当前位置:网站首页>[CF 1425d] danger of mad snakes
[CF 1425d] danger of mad snakes
2022-04-23 09:43:00 【Zimba_】
The question :
There is one 1000 × 1000 1000\times 1000 1000×1000 Of the lattice . Yes n n n The snake is in the square , Each snake tells you the coordinates in the grid ( X i , Y i ) (X_{i},Y_{i}) (Xi,Yi) And a weight B i B_{i} Bi.
Then choose any of them m m m A snake , For each selected snake , It and all satisfaction m a x ( ∣ X ′ − X ∣ , ∣ Y ′ − Y ∣ ) < = R max(|X'-X|,|Y'-Y|)<=R max(∣X′−X∣,∣Y′−Y∣)<=R Located at ( X ′ , Y ′ ) (X',Y') (X′,Y′) All snakes will be killed .
For one of the options , Its weight is the square of the sum of the weights of all snakes killed in the selection .
Find the sum of the weights of all the selected methods .
Ideas :
Consider the square of the sum of weights ( B i + B j + B k ) 2 (B_{i}+B_{j}+B_{k})^{2} (Bi+Bj+Bk)2, Let's take the square form apart and turn it into B i 2 + B j 2 + B k 2 + 2 B i B j + 2 B i B k + 2 B j B k B_{i}^{2}+B_{j}^{2}+B_{k}^{2}+2B_{i}B_{j}+2B_{i}B_{k}+2B_{j}B_{k} Bi2+Bj2+Bk2+2BiBj+2BiBk+2BjBk.
Consider calculating a single square term B i 2 B_{i}^{2} Bi2 The contribution of , The total number of times each snake is selected × B i 2 \times B_{i}^{2} ×Bi2.
Let's calculate Total cases − - − The number of cases not selected That's it .
Consider calculating the multiplication of two terms 2 B i B j 2B_{i}B_{j} 2BiBj The contribution of , Is the number of times both snakes are selected × 2 B i B j \times 2B_{i}B_{j} ×2BiBj.
Let's excuse this , Calculation The number of cases where neither is selected + i i i Number of cases selected + j j j Number of cases selected - The total number of cases That's it .
Code :
#include <bits/stdc++.h>
using namespace std;
typedef long long ll;
const ll mod = 1000000007;
ll fpow(ll a,ll n)
{
ll sum=1,base=a%mod;
while(n!=0)
{
if(n%2)sum=sum*base%mod;
base=base*base%mod;
n/=2;
}
return sum;
}
ll inv(ll a)
{
return fpow(a,mod-2);
}
ll jie[1000005],rjie[1000005];
void initJie(ll n)
{
jie[0]=1;
for(ll i=1;i<=n;i++)jie[i]=jie[i-1]*i%mod;
for(ll i=0;i<=n;i++)rjie[i]=inv(jie[i]);
}
ll C(ll n,ll k)
{
if(k>n)return 0;
else return jie[n]*rjie[k]%mod*rjie[n-k]%mod;
}
ll n,m,r;
ll x[2005],y[2005],b[2005];
bitset<2005>num[2005],tmp;
ll get1(ll i)
{
return (b[i]*b[i]%mod*(C(n,m)-C(n-num[i].count(),m))%mod+mod)%mod;
}
ll get2(ll i,ll j)
{
tmp=num[i]|num[j];
return 2*b[i]*b[j]%mod*(C(n-tmp.count(),m)+(C(n,m)-C(n-num[i].count(),m))-C(n-num[j].count(),m))%mod;
}
int main()
{
initJie(100000);
scanf("%lld%lld%lld",&n,&m,&r);
for(ll i=1;i<=n;i++)
{
scanf("%lld%lld%lld",&x[i],&y[i],&b[i]);
}
for(ll i=1;i<=n;i++)
{
for(ll j=1;j<=n;j++)
{
if(max(abs(x[j]-x[i]),abs(y[j]-y[i]))<=r)
{
num[i].set(j);
}
}
}
ll ans=0;
for(ll i=1;i<=n;i++)
{
ans=(ans+get1(i))%mod;
}
for(ll i=1;i<=n;i++)
{
for(ll j=i+1;j<=n;j++)
{
ans=(ans+get2(i,j))%mod;
}
}
printf("%lld\n",(ans%mod+mod)%mod);
return 0;
}
版权声明
本文为[Zimba_]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230621424809.html
边栏推荐
- High paid programmer & interview question series 91 limit 20000 loading is very slow. How to solve it? How to locate slow SQL?
- 理解作用域
- JS DOM learn three ways to create elements
- Go language learning notes - array | go language from scratch
- kernel-pwn学习(4)--Double Fetch&&0CTF2018-baby
- Chapter VIII project stakeholder management of information system project manager summary
- Practice of Flink streaming batch integration in Xiaomi
- 重载、重写、隐藏的对比
- SQL used query statements
- 个人主页软件Fenrus
猜你喜欢

防疫登记小程序
![Buuctf [actf2020 freshman competition] include1](/img/47/b8f46037f7e9476b8e01e8d6a7857a.png)
Buuctf [actf2020 freshman competition] include1

Number of islands

Pre parsing of JS

SAP ECC connecting SAP pi system configuration

JS DOM event

Set the maximum width of the body, but why does the background color of the body cover the whole page?

SAP salv14 background output salv data can directly save files and send emails (with sorting, hyperlink and filtering format)
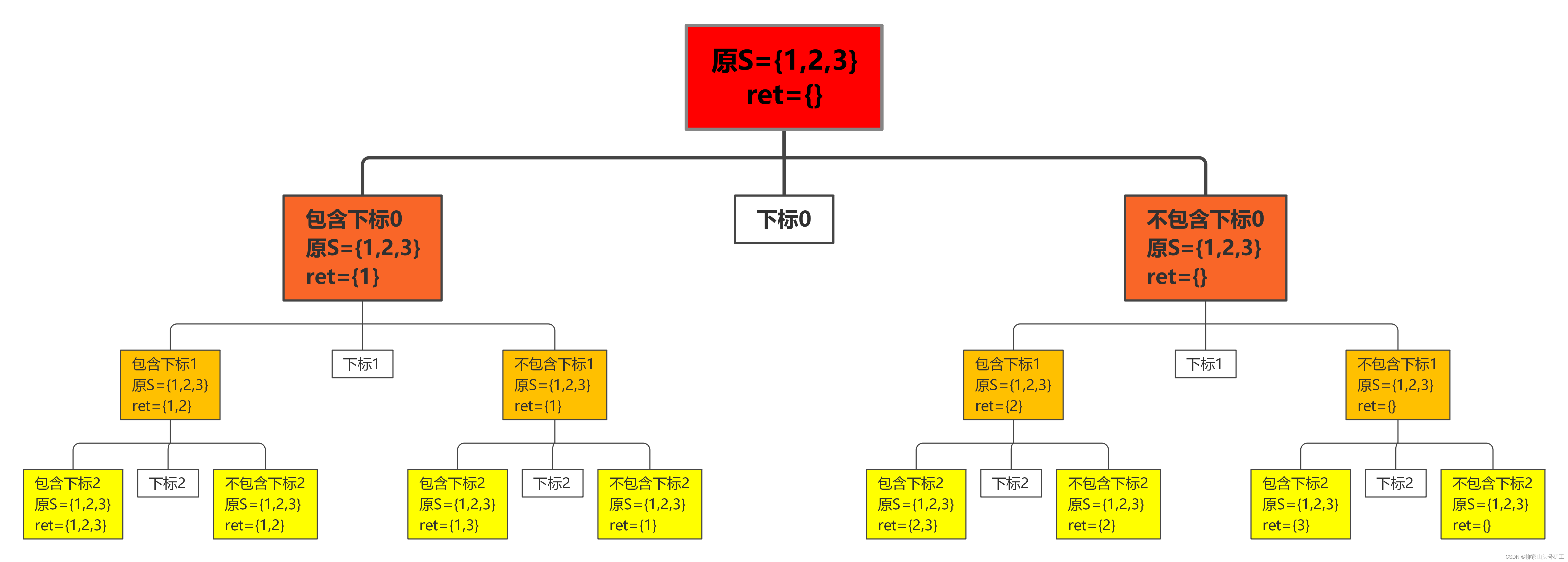
Leetcode question bank 78 Subset (recursive C implementation)

Alibaba cloud architects interpret the four mainstream game architectures
随机推荐
The sap export excel file opens and shows that the file format and extension of "XXX" do not match. The file may be damaged or unsafe. Do not open it unless you trust its source. Do you still want to
Exclusive thoughts and cases of JS
SAP salv14 background output salv data can directly save files and send emails (with sorting, hyperlink and filtering format)
Simple understanding of arguments in JS
Integral function and Dirichlet convolution
MySQL of database -- overview and installation
SQL used query statements
kernel-pwn学习(3)--ret2user&&kernel ROP&&QWB2018-core
如何实现根据照片获取地理位置及如何防御照片泄漏地理位置
Educational Codeforces Round 81 (Rated for Div. 2)
AI上推荐 之 MMOE(多任务yyds)
Number of islands
Sql1 [geek challenge 2019]
653. Sum of two IV - input BST
Your guide to lowering your cholesterol with TLC (continuously updated)
Go language learning notes - structure | go language from scratch
论文阅读《Integrity Monitoring Techniques for Vision Navigation Systems》
成功的DevOps Leader 应该清楚的3个挑战
Leetcode question bank 78 Subset (recursive C implementation)
Kettle experiment