当前位置:网站首页>Daily CISSP certification common mistakes (April 14, 2022)
Daily CISSP certification common mistakes (April 14, 2022)
2022-04-23 18:18:00 【Tang Junfei - Mingxue Online】
CISSP Certification is often wrong ( From Mingxue online test platform :https://www.maxstu.com/page/1773704)
【 The answer is analyzed after the question 】
subject 1
Q:Melissa Be responsible for the safety compliance work of its organization , And was told that the organization would not install the patch until one month after it was released Windows Patch , Unless there are zero day vulnerabilities being actively exploited . Why do companies delay patching like this ?
Melissa is in charge of her organization’s security compliance efforts and has been told that the organization does not install Windows patches until a month has passed since the patch has been released unless there is a zero-day exploit that is being actively exploited. Why would the company delay patching like this?
A、 In order to minimize the impact of installation on the business
To minimize business impact of the installation
B、 To identify any defects in the patch
To allow any flaws with the patch to be identified
C、 In order to prevent malware in the patch from being installed before it is identified
To prevent malware in the patches from being installed before it is identified
D、 In order to distribute the patch to all systems
To allow the patch to be distributed to all systems
subject 2
Q:Fred Our company wants to ensure the integrity of e-mail sent through its central e-mail server . If the confidentiality of the message is not important ,Fred What solutions should be suggested ?
Fred's company wants to ensure the integrity of email messages sent via its central email servers. If the confidentiality of the messages is not critical, what solution should Fred suggest?
A、 Digitally sign and encrypt all messages , To ensure integrity
Digitally sign and encrypt all messages to ensure integrity.
B、 digital signature , But don't encrypt all messages
Digitally sign but don’t encrypt all messages.
C、 Use TLS Protect message , Ensure its integrity
Use TLS to protect messages, ensuring their integrity.
D、 Provide a hash in each message using a hash algorithm , To prove that it hasn't changed
Use a hashing algorithm to provide a hash in each message to prove that it hasn't changed.
subject 3
Q: service ticket (ST) stay Kerberos What is the role of authentication ?
What does a service ticket (ST) provide in Kerberos authentication?
A、 It acts as the authentication host
It serves as the authentication host.
B、 It can prove that the subject's access to the object is legal
It provides proof that the subject is authorized to access an object.
C、 It can prove that the subject has passed KDC Authentication , The subject can request a ticket to access a specific object
It provides proof that a subject has authenticated through a KDC and can request tickets to access other objects.
D、 It provides ticket granting Services
It provides ticket granting services.
---------------
There are more free online security certification test questions and wechat learning discussion groups , You can add Mingxue online assistant vx:maxstu_com, Get and join .
---------------
subject 1
answer :B
analysis : Many organizations delay the patch for a period of time , To ensure that any previously unrecognized defects are found before the patch is installed throughout the organization . Melissa She needs to balance business impact and security in her role , And according to the organization's risk tolerance and safety needs , Choose to support or promote more aggressive installation practices .
Many organizations delay patches for a period of time to ensure that any previously unidentified flaws are found before the patches are installed throughout their organization. Melissa needs to balance business impact against security in her role and may choose to support this or to push for more aggressive installation practices depending on the organization’s risk tolerance and security needs.
subject 2
answer :B
analysis :Fred Your company needs to protect integrity , This can be achieved by digitally signing messages . Any changes will invalidate the signature . Encryption is not required , Because the company doesn't want to protect confidentiality .TLS Can provide transmission protection , But it will not protect the integrity of the message ; Of course , If it cannot be verified that the hash value has not changed , Hash values also do not guarantee integrity .
Fred's company needs to protect integrity, which can be accomplished by digitally signing messages. Any change will cause the signature to be invalid. Encrypting isn't necessary because the company does not want to protect confidentiality. TLS can provide in-transit protection but won't protect integrity of the messages, and of course a hash used without a way to verify that the hash wasn't changed won't ensure integrity either.
subject 3
answer :B
analysis :Kerberos The service ticket in authentication proves that the subject is authorized to access the object . The ticket granting service is provided by TGS Provided .TGT The grant ticket provides proof that the subject has been authenticated , And authorize requests for access to other objects . Authentication host is a fabricated term .
The service ticket in Kerberos authentication provides proof that a subject is authorized to access an object. Ticket granting services are provided by the TGS. Proof that a subject has authenticated and can request tickets to other objects uses ticket-granting tickets, and authentication host is a made-up term.
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610263651.html
边栏推荐
- Log4j2 cross thread print traceid
- 多功能工具箱微信小程序源码
- Multi thread safe reference arc of rust
- Rewrite four functions such as StrCmp in C language
- Hard core parsing promise object (do you know these seven common APIs and seven key questions?)
- Crawl the product data of cicada mother data platform
- Install pyshp Library
- Serial port debugging tools cutecom and minicom
- positioner
- Nodejs安装
猜你喜欢
Install pyshp Library
QT add external font ttf
Docker 安装 MySQL
Hard core parsing promise object (do you know these seven common APIs and seven key questions?)

Jeecg boot microservice architecture

powerdesigner各种字体设置;preview字体设置;sql字体设置
Analysez l'objet promise avec le noyau dur (Connaissez - vous les sept API communes obligatoires et les sept questions clés?)
函数递归以及趣味问题的解决
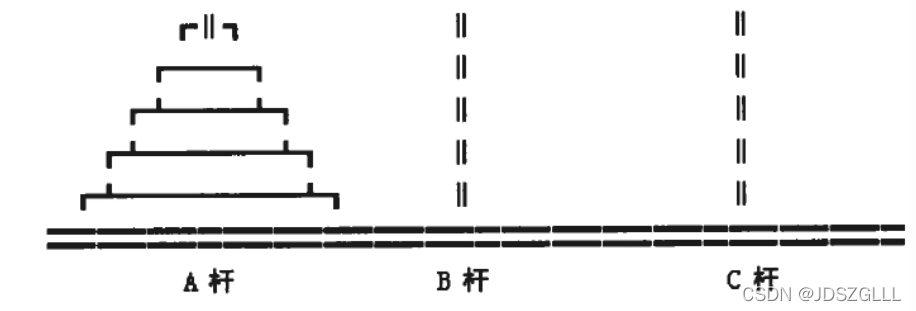
由tcl脚本生成板子对应的vivado工程
Qt读写XML文件(含源码+注释)
随机推荐
Installation du docker redis
【ACM】509. 斐波那契数(dp五部曲)
Software test summary
SSD硬盘SATA接口和M.2接口区别(详细)总结
re正則錶達式
Stm32mp157 wm8960 audio driver debugging notes
Generate verification code
How to restore MySQL database after win10 system is reinstalled (mysql-8.0.26-winx64. Zip)
Quantexa CDI(场景决策智能)Syneo平台介绍
Map basemap Library
Selenium + webdriver + chrome realize Baidu to search for pictures
Box pointer of rust
串口调试工具cutecom和minicom
Mysql database backup command -- mysqldump
Deep learning classic network analysis and target detection (I): r-cnn
A few lines of code teach you to crawl lol skin pictures
Solving the problem of displaying too many unique values in ArcGIS partition statistics failed
【ACM】70. 爬楼梯
How to install jsonpath package
Crawl the product data of cicada mother data platform