当前位置:网站首页>virtual address space
virtual address space
2022-08-10 22:30:00 【dry rice white】
In the early days when there was no virtual memory, the memory was divided directly for the program in memory.This will cause some problems
The process address space is not isolated: Since the program directly accesses the memory, in the case of multiple processes, some malicious programs can modify the data of other programs at will, which is obviously unwillingsaw.Even some non-malicious programs may cause data changes in other programs when used inappropriately. We hope that the error of removing the program will not affect other programs.
Low memory usage efficiency: For example, the memory size is 128MB, and our A program and B program have already occupied 110MB. At this time, the C program with a size of 20MB needs to run, and there is free space in the memory at this time.If it is not enough, then part of the data of the memory occupied in the program in use will be copied to the disk for storage, and enough space will be moved out for the C program.This involves copying in and out of a large amount of data, which greatly affects efficiency
The address where the program runs is uncertain: At this time, the memory of C is likely to be randomly allocated (A and B are not mentioned here), so the running address of C is uncertain.
To solve this problem?
Proposes the idea of an intermediate isolation, that is to say, adding an intermediate layer indirectly to solve the access to the physical address.According to this method, the memory address accessed in the program is no longer an actual physical memory address, but a virtual address.How to implement it, map it through MMU (map f(x)=y).For each process, we only need to consider its own corresponding virtual address, the operating system can automatically help us correspond to the corresponding physical address, the operating system completes the mapping relationship, maps different programs in different areas, and realizes the processAddress space isolation.
Subsection
People think of doing a one-to-one mapping between the virtual address space and the physical address space.The operating system ensures that the address spaces of different processes are mapped to different regions in the physical address space, so that address isolation can be formed.
Assume there are two processes A and B, the memory required by process A is 10M, and its virtual address space is distributed from 0x00000000 to 0x00A00000, and the memory required by process B is 100M, and its virtual address space is distributed from 0x00000000 to 0x06400000.Then, according to the segmentation mapping method, the mapping area of process A in physical memory is 0x00100000 to 0x00B00000, and the mapping area of process B in physical memory is 0x00C00000 to 0x07000000.Therefore, process A and process B are respectively mapped to different memory ranges, which do not overlap with each other, realizing address isolation.
(Brief understanding: Segmentation completes segmentation of physical memory according to the virtual address space of the process to ensure that different physical memory segments correspond to different processes, and we operate in the virtual address space in the program, and eachThe physical segment mapped by the virtual address space of the process is fixed, so there is no need to worry about modifying the data of other programs)
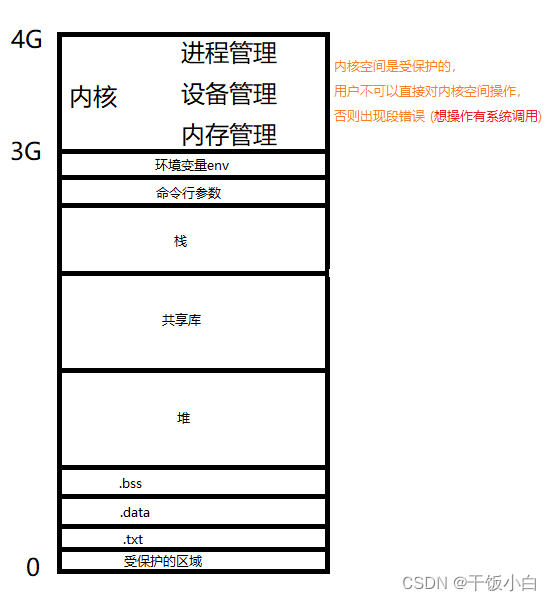
Note: In the virtual address space of each application, the starting address starts at 0, so As if each application is exclusive all memory space.In fact, not in physical memory, physical memory is segmented

Pagination
In the segmented method, the program is always loaded into memory every time the program is run, while the paging method is different.The idea of paging is that the program allocate memory for which page is used when it is running, and the unused pages are temporarily kept on the hard disk.superior.When these pages are used, memory is allocated for these pages in the physical address space, and then establishes the link between the pages in the virtual address space and the physical memory pages just allocated.map.
A executable file (PE file) is actually a collection of compiled and linked data and instructions. It will also be divided into many pages and executed in the PE file.During the process, the unit it loads into memory is the page.When a PE file is executed, the operating system first creates a 4GB process virtual address space for the program.
To create a 4GB virtual address space is not really to create a space, just to create the data structure required by that kind of mapping mechanism,This data structure is page headings and page tables.
The core idea of the paging method is to allocate a memory page y for the xth page when the executable file is executed to the xth page, and then add this memory page to the process virtual address space Mapping table, this mapping table is equivalent to a y=f(x) function.The application can access the y page associated with the x page through this mapping table.
The source of 4G
We all say that the size of the virtual address space is 0~4G, why is it 0~4G?Because the length of the pointer is 4 under the 32-bit platform, the addressing range of the pointer: 0x00000000-0xFFFFFFFF is exactly 0~4G capacity.
Details about virtual address space
Stack model, solver loading memory
Every program running in Linux is allocated a virtual address space by the operating system.
I've already said this, I don't want to say it
边栏推荐
猜你喜欢
H3C S5130 IRF做堆叠
What is Jmeter? What are the principle steps used by Jmeter?
链表中的节点每k个一组翻转
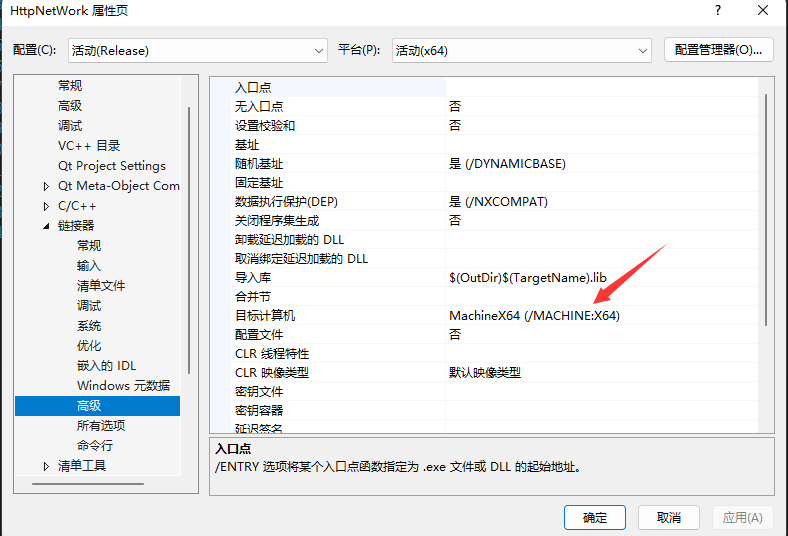
QT笔记——用VS + qt 生成dll 和 调用生成的dll

解码2022中国网安强星丨正向建、反向查,华为构建数字化时代的网络安全防线
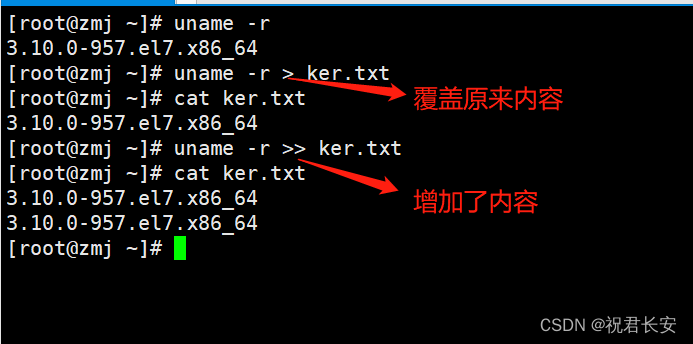
Shell编程规范与变量
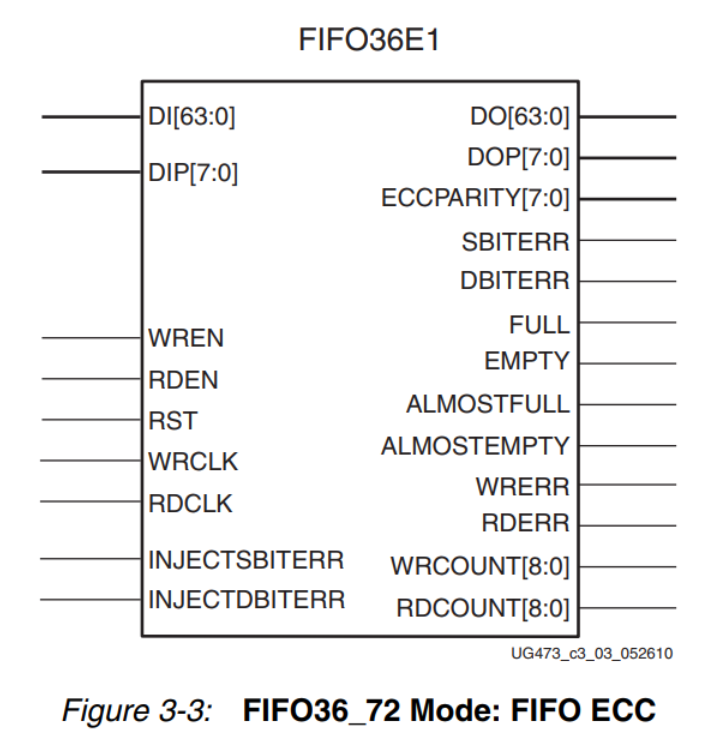
FPGA - 7系列 FPGA内部结构之Memory Resources -03- 内置纠错功能
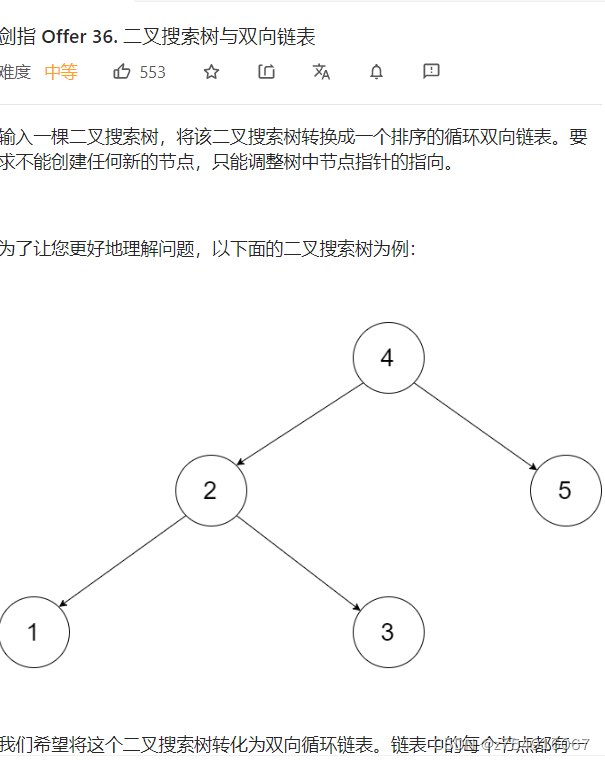
LeetCode-36-Binary search tree and doubly linked list
shell脚本循环语句for、while语句

2022年8月的10篇论文推荐
随机推荐
《DevOps围炉夜话》- Pilot - CNCF开源DevOps项目DevStream简介 - feat. PMC成员胡涛
黑猫带你学Makefile第12篇:常见Makefile问题汇总
VLAN huawei 三种模式
xshell (sed command)
FPGA - Memory Resources of 7 Series FPGA Internal Structure -03- Built-in Error Correction Function
Service - DHCP principle and configuration
web逆向之丁香园
基于交流潮流的电力系统多元件N-k故障模型研究(Matlab代码实现)【电力系统故障】
自组织是管理者和成员的双向奔赴
BM7 链表中环的入口结点
Shell programming specification and variables
接口测试的概念、目的、流程、测试方法有哪些?
美味的石井饭
云服务器基于 SSH 协议实现免密登录
今日睡眠质量记录75分
QT笔记——vs + qt 创建一个带界面的 dll 和 调用带界面的dll
Shell编程之条件语句(二)
c语言之 练习题1 大贤者福尔:魔法数,神奇的等式
These must-know JVM knowledge, I have sorted it out with a mind map
ThreadLocal comprehensive analysis (1)