当前位置:网站首页>Basic understanding of network models
Basic understanding of network models
2022-08-10 03:59:00 【Ignorance Xiaojiu】
边栏推荐
- 从零开始配置 vim(10)——快捷键配置
- [Kali Security Penetration Testing Practice Course] Chapter 9 Wireless Network Penetration
- 单体架构应用和分布式架构应用的区别
- MySQL: What MySQL optimizations have you done?
- MySQL: Introduction to Logging System | Error Log | Query Log | Binary Log: Bin-log Data Recovery Practice | Slow Log Query
- 如何使用腾讯字体,已经在什么场合下可以使用该字体?TTTGB-Medium
- flutter 每天一背,需要掌握
- 嵌入式分享合集32
- 小程序wxs
- 【每日一题】大佬们进来看看吧
猜你喜欢

实测办公场景下,国产远程控制软件的表现力如何?(技术解析)
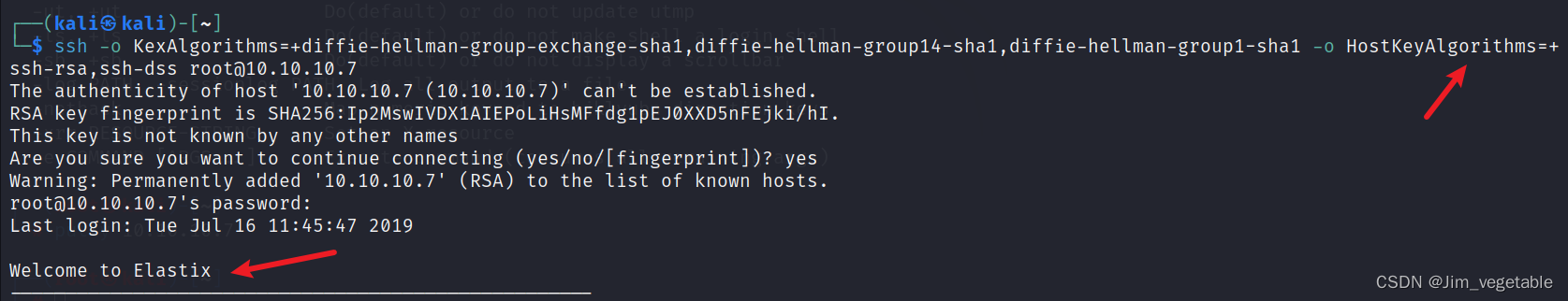
HackTheBox——Beep

nodejs 时钟案例(fs模块),重复使用fs.writeFile方法,旧内容会被覆盖
![[Red Team] ATT&CK - Self-starting - Self-starting mechanism using LSA authentication package](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[Red Team] ATT&CK - Self-starting - Self-starting mechanism using LSA authentication package
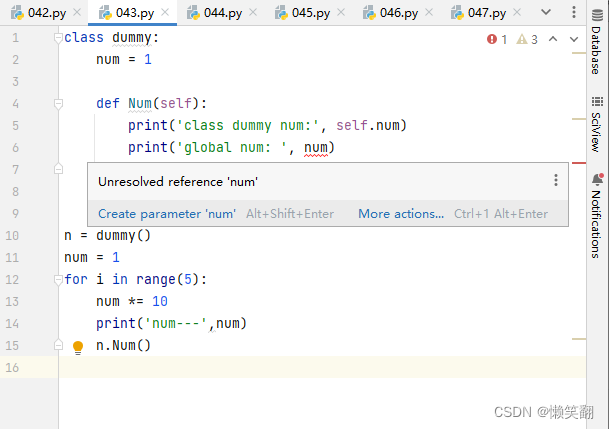
实例043:作用域、类的方法与变量
一个刚入行的测试员怎么样做好功能测试?测试思维真的很重要
![[Kali Security Penetration Testing Practice Course] Chapter 8 Web Penetration](/img/5f/907057956658a19306da21c71185ea.png)
[Kali Security Penetration Testing Practice Course] Chapter 8 Web Penetration

金融口译,口译中金融高频词有哪些
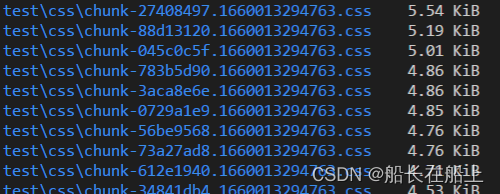
vue项目 npm run build 打包项目防止浏览器缓存
liunx PS1 settings
随机推荐
[Red Team] ATT&CK - Auto Start - Registry Run Key, Startup Folder
2022.8.9 Exam arrangement and transformation--1200 questions solution
excel高级绘图技巧100讲(二十三)-Excel中实现倒计时计数
Robust Real-time LiDAR-inertial Initialization(实时鲁棒的LiDAR惯性初始化)论文学习
2022.8.8 exam sweeps the horse (sweeper) antithesis
proxy代理服务
[Semantic Segmentation] 2022-HRViT CVPR
(面试加分新技能) 总结11个ES2022中你可能遗漏的语法
实例044:矩阵相加
6 common plugin recommendations in Pycharm
Chapter 21 Source Code File REST API Reference (3)
论文理解:“PIAT: Physics Informed Adversarial Training for Solving Partial Differential Equations“
Arrays类
【每日一题】大佬们进来看看吧
Anchor_generators.py analysis of MMDetection framework
MongoDB 常用查询语句
2022.8.8 Exam written in memory (memory)
HackTheBox——Beep
[Red Team] ATT&CK - Self-starting - Self-starting mechanism using LSA authentication package
[Kali Security Penetration Testing Practice Course] Chapter 8 Web Penetration