当前位置:网站首页>Thoughts on the 2022 national network security competition of the national secondary vocational group (only one idea for myself) - network security competition questions (9)
Thoughts on the 2022 national network security competition of the national secondary vocational group (only one idea for myself) - network security competition questions (9)
2022-04-23 03:01:00 【Shandong Wangan vegetable chicken】
Personal thoughts only
Yes word file , I want a private letter
modular A Infrastructure setting and security reinforcement
A-1 Task a Login security (Windows)
1. Password policy
a. Perform complexity requirements when changing or creating passwords ;
Just look at the questions in front , There are answers
b. Password must meet complexity requirements ;
c. The minimum password life is 10 God .
2. User security management
a. Disable guest accounts &
版权声明
本文为[Shandong Wangan vegetable chicken]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220633315240.html
边栏推荐
- REINFORCE
- Summary of interface automation interview questions for software testing
- How to use C language to realize [guessing numbers game]
- Solve the problem that PowerShell mining occupies 100% of cpu7 in win7
- How can enterprises with major hazard installations ensure the completion of the digital construction task of double prevention mechanism by the end of the year
- Introduction to ACM [TSP problem]
- [hcip] detailed explanation of six LSAS commonly used by OSPF
- 基于Scrum进行创新和管理
- OCR识别PDF文件
- JZ22 链表中倒数最后k个结点
猜你喜欢
Android high-level interview must ask: overall business and project architecture design and reconstruction
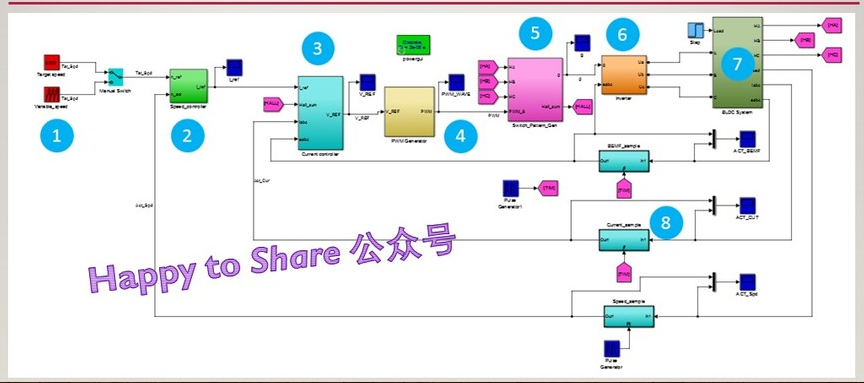
BLDC double closed loop (speed PI + current PI) Simulink simulation model

重大危险源企业如何保障年底前完成双预防机制数字化建设任务
Detailed explanation of distributed things

Traversée de l'arbre L2 - 006

Store consumption SMS notification template

Processes and threads
Linux Redis ——Redis HA Sentinel 集群搭建详解 & Redis主从部署

工业互联网+危化安全生产综合管理平台怎样建

tf. keras. layers. MaxPooling? D function
随机推荐
[hcip] detailed explanation of six LSAS commonly used by OSPF
JZ76 删除链表中重复的结点
《信息系统项目管理师总结》第四章 项目成本管理
ele之Table表格的封装
Q-Learning & Sarsa
ROP Emporium x86_64 7~8题
Encapsulate components such as pull-down menu based on ele
AC380V drop 5v12v24v200ma, UHV non isolated chip IC scheme
VirtualBox virtual machine (Oracle VM)
Android high-level interview must ask: overall business and project architecture design and reconstruction
REINFORCE
The interface request takes too long. Jstack observes the lock holding
Deep q-network (dqn)
Basic workflow of CPU
Restart redis
[learn junit5 from official documents] [II] [writingtests] [learning notes]
JS learning notes
The shell monitors the depth of the IBM MQ queue and scans it three times in 10s. When the depth value exceeds 5 for more than two times, the queue name and depth value are output.
Reverse a linked list < difficulty coefficient >
It turns out that PID was born in the struggle between Lao wangtou and Lao sky