当前位置:网站首页>CISSP certified daily knowledge points (April 14, 2022)
CISSP certified daily knowledge points (April 14, 2022)
2022-04-23 18:18:00 【Tang Junfei - Mingxue Online】
The following knowledge points are derived from CISSP Official study guide Flash CARD)
---------------
【 Knowledge point 】1
Q:What is the threat posed by ransomware?
ask : What is the threat of blackmail Software ?
A:Ransomware uses traditional malware techniques to infect a system and then encrypts data on that system using a key known only to the attacker. The attacker then demands payment of a ransom from the victim in exchange for providing the decryption key.
answer : Blackmail software uses traditional malware technology to infect the system , Then encrypt the data on the system with a key that only the attacker knows . then , The attacker demanded ransom from the victim , In exchange for providing a decryption key .
【 Knowledge point 】2
Q:What forms of backup always set the archive bit to 0?
ask : What form of backup always sets the archive bit to 0?
A:Full and incremental
answer : Full backup and incremental backup
【 Knowledge point 】3
Q:Name five generic terms that refer to mobile phones, tablets, and other similar devices.
ask : List five general terms , They refer to mobile phones 、 Tablets and other similar devices .
A:A device owned by an individual can be referenced using any of these terms: portable device, mobile device, personal mobile device (PMD), personal electronic device or portable electronic device (PED), and personally owned device (POD).
answer : Personal owned devices can be referenced using any of the following terms : Portable devices 、 Mobile devices 、 Personal mobile devices (PMD)、 Personal electronic device or portable electronic device (PED) And personal owned equipment (POD).
---------------
More knowledge points can be entered into wechat learning discussion group , Add Mingxue online assistant vx:maxstu_com, Get and join .
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610263692.html
边栏推荐
- word frequency count
- The vivado project corresponding to the board is generated by TCL script
- Robocode tutorial 8 - advanced robot
- WIN1 remote "this may be due to credssp encryption Oracle correction" solution
- Multifunctional toolbox wechat applet source code
- Correct opening method of option
- Stm32mp157 wm8960 audio driver debugging notes
- 消费者灰度实现思路
- NVIDIA Jetson: GStreamer and openmax (GST OMX) plug-ins
- powerdesigner各种字体设置;preview字体设置;sql字体设置
猜你喜欢
Docker 安裝 Redis
Function recursion and solving interesting problems
Map basemap Library
From source code to executable file
Robocode Tutorial 4 - robocode's game physics
![[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (2)](/img/91/3272d5ad04cd1d8476c739546f4356.png)
[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (2)
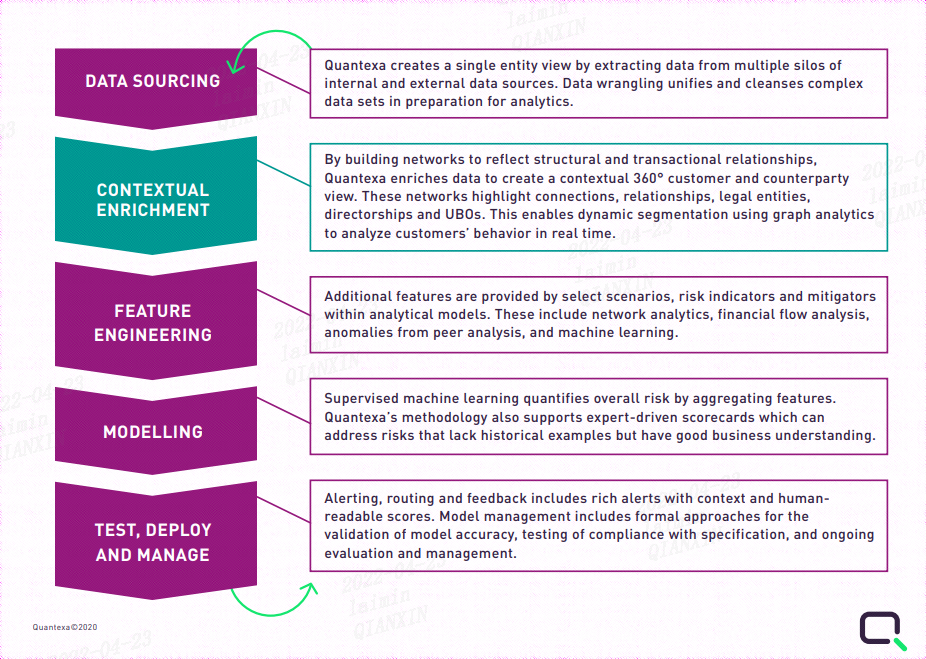
Quantexa CDI(场景决策智能)Syneo平台介绍
JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
Nodejs installation
STM32 learning record 0008 - GPIO things 1
随机推荐
mysql自动启动设置用Systemctl start mysqld启动
Robocode tutorial 8 - advanced robot
Custom prompt box MessageBox in QT
The difference between deep copy and shallow copy
[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (1)
Excel opens large CSV format data
Selenium + webdriver + chrome realize Baidu to search for pictures
proxy server
Multi thread crawling Marco Polo network supplier data
【ACM】376. 摆动序列
Quantexa CDI(场景决策智能)Syneo平台介绍
Format problems encountered in word typesetting
Serialization scheme of serde - trust
Install pyshp Library
MATLAB小技巧(6)七种滤波方法比较
Notepad + + replaces tabs with spaces
Ionic 从创建到打包指令集顺序
Correct opening method of option
According to the result set queried by SQL statement, it is encapsulated as JSON
Pointers in rust: box, RC, cell, refcell