当前位置:网站首页>iptables初探
iptables初探
2022-04-23 18:29:00 【喝醉酒的小白】
一、概念
iptables是Linux下功能强大的防火墙工具,由于它集成于Linux内核,所以效率极高。
二、分类
按照对数据包的操作类别分类,iptables可以分为4个表,按照不同的Hook点可区分为5个链。
其中4个表分别是filter表(用于一般的过滤)、nat表(地址或端口映射)、mangle表(对特定数据包的修改)、raw表,这里面最常用的是filter表;
5个链分别是PREROUTING链(数据包进入路由决策之前)、INPUT(路由决策为本机的数据包)、FORWARD(路由决策不是本机的数据包)、OUTPUT(由本机产生的向外发送的数据包)、POSTROUTING(发送给网卡之前的数据包),最常用的是INPUT、OUTPUT链。
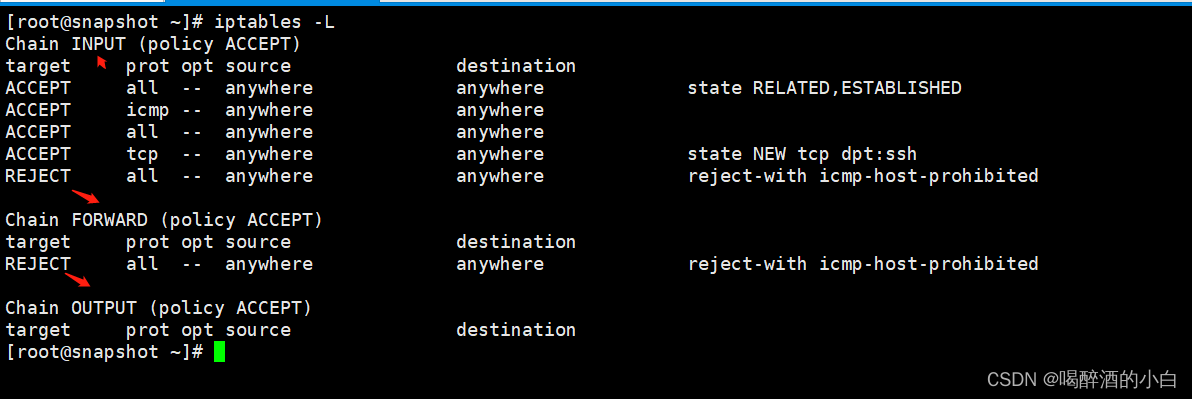
三、工作策略
第一种是仅接受允许的数据,这种策略一般是设置防火墙的默认策略为拒绝所有数据包(也就是拒绝网卡上出入的数据包),然后有针对性地放开特定的访问;第二种是只防止不允许的数据访问请求,这种策略一般是设置防火墙的默认策略为允许所有数据包,只拒绝已知的非法访问数据。从安全效果而言,前一种防火墙策略表现更为优秀/
四、配置规则
#cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT #允许已经建立和相关的数据包进入 / 代表目前已经与本机建立连接的主机,依然保持连接状态
-A INPUT -p icmp -j ACCEPT #在INPUT规则链中添加允许ICMP流量进入
-A INPUT -i lo -j ACCEPT
-A INPUT -i bond0 -s x.x.x.x -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT #允许固定的IP能SSH到该服务器上
-A INPUT -p tcp -m state --state NEW -m tcp --dport 8080 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 80 -j ACCEPT #允许访问80端口
-A INPUT -s x.x.x.x -p tcp -m multiport --dports 80,10011,3000,6379,9307 -j ACCEPT #允许固定的IP能访问该服务器某些端口
-A INPUT -p tcp --dport 3000 -d 127.0.0.1 -j ACCEPT
-A INPUT -p tcp --dport 3000 -j DROP #DROP(丢弃)
-A OUTPUT -p tcp --sport 5900:5930 -j DROP
-A INPUT -j REJECT --reject-with icmp-host-prohibited #REJECT(拒绝)
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
五、直接配置并保存规则
iptables -A INPUT -p tcp -m tcp --dport 80 -j ACCEPT #添加
iptables -D INPUT -p tcp -m tcp --dport 80 -j ACCEPT #清理
iptables -L #查看
保存
service iptables save
重启后永久生效
service iptables restart
六、参考链接
版权声明
本文为[喝醉酒的小白]所创,转载请带上原文链接,感谢
https://blog.csdn.net/hezuijiudexiaobai/article/details/124359382
边栏推荐
- Correct opening method of option
- CISSP certified daily knowledge points (April 13, 2022)
- Ionic instruction set order from creation to packaging
- Matlab tips (6) comparison of seven filtering methods
- MATLAB小技巧(6)七种滤波方法比较
- With the use of qchart, the final UI interface can be realized. The control of qweight can be added and promoted to a user-defined class. Only the class needs to be promoted to realize the coordinate
- Installation du docker redis
- Use of regular expressions in QT
- 硬核解析Promise對象(這七個必會的常用API和七個關鍵問題你都了解嗎?)
- kettle庖丁解牛第17篇之文本文件输出
猜你喜欢
【ACM】455. Distribute Biscuits (1. Give priority to big biscuits to big appetite; 2. Traverse two arrays with only one for loop (use subscript index -- to traverse another array))

PowerDesigner various font settings; Preview font setting; SQL font settings

昇腾 AI 开发者创享日全国巡回首站在西安成功举行
ESP32 LVGL8. 1 - label (style 14)
Excel intercept text
JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
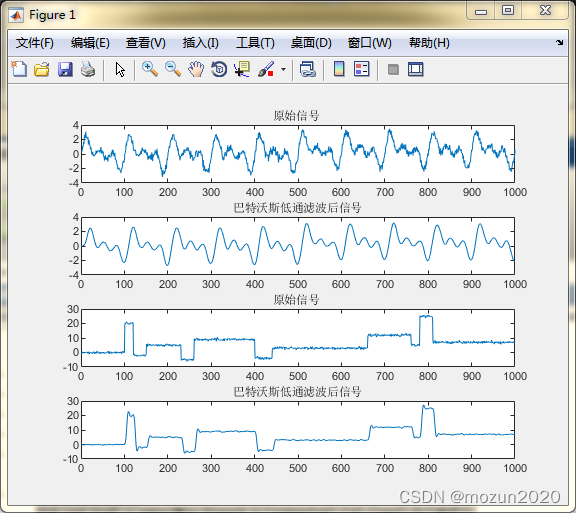
MATLAB小技巧(6)七种滤波方法比较
From source code to executable file
CANopen STM32 transplantation

powerdesigner各种字体设置;preview字体设置;sql字体设置
随机推荐
Gobang game based on pyGame Library
Multi thread safe reference arc of rust
Ionic instruction set order from creation to packaging
函数递归以及趣味问题的解决
昇腾 AI 开发者创享日全国巡回首站在西安成功举行
Interpretation and compilation of JVM
Rust: how to match a string?
According to the result set queried by SQL statement, it is encapsulated as JSON
Matlab tips (6) comparison of seven filtering methods
CISSP certified daily knowledge points (April 13, 2022)
Resolves the interface method that allows annotation requests to be written in postman
Use of regular expressions in QT
14个py小游戏源代码分享第二弹
串口调试工具cutecom和minicom
Software test summary
JD-FreeFuck 京东薅羊毛控制面板 后台命令执行漏洞
Permission management with binary
Mode of interprocess communication
Dynamically add default fusing rules to feign client based on sentinel + Nacos
How to restore MySQL database after win10 system is reinstalled (mysql-8.0.26-winx64. Zip)