当前位置:网站首页>Ways to prevent data fraud
Ways to prevent data fraud
2022-08-09 11:44:00 【Programmer Malatang】
I. Example
Let's look at a classic example of data fraud:
After successful login to some websites, the browser's cookie will set the serviceToken value, and the server can obtain user information through this value.
If the serviceToken is hijacked, others can use your identity to perform various operations.
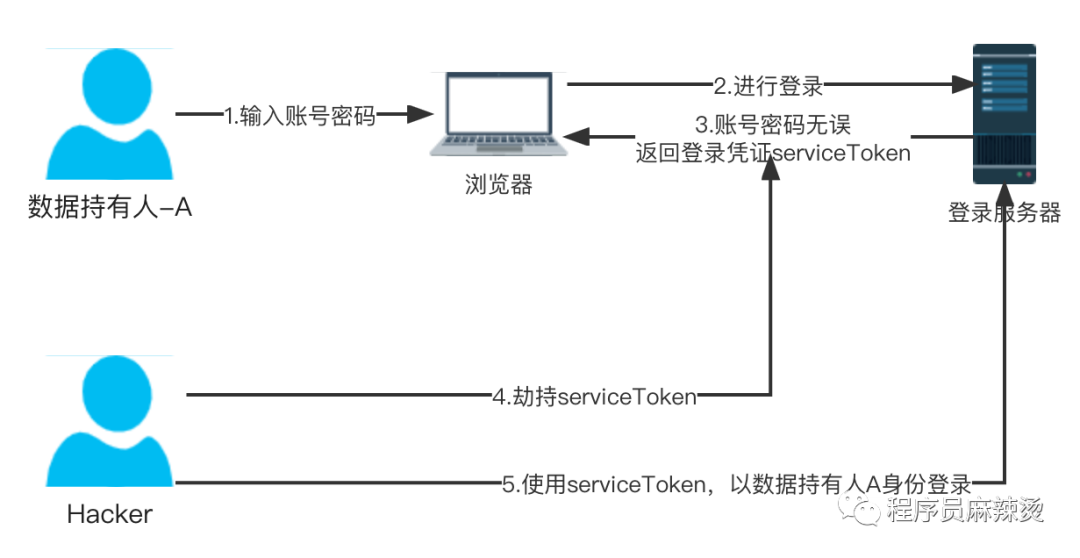
Most scalper software also uses this principle. You do not need to obtain your account password, but only need to obtain the serviceToken, and then use these serviceToken values to perform various operations with your identity.
Is there a solution on the server side to determine that the data sent is really sent by me?
Second, the plan
At the heart of this question is the question of identification: the data really belongs to you!
2.1 Prerequisites
We can take advantage of the capabilities of public and private keys.The realization of this scheme requires:
A public and private key pair is required on the requester
Ensure the security of the private key and the private key will not be leaked
2.2 Flowchart
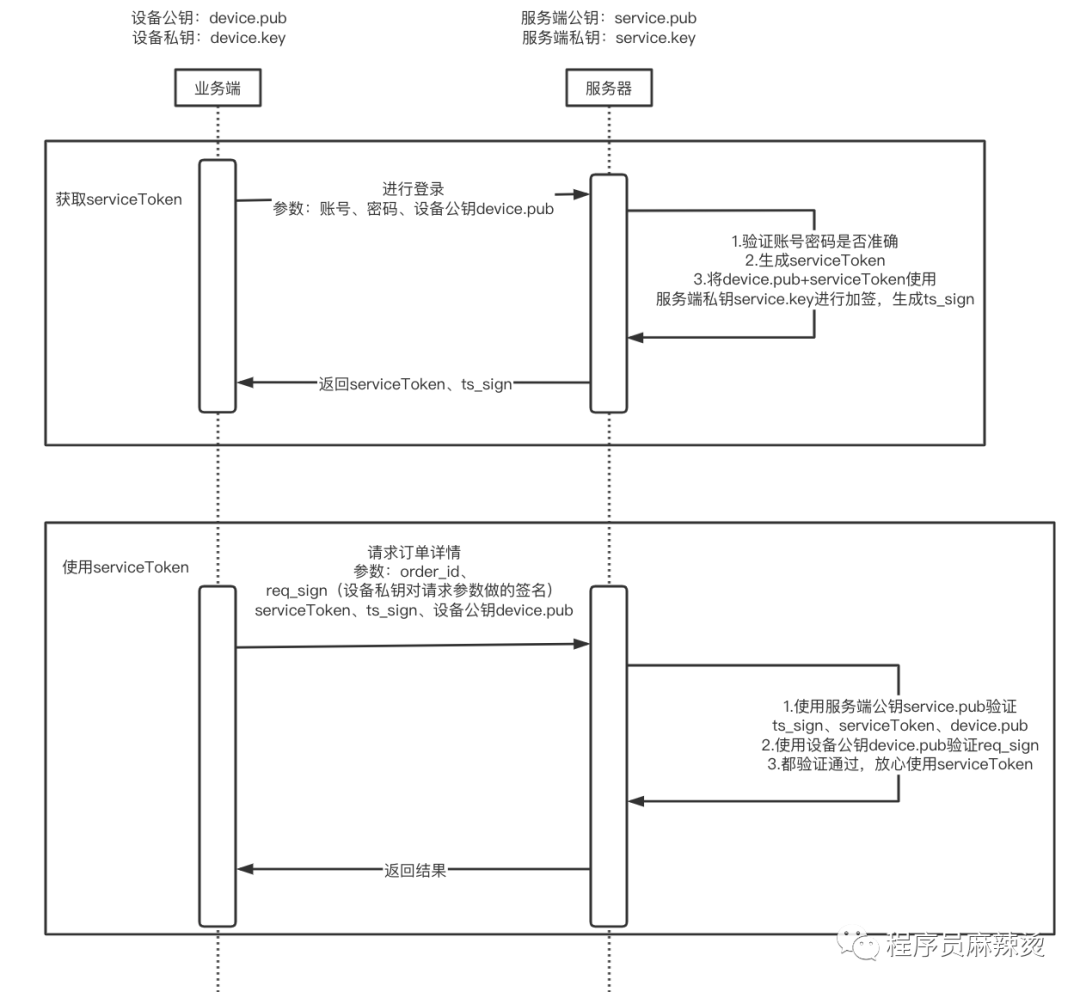
2.3 Description
When obtaining serviceToken, the server uses the server's private key to sign the combination (device public key device.pub and serviceToken), so that the device public key and serviceToken are associated together
When using serviceToken, you need to pass ts_sign and the device public key device.pub. The server uses the server public key to verify whether these three data are legal. If they are legal, it indicates that the server signed theIt is this device public key device.pub and this serviceToken
The last remaining problem to be solved is, how does the server know that this request is initiated by the private key holder?Because the request data uses the device private key device.key to sign req_sign, and uses the passed device public key device.pub to verify the signature. If it passes, it can be confirmed that it is indeed sent by the private key holder
li>
Through this series of derivations, we can achieve the effect of data fraud prevention.
III. Summary
A lot of preconditions are needed to realize this solution, and the complexity of the system has also increased, but it is indeed a very delicate design.What other solutions do you know of to prevent fraudulent use of data?
Last
If you like my articles, you can pay attention to my public account (programmer Malatang)
My personal blog is: https://shidawuhen.github.io/
Review of past articles:
边栏推荐
猜你喜欢
随机推荐
BeanFacroty和FactoryBean到底是什么?AppliacationContext它又是什么?
SQL Server查询优化
Use gdb to debug multi-process programs, debug parent and child processes at the same time
PAT1013 并查集 DFS(查找联通分量的个数)
The use of gdb tui
ACM01背包问题
【DB运营管理/开发解决方案】上海道宁为您提供提高工作便利性的集成开发工具——Orange
This application has no explicit mapping for /error, so you are seeing this as a fallback
PAT1005
gdb tui的使用
fork创建多个子进程
ZOJ1298(单源最短路径)
wpf实现简易画板功能(带截取画板,签名截图等等)
Win10调整磁盘存储空间详解
Paper Sharing | ACL2022 | Argument Relation Extraction Based on Transfer Learning
Semaphore SIGCHLD use, how to make the parent that the child performs over, how to make the distinction between multiple child processes. The end
信号量SIGCHLD的使用,如何让父进程得知子进程执行结束,如何让父进程区分多个子进程的结束
数论知识点
Fapi_StatusType Fapi_issueProgrammingCommand使用注意事项
fork creates multiple child processes
![[工程数学]1_特征值与特征向量](/img/9a/7ed63b86697d6f605d7fc9927496d9)