当前位置:网站首页>CISSP certified daily knowledge points (April 11, 2022)
CISSP certified daily knowledge points (April 11, 2022)
2022-04-23 18:17:00 【Tang Junfei - Mingxue Online】
The following knowledge points are derived from CISSP Official study guide Flash CARD
---------------
【 Knowledge point 】1
Q:What are the benefits of security guards?
ask : What are the benefits of security personnel ?
A:They are able to adapt and react to any condition or situation, are able to learn and recognize attack patterns, can adjust to a changing environment, and are able to make decisions and judgment calls.
answer : They can adapt to any condition or situation and respond , Be able to learn and recognize attack patterns , Able to adapt to the changing environment , Able to make decisions and judgments .
【 Knowledge point 】2
Q:What is a Faraday cage?
ask : What is a Faraday cage ?
A:A Faraday cage is EM blocking enclosure, often a wire mesh that fully surrounds an area on all sides. This metal skin acts as an EMI absorbing capacitor (which is why it's named after Michael Faraday, a pioneer in the field of electromagnetism) that prevents electromagnetic signals (emanations) from exiting or entering the area that the cage encloses.
answer : Faraday cage is an electromagnetic shielding shell , Usually a wire mesh , Completely surround all aspects of an area . This metal shell acts as EMI Absorption capacitor ( That's why it's a pioneer in the field of electromagnetism · Faraday's name is ), Prevent electromagnetic signals ( radiation ) Leave or enter the area surrounded by the cage .
【 Knowledge point 】3
Q:What are key concepts of the Mandatory Access Control (MAC) model?
ask : Enforce access control (MAC) What are the key concepts of the model ?
A:The MAC model uses labels to identify security domains. Subjects need matching labels to access objects. The MAC model enforces the need to know principle and supports a hierarchical environment, a compartmentalized environment, or a combination of both in a hybrid environment. It is frequently referred to as a lattice-based model.
answer :MAC The model uses tags to identify security domains , A matching tag is required to access the object .MAC The model strengthens “ instructions ” principle , And support layered environments in mixed environments 、 Environment or a combination of both . It is often referred to as a lattice based model .
---------------
More knowledge points can be entered into wechat learning discussion group , Add Mingxue online assistant vx:maxstu_com, Get and join .
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610264091.html
边栏推荐
猜你喜欢
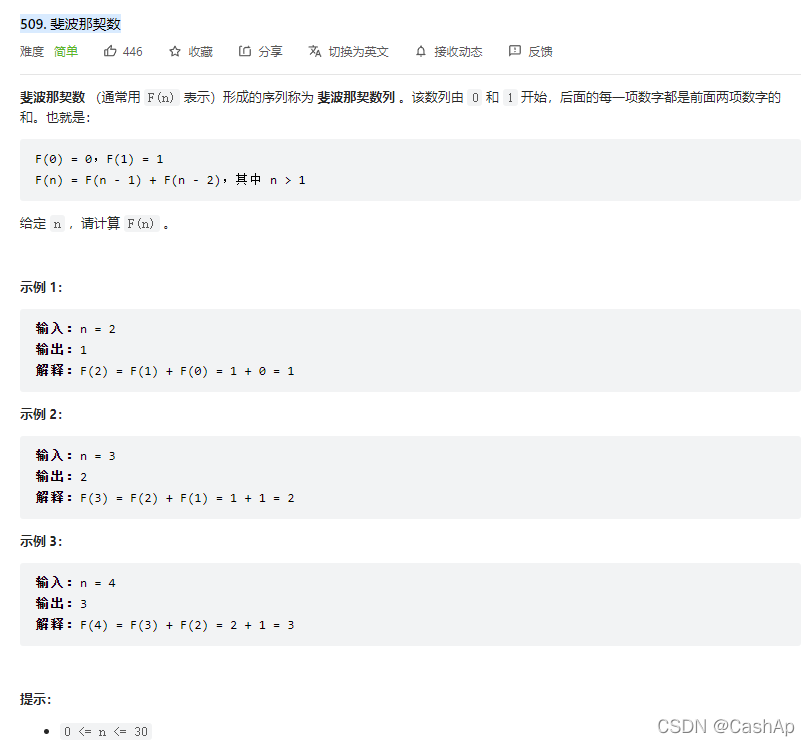
【ACM】509. 斐波那契数(dp五部曲)
Batch export ArcGIS attribute table
Installation du docker redis
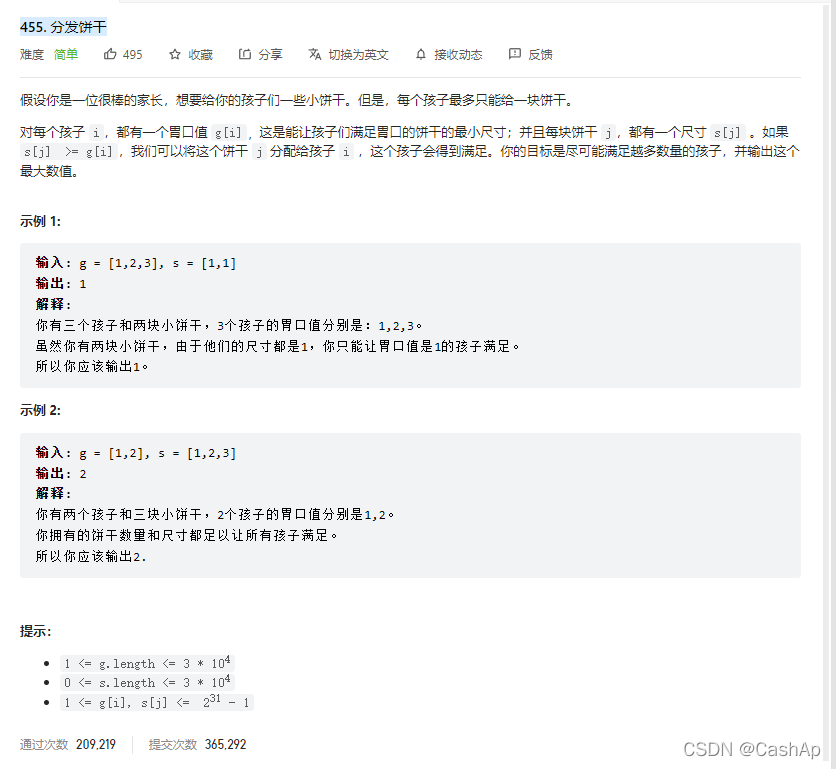
【ACM】455. Distribute Biscuits (1. Give priority to big biscuits to big appetite; 2. Traverse two arrays with only one for loop (use subscript index -- to traverse another array))
Resolves the interface method that allows annotation requests to be written in postman

Solving the problem of displaying too many unique values in ArcGIS partition statistics failed
Robocode tutorial 7 - Radar locking

In win10 system, all programs run as administrator by default
re正則錶達式
JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
随机推荐
Docker 安装 MySQL
Calculation of fishing net road density
STM32学习记录0008——GPIO那些事1
Dock installation redis
【ACM】70. climb stairs
Multi thread crawling Marco Polo network supplier data
Quantexa CDI(场景决策智能)Syneo平台介绍
【ACM】376. Swing sequence
Crawl lottery data
C language to achieve 2048 small game direction merging logic
Solving the problem of displaying too many unique values in ArcGIS partition statistics failed
Visualization of residential house prices
解决允许在postman中写入注释请求接口方法
Robocode Tutorial 4 - robocode's game physics
Cutting permission of logrotate file
Stanford machine learning course summary
Realization of consumer gray scale
7-21 wrong questions involve knowledge points.
Multifunctional toolbox wechat applet source code
positioner