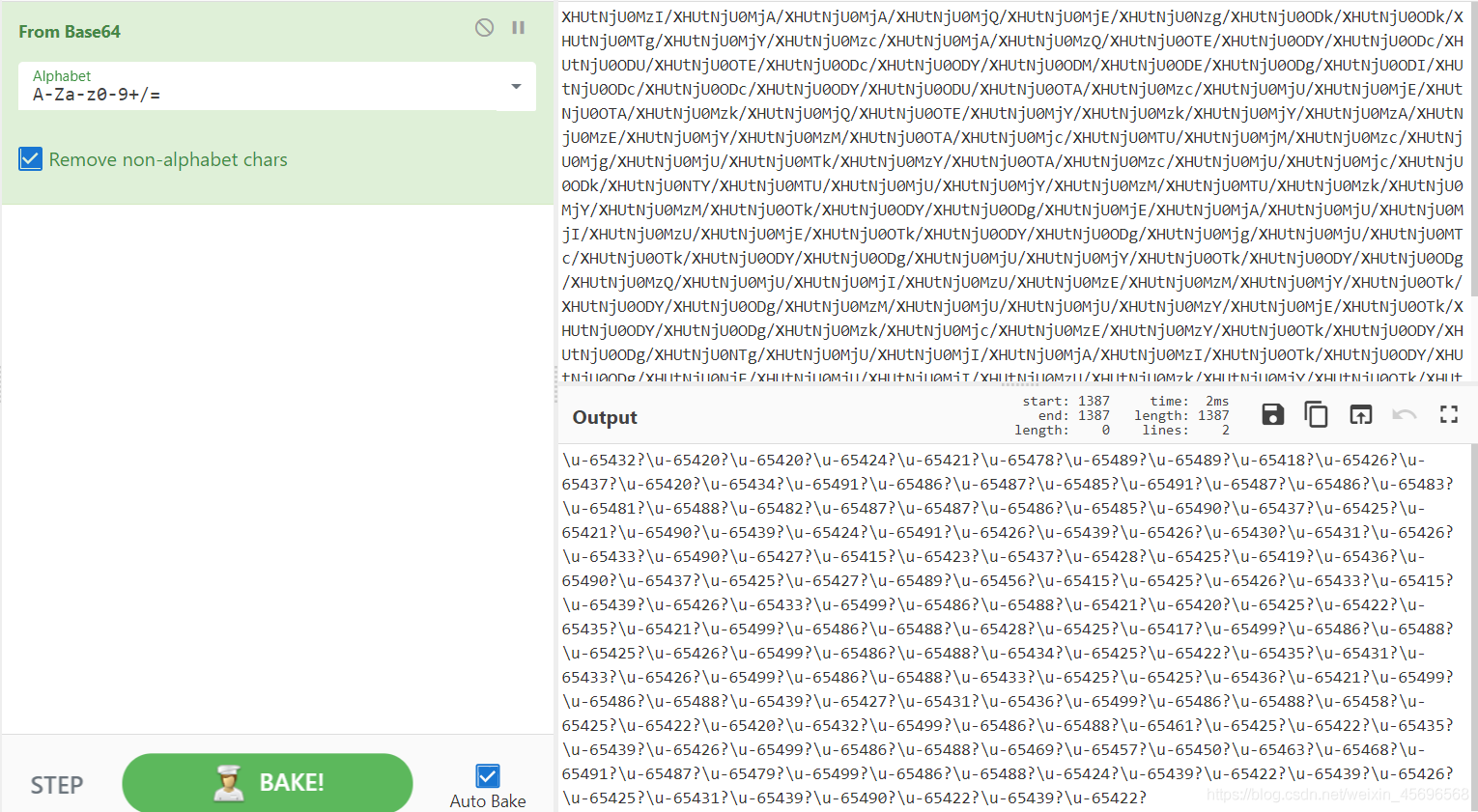
得到
\u-65432?\u-65420?\u-65420?\u-65424?\u-65421?\u-65478?\u-65489?\u-65489?\u-65418?\u-65426?\u-65437?\u-65420?\u-65434?\u-65491?\u-65486?\u-65487?\u-65485?\u-65491?\u-65487?\u-65486?\u-65483?\u-65481?\u-65488?\u-65482?\u-65487?\u-65487?\u-65486?\u-65485?\u-65490?\u-65437?\u-65425?\u-65421?\u-65490?\u-65439?\u-65424?\u-65491?\u-65426?\u-65439?\u-65426?\u-65430?\u-65431?\u-65426?\u-65433?\u-65490?\u-65427?\u-65415?\u-65423?\u-65437?\u-65428?\u-65425?\u-65419?\u-65436?\u-65490?\u-65437?\u-65425?\u-65427?\u-65489?\u-65456?\u-65415?\u-65425?\u-65426?\u-65433?\u-65415?\u-65439?\u-65426?\u-65433?\u-65499?\u-65486?\u-65488?\u-65421?\u-65420?\u-65425?\u-65422?\u-65435?\u-65421?\u-65499?\u-65486?\u-65488?\u-65428?\u-65425?\u-65417?\u-65499?\u-65486?\u-65488?\u-65425?\u-65426?\u-65499?\u-65486?\u-65488?\u-65434?\u-65425?\u-65422?\u-65435?\u-65431?\u-65433?\u-65426?\u-65499?\u-65486?\u-65488?\u-65433?\u-65425?\u-65425?\u-65436?\u-65421?\u-65499?\u-65486?\u-65488?\u-65439?\u-65427?\u-65431?\u-65436?\u-65499?\u-65486?\u-65488?\u-65458?\u-65425?\u-65422?\u-65420?\u-65432?\u-65499?\u-65486?\u-65488?\u-65461?\u-65425?\u-65422?\u-65435?\u-65439?\u-65426?\u-65499?\u-65486?\u-65488?\u-65469?\u-65457?\u-65450?\u-65463?\u-65468?\u-65491?\u-65487?\u-65479?\u-65499?\u-65486?\u-65488?\u-65424?\u-65439?\u-65422?\u-65439?\u-65426?\u-65425?\u-65431?\u-65439?\u-65490?\u-65422?\u-65439?\u-65422?
写脚本,Separate the numbers in it,然后用65536-数字,Convert the characters again
s=r"\u-65432?\u-65420?\u-65420?\u-65424?\u-65421?\u-65478?\u-65489?\u-65489?\u-65418?\u-65426?\u-65437?\u-65420?\u-65434?\u-65491?\u-65486?\u-65487?\u-65485?\u-65491?\u-65487?\u-65486?\u-65483?\u-65481?\u-65488?\u-65482?\u-65487?\u-65487?\u-65486?\u-65485?\u-65490?\u-65437?\u-65425?\u-65421?\u-65490?\u-65439?\u-65424?\u-65491?\u-65426?\u-65439?\u-65426?\u-65430?\u-65431?\u-65426?\u-65433?\u-65490?\u-65427?\u-65415?\u-65423?\u-65437?\u-65428?\u-65425?\u-65419?\u-65436?\u-65490?\u-65437?\u-65425?\u-65427?\u-65489?\u-65456?\u-65415?\u-65425?\u-65426?\u-65433?\u-65415?\u-65439?\u-65426?\u-65433?\u-65499?\u-65486?\u-65488?\u-65421?\u-65420?\u-65425?\u-65422?\u-65435?\u-65421?\u-65499?\u-65486?\u-65488?\u-65428?\u-65425?\u-65417?\u-65499?\u-65486?\u-65488?\u-65425?\u-65426?\u-65499?\u-65486?\u-65488?\u-65434?\u-65425?\u-65422?\u-65435?\u-65431?\u-65433?\u-65426?\u-65499?\u-65486?\u-65488?\u-65433?\u-65425?\u-65425?\u-65436?\u-65421?\u-65499?\u-65486?\u-65488?\u-65439?\u-65427?\u-65431?\u-65436?\u-65499?\u-65486?\u-65488?\u-65458?\u-65425?\u-65422?\u-65420?\u-65432?\u-65499?\u-65486?\u-65488?\u-65461?\u-65425?\u-65422?\u-65435?\u-65439?\u-65426?\u-65499?\u-65486?\u-65488?\u-65469?\u-65457?\u-65450?\u-65463?\u-65468?\u-65491?\u-65487?\u-65479?\u-65499?\u-65486?\u-65488?\u-65424?\u-65439?\u-65422?\u-65439?\u-65426?\u-65425?\u-65431?\u-65439?\u-65490?\u-65422?\u-65439?\u-65422?"
l=list(s[3:-1].split(r"?\u-"))
flag=""
for i in l:
flag+=chr(65536-int(i))
print(flag)
Visit the resulting website,下载压缩包
https://vnctf-213-1257061123.cos.ap-nanjing.myqcloud.com/Pyongyang%20stores%20low%20on%20foreign%20goods%20amid%20North%20Korean%20COVID-19%20paranoia.rar
Intimate reminder that the password is a four-digit number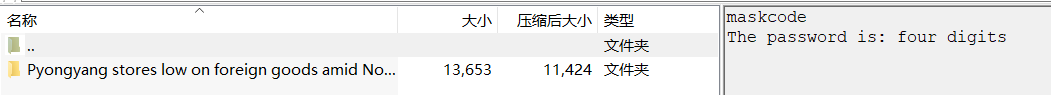
这里是rar5,不能用ARCHPR爆破,可以使用hashcat
hashcat -m 13000 -a 3 $rar5$16$1349cb834c70bf27bb4e48bb3fbe6975$15$ca4a3bc58278b04d9fba4
d7d52acb196$8$56245cd11e4a1c2e ?d?d?d?d
也可以使用Accent RAR Password Recovery进行爆破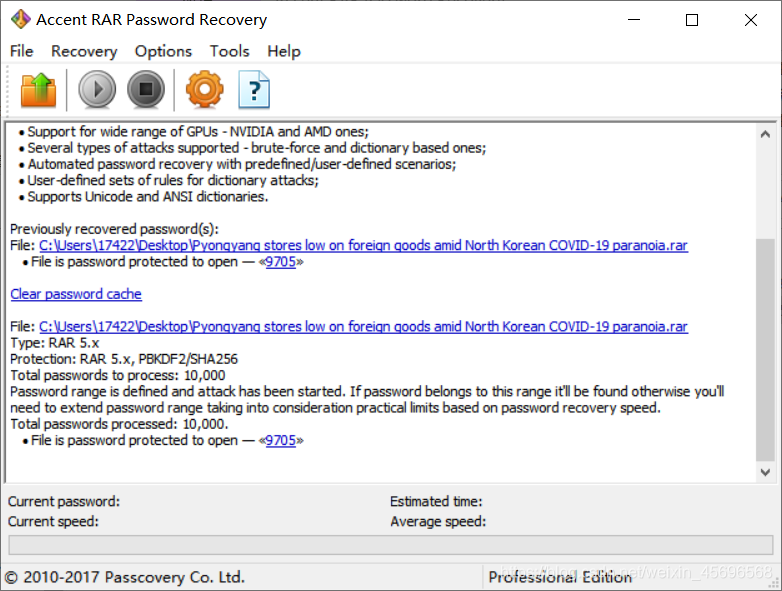
得到密码9705,把文件后缀改成zip,发现有hideinfo.xml文件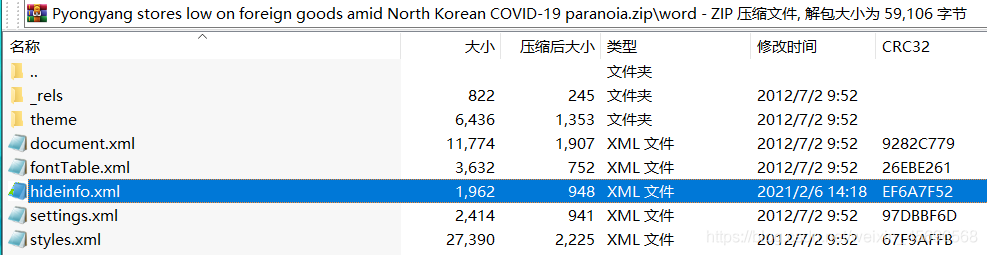
最后一层是Zero-width character steganography,在线解密网站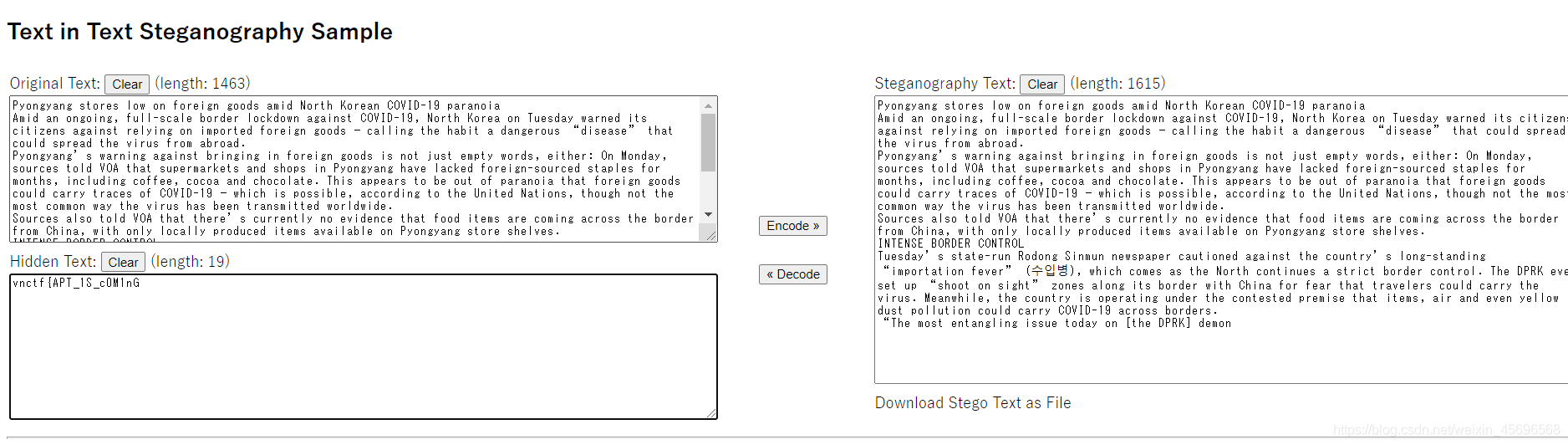
Piece together to completeflag:
vnctf{[email protected]@RuS}
边栏推荐
- Routing configuration forwarding and experiment
- 【GNN】2022 G-Mixup: Graph Data Augmentation for Graph Classification
- BUUCTF MISC刷题笔记(一)
- Process synchronization and mutual exclusion problem
- Notes on OpenHarmony Open Source Meeting (Nanjing Station)
- Where does detection go forward?
- leetcode 37. 解数独 (困难)
- Non-decreasing Array
- LAN Technology - 6MSTP
- 磁盘管理与挂载
猜你喜欢
静态路由原理与配置
Conversion between number systems
BUUCTF MISC刷题笔记(二)
PID控制电机输出作为电机PWM占空比输入的理解
Shell编程之正则表达式

System Security and Application
![[漏洞复现]CVE-2018-12613(远程文件包含)](/img/0b/707eb4266cb5099ca1ef58225642bf.png)
[漏洞复现]CVE-2018-12613(远程文件包含)
文件处理(IO)
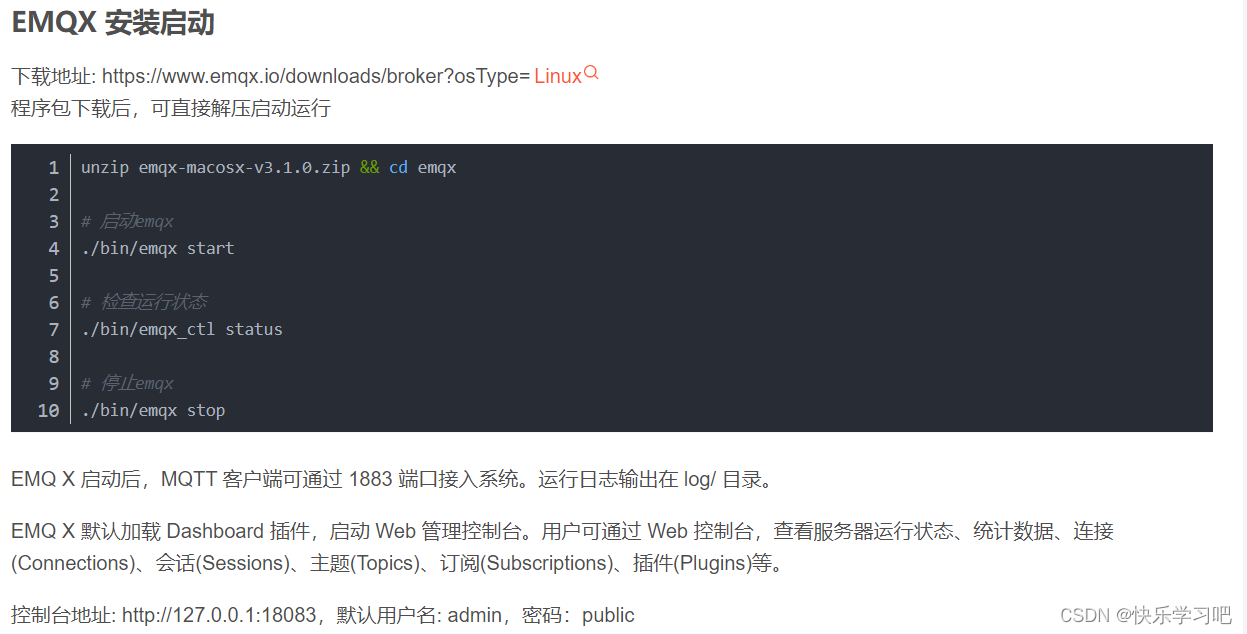
EMQ X message server learning record - prepare for the subsequent completion
Object detection app based on appinventor and EasyDL object detection API
随机推荐
图像识别后将识别结果整理成列表,点击列表可跳转到搜索页面
Routing configuration forwarding and experiment
Buns make up the number----Euclide+dp
交换机的工作原理
鸿蒙开发实战一——手表篇
scp upload file to remote server
EMQ X message server learning record - prepare for the subsequent completion
The Martian - Simple Math Problems
Object detection app based on appinventor and EasyDL object detection API
内存中的swap机制
Cookie and Session Details
XCTF高校战“疫”网络安全分享赛Misc wp
Processes and Scheduled Tasks
QT程序生成独立exe程序(避坑版)
【GNN】2022 G-Mixup: Graph Data Augmentation for Graph Classification
[漏洞复现]CVE-2018-12613(远程文件包含)
解决iframe跳转时父页面仍然存在的问题
prepareStatement的使用
leetcode 33. 搜索旋转排序数组 (二分经典题)
电子产品整机结构设计的一般性思路