当前位置:网站首页>DNS cloud school | analysis of hidden tunnel attacks in the hidden corner of DNS
DNS cloud school | analysis of hidden tunnel attacks in the hidden corner of DNS
2022-04-23 20:15:00 【National Engineering Research Center】
DNS It's a web service portal , It is the only way for all business visits . Normal business needs to pass DNS Access the service , Malicious programs also need to pass DNS Outreach . data display , near 91.3% Malicious programs were found to use DNS As the main means of invasion . This is because DNS The fragility of the protocol itself makes it easy to be used , And the attacker can hide himself well .DNS Tunnel attack is one of the attack methods often used by attackers , Analysis of cloud school in this issue DNS The principle of tunnel attack , Share the basic ideas for judging tunnel attacks ,enjoy:
One 、DNS Principle and characteristics of tunnel attack

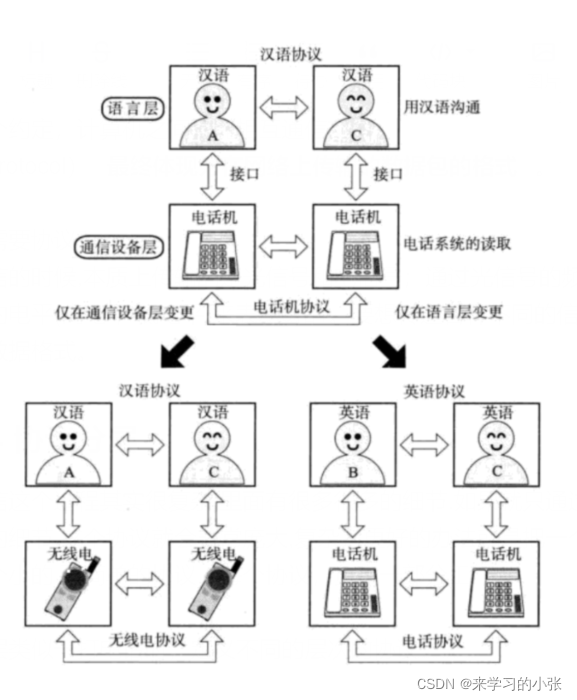
Schematic diagram of basic principle
-
DNS Overview of tunnel attack principle
utilize DNS The query process , Encapsulate illegal data compression coding in DNS Agreement , And then to DNS Request and response packets complete the transmission of data ( signal communication ).
-
DNS Application of tunnel attack
Through C&C The server completes point-to-point data propagation , Or implant a Trojan horse 、 worm 、 Malware, etc. complete long-term hidden APT attack .
-
DNS The advantages of tunnel attack
For traditional safety equipment , Such as network firewall, it has strong penetration ;DNS The cost of attack is relatively low , But the attack effect is obvious .
-
DNS Tunnel attack features
The attacker's traffic data is encapsulated in DNS Agreement , Traditional safety equipment is difficult to find , From the perspective of traffic packets, it is not easy to identify , No professional analysis will only be considered 53 port DNS data , Concealment is strong .
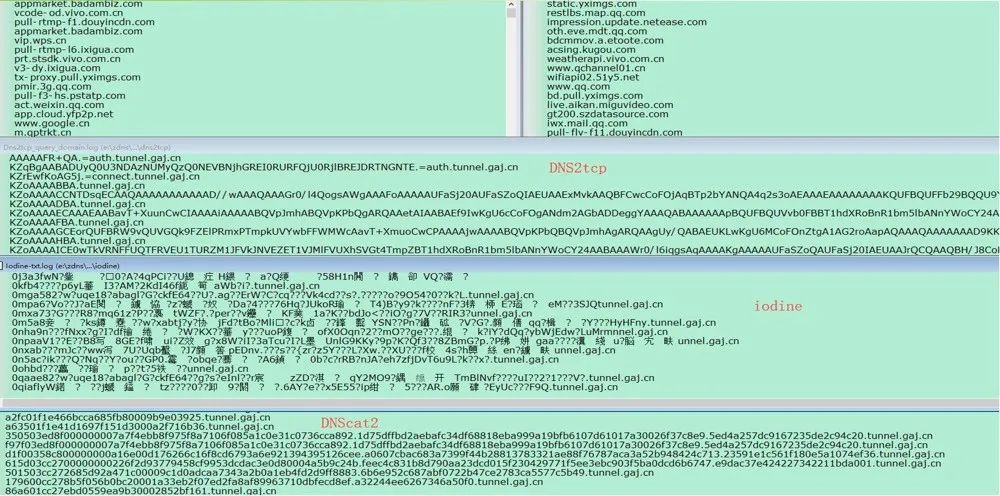
Two 、 utilize DNS Tunnel attack example
-
adopt DNS The tunnel realizes data transmission
A malicious program encapsulates control instructions in DNS Request and response interaction in the protocol , The real control instructions in the request and response are encoded into a string .

Generally, the domain name that initiates the request is Base64,Binary code ,NetBios code 、Hex Code and other coding methods for encryption , In order to transmit more data, generally TXT type (DNS A type of request ). Therefore, it is difficult to consider that firewall and intrusion detection equipment are in normal recursive out of the network DNS Flow analysis and filtration , therefore , Attackers can use it to achieve attacks such as remote control .
-
adopt DNS The tunnel realizes data transmission

DNS In addition to enabling malicious programs and C&C Control instruction interaction at the end , It can also provide an always available rear tunnel for attackers to disclose stolen data or sensitive data . Although limited by the length of the domain name , as well as UDP Unreliability of transmission , utilize DNS It is difficult for the tunnel to transmit large documents to the outside , But transmitting important and sensitive information is enough . The above figure shows that it is transmitted to the control end through continuous subdomain request , Then, at the control end, these requests are spliced together in order to obtain sensitive data .

Pass... In the test environment Wireshark And other packet capture tools , It can be seen that DNS Tunnel file transfer DNS The message interaction process has the following characteristics : Request a series of super long random subdomains 、 The requested domain name contains a serial number 、 High frequency access to the same parent domain 、 The request response packet is large 、 Faster request frequency 、DNS Traffic surge .
3、 ... and 、DNS Tunnel attack judgment and analysis method
at present ,DNS Tunnel technology has been very mature , There are many related tools , And different tools have their own characteristics . At present, the more active ones are iodine,dnscat2, Others are DeNise,dns2tcp,Heyoka wait .
Through the previous introduction , It's not hard to see DNS Tunnel attack has a strong camouflage . But they all have one thing in common —— The request and response look strange ; So how do we detect ? So , in the light of DNS Principle and characteristics of tunnel attack , We sorted out the ideas and methods of judging the attack :
① Comparative analysis of modeling features
Let's take a look at modeling and comparing the following features :
-
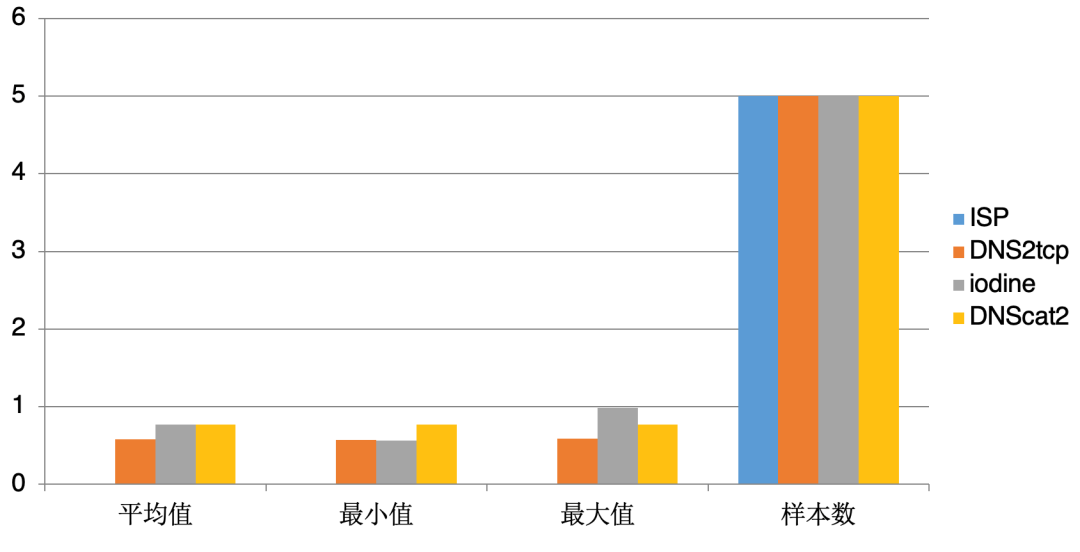
Domain name length 、 Legal characters of domain name 、 domain name RFC The rules , Modeling feature comparison
-
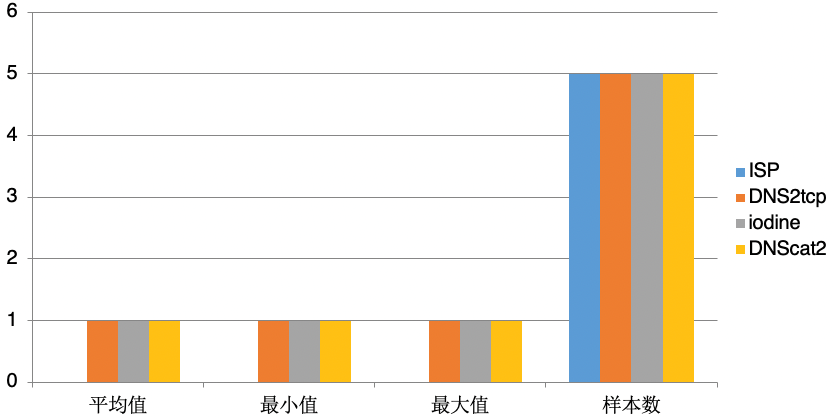
Proportion of uplink large packet in request message , Modeling feature comparison
-
The proportion of downlink packets in the total number of response messages , Modeling feature comparison
-
Information entropy , Modeling feature comparison
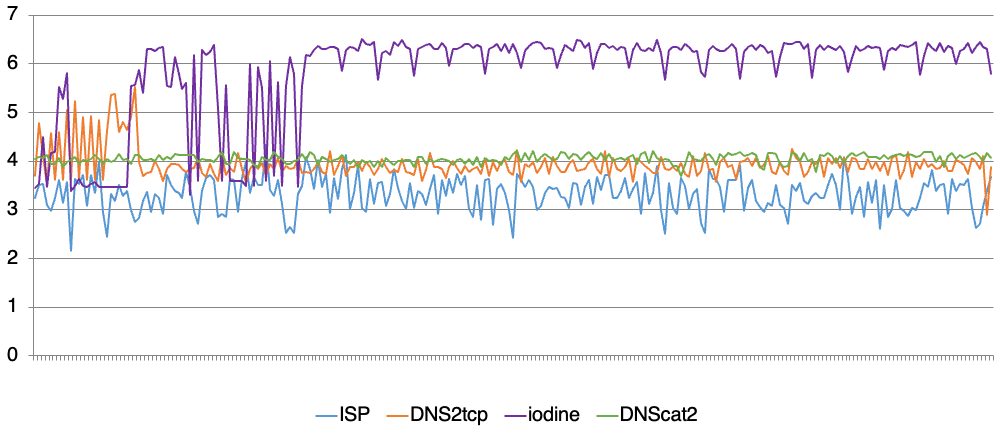
② Critical value of characteristic analysis
Through our modeling and analysis of different scenarios , It's not hard to find that we can target DNS Some characteristics of tunnel flow are summarized, namely “ critical value ”, For example, domain name label String length 52、 Legal characters of domain name a-z, A-Z, 0-9、 Upload and download ratio %500; At the same time, the total number of session messages is greater than 20 Wait a minute . By targeting DNS For the detection of tunnel flow, we can achieve certain effective defense by matching the critical value .
In addition, we can also learn from other DNS Carry features 、 Flow analysis and other aspects, so as to achieve the effect of protection .

Four 、 Conclusion
DNS Tunnel is an important for network attackers “ Commit crime ” methods , At present, there are many public or undisclosed tools . In the traditional means of safety protection , Not for DNS Traffic protection strategy , Boundary devices usually target 53 Port traffic release , therefore , If the DNS The flow is not subject to any supervision , It is very likely that DNS Safety protection , Make the safety system that enterprises spend a lot of money to build become “ Achilles' Heel ”.
This article is only for DNS The principle and basic analysis and judgment of tunnel attack 、 Protection is briefly introduced , Deeper targeted strategies also need to be summarized from practice . Today's sharing is here , If you have any questions about DNS Other problems with tunnel attacks , Welcome to leave a message at the bottom of the article , We will arrange professional engineers to answer your questions , Next stage 《DNS Cloud school 》 Let's see each other !
版权声明
本文为[National Engineering Research Center]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210554571159.html
边栏推荐
- 腾讯邱东洋:深度模型推理加速的术与道
- redis 分布式锁
- R语言使用econocharts包创建微观经济或宏观经济图、indifference函数可视化无差异曲线、自定义计算交叉点、自定义配置indifference函数的参数丰富可视化效果
- Mfcc: Mel frequency cepstrum coefficient calculation of perceived frequency and actual frequency conversion
- PCL点云处理之直线与平面的交点计算(五十三)
- Mysql database backup scheme
- Comment créer un pass BEP - 20 sur la chaîne BNB
- Vericrypt file hard disk encryption tutorial
- 考研英语唐叔的语法课笔记
- How to create bep-20 pass on BNB chain
猜你喜欢
CVPR 2022 | querydet: use cascaded sparse query to accelerate small target detection under high resolution
【文本分类案例】(4) RNN、LSTM 电影评价倾向分类,附TensorFlow完整代码

CVPR 2022 | QueryDet:使用级联稀疏query加速高分辨率下的小目标检测
Unity general steps for creating a hyper realistic 3D scene
MySQL advanced lock - overview of MySQL locks and classification of MySQL locks: global lock (data backup), table level lock (table shared read lock, table exclusive write lock, metadata lock and inte
Shanda Wangan shooting range experimental platform project - personal record (V)
波场DAO新物种下场,USDD如何破局稳定币市场?
山东大学软件学院项目实训-创新实训-网络安全靶场实验平台(六)

山东大学软件学院项目实训-创新实训-网络安全靶场实验平台(五)
网络通信基础(局域网、广域网、IP地址、端口号、协议、封装、分用)
随机推荐
How does onlyoffice solve no route to host
AQS learning
Efficient serial port cyclic buffer receiving processing idea and code 2
Vericrypt file hard disk encryption tutorial
R语言survival包coxph函数构建cox回归模型、ggrisk包ggrisk函数和two_scatter函数可视化Cox回归的风险评分图、解读风险评分图、基于LIRI数据集(基因数据集)
山东大学软件学院项目实训-创新实训-网络安全靶场实验平台(六)
Remote code execution in Win 11 using wpad / PAC and JScript
Mysql database - single table query (III)
Use test of FFT and IFFT library functions of TI DSP
Database query - course selection system
DTMF双音多频信号仿真演示系统
R language ggplot2 visual facet_wrap, and use the lineheight parameter to customize the height of the facet icon tab (gray label bar)
php参考手册String(7.2千字)
selenium.common.exceptions.WebDriverException: Message: ‘chromedriver‘ executable needs to be in PAT
考研英语唐叔的语法课笔记
redis 分布式锁
Devops integration - environment variables and building tools of Jenkins service
SIGIR'22 "Microsoft" CTR estimation: using context information to promote feature representation learning
Five minutes to show you what JWT is
MySQL数据库 - 连接查询