当前位置:网站首页>BUUCTF MISC brush notes (2)
BUUCTF MISC brush notes (2)
2022-08-09 08:41:00 【z.volcano】
BUUOJ
Misc
[WUSTCTF2020]spaceclub
直接用记事本打开txtThe file cannot see the content,所以用notepad打开
It is found that there are several hundred lines of spaces,有长有短
Replace the long with1,Replaced with short0,每8Bit-shift characters,得到flag
f = open("1.txt","r")
flag = ""
for line in f.readlines():
if len(line) == 13:
flag += "1"
else:
flag += "0"
f.close()
for i in range(len(flag)//8):
print(chr(int(flag[8*i:(i+1)*8],2)),end="")
派大星的烦恼
Pai Daxing has been very troubled recently,Because of a scar on its butt!We took a picture of its ass16位位图,0x22,0x44Two cells representing the scar,0xf0It is Pai Daxing's fat.restore scars,Know who beat the big star!(答案为32A string of bits) 注意:得到的 flag 请包上 flag{} 提交
给了一个bmp图片,提示中提到了0x22和0x44,010打开图片,搜索一下发现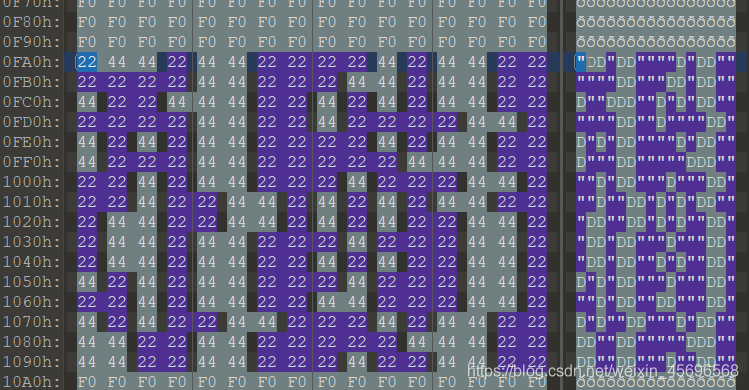
这里有:
"DD"DD""""D"DD""""""DD"""DD"DD""D""DDD""D"D"DD""""""DD""D""""DD"D"D"DD""""D"DD""D"""DD"""""DDD""""D"DD"""D"""DD"""D""DD"D"D"DD"""DD""DD"D"D""DD""DD"DD"""D"""DD""DD"DD""D"D""DD"D"D"DD"""D"""DD"""D"DD""DD"""DD"D"D""DD"""D"DD""DD""DD"""""DDD""DD""DD"""D""DD""
把"换成0,D换成1,Get a string of length 256的二进制,因为256/8=32,而最后的flag长度正好是32
0110110000101100000011000110110010011100101011000000110010000110101011000010110010001100000111000010110001000110001001101010110001100110101001100110110001000110011011001010011010101100010001100010110011000110101001100010110011001100000111001100110001001100
Try each directly8Bit-to-string,发现乱码了…
一番尝试后,Discovery needs to be reversed as a whole,再转字符,to get a normal string,But the commit fails…
In the end, it was found that the results were reversed again…
flag="0110110000101100000011000110110010011100101011000000110010000110101011000010110010001100000111000010110001000110001001101010110001100110101001100110110001000110011011001010011010101100010001100010110011000110101001100010110011001100000111001100110001001100"
flag=flag[::-1]
x=""
for i in range(len(flag)//8):
x += chr(int(flag[8*i:(i+1)*8],2))
print(x[::-1])
[SCTF2019]电单车
拿到一个wav文件,用Audacity打开,观察波形
这里的知识点
对照一下,转换成
0 0111010010101010 0 110 0010 0 011101001010101001100010
空格去掉,套上flag{}即可
hashcat
The download gets a file without a suffix,用winhex打开发现文件头是D0CF11E0,可能是doc、xls、ppt
改后缀为doc,When opening it found that a password was required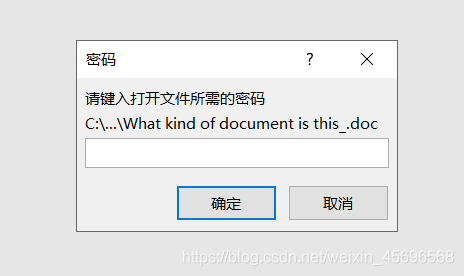
Prompt by title,可以用hashcat爆破密码
不过我有其他工具,用起来会更方便
拿到密码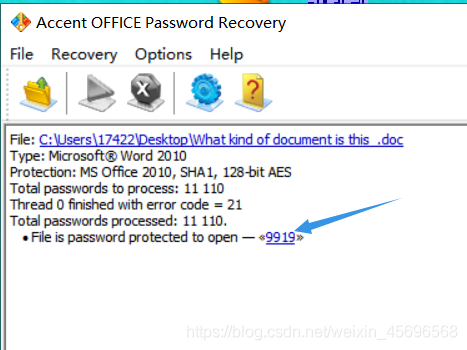
But after opening it gives an error,Try changing the suffix to ppt,成功打开
Found that the seventh page seems to have words
Change the color to get itflag
[UTCTF2020]zero
打开txt,内容如下
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Phasellus quis tempus ante, nec vehicula mi. Aliquam nec nisi ut neque interdum auctor. Aliquam felis orci, vestibulum sit amet ante at, consectetur lobortis eros. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. In finibus magna mauris, quis auctor libero congue quis. Duis sagittis consequat urna non tristique. Pellentesque eu lorem id quam vestibulum ultricies vel ac purus.
In fact, when you see the title of this topic, you know what you are investigating零宽字符隐写
winhexOpen to see a lot of zero-width characters,或者直接在linux系统下打开,看的更明显
到在线网站解密,拿到flag
[*CTF2019]otaku

先看这个doc,Because my default is to show hidden text
It is very possible that some text is hidden,So turn on hidden text again,对比一下
Find hidden text is:
Hello everyone, I am Gilbert. Everyone thought that I was killed, but actually I survived. Now that I have no cash with me and I’m trapped in another country. I can’t contact Violet now. She must be desperate to see me and I don’t want her to cry for me. I need to pay 300 for the train, and 88 for the meal. Cash or battlenet point are both accepted. I don’t play the Hearthstone, and I don’t even know what is Rastakhan’s Rumble.
flag.zip是伪加密,Tools can be used to solve or use360Compressed extraction(无视伪加密)
These tips are given,应该是明文攻击,新建一个txt文档,Put the text you got above in it,Compress with the given compression method
不过试了几次,得到的crc值都和last word.txt的不一致
参考师傅们的wp发现,是编码的问题,我这里默认是UTF-8,需要换成GBK
#encoding=GBK
f = open("test.txt", "w")
s="Hello everyone, I am Gilbert. Everyone thought that I was killed, but actually I survived. Now that I have no cash with me and I’m trapped in another country. I can't contact Violet now. She must be desperate to see me and I don't want her to cry for me. I need to pay 300 for the train, and 88 for the meal. Cash or battlenet point are both accepted. I don't play the Hearthstone, and I don't even know what is Rastakhan's Rumble."
f.write(s)
f.close()
Then compress in the same way to start a plaintext attack
After running for a while, you can get the password My_waifu,解压得到flag.png
发现lsb隐写痕迹,然后拿到flag
[湖南省赛2019]Findme
Five pictures are given
1.png
The first picture is weird,The width and height should have been modified,First run the script to blast the width and height,发现是227*453,Get it changed
继续用010分析,发现chunk[2]、chunk[3]缺少IDAT标识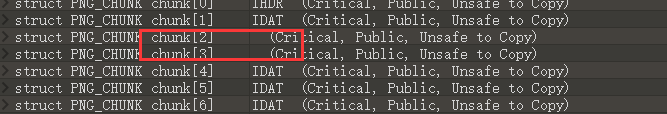
Fill in the mark at the corresponding location
修改保存之后,用Stegsolve打开图片,发现二维码
扫码得到ZmxhZ3s0X3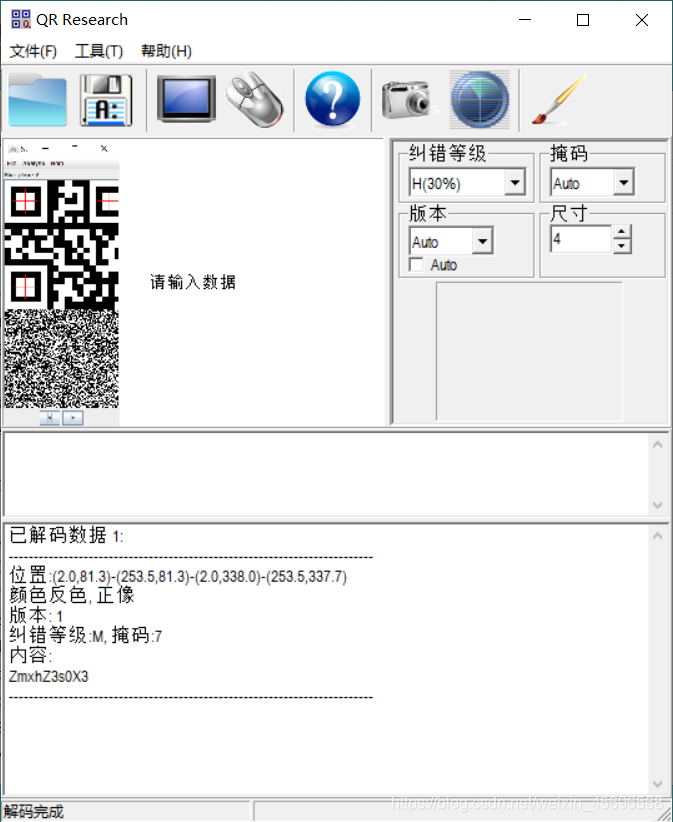
2.png
发现2.pngThere is extra data at the end
Extract this piece of data,保存为7z文件,发现打不开,于是把所有的7z换成PK,保存为zip文件,If you still get an error when you open it, fix it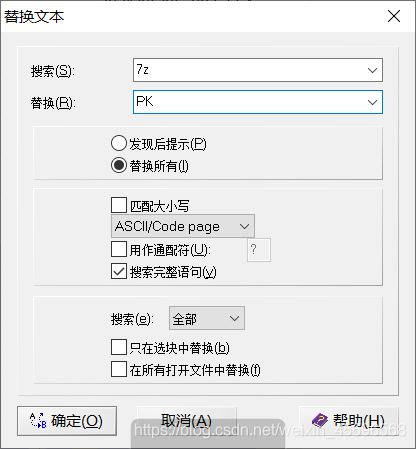
Decompression found a lottxt文件,其中618.txt是特殊的,Check it out1RVcmVfc
3.png
Take note of these blockscrc32The check values are relatively small
把它们提取出来,Convert to decimal and then convert characters,得到3RlZ30=
4.png
given directly:cExlX1BsY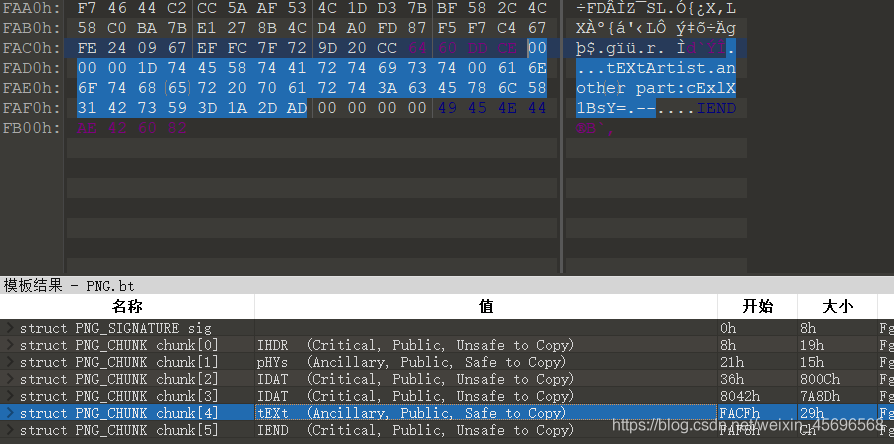
5.png
也是直接给:Yzcllfc0lN
Next is integration,注意到3.png给的base64编码是以=结尾的,Then its corresponding should be placed at the end,1.pngShould be in the first place
最后按照1 5 4 2 3的顺序得到,base64解码得到flag
ZmxhZ3s0X3Yzcllfc0lNcExlX1BsY1RVcmVfc3RlZ30=
Really complicated
Miscellaneous topics are often mixed with weird stuff...不要想歪了!Focus on the question= =!The last thing you get requires violence(提示:前一个字母,后一个数字) 注意:得到的 flag 请包上 flag{} 提交
When I came up, I was molested by the questioner
There is extra data at the end,binwalk提取,There are so many things…
注意到有一个dex文件,使用dex2jar反编译
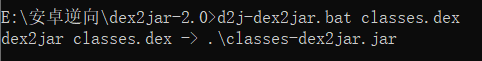
再用jd-gui打开得到的classes-dex2jar.jar,Flip over to seeflag
There are two locations that need to be blasted,最后得到flag{25f991b27fcdc2f7a82a2b34386e81c4}
[QCTF2018]X-man-A face
有个二维码,Two anchor points are missing,用QR扫不出来
两个思路,一个是p图,Complete the anchor point,也可以到在线网站手动补
没啥技术含量,扫码得到KFBVIRT3KBZGK5DUPFPVG2LTORSXEX2XNBXV6QTVPFZV6TLFL5GG6YTTORSXE7I=
base32解码得到flag
voip
一个流量包,用wireshark打开,Simple analysis is fruitless
百度一下看看voip是啥东西
Then click this option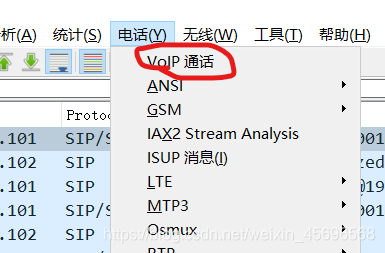

听声音,它会读flag
得到flag{9001IVR}
u1s1,Sounds like a lot of work
边栏推荐
- Routing configuration forwarding and experiment
- elder blind date
- jdbctemplate connects to sql server, the data found in the code is inconsistent with the database, how to solve it?
- 解决iframe跳转时父页面仍然存在的问题
- 电子产品整机结构设计的一般性思路
- 网络层协议介绍
- 数据解析之bs4学习
- QT程序生成独立exe程序(避坑版)
- 加密技术和电子竞技如何促进彼此的发展
- Static routing principle and configuration
猜你喜欢
随机推荐
MySql homework practice questions
数制转换及子网划分
eTS UI开发学习
jdbctemplate连接sql server,代码中查出来的数据跟数据库中不一致,如何解决?
Object detection app based on appinventor and EasyDL object detection API
get一个小技巧,教你如何在typora写文章上传图片到博客上
静态路由原理与配置
leetcode 36. 有效的数独(模拟题)
204. 数素数
App testing
进程和计划任务
解决iframe跳转时父页面仍然存在的问题
Euclid and the game
SAE定时备份博客数据库
正则之re模块
【愚公系列】2022年08月 Go教学课程 033-结构体方法重写、方法值、方法表达式
nyoj306 走迷宫(搜索+二分)
大端小端存储区别一看即懂
Shell programming loop statement and function
leetcode 37. 解数独 (困难)