当前位置:网站首页>Tun equipment principle
Tun equipment principle
2022-04-23 15:04:00 【Mrpre】
TUN Equipment principle
What this article wants to elaborate is sslvpn Operation mechanism of . Technical refinement of its problems , It is to solve two private networks that are separated by the public network environment , How to establish a channel . The core detail is tun equipment .TUN The device is also used in flannel in , Network communication between containers as a cross host .
simpletun
Let's start with a simple example https://github.com/gregnietsky/simpletun.git Then have an intuitive feeling
Let's find 2 Taiwan machine Separate use make Command to compile the above code , Generate Binary system simpletun
A Physics ip 11.238.116.73
B Physics ip 11.238.116.75
stay B Executed on machine
sudo ./simpletun -i tun90 -s -d &
sudo ifconfig tun90 6.6.6.2/24
stay A Executed on machine
sudo ./simpletun -i tun90 -c 11.238.116.75 -d &
sudo ifconfig tun90 6.6.6.1/24
simpletun Binary will help generate a file called tun90 Virtual network card , And then we use ifconfig To carry out ip Distribution of addresses
secondly ,B On the machine , adopt -s tell simpletun monitor This machine TCP Of 55555 port , And as a server ;A Machine pass -c Command attach B The physical ip.
Once the boot is complete , stay A Executed on machine ping 6.6.6.2 The following log will appear , Some logs are ping Output , Express ping success , Part of it is simpletun Printed logs .
PING 6.6.6.2 (6.6.6.2) 56(84) bytes of data.
TAP2NET 4: Read 84 bytes from the tap interface
TAP2NET 4: Written 84 bytes to the network
NET2TAP 4: Read 84 bytes from the network
NET2TAP 4: Written 84 bytes to the tap interface
64 bytes from 6.6.6.2: icmp_seq=1 ttl=64 time=39.7 ms
TAP2NET 5: Read 84 bytes from the tap interface
TAP2NET 5: Written 84 bytes to the network
NET2TAP 5: Read 84 bytes from the network
NET2TAP 5: Written 84 bytes to the tap interface
64 bytes from 6.6.6.2: icmp_seq=2 ttl=64 time=39.9 ms
alike , We are B Execute above nc -l -k 9090 monitor This machine 9090 Port program , And then again A Execute above nc 6.6.6.2 9090 Rear knock in abc
A Output
$nc 6.6.6.2 9090
TAP2NET 12: Read 60 bytes from the tap interface
TAP2NET 12: Written 60 bytes to the network
NET2TAP 11: Read 60 bytes from the network
NET2TAP 11: Written 60 bytes to the tap interface
TAP2NET 13: Read 52 bytes from the tap interface
TAP2NET 13: Written 52 bytes to the network
abc
TAP2NET 14: Read 56 bytes from the tap interface
TAP2NET 14: Written 56 bytes to the network
NET2TAP 12: Read 52 bytes from the network
NET2TAP 12: Written 52 bytes to the tap interface
B Output
NET2TAP 12: Read 60 bytes from the network
NET2TAP 12: Written 60 bytes to the tap interface
TAP2NET 11: Read 60 bytes from the tap interface
TAP2NET 11: Written 60 bytes to the network
NET2TAP 13: Read 52 bytes from the network
NET2TAP 13: Written 52 bytes to the tap interface
NET2TAP 14: Read 56 bytes from the network
NET2TAP 14: Written 56 bytes to the tap interface
TAP2NET 12: Read 52 bytes from the tap interface
TAP2NET 12: Written 52 bytes to the network
abc
We found that ,A The machine passes through tcp visit 6.6.6.2 Of 9090 port , This 6.6.6.0/24 Equivalent to private network request , and A and B There is no network between 6.6.6.0/24 Route of network segment , that B How to receive A What about the private network request sent , Of course, this is the doubt that we need to explain in this article .
TUN Equipment characteristics
about tun The equipment write operation (open tun, Then on fd Conduct write),tun After the user state data is obtained in the kernel state , call netif_rx, Usually ,netif_rx This function is called and submitted to the protocol stack only when the machine receives the message , Show that we are right tun The equipment write operation , It's equivalent to letting the machine simulate receiving packets . So the key point is ,tunwrite The data must contain three protocol headers (IP), otherwise linux The protocol stack cannot route it .
about tun Data acquisition operation of the device , First tun Under what circumstances does the equipment , Will get the data ? That is, when we have no perception in external applications tun In the presence of equipment ,tun How does the device get data from external programs .
First tun The equipment has three layers ip Address of the , Which means ,tun The device can be used as a three-layer forwarding interface to send data , We just need to let External procedures Requests made , Be routed to tun Equipment can . for example We visit 200.100.1.1 This public network address goes tun equipment ,route add -net 200.100.1.1/32 dev tun90, So the request will go tun Go out .
then tun The equipment The driver and Conventional similar eth Different , It doesn't really send data from its own interface .
tun The sending interface of the device , The operation is to data Save it and put it in your list On , Then notify the listener tun The user program of the device reads .
So I want to TUN Intercepted data , Then you need the destination address of the application , Can from TUN Equipment port “ get out ”, Configuring a route is a common operation .
Be careful tun Data acquired by the device , When carrying the data of the three-tier head .
TUN practice
The above explanation says TUN The characteristics of the device , All features are TUN Character driver and device driver implementation , We combine this feature , You can make a simple private network traversal function , That's the beginning simpletun The function of
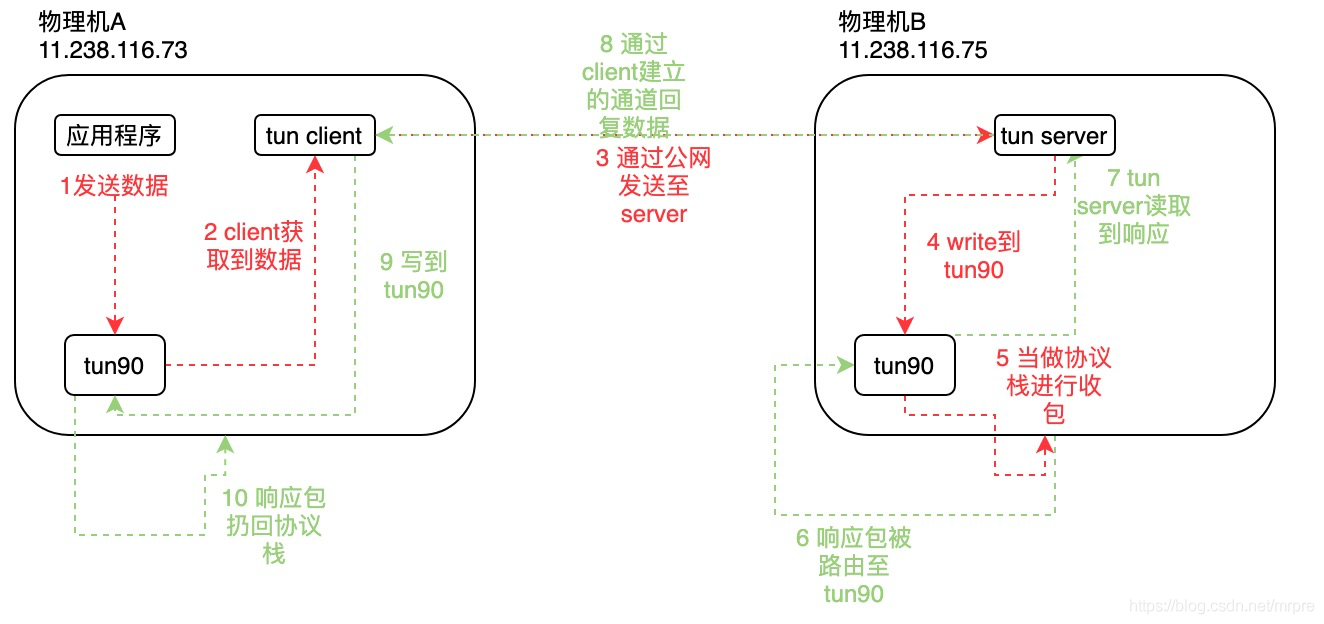
Request to send
1、 Applications send data , for example ping To 6.6.6.2, Because of the routing and other rules configured locally , The data is linux The kernel routes to tun90 Send .
2、tun90 After getting the data , There will be no real sending operation ,, Instead, it is encapsulated into three-tier messages , Then put it in your own queue , Wait for the user program to read , This is it. tun The characteristics of the device .
here tun client Will get the data . Data is data that contains three-tier headers , One of the sources ip yes tun The equipment 6.6.6.1 The destination address is the destination address accessed by the application 6.6.6.2.
3、tun client take This contains three-tier header data , Send through the public network , natural The five tuples on this public network are the local physical address and the destination physical address , Naturally, this message can be sent through the public network .
4、tun server received data , The data is The previous step 2 Data in , Contains 6.6.6.1->6.6.6.2 The data of this three-tier header ,tun server writes tun equipment .
5、tun90 Received from the user write After the operation , Will throw data into linux Protocol stack ,linux The protocol stack will parse 6.6.6.1->6.6.6.2 How to forward the data of the three-tier header , natural 6.6.6.2 Is your local address , Nature can handle .
Be careful 1 Sending of , the truth is that tun The equipment xmit send out ,4 Of write the truth is that tun The equipment receive, It's different .
This example is only based on PING As an example . If The physical machine A Of Applications What I visited was One The address of the public network , for example 100.100.100.100, that , The physical machine B If it's on ip_forward And myself and 100.100.100.100 through , that , The request is forwarded to 100.100.100.100, Turn on nat Under the circumstances , Will send to the public network 11.238.116.75 -> 100.100.100.100 Request , The response data 100.100.100.100->11.238.116.75 Come back and rely on nat restore 100.100.100.100->6.6.6.1.
Data response
The back package is also very interesting
6、 hypothesis machine B To reply 6.6.6.1->6.6.6.2 PING Corresponding Response package , So the machine B The response of IP The head is 6.6.6.2->6.6.6.1, This packet will be routed to the machine tun90, This process is equivalent to the above sending process 1,tun90 After intercepting this packet , expect tun server Read it .
7、tun server Detected tun The device has data , So I read the data , The data contains 6.6.6.2->6.6.6.1 This ip Header data .
8、tun server Use tun client Established access , Transmit data to via the public network client.
9、tun client Writes data to machine A Of tun.
10、 according to tun characteristic ,tun Opportunity will contain 6.6.6.2->6.6.6.1 This ip Header data The data will be thrown into the protocol stack ,linux can such , Externally executed ping You can get the response data .
版权声明
本文为[Mrpre]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231409587869.html
边栏推荐
- Detailed explanation of C language knowledge points -- first understanding of C language [1] - vs2022 debugging skills and code practice [1]
- Set up an AI team in the game world and start the super parametric multi-agent "chaos fight"
- Basic operation of sequential stack
- Leetcode167 - sum of two numbers II - double pointer - bisection - array - Search
- Borui data and F5 jointly build the full data chain DNA of financial technology from code to user
- Little red book timestamp2 (2022 / 04 / 22)
- Progress in the treatment of depression
- C语言超全学习路线(收藏让你少走弯路)
- Detailed comparison between asemi three-phase rectifier bridge and single-phase rectifier bridge
- Basic operation of circular queue (Experiment)
猜你喜欢
Programming philosophy - automatic loading, dependency injection and control inversion

如何设计一个良好的API接口?

What is the main purpose of PCIe X1 slot?
We reference My97DatePicker to realize the use of time plug-in

Swift - literal, literal protocol, conversion between basic data types and dictionary / array
win10 任务栏通知区图标不见了
三、梯度下降求解最小θ
LeetCode162-寻找峰值-二分-数组

How to design a good API interface?
Redis主从同步
随机推荐
Ffmpeg installation error: NASM / yasm not found or too old Use --disable-x86asm for a clipped build
Set onedrive or Google drive as a drawing bed in upic for free
epoll 的EPOLLONESHOT 事件———实例程序
One of the advanced applications of I / O reuse: non blocking connect -- implemented using select (or poll)
epoll 的 ET,LT工作模式———实例程序
8.5 concise implementation of cyclic neural network
Select receives both normal data and out of band data
thinkphp5+数据大屏展示效果
Detailed analysis of SQL combat of Niuke database (26-30)
Detailed comparison between asemi three-phase rectifier bridge and single-phase rectifier bridge
Little red book timestamp2 (2022 / 04 / 22)
January 1, 1990 is Monday. Define the function date_ to_ Week (year, month, day), which realizes the function of returning the day of the week after inputting the year, month and day, such as date_ to
[stc8g2k64s4] introduction of comparator and sample program of comparator power down detection
解决computed属性与input的blur事件冲突问题
How to write the keywords in the cover and title? As we media, why is there no video playback
JUC learning record (2022.4.22)
Swift - literal, literal protocol, conversion between basic data types and dictionary / array
LeetCode165-比较版本号-双指针-字符串
js——实现点击复制功能
8.4 realization of recurrent neural network from zero