当前位置:网站首页>Recommended scheme of national manufactured electronic components
Recommended scheme of national manufactured electronic components
2022-04-23 04:38:00 【leiditech】

Program Overview :
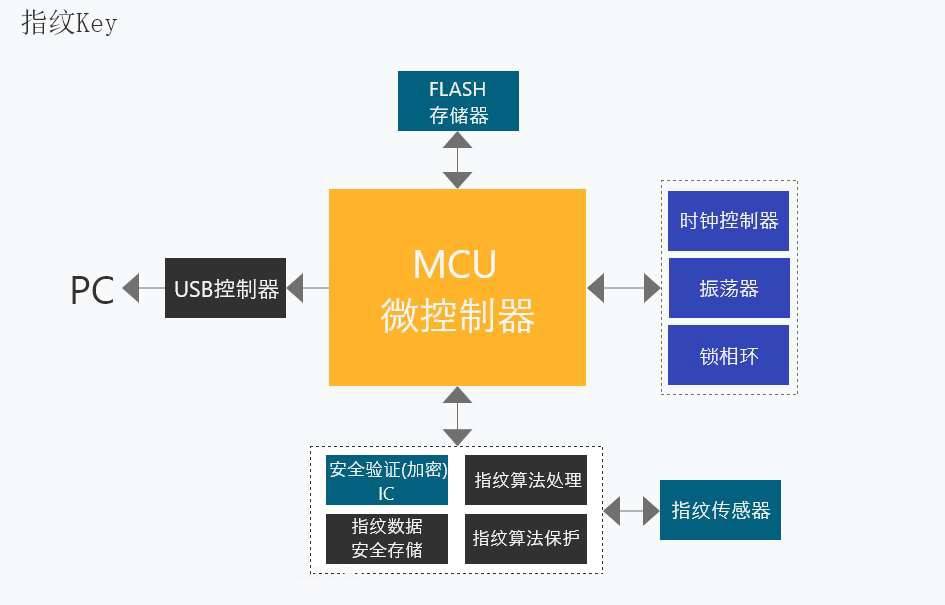
The fingerprint Key Take control of MCU At the core , The memory stores fingerprint digital template and authentication information . The fingerprint collector collects fingerprints and sends them to MCU, USB For controller Thousand connection PC End and MCU Communication for , Perform verification and comparison operations , All operations need a unified timing control . Secure authentication encryption IC Use thousands to ensure user trust The safety of interest .

Hot spots in the industry :
At present, network identity authentication methods are divided into single factor authentication / Two factor authentication / Multifactor authentication , The more factors, the higher the safety . The most typical way of multi factor authentication is certificate +us bke y, And fingerprints ke y+ Certificate is the most secure and reliable multi factor authentication
A convenient , Therefore, it has become the most perfect way to solve identity authentication . among Adopt financial grade security chip , It can resist various physical attacks .

Core devices :
As shown in the figure above, the of the aircraft core ACH51 2- LQFP100 It is a high-performance based on security algorithm SoC chip .
1. It is mainly used in thousands of eMMC/ SD/ Na ndf l a s h Mass storage devices 、 encryption U disc 、 Fingerprint recognition and other markets .
2. The chip uses 32 Bit kernel , A variety of security password modules are integrated in the chip , Include SMl 、SM2、SM3、SM4、SSF33 count Law ,
as well as RSA/ ECC、 ECDSA、DES/ 3DES、AES128/ 192/ 256 、SHAl / 256/ 384/ 512 And other security algorithms .
3. The chip provides a variety of peripheral interfaces : USB2. 0、UART 、SDI O、 I S07816、I 2C、 SPI 、NFM, MI M See the specification on the product details page for others
Industry combing :


For fingerprints Key Recommended products

The fingerprint Key source : Use the core box
Note: The information on this document is subject to change without notice.
版权声明
本文为[leiditech]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230403229249.html
边栏推荐
- FAQ of foreign lead and alliance Manager
- 第四章 --- 了解标准设备文件、过滤器和管道
- [timing] empirical evaluation of general convolution and cyclic networks for sequence modeling based on TCN
- Common string processing functions in C language
- [pytoch foundation] torch Split() usage
- 单片机串口数据处理(2)——uCOSIII+循环队列接收数据
- Introduction to Cortex-M3 register set, assembly language and C language interface
- IDE idea automatic compilation and configuration of on update action and on frame deactivation
- Basic use of shell WC (counting the number of characters)
- 兼容NSR20F30NXT5G的小体积肖特基二极管
猜你喜欢
![[echart] Introduction to echart](/img/40/e057f4ac07754fe6f3500f3dc72293.jpg)
[echart] Introduction to echart

The 14th issue of HMS core discovery reviews the long article | enjoy the silky clip and release the creativity of the video
Detailed explanation of life cycle component of jetpack

协程与多进程的完美结合

Matlab minimalist configuration of vscode configuration

Jetpack 之 LifeCycle 组件使用详解

How to regulate intestinal flora? Introduction to common natural substances, probiotics and prebiotics
指纹Key全国产化电子元件推荐方案
无线键盘全国产化电子元件推荐方案
Nature medicine reveals individual risk factors of coronary artery disease
随机推荐
Error occurs when thymeleaf th: value is null
Experience summary and sharing of the first prize of 2021 National Mathematical Modeling Competition
[AI vision · quick review of today's sound acoustic papers, issue 3] wed, 20 APR 2022
【论文阅读】【3d目标检测】Voxel Transformer for 3D Object Detection
How to regulate intestinal flora? Introduction to common natural substances, probiotics and prebiotics
IEEE Transactions on industrial information (TII)
Coinbase: basic knowledge, facts and statistics about cross chain bridge
2019 is coming to an end, the longest day.
[echart] démarrer avec echart
Common string processing functions in C language
Go reflection rule
2021数学建模国赛一等奖经验总结与分享
Go反射法则
A lifetime of needs, team collaboration can play this way on cloud nailing applet
Redis 命令大全
智能电子秤全国产化电子元件推荐方案
Go reflection - go language Bible learning notes
协程与多进程的完美结合
MYSQL50道基础练习题
Go 语言中的 logger 和 zap 日志库