当前位置:网站首页>C1 notes [task training chapter I]
C1 notes [task training chapter I]
2022-04-23 17:48:00 【Lazy review, half yuan Jun】
Task training
Computer science
Hexadecimal conversion
Information unit
1、 Unit definition
Storage unit :
The amount of information stored on a computer's hard disk or memory , The minimum unit of measurement is “ position ”(bit, The bit ), A bit represents a binary 0 or 1 The storage space occupied in the computer
Transmission unit :
In computer networks, it is called bandwidth , The unit of broadband transmission rate is bps,bps yes bit per second Abbreviation , Indicates how many bits of information are transmitted per second ( Many people will put here bit Mistaken for Byte, That is, mistaking bits for bytes ),
for example : The unit of bandwidth is 10Mb/s, This actually refers to the transmission per second 10 Megabit , instead of 10 Megabytes of data , So the number of digits needs to be divided by 8 Convert to bytes , That is, transmission per second 1.25 Megabytes , namely 10Mbit/s= 1.25MByte/s
2、 Conversion formula
1 byte (Byte)= 8 position (bit)
1KB(Kilo Byte, kilobytes )= 1024B(Byte)
1MB(Mega Byte, Megabytes )= 1024KB
1GB(Giga Byte, Gigabyte )= 1024MB
1TB(Tera Byte, Terabytes )= 1024GB
1PB(Peta Byte, Petabyte )= 1024TB
1EB(Exa Byte, Ebyte )= 1024PB
1ZB(Zeta Byte, Zebyte )= 1024EB
1YB(Yotta Byte, Yao byte )= 1024ZB
1BB(Bronto Byte, This byte )= 1024YB
1NB(Nona Byte, Nuo byte )= 1024BB
1DB(Dogga Byte, Knife byte )= 1024NB
data verification
1、 Parity check
According to the transmitted binary data and parity bits “1” Check the number of . If, together with the check bit “1” The number of is odd , It's odd check ;
conversely , Even check .

chart 1: Parity principle
Technical characteristics : Simple , Errors can be detected , But there's no way to know exactly what's wrong , It can't be modified , Can only request retransmission .
Applicable scenario : Widely applied , However, it is not suitable for transmission in the environment with more signal noise
Multimedia basic parameters
Multimedia (Multimedia) It refers to the integration of multiple media , Generally include images 、 Forms such as sound and video or a combination of them . The quality of multimedia files can be measured by basic parameters .
1、 Parameters are defined
Bit rate :
Audio and video 、 This indicator can be used in all images , It refers to the number of bits transmitted within a specified time , The unit is bps(bit per second), Higher bit rate , The faster the data is transmitted , The better the playback quality of streaming media ( The clearer the audio and video ), The more bandwidth is required , Bit rate is sometimes confused with bit rate , But the unit of code rate is generally kbps( Thousand bits per second ).
Sampling rate :
Dedicated to audio multimedia , Also known as sampling rate or sampling frequency , It defines the number of samples extracted from continuous signals and composed of discrete signals per second , In Hertz (Hz).
The significance of sampling rate is the sampling frequency when converting analog signal into digital signal , That is, how many points are sampled per unit time , The commonly used sampling rate is 44.1KHz.
Sampling bit depth :
Also known as sampling accuracy , Unit is Bit, Common bit depths are 16Bit and 24Bit, It is actually the number of bits of information in each sampling sample .
2、 Calculation formula
Video bit rate calculation formula (kbps, Thousand bits per second ) = file size (KB, kilobytes )* 8 / Number of seconds
Audio bit rate calculation formula (kbps, Thousand bits per second ) = Sampling rate × Sampling bit depth × The channel number
HTTP
One 、 Mission objectives
- Understand and master HTTP The concept and operation mechanism of the protocol
- understand HTTP Format and function of request header and response header
- Master all kinds of common HTTP The meaning of request method and response status code
- understand Cookie and Session Functions and differences of
Two 、 Mission background
Hypertext transfer protocol (Hyper Text Transfer Protocol,HTTP) It's a simple request - Response protocol , It usually runs on TCP above . It specifies what messages the client can send to the server and what response it can get . This simple model is early Web An important guarantee for the popularization of applications , It can be said that there is no HTTP agreement , Not as colorful as it is today 、 Thriving Internet .
3、 ... and 、 Task content
Use Chrome The browser opens any website , For example, Baidu (https://www.baidu.com), Then right click on the page , Select... From the menu that pops up 「 Check 」 Options .
chart 1: Select... On the web page 「 Check 」 Options
In the developer options interface that appears , choice 「Network」 Options .

chart 2: choice 「Network」 Options
Refresh the page , Click on 「Name」 Any request address in the list , You can see that HTTP The agreement is asking for / Data content and format involved in the response process .

chart 3: see Header head
Focus on HTTP Request headers and response headers (Request Headers and Response Headers)
Contents and functions of .
Write Cookie and Session The difference between ( Write as much as you can ):

HTTPS
HTTPS( The full name is Hyper Text Transfer Protocol over SecureSocket Layer) It's a poncho SSL/TLS The shell HTTP. It's in HTTP Make use of SSL/TLS Establish a secure channel , Encrypted data transmission . It is widely used in security sensitive communication on the Internet , For example, electricity supplier 、 Payment and other applications .
1、 encryption algorithm
Symmetric encryption : Encryption and decryption use the same set of keys , Such as DES、3DES and AES etc.
Asymmetric encryption : Encryption and decryption use different keys , Such as RSA、DSA etc.
Irreversible encryption : After plaintext encryption, it cannot be recovered by decryption , Such as MD5、SHA etc.
2、SSL
Full name Secure Sockets Layer, Secure socket protocol , because HTTP It uses Ming text to transmit data , The transmitted content may be peeped ( Sniffing ) And tampering ,
SSL The emergence of is used to solve the problem of information security , The current version is 3.0.
It is located in TCP/IP Protocol and various application layer protocols , Itself is divided into two layers :
SSL Record agreements (SSL Record Protocol) and SSL handshake protocol (SSL Handshake Protocol).


3、TLS
Full name Transport Layer Security, Transport layer protocol , It's in SSL3.0 Designed on the basis of ,
amount to SSL Subsequent versions , Its goal is to make SSL More secure .

4、 Certificate and certificate chain
After college, I have a diploma , And this certificate can be queried on Xuexin
There are professional annotation meetings 、CCIE、 Lawyer's certificate, etc , It can be found on the website of the national vocational certification authority or entrusted institution
After the company is registered , Business license information can also be found in Tianyan check or enterprise check
Role of certificate
- Proof of past experience
- Third party credit guarantee
- Sole validity test


OSI Seven layer model
One 、 Mission objectives
- understand OSI The role and significance of each layer in the seven layer network model
- understand OSI The protocols involved in each layer of the seven layer network model and their functions
- Understand and be familiar with the complete transmission process of data from sending to receiving
Two 、 Mission background
College students majoring in computer network , Probably all know OSI Seven layer model .OSI The full name is Open System
Interconnection( Open systems interconnection ), It is a well-defined protocol specification . Its greatest significance is to solve the problem of interconnection between different networks , And clearly define the boundaries and responsibilities between different network levels .
3、 ... and 、 Task content !!!!!!!
application layer (Application Layer):
yes OSI The highest level of the reference model , It is user 、 Interface between application and network , It goes directly to user Provide services , Complete all kinds of work for users on the network .
The presentation layer (Presentation Layer):
yes OSI The sixth layer of the reference model , it From the application layer Instructions and data for interpretation , Give meaning to all kinds of grammar , Its main function is to deal with the representation of user information , For example, data coding 、 Data format conversion, encryption and decryption, etc .
The session layer (Session Layer):
yes OSI The fifth layer of the reference model , Its main task is to The presentation layer of two entities Provide methods for establishing and using connections ( The connection of presentation layer between different entities is called session ), Organize and coordinate communication between two session processes , And manage data exchange .
Transport layer (Transport Layer):
yes OSI The fourth layer of the reference model . The main task of this layer is Provide users with Reliable end-to-end error and flow control , Ensure the correct transmission of messages , At the same time, the details of lower data communication are shielded to the upper layer .
The network layer (Network Layer):
yes OSI The third layer of the reference model , It is the most complex layer , It is also the highest layer of communication subnet . It provides services to the upper layer on the basis of the lower two layers . Its main task is through the routing algorithm , Select the most appropriate path for the message or packet . This layer controls the information forwarding between the data link layer and the transmission layer , establish 、 Maintain and terminate network connections .
Data link layer (Data Link Layer):
yes OSI Reference the second layer of the model , It is responsible for Establish and manage links between nodes . At the same time, through various control protocols , Change the physical channel with errors into error free 、 A data link that can reliably transmit data frames .
The physical layer (Physical Layer):
yes OSI The first layer of the reference model , And the bottom . Its main function is Use the transmission medium to provide physical connection for the data link layer , Transparent transmission of bitstream . It makes it unnecessary for the data link layer to consider the specific transmission medium of the network .“ Transparent transmission of bitstreams ” Indicates that the bit stream transmitted by the actual circuit has not changed , For the transmitted bitstream , This circuit seems to be invisible .
.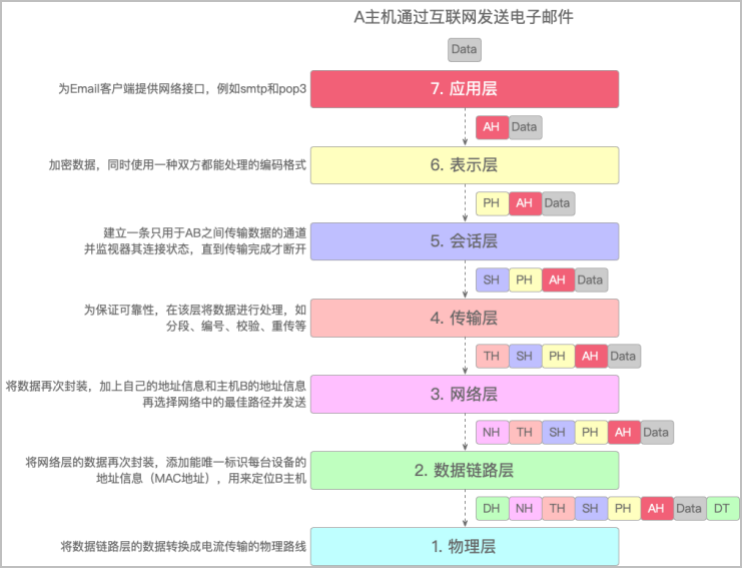
chart 1:A The process of sending e-mail through the Internet

chart 2:B The process of receiving e-mail through the Internet

chart 3:OSI The network protocols involved in each layer
IP Basics
IP yes Internet Protocol( Internet protocol ) Abbreviation , As a whole TCP/IP The core of protocol family ,
It's also the foundation of the Internet , so to speak , As long as the computer exists in the network ,
There must be someone who can find it IP Address .
IP It mainly includes three aspects :IP addressing scheme 、 Packet encapsulation format and packet forwarding rules .
This task involves only IP addressing scheme .
1、IP Address
IP On the network layer , It is used for communication between hosts , Responsible for transmitting communication data between two networks without direct connection , and MAC At the data link layer , The function is to realize the direct communication between two devices

IP Address (IPv4) from 32 Bit binary number means , In the computer, it is processed in binary , In order to facilitate memory, human beings have adopted the marking method of dotted decimal system : Also is to 32 Bit binary IP The address of each 8 Bit is a group. , Will be divided into 4 Group , Between groups “.” separate , Then convert each group into decimal numbers to represent . in other words ,IP The maximum value of the address is 232
= 4294967296

2、IP Address classification
The beginning of the Internet ,IP The address seems abundant , So computer scientists designed classified addresses . They put the IP There are five types of addresses :A、B、C、D、E.

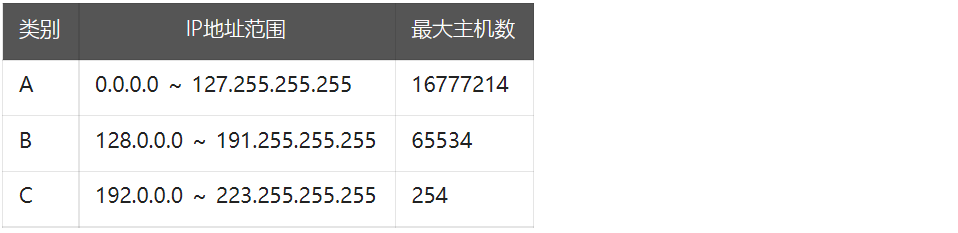
Why have a network number ? Because in addition to the need to locate a specific computer , You also need to locate a network .
Relationship between network number and host number , Just like the relationship between buildings and residents , That is to say 「 network number : Host number == Building No : Resident 」.Maximum number of hosts = 2 The number of digits of the host number - 2, for example C class IP The host number digits of the address are 8, that C class IP The maximum number of hosts for the address = 28 - 2 = 254.
The reason why we want to reduce 2, Because there are two IP It's special , The host numbers are all 1 And the host number are all 0.

3、 No classified address CIDR
No more A、B、C、D、E And so on , But just will 32 Bit IP The address is divided into two parts :
network number + Host number , In the form of :a.b.c.d/x,
among /x Before presentation x Bit belongs to network number , The scope is 0~32. for example 10.100.122.2/24, adopt CIDR You can also get the subnet mask .

4、 Little knowledge
stay A、B、C Of the three types of addresses , Each has a reserved address .
A class :10.0.0.0 ~ 10.255.255.255
B class :172.16.0.0 ~ 172.31.255.255
C class :192.168.0.0 ~ 192.168.255.255
in other words , These three groups of addresses are private network addresses , It doesn't work on the Internet
This machine IP、127.0.0.1 and localhost: You can often see these three different in development IP Address . What's the difference between them ?
This machine IP: To be exact, it is the of the local physical network card IP Address , Its sending and receiving data will be limited by firewall and network card
127.0.0.1: This is a loopback address , It is also a special network interface , Any packet sent from it will not appear in the network , Its sending and receiving data will also be limited by firewalls and network cards
localhost: It's a domain name , It used to point to 127.0.0.1 This IP Address , Now it also points to IPv6 Address :[::1] , Its sending and receiving data will not be limited by firewalls and network cards
IPv6
stay IPv4 The era of birth , It is impossible to predict the prosperity of today's Internet , Therefore, many design problems are gradually exposed in the process of development , For example, the classification is unreasonable , Available public network IP The total number of addresses is too small, etc .
——
In this case , There is IPv6.IPv6 It's English “Internet Protocol Version 6”( Internet Protocol No 6 edition ) Abbreviation , It's the Internet Engineering Task Force (IETF) Designed to replace IPv4 The next generation of IP agreement , The number of addresses is said to be able to make an address for every grain of sand in the world .
3、 ... and 、 Task content
It's divided into hexadecimal notation :
The format is X:X:X:X:X:X:X:X, Every X Represents... In the address 16 Binary bits ( Or hexadecimal number ), for example :ABCD:EF01:2345:6789:ABCD:EF01:2345:6789, In this representation ,X Leading in 0 It can be omitted .
0 Bit compression representation :
If one IPv6 The address contains a long paragraph in the middle 0, You can put a continuous paragraph 0 Compress it into “::”. But this form “::” Only once .
Embedded IPv4 notation :
In order to and IPv4 compatible ,IPv4 The address can be embedded in IPv6 In the address , The address format is :X:X:X:X:X:X:d.d.d.d,
front 96 Bits are represented in bold hexadecimal , And finally 32 Bit uses IPv4 Dot decimal representation of ,
for example :::192.168.0.1.
Network topology
Internet is a broad concept , It generally refers to the collection of computers connected together through the network . therefore , If you only observe the part , For example, the network of a company , Then you can't say that the company's network is “ Internet ” 了 . that , For every company , How is the network composed ? This is the problem to be solved by the network topology . Just as data structures organize data in some form , Network topology refers to the connection of different physical computers in some form .
3、 ... and 、 Task content
Star structure :
It means that all computers are connected into a network in a star mode . The network has a central node , Other nodes ( The workstation 、 The server ) They are all directly connected to the central node , This structure takes the central node as the center , So it's also called centralized network . It has a simple structure 、 Easy to manage 、 Simple control 、 The network delay time is small 、 Low transmission error . But the disadvantages are also obvious : Low reliability 、 Poor resource sharing ability 、 Low line utilization .
chart 1: Star network topology
Bus structure : It means that all workstations and servers are hung on one bus , All workstations are equal , No central node control , It has a simple structure 、 Good scalability 、 Easy to install , But maintenance is difficult .
chart 2: Bus network topology
Ring structure :
Several nodes in the network are connected end to end through communication links to form a closed ring , This structure makes the public transmission cable form a ring , Data is transmitted between nodes in one direction in the loop , Information from one node to another . It has strong real-time performance 、 Transmission control is easy , But maintenance is difficult , Low reliability .
chart 3: Ring network topology
Network structure :
It refers to the point-to-point link connection between each device , This connection is not economical , Use this method only if every site has to send information frequently . Its installation is also complicated , But the system has high reliability , Strong fault tolerance . Sometimes referred to as distributed architecture .
chart 4: Mesh network topology
Tree structure :
This is a hierarchical centralized control network , Compared with star shape , Its total length of communication line is short , Lower cost 、 Nodes are easy to expand 、 Finding a path is convenient , But apart from the leaf nodes and their connected lines , Any node or its connected line failure will affect the system .
chart 5: Tree network topology
Domain name resolution
There are thousands of computers on the Internet , In order to accurately access the services on one of these computers , stay OSI In the network layer of the seven layer model , adopt IP Address to uniquely mark the location of each host in the network ,
such as :39.106.226.142. But these pure numbers IP The address is too hard to remember , Therefore, domain names appear ( such as csdn.net) This is an address symbol convenient for human memory .
This is equivalent to the name of a city in the real world , Such as Wuhan ,IP The address is equivalent to the internal code of the post office , Such as 420000, Domain name resolution is to convert the domain name into IP Address process .
3、 ... and 、 Task content
1、 Domain name rules
English domain names can only be used by 26 English letters 、0~9 Ten numbers and “-” A mixture of hyphens ( except “-” Cannot be the first character ), Spaces and some special characters are not supported , such as !?/;: @ #$%^~_=+,*<> etc. .
English domain names are not case sensitive , It can also be pure English and digital domain name , For Chinese domain names , Must contain Chinese characters .
The number of domain names is from right to left “.” The separated part is determined , There are several “.” Just a few levels , In general , The domain name should not exceed level 5 , for example a.com It's a domain name , and a.b.com Is a secondary domain name .
The length limit of each level of domain name is 63 Characters , The total length of the domain name cannot exceed 253 Characters .
Common top-level domain names are :.biz .com .edu .gov .info .int .mil .name .net .org.
National top-level domain name reference ISO 3166-1 Two letter code generation in , For example, Chinese mainland is .cn, Hong Kong, China is .hk, Taiwan, China .tw, The United States for .us.
Common domain names can be combined with country domain names , Indicate location ( As long as the domain name management organization allows ), for example .gov.cn.
2、 Domain name resolution type
A Record resolution :
A The record is Address Record , It is used to specify the corresponding domain name IP Address , It is usually to point the website service to the server address , For example, the domain name www.csdn.net Point to 39.106.226.142 This IP Address , Is a typical A Record resolution .
CNAME Record resolution :
If the address of the server changes , The light on A The record won't work . And that's where it comes in CNAME, It is also called alias resolution , For example, domain name www.csdn.net, Actual IP The address is 39.106.226.142, Corresponding CNAME May be abc.csdnweb.com, That is, multiple domain names are allowed to correspond to the host name of the server , So even if the server IP Change of address , There is no need to change the resolution record , Domain name resolution will automatically update based on the host name IP Address . If A Analyze and record CNAME Record resolution coexistence , that A Record resolution will take precedence .
MX Record resolution :
That's mail exchange records , This record resolution is used to point the e-mail ending in the domain name to the corresponding e-mail server , For example, the mail used by the user is csdn.net For the end , Then you need to add the name of the domain name in the domain name management MX Record to handle all with @csdn.net Message ending with .
3、 Pan domain name resolution
It refers to resolving a certain type of domain name to the same IP Address , Implemented as a wildcard ,
For example *.csdn.net Pan domain name pointing IP Address 39.106.226.142 when ,
that a.csdn.net、b.csdn.net Wait for all csdn.net The domain name at the end will point to 39.106.226.142 This IP.
Common network commands and ports
1、 Common network commands
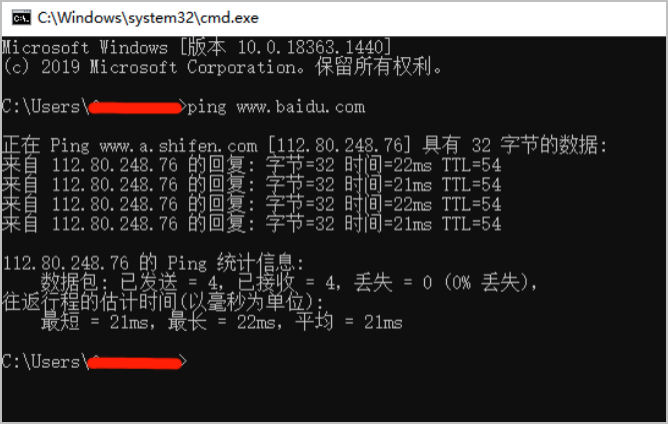
ping command : This is a command used very frequently in development , Mainly used to determine the connectivity of the network , For example, many computers that have just installed the operating system , The first thing is to see if you can connect to the Internet , So often the first command to execute is ping command . Its format is :ping Host name / domain name /IP Address .
Notice that there are spaces !
ipconfig/ifconfig command : When using the option without any parameters ipconfig/ifconfig On command , Displays the... Of each configured interface IP Address 、 Subnet mask and default gateway values . Among them in Windows Is used in ipconfig, And in the Mac or Linux In the system , It uses ifconfig.
netstat command :
Able to display active TCP Connect 、 The port on which the computer listens 、 Ethernet statistics 、IP Routing table 、IPv4 as well as IPv6 Statistics , Through it, we can understand the current state of the network .
2、 Common network ports
TCP And UDP The port range in the segment structure is 0~65535 Between .
The port number is less than 256 Is a common port , Servers are generally identified by common port numbers .
whatever TCP/IP All the services provided are implemented with 0~1023 Port number between .
1024~49151 The port number is the registered port number , It can be freely used by users ,
Also by IANA Designated for special services ,
from 49152~65535 Is a dynamic or private port number ( The above is not mandatory ).

Common sense of data structure
web Basics
Semantic tags
| Elements | explain |
|---|---|
article |
Define independent external documents , Such as news contribution 、 Blog posts 、 Forum posts, etc |
aside |
It is generally used for the sidebar in the web page or the label box inside the article |
header |
The header area of the page , Usually includes websites logo、 Link navigation 、 Search box 、banner |
nav |
The navigation link area of the page |
main |
Define the main content of the document |
section |
Define the area of the document |
footer |
Footer of the document |
mark |
Mark 、 Highlight text |
ul |
Unordered list |
form |
establish HTML Forms |
button |
Define buttons |
i |
Used to represent other text that distinguishes ordinary text , Browsers usually display their contents in italics |
Form labels ( Next )
版权声明
本文为[Lazy review, half yuan Jun]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231744289674.html
边栏推荐
- Read software engineering at Google (15)
- Kubernetes service discovery monitoring endpoints
- SQL optimization for advanced learning of MySQL [insert, primary key, sort, group, page, count]
- Ring back to origin problem - byte jumping high frequency problem
- This point in JS
- 958. Complete binary tree test
- Halo 开源项目学习(二):实体类与数据表
- Write a regular
- PC uses wireless network card to connect to mobile phone hotspot. Why can't you surf the Internet
- In embedded system, must the program code in flash be moved to ram to run?
猜你喜欢
索引:手把手教你索引从零基础到精通使用
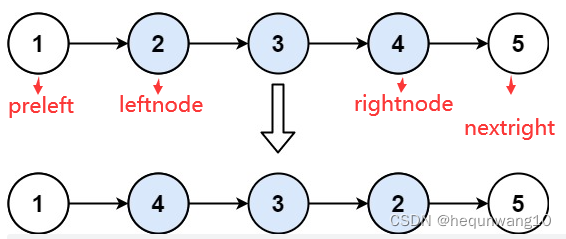
92. Reverse linked list II byte skipping high frequency question
MySQL installation
常用SQL语句总结

JS forms the items with the same name in the array object into the same array according to the name

极致体验,揭晓抖音背后的音视频技术
Compare the performance of query based on the number of paging data that meet the query conditions
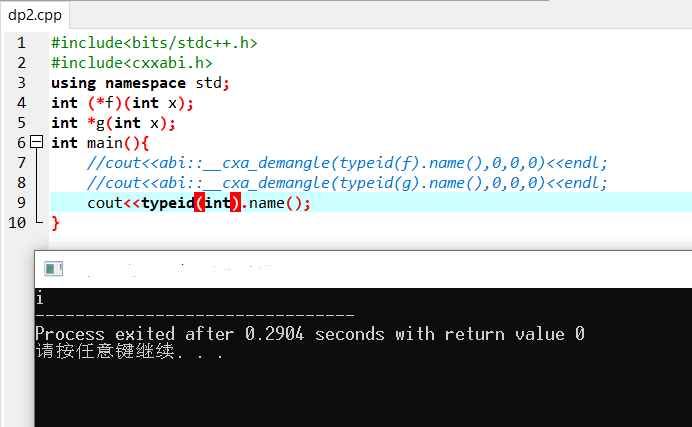
On the method of outputting the complete name of typeID from GCC
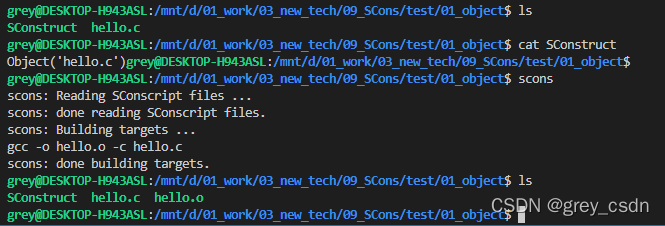
1217_ Generating target files using scons
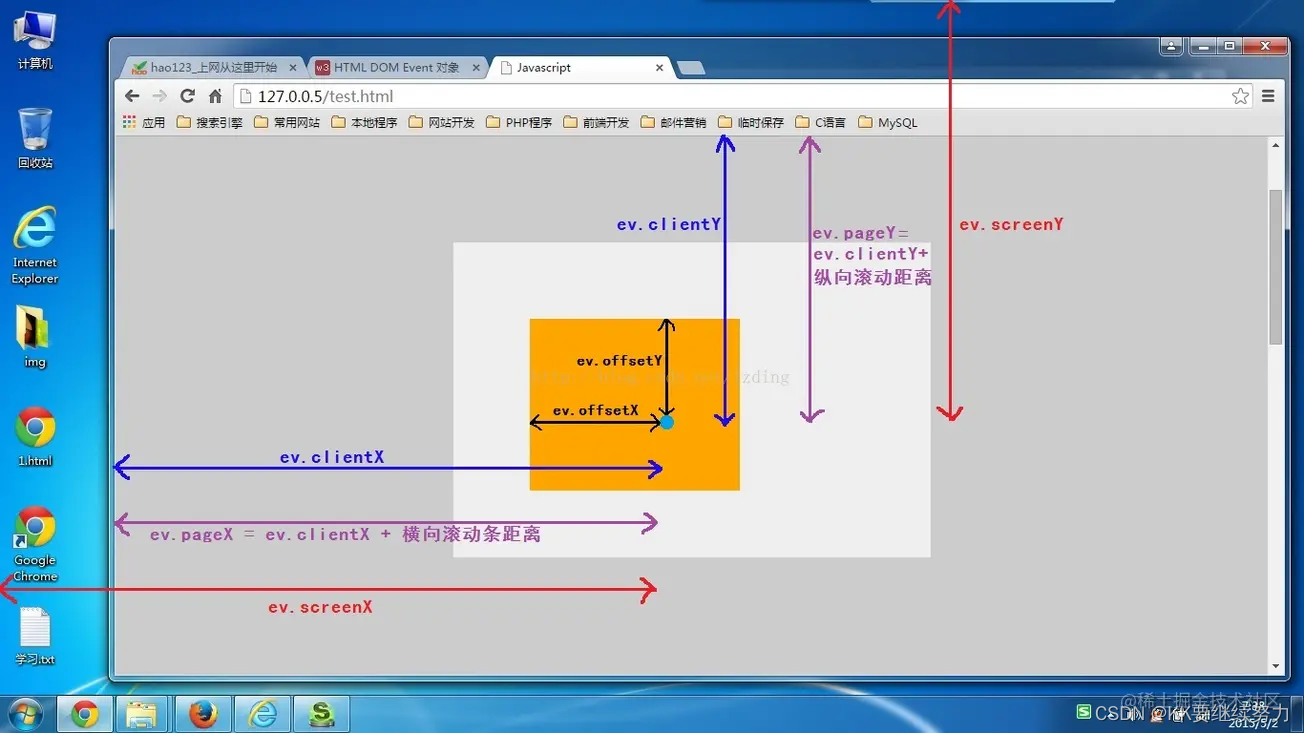
Element calculation distance and event object
随机推荐
Utilisation de la liste - Ajouter, supprimer et modifier la requête
1217_使用SCons生成目标文件
双闭环直流调速系统matlab/simulink仿真
Where is the configuration file of tidb server?
Halo 开源项目学习(二):实体类与数据表
The system cannot be started after AHCI is enabled
122. 买卖股票的最佳时机 II-一次遍历
Allowed latency and side output
EasymodbusTCP之clientexample解析
48. 旋转图像
Index: teach you index from zero basis to proficient use
MySQL进阶学习之SQL优化【插入,主键,排序,分组,分页,计数】
Ring back to origin problem - byte jumping high frequency problem
Tell the truth of TS
Why do some people say SCM is simple and I have to learn it so hard?
386. Dictionary order (medium) - iteration - full arrangement
JS get link? The following parameter name or value, according to the URL? Judge the parameters after
Use of list - addition, deletion, modification and query
2022年上海市安全员C证操作证考试题库及模拟考试
JVM类加载机制