当前位置:网站首页>Network Security - nmap
Network Security - nmap
2022-08-11 11:30:00 【Make money to marry, sweet,】
一、什么是nmap(安装包下载地址:Download the Free Nmap Security Scanner for Linux/Mac/Windows)
1、是Linux下一款开源免费的网络发现和安全审计工具
2、Nmap的家族成员:
Zenmap:nmap的图形界面版
Ncat:基于netcat,并扩展了一些功能,如ncat链、SSL支持、二进制等
Ncrack:Test the deployed authentication system and password strength,支持常用协议
Ndiff:Used for network baseline testing,对比nmapDifferences in scan results
Nping:Allows the integration of self-constructed packets into the scanning process,and manipulate the raw data
3、nmap的功能:
基本功能:主机发现、端口扫描、应用程序与版本信息侦测、操作系统侦测
附加功能:规避FW/IDS、NSEScript customization and usage
4、命令格式

二、基本操作
实验工具:一台kali(IP:192.168.29.129) 一台win7(IP:192.168.29.131)
1、默认扫描
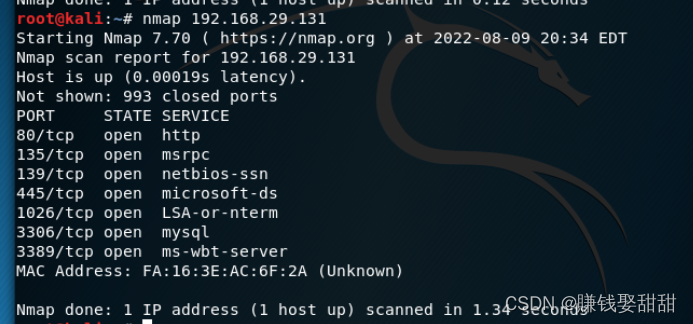
2、全面扫描:
三、主机发现
1、

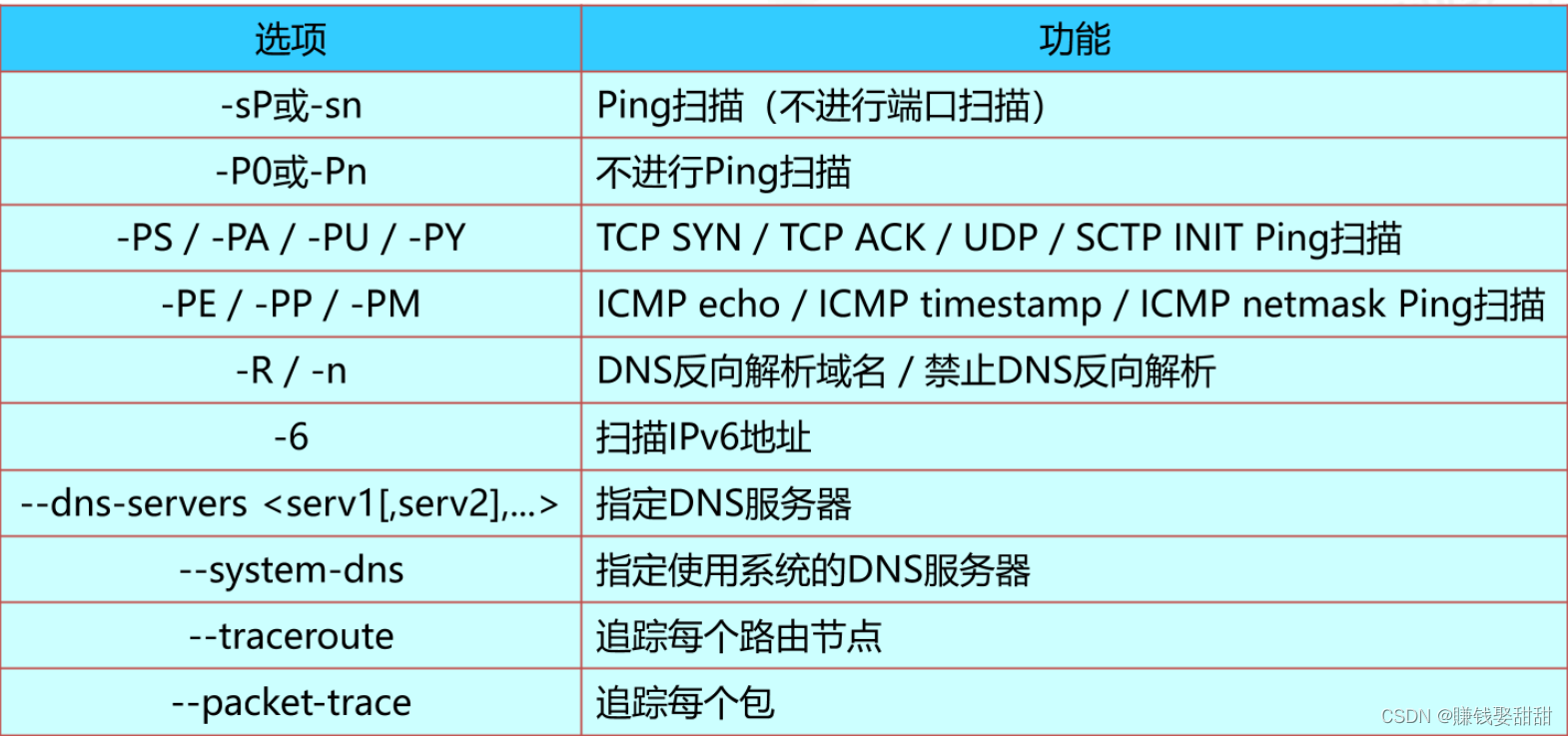
2、Related command options
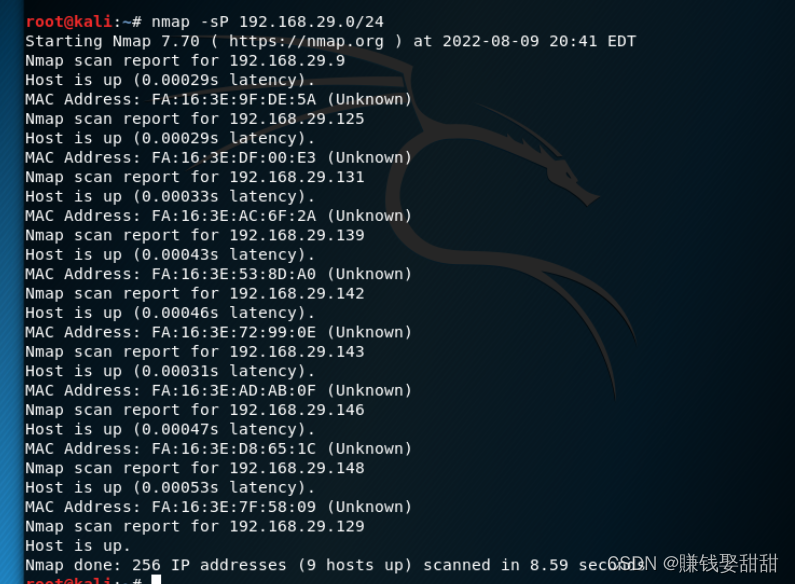
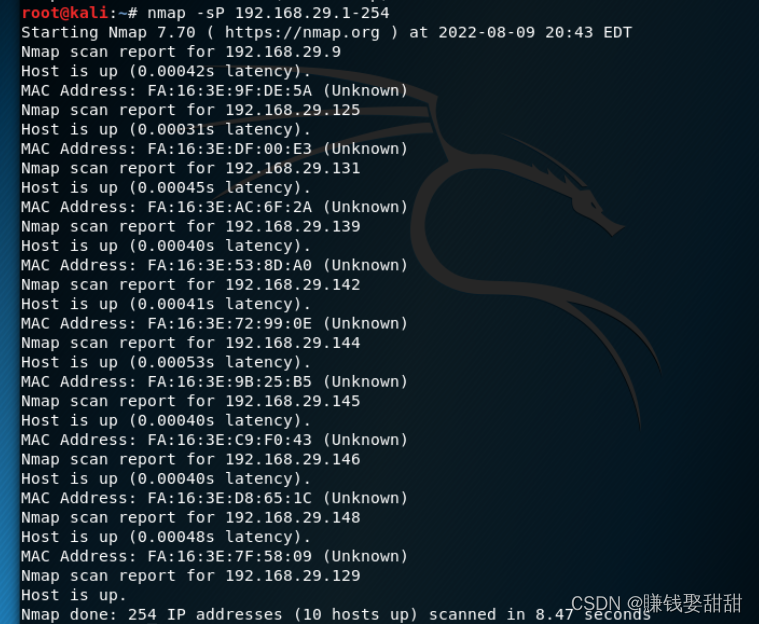
3、Host discovery in the LAN
命令:nmap -sP 192.168.29.0/24 或者 nmap -sP 192.168.29.1-254
在局域网内,Whichever option is used,Nmap都是采用ARP包来询问IP地址上的主机是否活动的,如果收到ARP回复包,It means the host is online
抓包
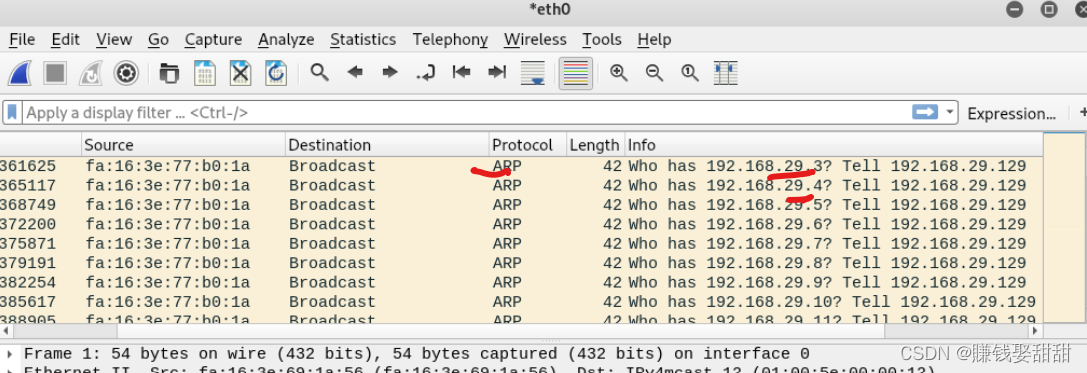
4、Host discovery across network segments
When scanning destination hosts across network segments,使用-sP/sn选项,默认情况下nmap会依次发送4different types of packets(ICMP echo request 、TCP SYN packet to port 443、TCP ACK packet to port 80、ICMP timestamp request)to detect whether the target host is online,Just get a reply for one of those packages,It means the host is online
例:Scan the address of my physical machine
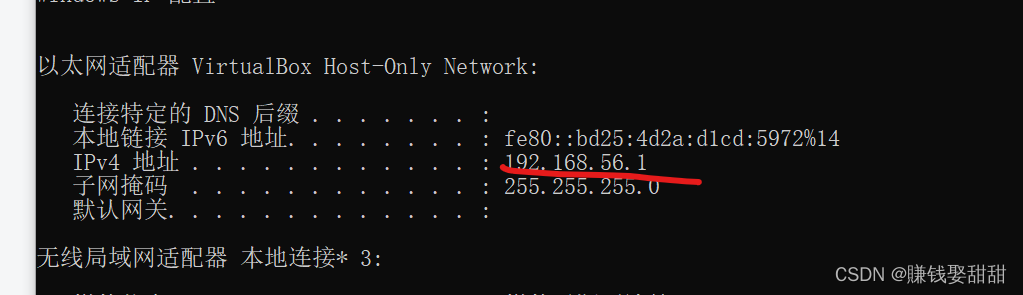
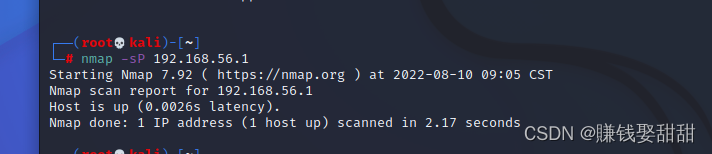
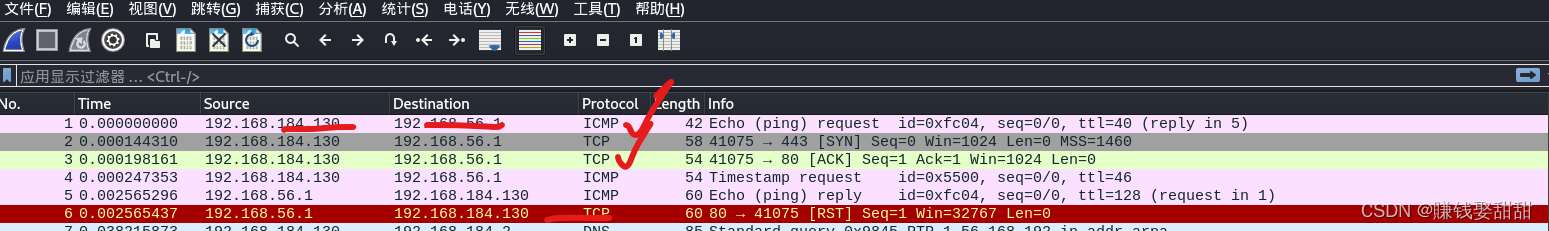
5、--packet-trace(You don't need to capture packets,Display the results directly)
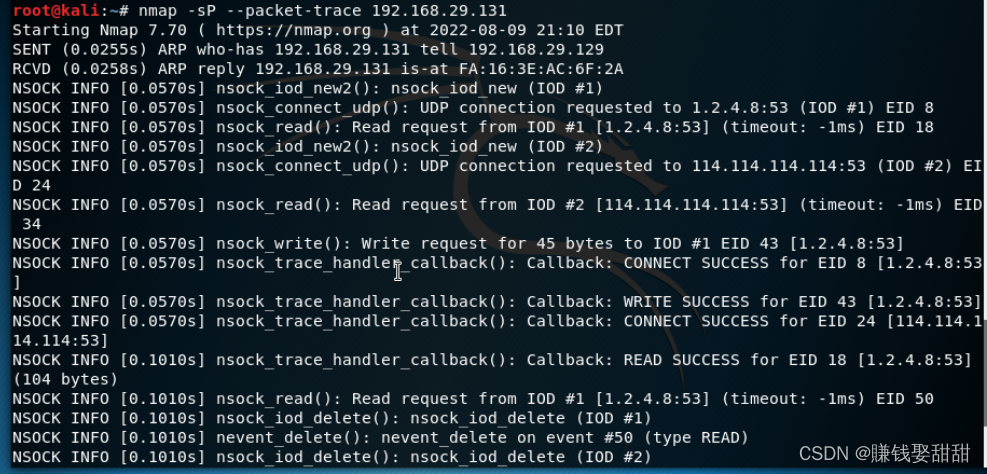
四、端口扫描
1、原理:发送TCP、UDPand other types of probe packets to the destination port,Determine whether the port is open according to the received reply packet
2、6种端口状态:
open:端口打开的
close:Port is closed
filtered:端口被防火墙/IDS/IPS屏蔽,Can't fault its status
unfiltered:端口没有被屏蔽,But whether it is open or not requires further confirmation
open|filtered:端口是开放的或被屏蔽
close|filtered:端口是关闭的或被屏蔽
3、Related command options
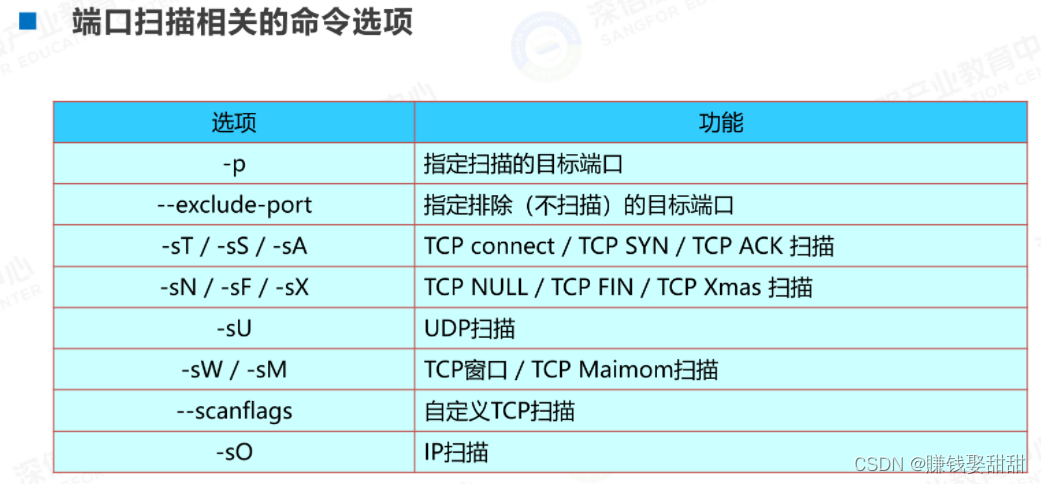
4、扫描指定端口
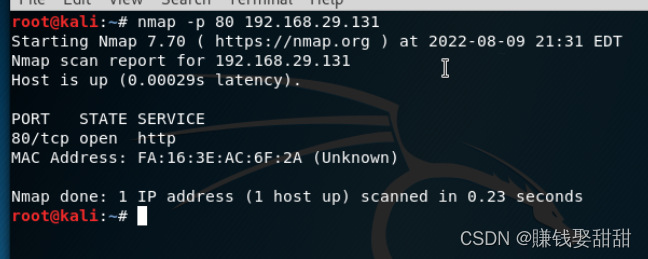

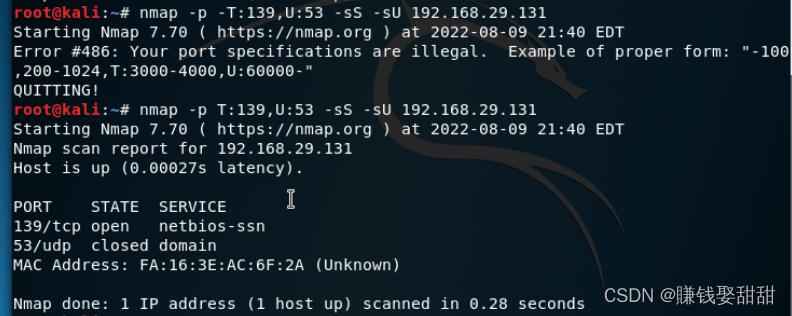
关于-p选项的说明:默认情况下,nmapfor use only-pScan the specified port,扫描方式为-sS(TCP SYN扫描).If you want to scan bothTCP端口,又要扫描UDP端口,则可以用“T:” “U:”The parameter specifies the destination port,并指定-sU(UDP扫描方式)和至少一种TCP扫描方式,例:
5、TCP SYN 扫描 (优点:隐蔽性较好)
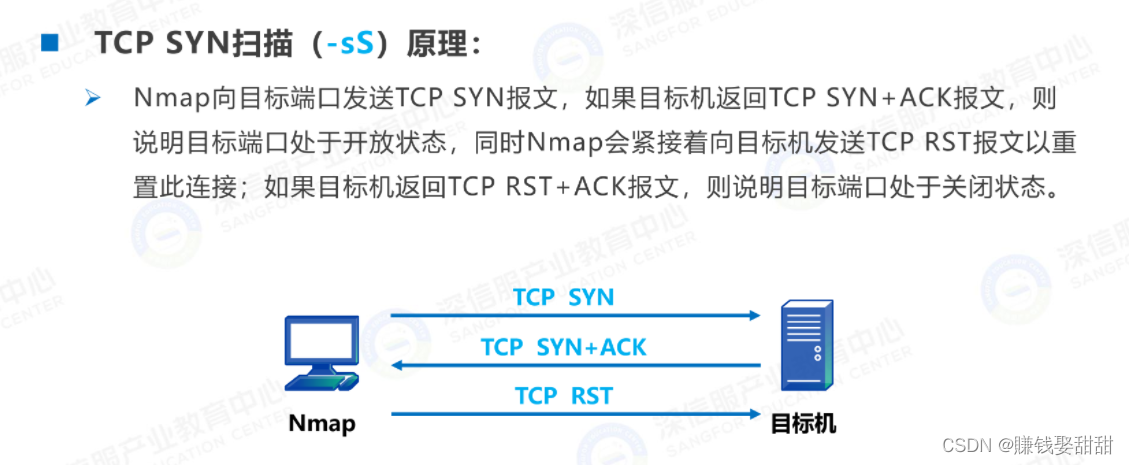
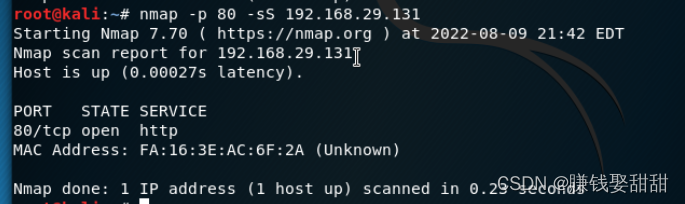
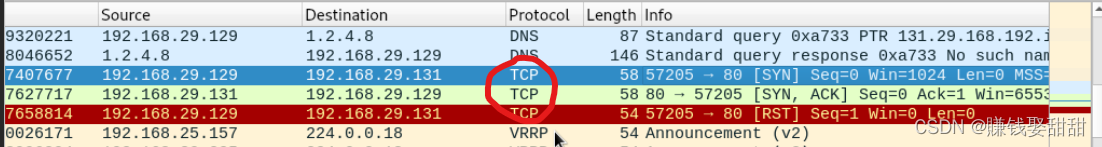
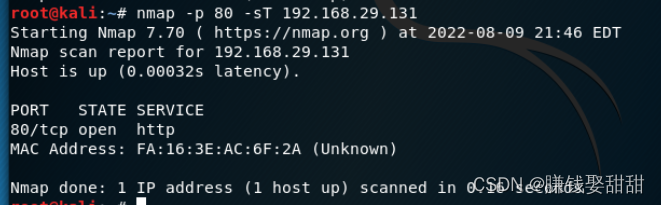
6、TCP connect 扫描

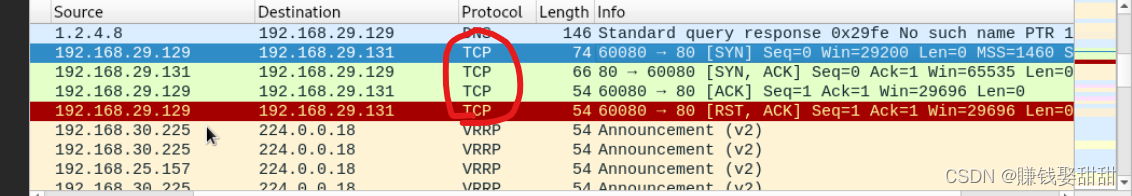
7、TCP ACK 扫描
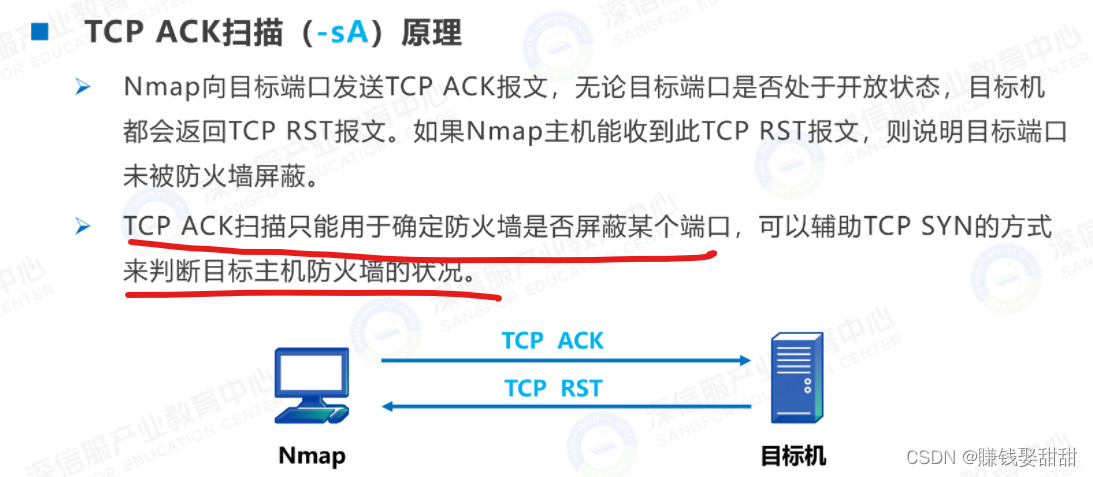
首先,我win7The firewall is turned off
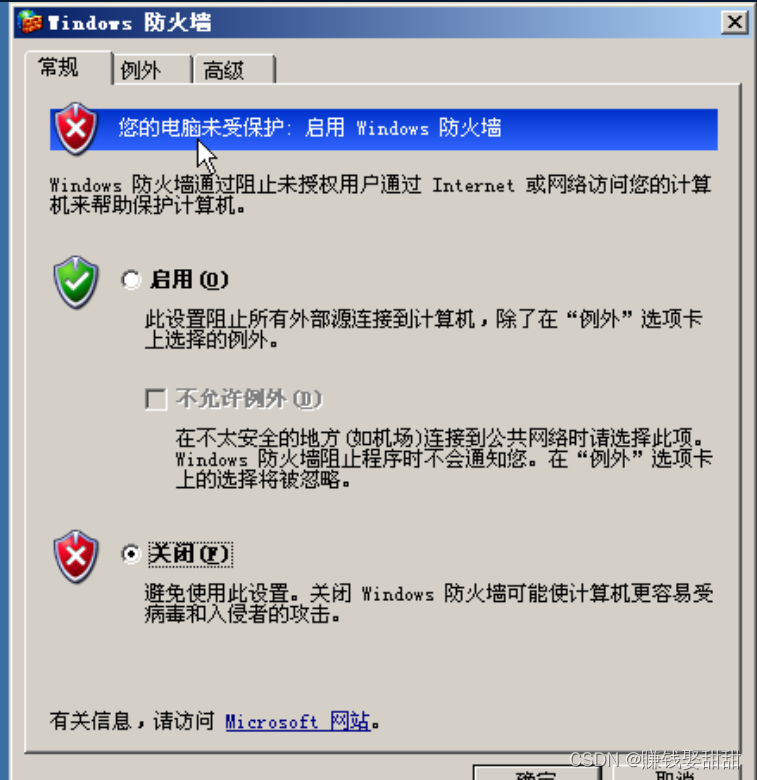
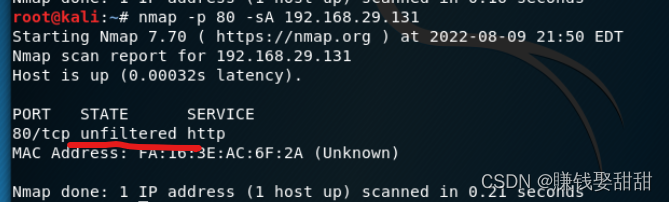
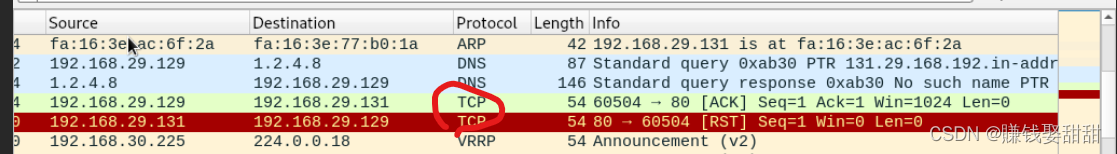
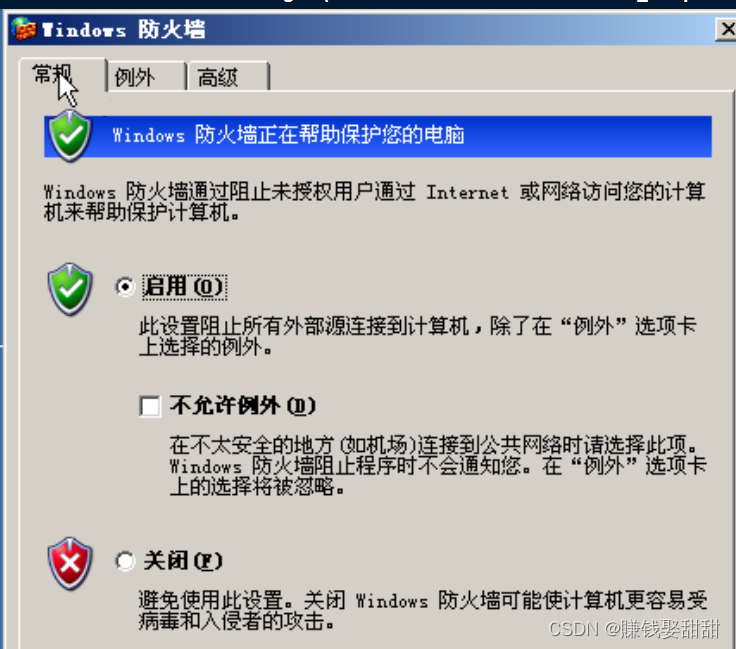
Then I turned on the firewall:
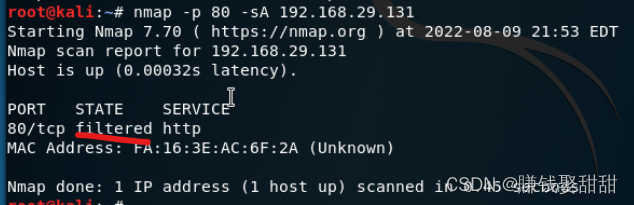
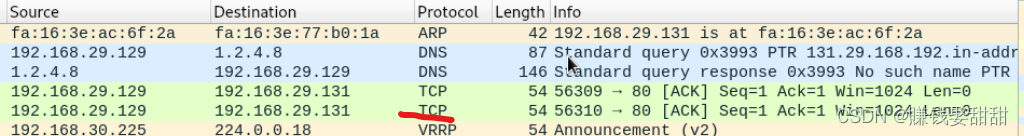
然后抓包,没有TCP RST包
8、隐蔽扫描(比较适用于Linux系统的主机)
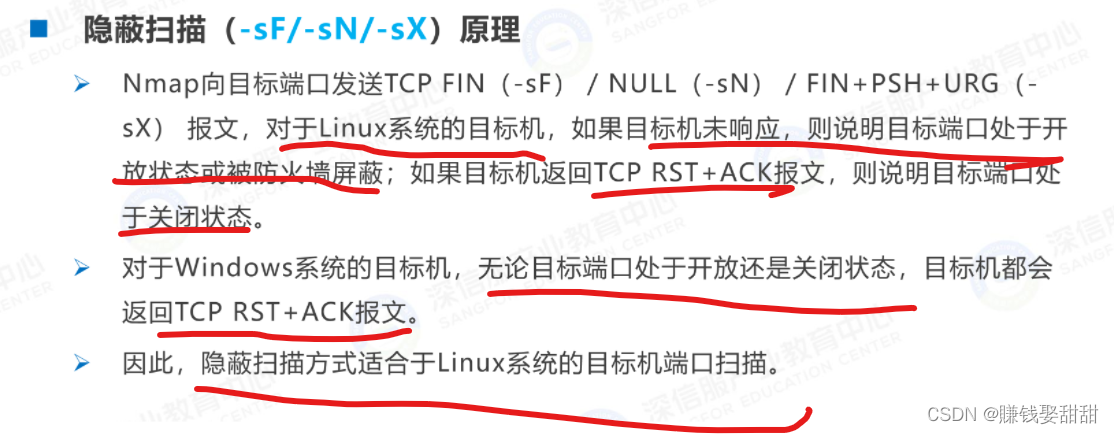
扫描windows系统主机
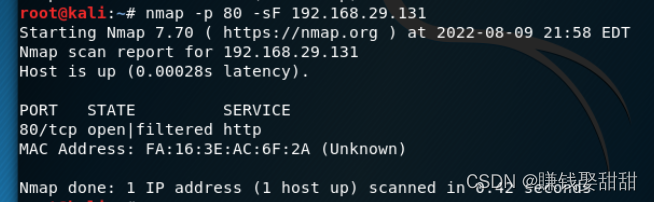

扫描Linux系统主机(IP:192.168.184.128)
![]()
五、应用程序与版本信息侦测
1、
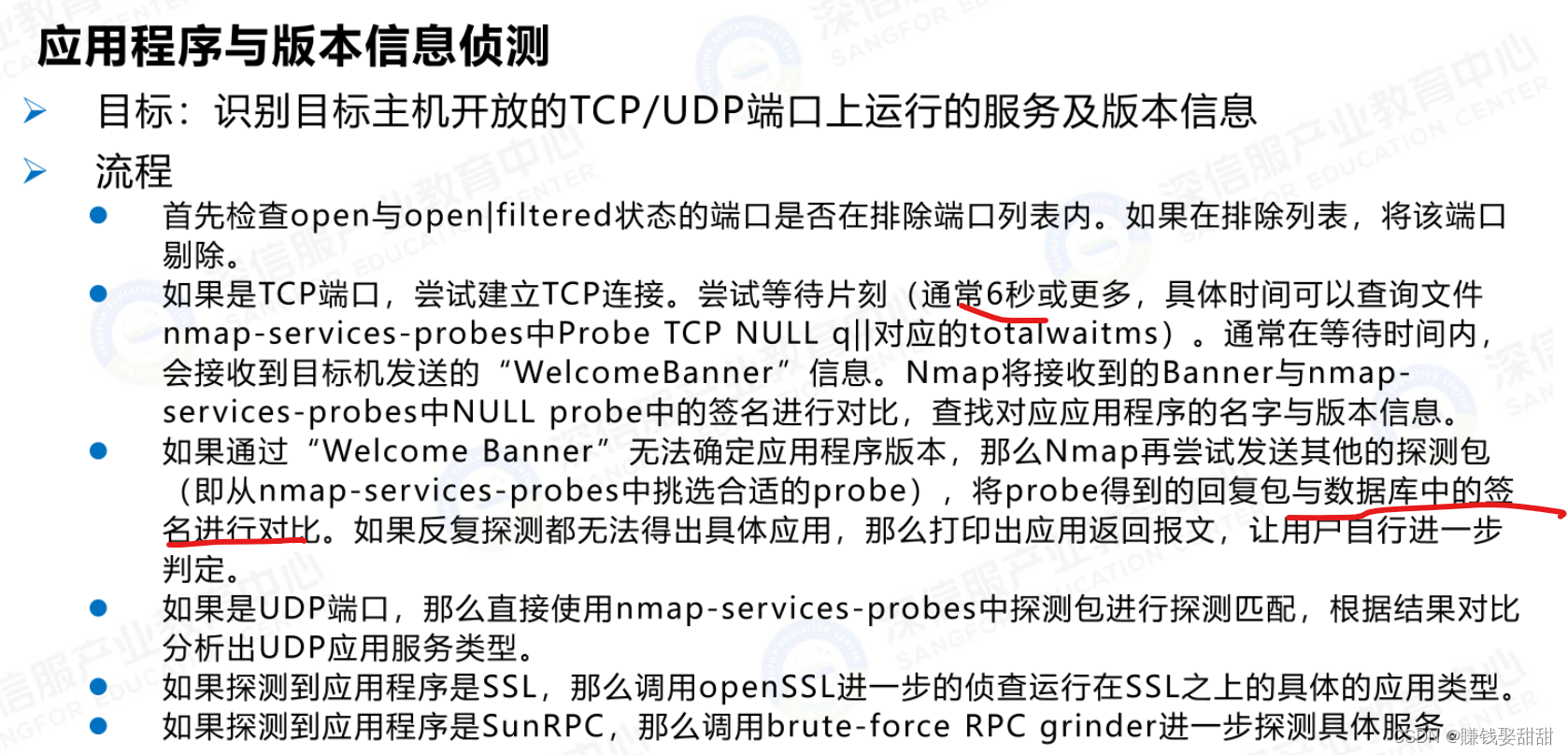
2、相关命令:
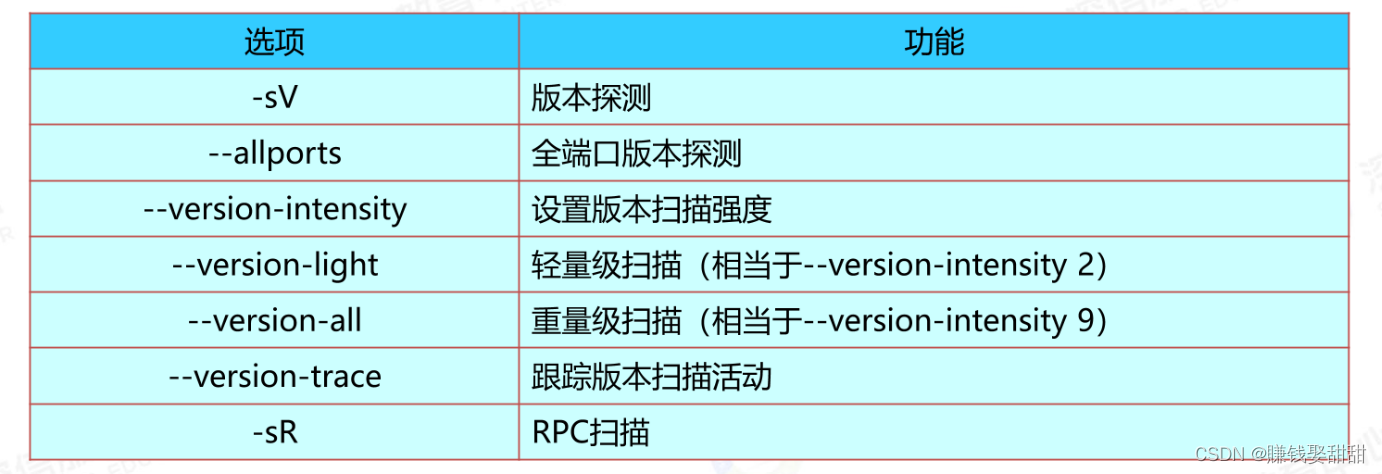
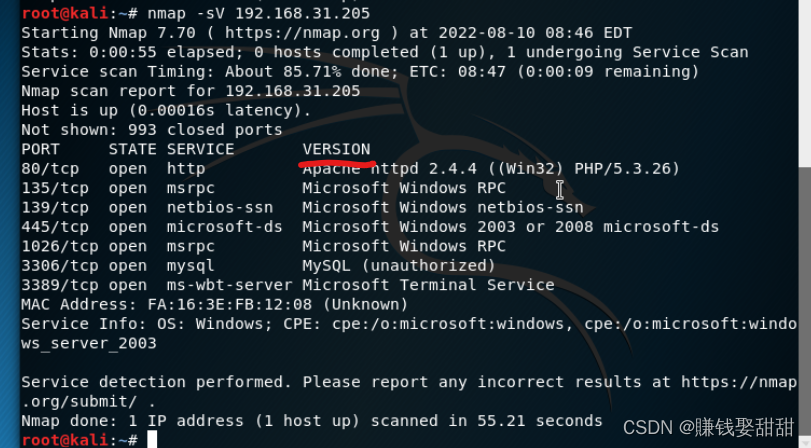
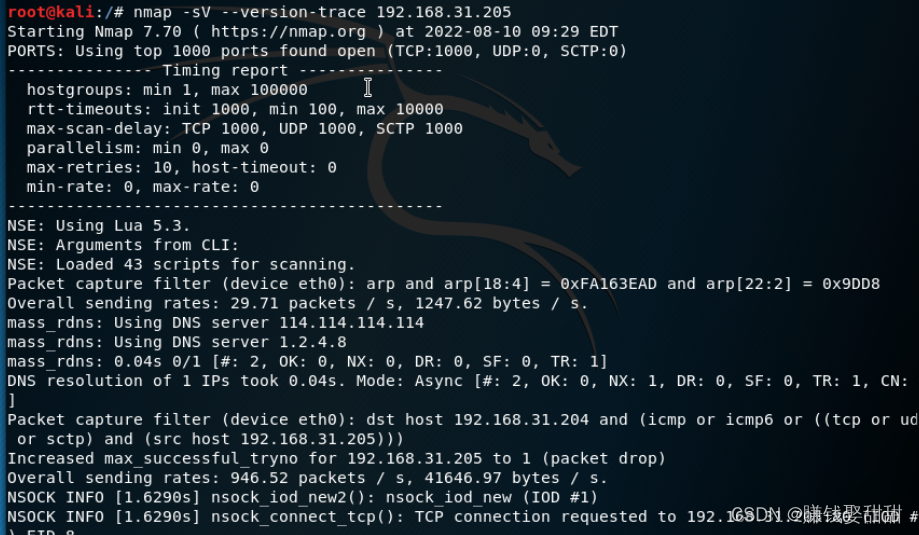
3、version-trace命令:
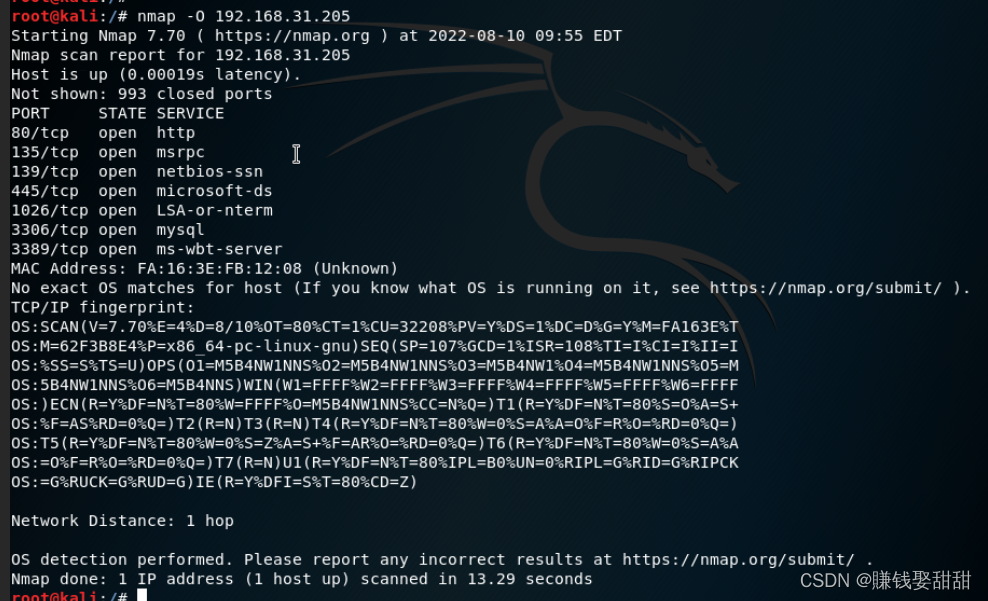
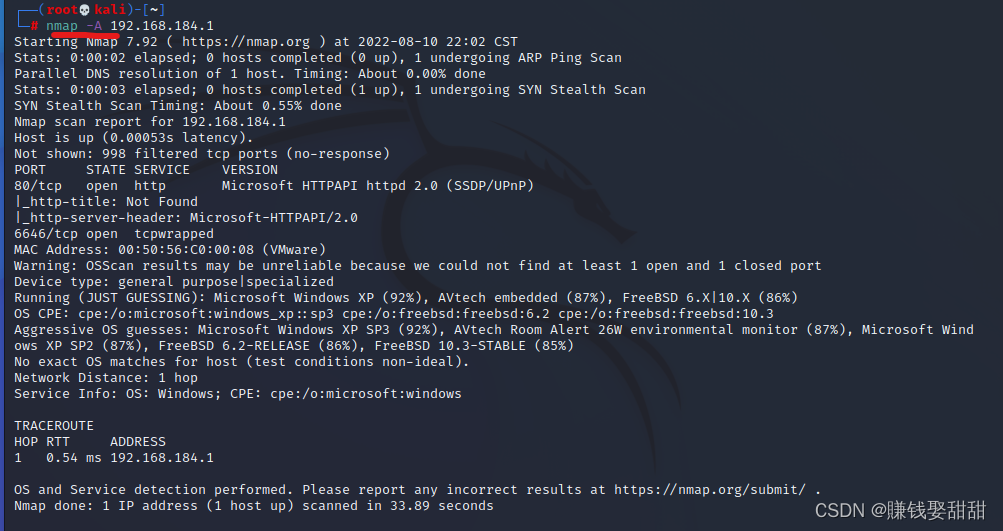
六、操作系统扫描:
1、侦测方法:Network protocol stack fingerprinting technology
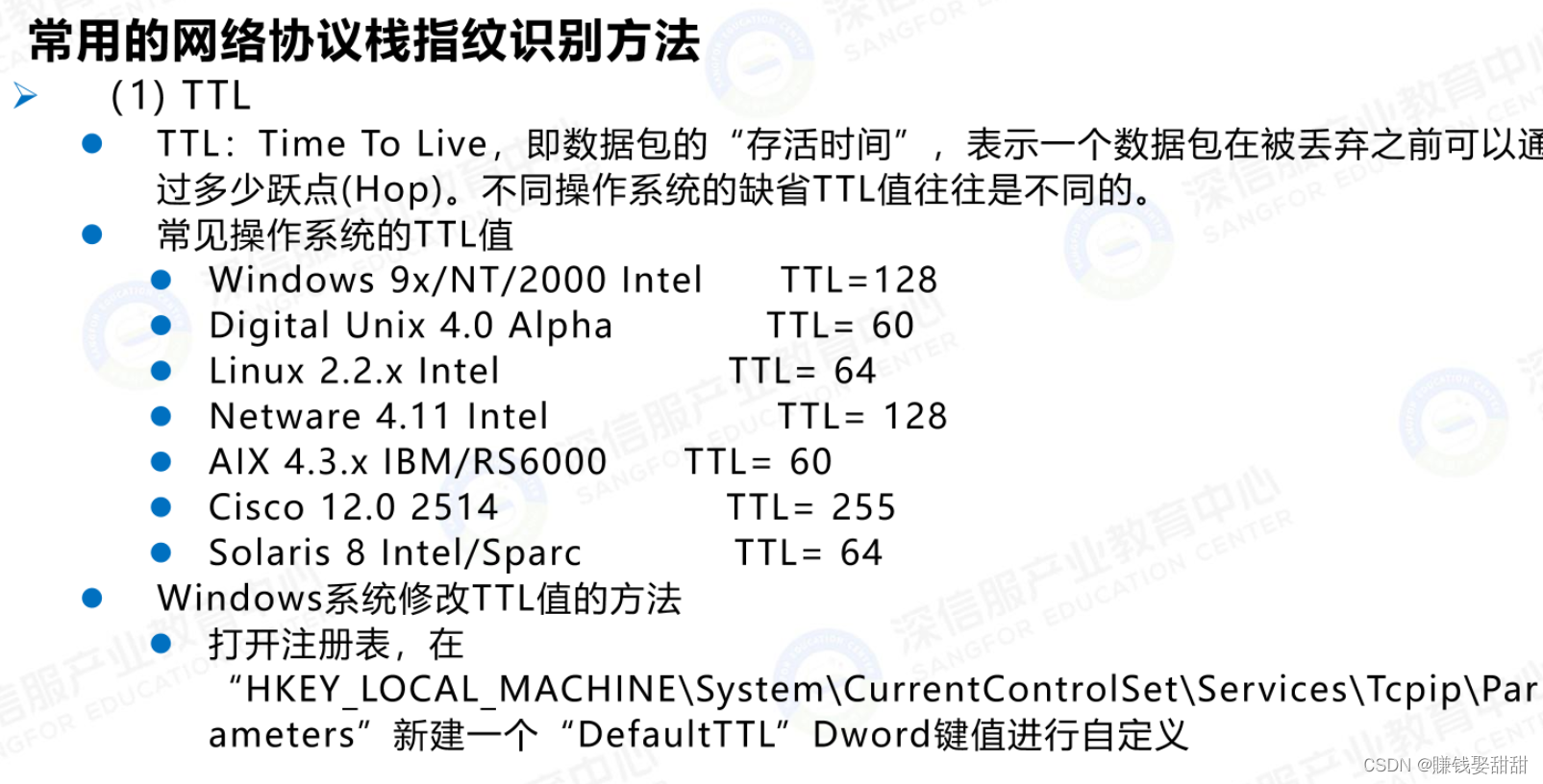
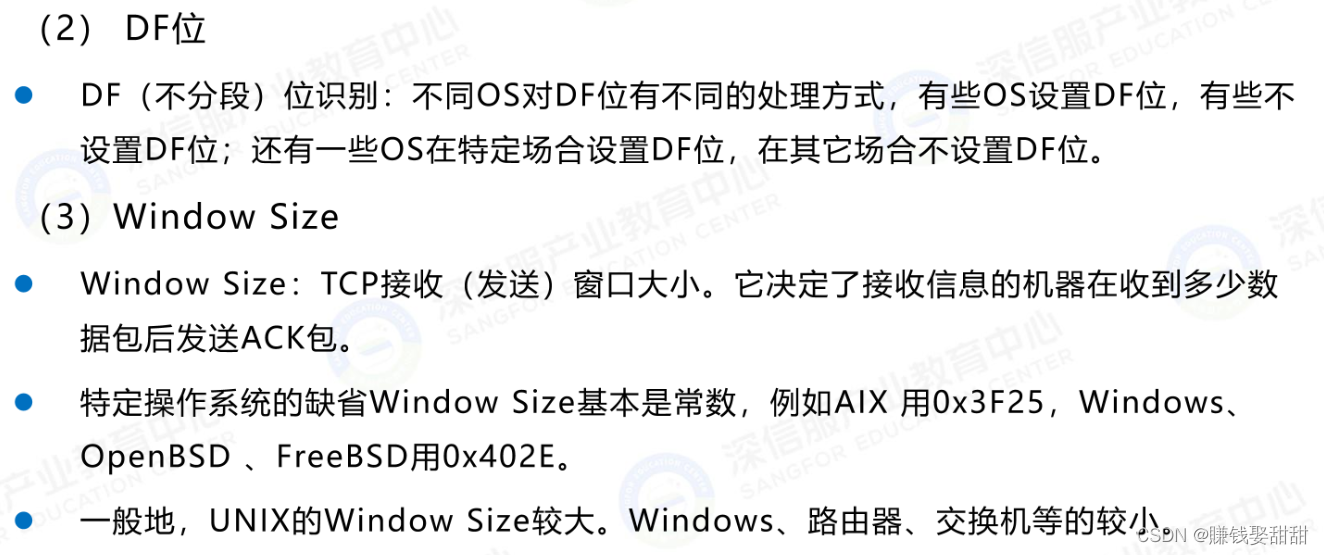

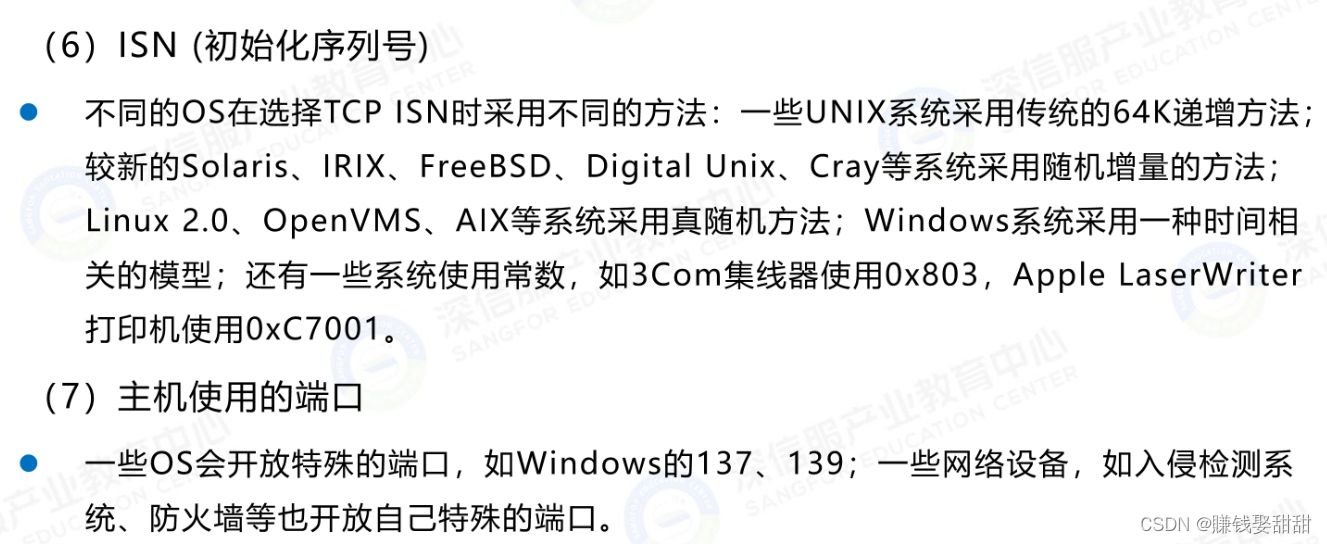
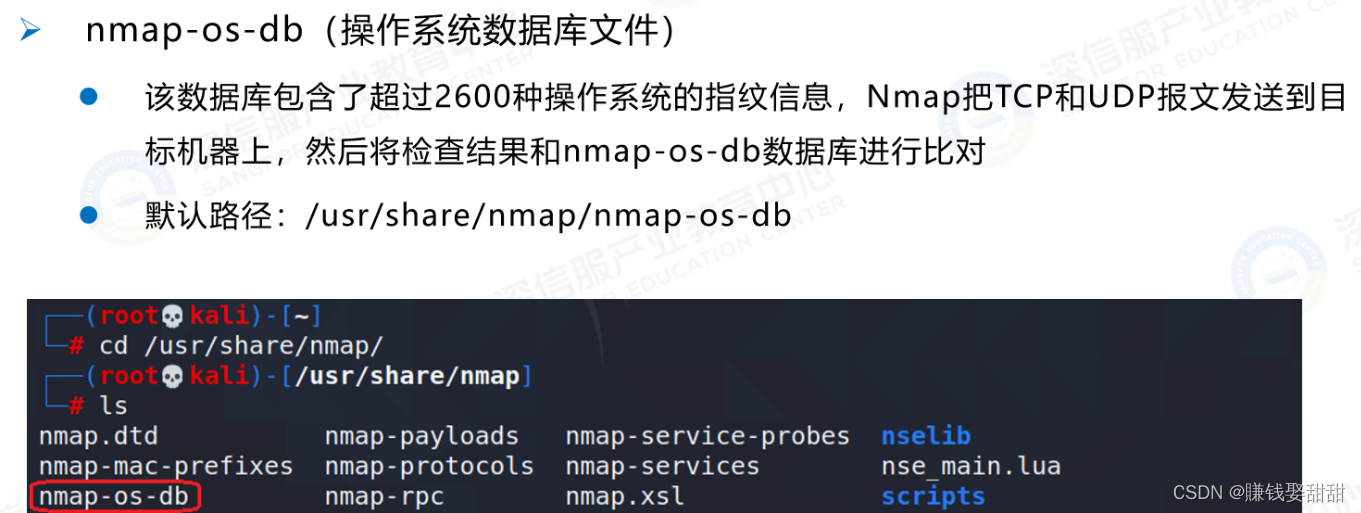
2、相关命令:
七、规避FW/IDS技术
1、
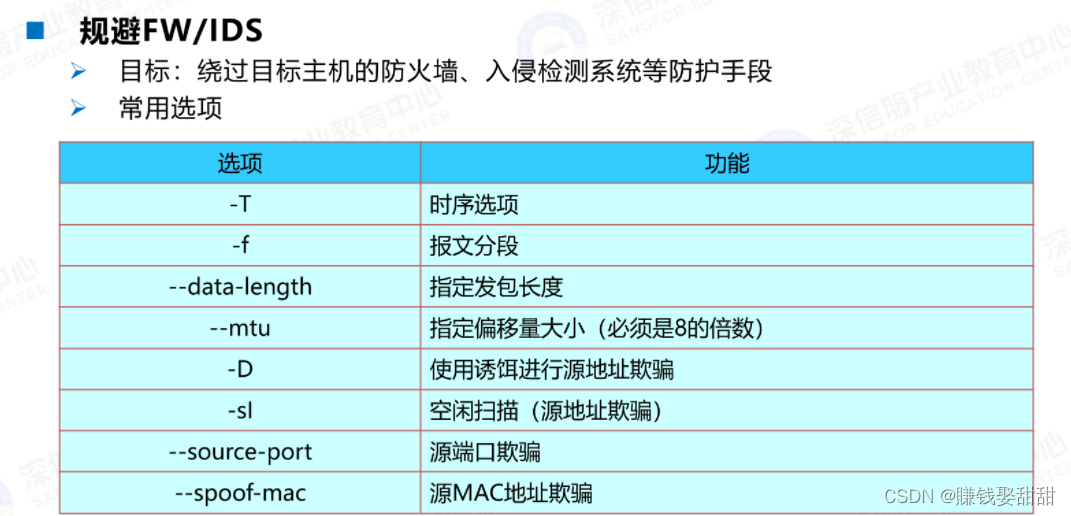
2、-T选项的应用

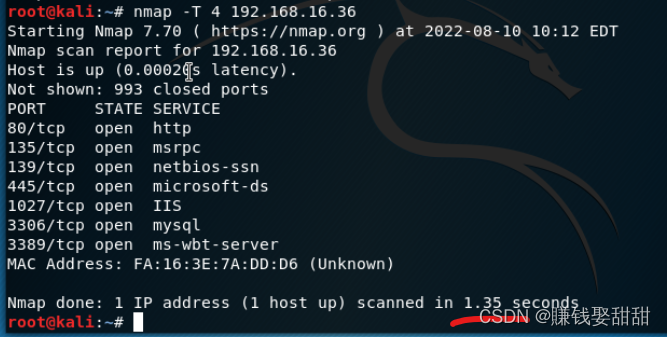
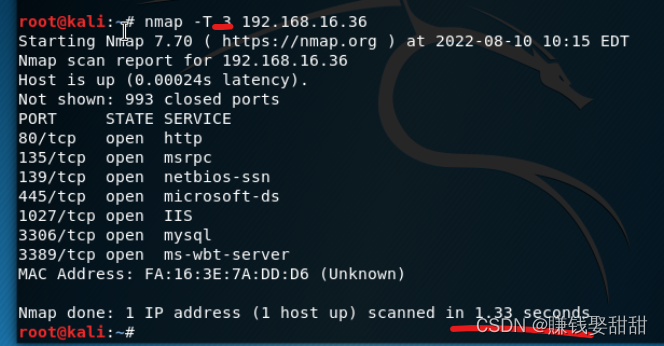
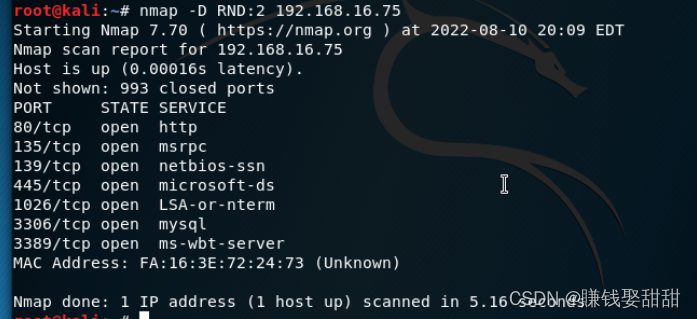
3、-D,进行源地址欺骗(原IP:192.168.16.74)

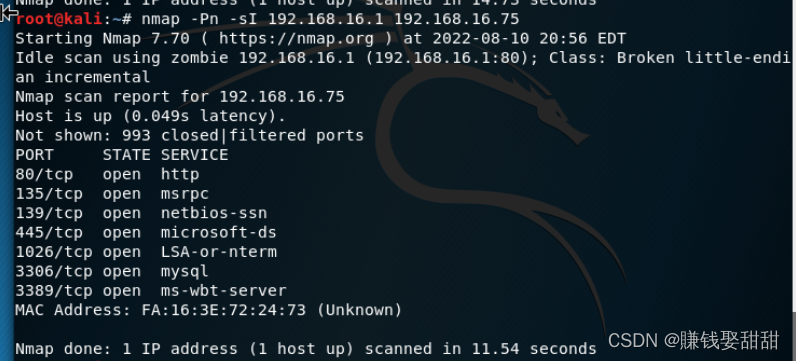
4、-sI(大写的i),伪装源IP
Use the gateway address to masquerade as the sourceIP(192.168.16.1),向目标主机(192.168.16.75)Send scan packets
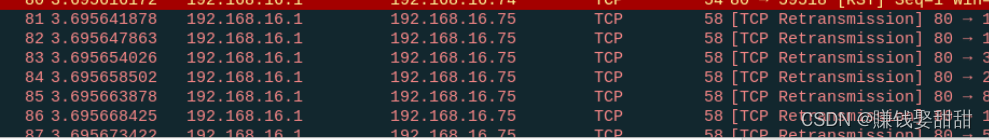
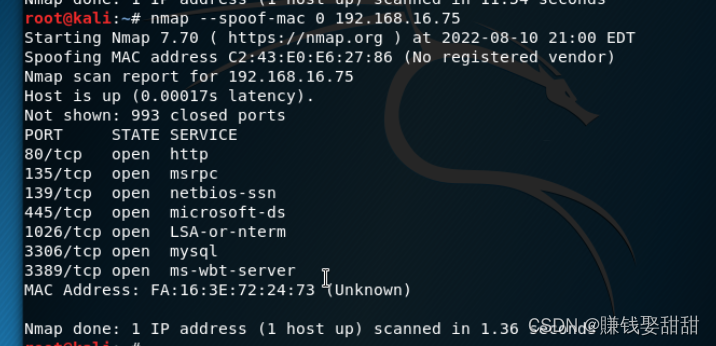
5、源MAC地址欺骗
nmap --spoof-mac 0 目标主机 0Represents a random assignmentmac地址,也可以指定一个mac
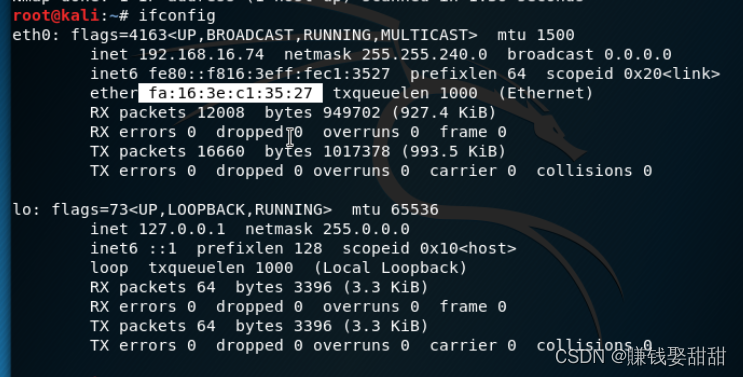
源mac地址
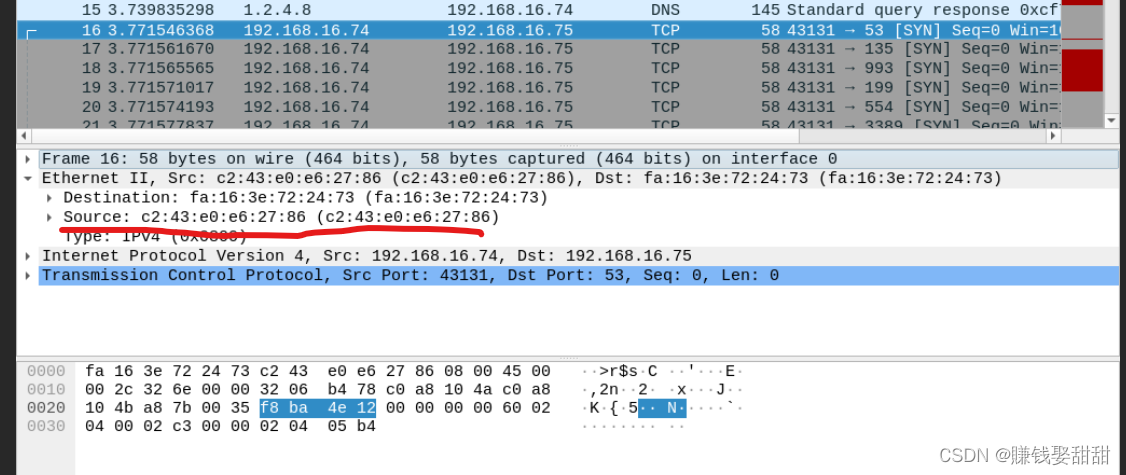
欺骗的mac地址
八、NSE脚本的使用
1、NSE脚本是基于Lua语言编写的
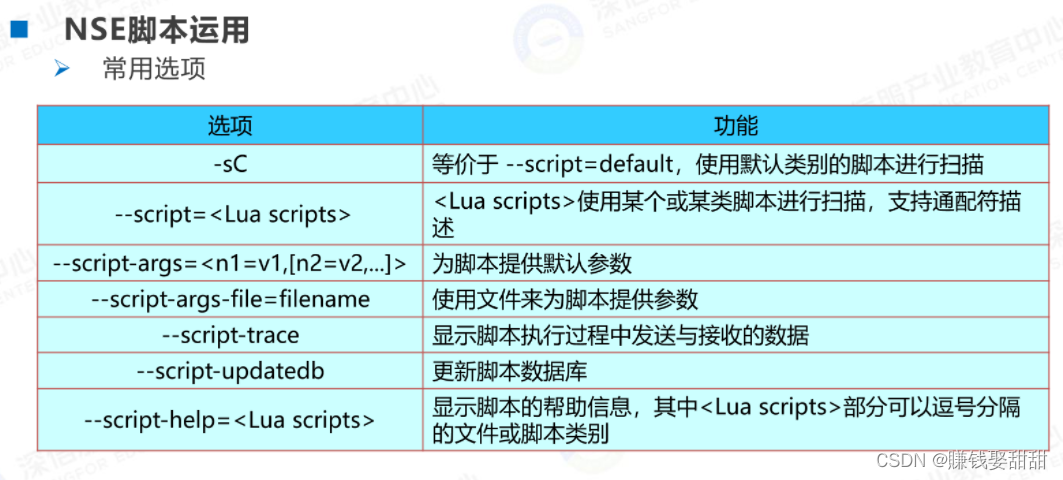
2、暴力破解脚本(--script brute)的使用
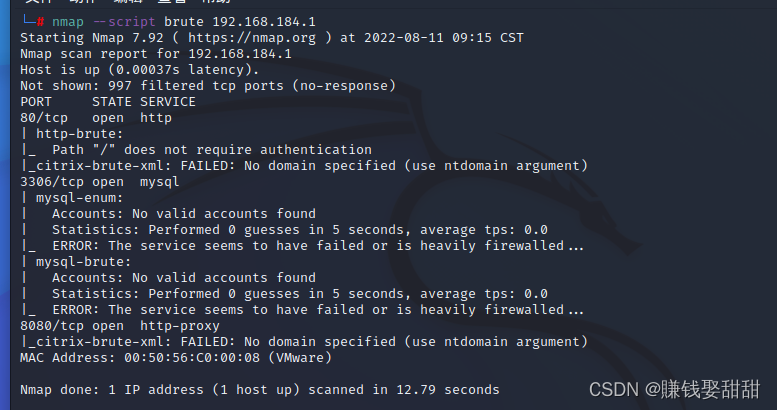 2、扫描常见的漏洞
2、扫描常见的漏洞
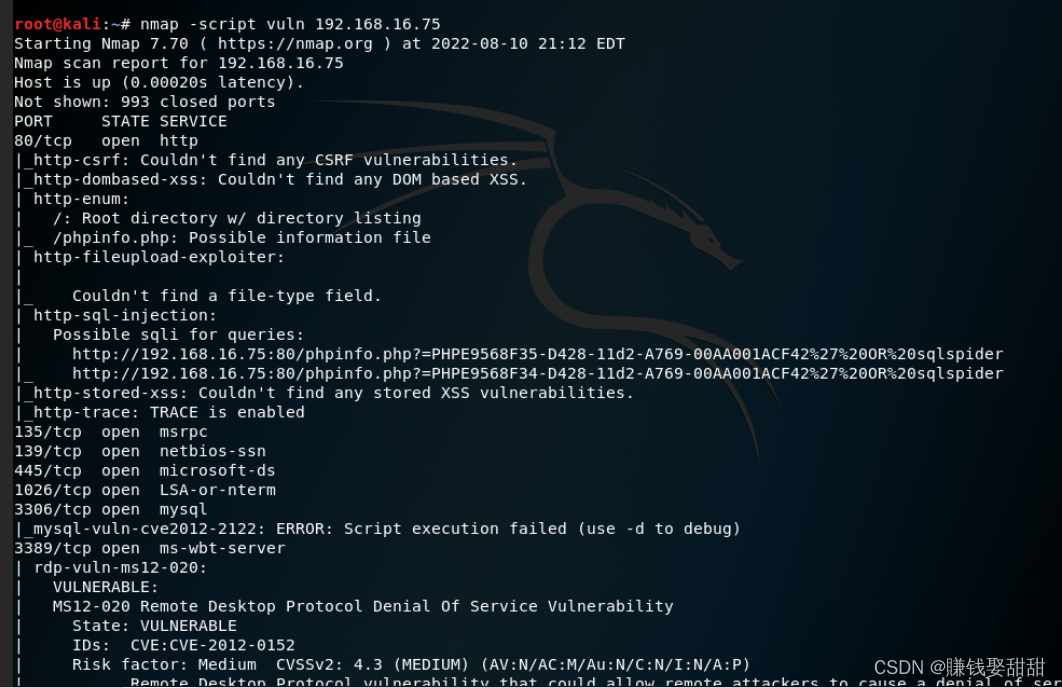
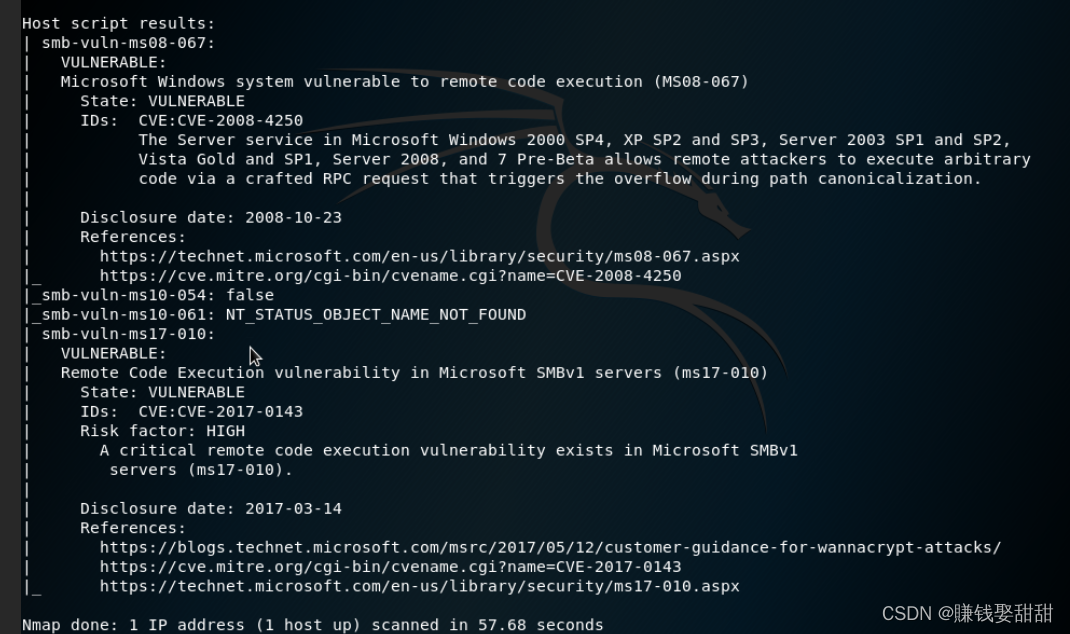
九、Save and output scan results
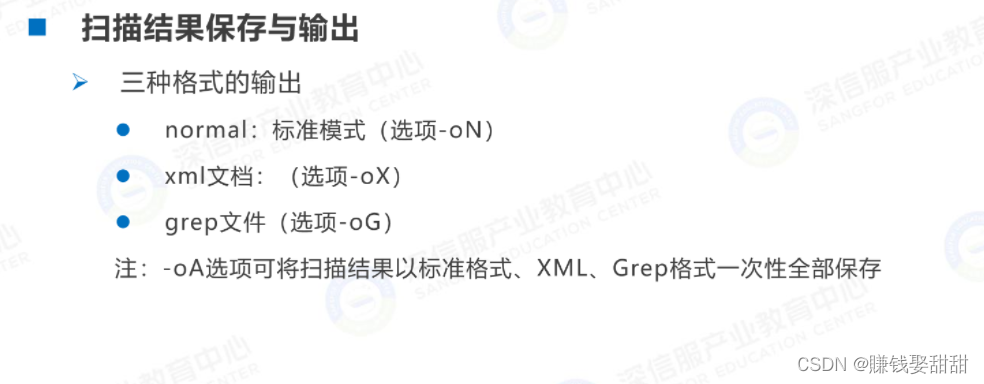
1、Output in standard mode
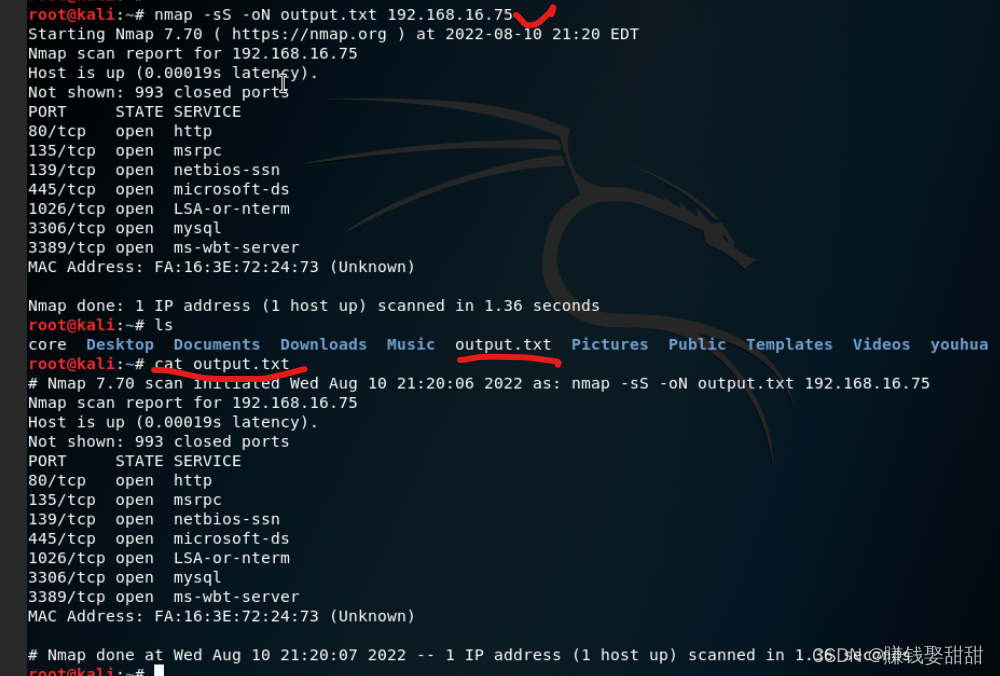
这篇文章就写到这里了,文章中的IPNot all addresses are the same!
边栏推荐
- Cholesterol-PEG-FITC,Fluorescein-PEG-CLS,胆固醇-聚乙二醇-荧光素水溶性
- Incredible, thanks to this Android interview question, I have won offers from many Internet companies
- 从零开始配置 vim(11)——插件管理
- The fertile soil cloud innovation plan is coming
- Bitmap这个“内存刺客”你也要小心
- 那些不用写代码也能做游戏的工具
- [Study Notes] Maximum matching of general graphs
- 十九、一起学习Lua 垃圾回收
- 论文笔记:《Time Series Generative Adversrial Networks》(TimeGAN,时间序列GAN)
- Getting Started with Chrome Plug-in Development - Nanny Level Raiders
猜你喜欢

参与openEuler社区不到1年,我成为了Maintainer……
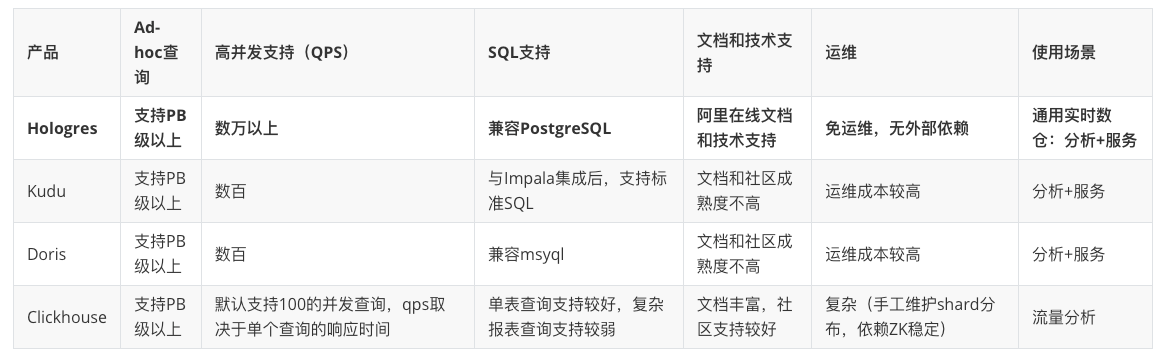
阿里云 Hologres助力好未来网校实时数仓降本增效

Qihua stores the future and interprets the origin of distributed
阿里云ssl证书申请,宝塔ssl证书部署
EXCLUSIVE INTERVIEW | INTELLIGENCE IS SPONTANED, NOT PLANNED: Evolution Fan, Former OpenAI Research Manager and UBC Associate Professor Jeff Clune
【项目篇- 项目团队部分怎么写、如何作图?(两千字图文总结建议)】创新创业竞赛项目计划书、新苗国创(大创)申报书、挑战杯创业计划竞赛
兴盛优选:时序数据如何高效处理?
![[10点公开课]:AV1编码器的优化及其在流媒体和实时通讯中的应用](/img/86/a6cd309cd66eb37159fcb8ae3338b1.png)
[10点公开课]:AV1编码器的优化及其在流媒体和实时通讯中的应用
如何批量下载hugging face模型和数据集文件

Azure IoT & NVIDIA Jetson 开发基础
随机推荐
SDS观察站
openEuler小程序会议指南
AWS、Splunk和Symantec牵头成立OCSF开放网络安全架构框架
悠漓带你玩转C语言(详解操作符1)
ID3v2 Library以便能够设置
一站式PCBA组装加工有哪些环节?
Install nodejs
10Super详解
a sequence of consecutive positive numbers with sum s
Notes and Recommendations for Using Logs
form-making notes on climbing pits (jeecg project replaces form designer)
阿里云 Hologres助力好未来网校实时数仓降本增效
关于数据权限的设计
Are there any foreign application cases for domestic databases?
3. static成员
开源汇智创未来 | 软通动力出席开放原子全球开源峰会OpenAtom openEuler分论坛
从抖音到火山引擎——看流媒体技术演进和机会
Spark Core
Analyzes how Flink task than YARN container memory limit
我用这个操作,代码可读性提升一个档次