当前位置:网站首页>Daily CISSP certification common mistakes (April 11, 2022)
Daily CISSP certification common mistakes (April 11, 2022)
2022-04-23 18:17:00 【Tang Junfei - Mingxue Online】
CISSP Certification is often wrong ( From Mingxue online test platform :https://www.maxstu.com/page/1773704)
【 The answer is analyzed after the question 】
subject 1
Q:Olivia Choosing a new biometric authentication technology , And is considering buying an iris scanner . Compared with most other types of biometric factors , What are the advantages of iris scanning ?
Olivia is selecting a new biometric authentication technology and is considering purchasing iris scanners. What advantage do iris scans have over most other types of biometric factors?
A、 Iris scanners are more difficult to cheat
Iris scanners are harder to deceive.
B、 The iris changes less than other factors
Irises don't change as much as other factors.
C、 Iris scanners are cheaper than other factors
Iris scanners are cheaper than other factors.
D、 Iris is not easy to copy
Iris scans cannot be easily replicated.
subject 2
Q: At which stage of the accident response process , Administrators design new safety controls to prevent accidents from happening again ?
During which phase of the incident response process would administrators design new security controls intended to prevent a recurrence of the incident?
A、 The report
Reporting
B、 recovery
Recovery
C、 Repair
Remediation
D、 Lessons learned
Lessons learned
subject 3
Q:Bethany Received an email from a colleague , There is an unusual attachment , be known as smime.p7s, She hasn't seen the attachment , I don't know what to do . What is the most likely attachment ?
Bethany received an email from one of her colleagues with an unusual attachment named smime.p7s. She does not recognize the attachment and is unsure what to do. What is the most likely scenario?
A、 This is an encrypted email
This is an encrypted email message.
B、 This is a phishing attack
This is a phishing attack.
C、 This is embedded malware
This is embedded malware.
D、 This is a spoofing attack
This is a spoofing attack.
---------------
There are more free online security certification test questions and wechat learning discussion groups , You can add Mingxue online assistant vx:maxstu_com, Get and join .
---------------
subject 1
answer :B
analysis : Iris scanning has a longer service life than many other types of biometric factors , Because they don't change throughout a person's life ( Unless the eye itself is damaged ). In some cases , Iris scanners can be fooled by high-resolution eye iris images , It is worth noting that , Iris scanners are no cheaper than other scanners .
Iris scans have a longer useful life than many other types of biometric factors because they don't change throughout a person's life span (unless the eye itself is damaged). Iris scanners can be fooled in some cases by high-resolution images of an eye, and iris scanners are not significantly cheaper than other scanners.
subject 2
answer :C
analysis : The repair phase of event handling focuses on root cause analysis , To determine the cause of the accident , And implement new safety controls as needed .
The remediation phase of incident handling focuses on conducting a root-cause analysis to identify the factors contributing to an incident and implementing new security controls, as needed.
subject 3
answer :A
analysis :S/MIME Secure e-mail format use for encrypted e-mail P7S Format . If the recipient does not support S/MIME Mail reader for , The message will display a message named smime.p7s Attachments to .
The S/MIME secure email format uses the P7S format for encrypted email messages.
If the recipient does not have a mail reader that supports S/MIME, the message will appear with an attachment named smime.p7s.
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610264030.html
边栏推荐
- Implement a simple function to calculate the sum of all integers between M ~ n (m < n)
- Robocode Tutorial 4 - robocode's game physics
- Qt读写XML文件(含源码+注释)
- Using transmittablethreadlocal to realize parameter cross thread transmission
- 线上怎么确定期货账户安全的?
- Docker 安装 Redis
- 硬核解析Promise对象(这七个必会的常用API和七个关键问题你都了解吗?)
- From source code to executable file
- Notepad + + replaces tabs with spaces
- How to install jsonpath package
猜你喜欢
WiFi ap6212 driver transplantation and debugging analysis technical notes
Docker installation MySQL
JD-FreeFuck 京東薅羊毛控制面板 後臺命令執行漏洞
【ACM】70. 爬楼梯
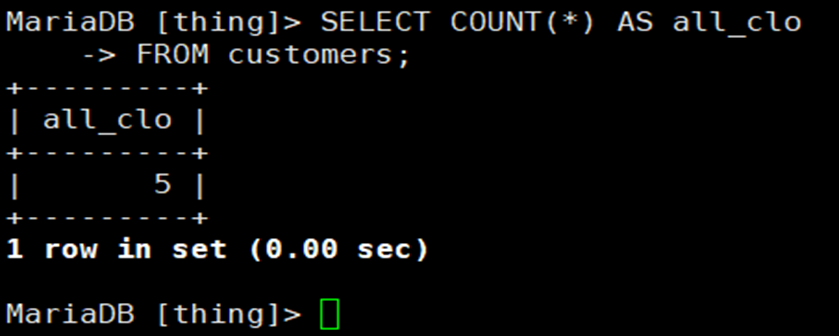
MySQL_ 01_ Simple data retrieval
Scikit learn sklearn 0.18 official document Chinese version
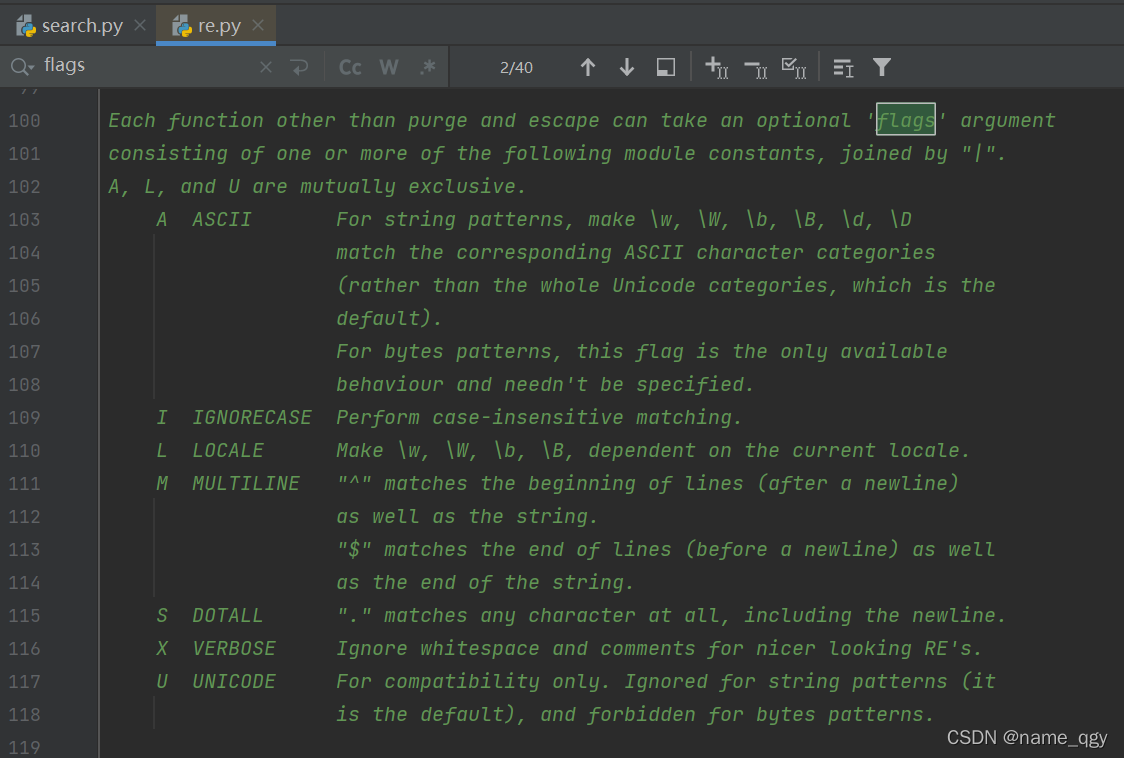
re正則錶達式
Qt读写XML文件(含源码+注释)

【ACM】70. climb stairs
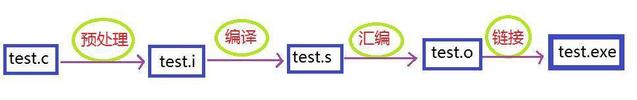
From source code to executable file
随机推荐
mysql自动启动设置用Systemctl start mysqld启动
SQL database syntax learning notes
Robocode tutorial 3 - Robo machine analysis
C medium? This form of
Log4j2 cross thread print traceid
Solving the problem of displaying too many unique values in ArcGIS partition statistics failed
Selenium + webdriver + chrome realize Baidu to search for pictures
Quantexa CDI(场景决策智能)Syneo平台介绍
Svn simple operation command
re正则表达式
Crawling mobile game website game details and comments (MQ + multithreading)
Stanford machine learning course summary
Solution to Chinese garbled code after reg file is imported into the registry
Crawl the product data of Xiaomi Youpin app
The vivado project corresponding to the board is generated by TCL script
Nodejs installation
Crawler for querying nicknames and avatars based on qqwebapi
登录和发布文章功能测试
Multi thread crawling Marco Polo network supplier data
ArcGIS table to excel exceeds the upper limit, conversion failed
