当前位置:网站首页>[leetcode 383] ransom letter
[leetcode 383] ransom letter
2022-04-23 06:23:00 【Don't steal my energy】
Topic introduction
Here are two strings :ransomNote and magazine , Judge ransomNote Can it be done by magazine The characters inside make up .
If possible , return true ; Otherwise return to false .
magazine Each character in can only be in ransomNote Used once in .
Example 1
Input :ransomNote = "a", magazine = "b"
Output :false
Example 2
Input :ransomNote = "aa", magazine = "ab"
Output :false
Example 3
Input :ransomNote = "aa", magazine = "aab"
Output :true
Tips
- 1 <= ransomNote.length, magazine.length <= 105
- ransomNote and magazine It's made up of lowercase letters
Ideas
The idea and of this question 【LeetCode 350 Intersection of two arrays II】 10 Fen is the same , The core is to use the idea of hash table . take magazine The letters in and the number of times they appear are stored separately , And then go through ransomNote Letters in , Judge , If the number of occurrences >0, The number of times it appears -1, Traverse the next letter ; If the number of occurrences ==0, shows ransomNote Can it be done by magazine The characters inside make up , return flase.
1. One dimensional array implementation
bool canConstruct(string ransomNote, string magazine) {
int a[123]={
0};// Small letters z Of ascii value 122
for(char x:magazine)
a[int(x)]++;
for(char y:ransomNote){
if(a[int(y)]>0)
a[int(y)]--;
else
return 0;
}
return 1;
}
2. Hash table implementation
bool canConstruct(string ransomNote, string magazine){
unordered_map<char,int>a; // take magazine The letters in and their occurrences are stored separately
for(char x:magazine)
a[x]++;
for(char y:ransomNote){
if(a[y]>0)
a[y]--;
else
return 0;
}
return 1;
}
On memory consumption , The array implementation is lower than the hash table implementation .
版权声明
本文为[Don't steal my energy]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210617012053.html
边栏推荐
- Generate excel template (drop-down selection, multi-level linkage)
- Supply chain service terms
- Traitement des séquelles du flux de Tensor - exemple simple d'enregistrement de torche. Utils. Données. Dataset. Problème de dimension de l'image lors de la réécriture de l'ensemble de données
- In depth understanding of the relationship between dncblevel and noise denoising in the paper
- Comparative study paper - [Moco, cvpr2020] momentum contract for unsupervised visual representation learning
- Sakura substring thinking
- Kingdee EAS "general ledger" system calls "de posting" button
- Rainbow (DP)
- Integers have friends interval GCD + double pointer
- PyTorch笔记——通过搭建ResNet熟悉网络搭建方式(完整代码)
猜你喜欢

C language file operation

线性代数第一章-行列式

Automatic control (Han min version)

深度学习基础——简单了解meta learning(来自李宏毅课程笔记)
![How to use comparative learning to do unsupervised - [cvpr22] training & [eccv20] image translation](/img/33/780b80693f70112eebc10941f7c134.png)
How to use comparative learning to do unsupervised - [cvpr22] training & [eccv20] image translation
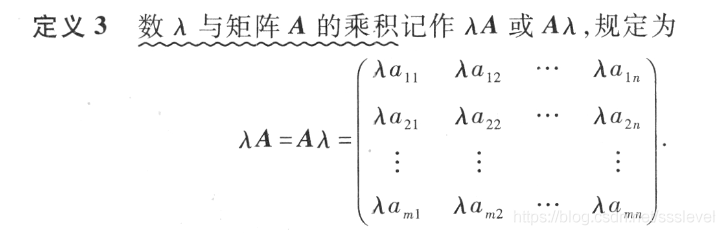
線性代數第二章-矩陣及其運算
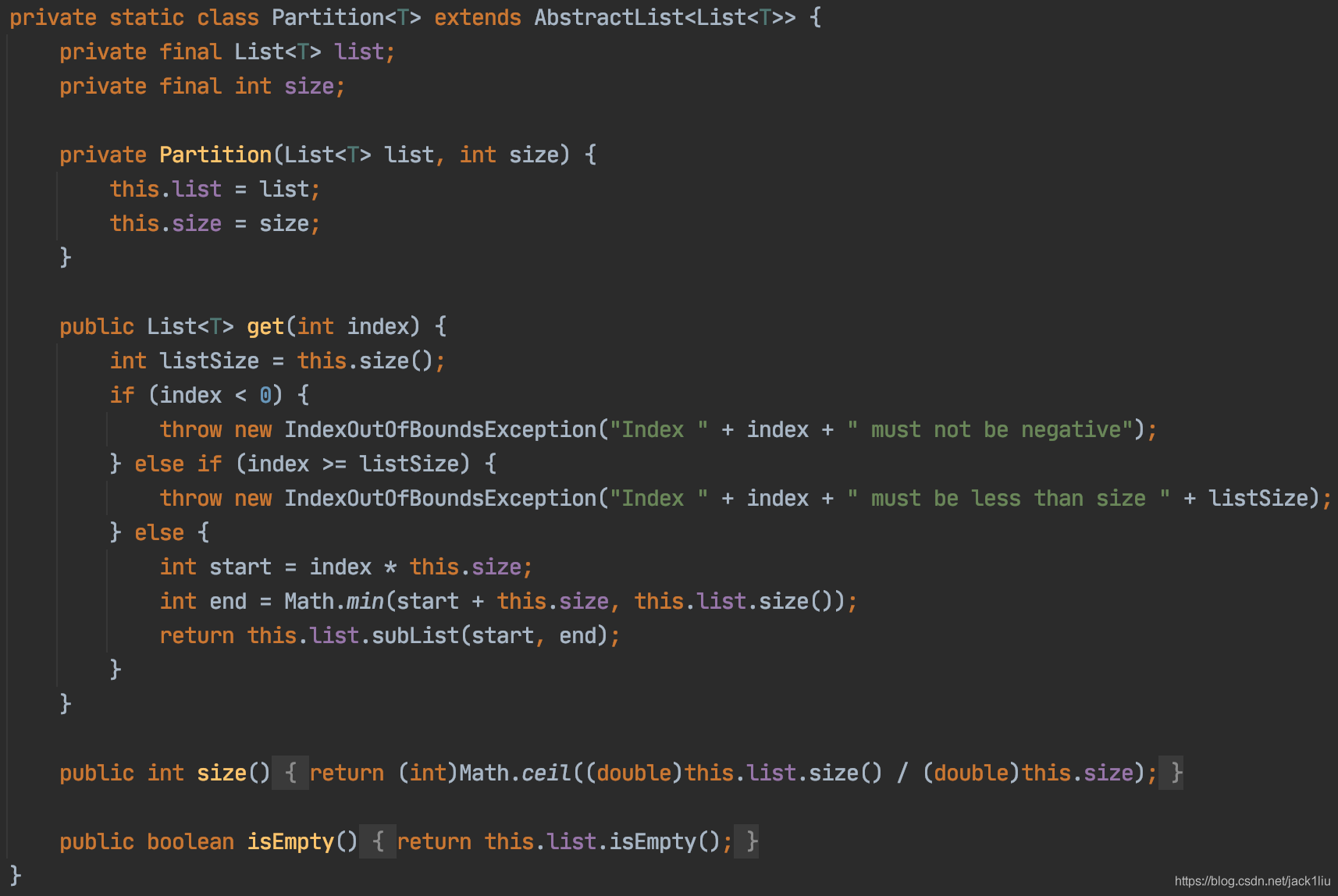
List segmentation best practices
![对比学习论文——[MoCo,CVPR2020]Momentum Contrast for Unsupervised Visual Representation Learning](/img/21/4bc94fe29f416c936436c04fc16fa8.png)
对比学习论文——[MoCo,CVPR2020]Momentum Contrast for Unsupervised Visual Representation Learning

线代第四章-向量组的线性相关

You cannot access this shared folder because your organization's security policy prevents unauthenticated guests from accessing it
随机推荐
深入理解去噪论文——FFDNet和CBDNet中noise level与噪声方差之间的关系探索
The problem that the page will refresh automatically after clicking the submit button on the form is solved
Optional best practices
Pytorch introduction notes - use a simple example to observe the output size of each layer of forward propagation
程序设计训练
PyTorch笔记——通过搭建ResNet熟悉网络搭建方式(完整代码)
深度学习基础——简单了解meta learning(来自李宏毅课程笔记)
Custom exception class
IO multiplexing of 09 redis
Pyqy5 learning (2): qmainwindow + QWidget + qlabel
Paper on Image Restoration - [red net, nips16] image restoration using very deep revolutionary encoder decoder networks wi
RPC must know and know
How does MySQL convert stored seconds into dates
C language file operation
图像恢复论文简记——Uformer: A General U-Shaped Transformer for Image Restoration
Automatic control (Han min version)
Integration and induction of knowledge points of automatic control principle (Han min version)
Numpy common function table sorting of data processing
Understanding and installing MySQL
对比学习论文——[MoCo,CVPR2020]Momentum Contrast for Unsupervised Visual Representation Learning