当前位置:网站首页>Analysis of the Status Quo of Enterprise Server Host Reinforcement
Analysis of the Status Quo of Enterprise Server Host Reinforcement
2022-08-11 08:12:00 【Cnsidna.No.1】
Current status
Whether it is a small and medium-sized enterprise or a large-scale enterprise or institution, each has its own intranet or public cloud server.Some of these servers are dedicated SVN and GIT code servers, some are document storage servers, and some are application servers.The server is the core lifeblood of an enterprise, and all intellectual property rights and years of hard work are concentrated on the server.However, the existing servers only take traditional security measures, such as deploying anti-virus software, firewalls, patching, etc. Even if this is done, the server still faces various data security risks:
-System poisoning, data tampering (ransomware)
-Trojan in the server, becoming a broiler and a miner
-The personnel in and out of the computer room can copy the data away
-Public cloud providers can peek at data

Summary of Requirements
The enterprise server does not have dedicated IT operation and maintenance personnel, and the server system protection is weak or even unprotected.The personnel who operate and maintain the server are also some non-professional IT operation and maintenance personnel. Often, the system is poisoned and paralyzed due to misoperation or unintentional operation, which brings huge losses to the enterprise.
The server has been running for a long time, causing the system to be overloaded and running slowly. Some of them are regarded as mining machines without knowing it.If the situation occurs, professionals must be invited to deal with it on-site, which will increase the operation and maintenance cost.
Because there is no professional protection, the system is extremely easy to be deleted, tampered and destroyed by competitors and hackers after intrusion, resulting in unpredictable losses and damages.
The server operation and maintenance personnel copied all the data on the server privately; the data was leaked after the computer hard disk was stolen.

MCK cloud private key data protection system (My Cloud Key)
MCK (My Cloud Key) is a server data protection system developed by Shenxinda. By embedding the MCK (Last Meter Data Security) security engine into the operating system, it redefines the functions of each module of the operating system.Build an independent identity authentication system, whitelist to define work scenarios and behaviors, protect core data, prevent Trojan virus intrusion, and prevent core data from being peeped, destroyed, tampered with, and stolen!.

MCK management terminal: It can be installed on an independent server or together with the publishing server to authorize client functions, collect client logs, and generate reports.
MCK client: Installed on the business server or database server to protect the security of the business server and database, prevent tampering with server files and database content, prevent hacker intrusion, virus infection, and peeping by operation and maintenance personnel.
Solution
Sangxinda MCK cloud private key has a system scenario whitelist protection mechanism.That is, the server lock redefines the operating system user permission module, issues a unique identity signature for each program behavior, and formulates a whitelist of executable programs to prevent illegal programs and Trojan viruses from running.
Effect:
When enabled, no new programs can run, no new applications can be installed indiscriminately, and no viruses will be infected.
The Trojan horse virus program has no chance to run, and any program cannot run if it is infected.


Construct a script execution container in the core of Shenxinda MCK cloud private key, and perform fingerprint-level identity signature on executable scripts. Only safe scripts are allowed to execute.Opportunity to run.

Sangxinda MCK cloud private key performs driver-level transparent encryption on the files of the business system, and reads the files
Write for signature authentication
Effect:
The normal operation of the business system and the stored data are encrypted to prevent proliferation.
Any file that is read or written must be authenticated to prevent peeping.
All business data is immutable, tamper-proof and anti-ransomware.

Sangxinda MCK cloud private key is deeply encrypted for the hard disk kernel, and the operation and maintenance personnel do not have the secret key and cannot open any protected data (does not affect normal operation and maintenance).Even if the hard drive is stolen, the data is still protected.

Support the protection of linux system platform.
MCK Control Center
Through the central host, the security status of the server protected by MCK can be monitored, and when the server is attacked, it can be discovered and controlled at the first time

边栏推荐
- 流式结构化数据计算语言的进化与新选择
- kali渗透测试环境搭建
- 1076 Wifi Password (15 points)
- One-hot in TF
- Two startup methods and differences of Service
- Keep track of your monthly income and expenses through bookkeeping
- go-grpc TSL authentication solution transport: authentication handshake failed: x509 certificate relies on ... ...
- 装饰器模式:Swift 实现
- 1.1-Regression
- 记录一些遇见的bug——Lombok和Mapstruct的冲突导致,A component required a bean of type ‘com.XXX.controller.converter.
猜你喜欢
随机推荐
2022-08-10 mysql/stonedb-慢SQL-Q16-耗时追踪
机器学习(三)多项式回归
囍楽cloud task source code
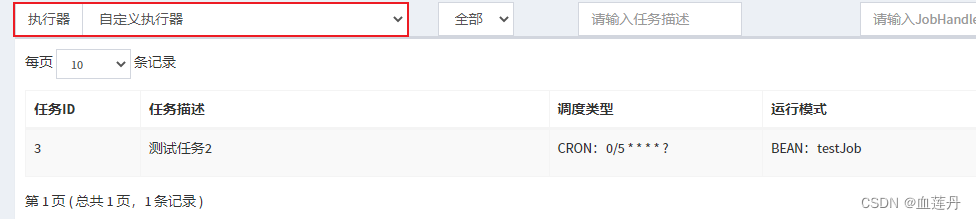
XXL-JOB 分布式任务调度中心搭建
分门别类输入输出,Go lang1.18入门精炼教程,由白丁入鸿儒,go lang基本数据类型和输入输出EP03
美术2.4 UV原理基础
Openlayers 聚合图、权重聚合图以及聚合图点击事件
The most complete documentation on Excel's implementation of grouped summation
快速幂,逆元的求解
如何通过 IDEA 数据库管理工具连接 TDengine?
3.2 - classification - Logistic regression
IQUNIX A80 exploring TTC金粉 初体验
excel 透视表 值显示内容 不显示计数
Analysys and the Alliance of Small and Medium Banks jointly released the Hainan Digital Economy Index, so stay tuned!
go sqlx 包
笔试题大疆08.07
2021-08-11 For loop combined with multi-threaded asynchronous query and collect results
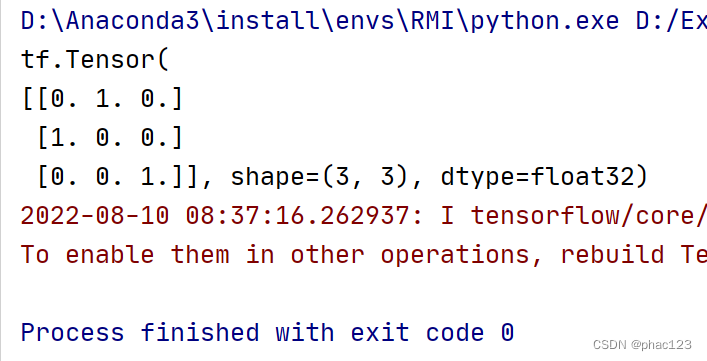
The softmax function is used in TF;
1036 Programming with Obama (15 points)
magical_spider远程采集方案