当前位置:网站首页>MySQL basics 3
MySQL basics 3
2022-04-23 05:07:00 【Write poetry for you@】
-
understand mysql
- Add new users
- Modify user rights
- Change user password
- Query the user
- Delete user
1. In essence, a database is a folder , Tables are files

2. establish user user1( new user )
create user 'user1'@'localhost' identified by '123456';
Installed mysql There is 4 individual user user , user1 It's a new user

Let's use this user link again
View the... Under this user database ( only one ,rooot Initially, there are four databases under the user )

3. Change user name Or code
Let's change the user name first
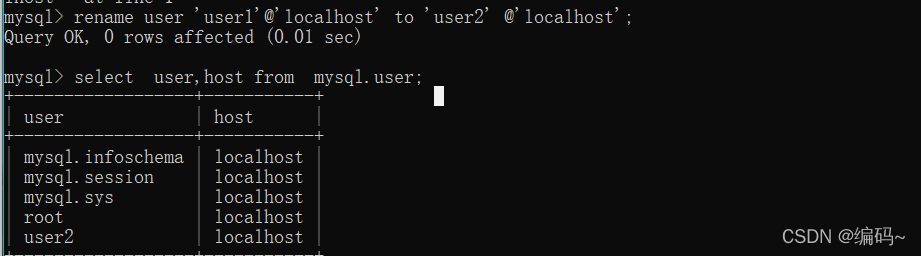
rename user 'user1'@'localhost' to 'user2' @'localhost';
adopt mysql.user This table query mysql Users in become use2 了
Changing the user's password
alter user 'user2'@'localhost' identified by '654321';
Be careful After revising user2 After this user name and password , Log in and change your password 654321

4. Modify user rights , Log in root User's permission to modify other protection , Or modify the user's permission under the user
ps: Add permissions to users , Or after revoking the permission , Need to reopen cmd, link mysql Check the code effect
privileges: User permissions
* Yes select,update,indert,delete etc. , If granted in full, you can use all
Refresh user rights flush privileges
grant privileges on database_name.table_name to 'user_name' @'host'
for example :1
grant all on *.* to 'user1'@'localhost'; // The table is for the user user1 to grant authorization , Give Way user1 Give all library and table operations to this machine , It feels like root And user1 Users operate some libraries together
2. grant select,insert on cesi.student to 'user1'@'localhost';
// To the user use1 to grant authorization , Give Way user1 can cesi In the library student surface implement select Query and insert operations
The following is to revoke the permission of so and so user Be careful (from) Adding permissions is to
revoke jurisdiction on Database name . Table name from' user name '@' Host name 'privileges: User permissions
* Yes select,update,indert,delete etc. , If granted in full, you can use all
revoke all on *.* from 'user1'@'localhost'; This cancels user1 User's operation authority on all databases , Except for the original one
ps: all All permissions ( Additions and deletions ) *.* Represents all libraries and tables
ps: Here is user1 user There is no database that can be operated before revoking
5. Query the user
stay mysql Under the user , adopt mysql.user Table query
select user,host from mysql.user;
6. Delete a user , It is not recommended to test root user , Delete... Here user2
First log in to any user , operation , drop user 'xxx user name '@' Host name '

版权声明
本文为[Write poetry for you@]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220549552436.html
边栏推荐
- DIY 一个 Excel 版的子网计算器
- Innovation training (XII) reptile
- [2021] Spatio-Temporal Graph Contrastive Learning
- 深度学习笔记 —— 物体检测和数据集 + 锚框
- 静态流水线和动态流水线的区别认识
- Kubectl command automatic replenishment
- 持续集成(CI)/持续交付(CD)如何彻底改变自动化测试
- 负载均衡简介
- AQS source code reading
- MySQL views the SQL statement details executed by the optimizer
猜你喜欢

Field injection is not recommended using @ Autowired

Backup MySQL database with Navicat
Learning Android II from scratch - activity

MySQL 慢查询

How can continuous integration (CI) / continuous delivery (CD) revolutionize automated testing

【数据库】MySQL多表查询(一)

深度学习笔记 —— 语义分割和数据集
![[2022 ICLR] Pyraformer: Low-Complexity Pyramidal Attention for Long-Range 时空序列建模和预测](/img/7c/51ac43080d9721f1bdc1cd78cd685b.png)
[2022 ICLR] Pyraformer: Low-Complexity Pyramidal Attention for Long-Range 时空序列建模和预测

Discussion on flow restriction
![[database] MySQL single table query](/img/27/99d174219109ea7a455cfdf55e0996.png)
[database] MySQL single table query
随机推荐
和谐宿舍(线性dp / 区间dp)
Define defines constants and macros, pointers and structures
Leetcode 1547: minimum cost of cutting sticks
深度学习笔记 —— 物体检测和数据集 + 锚框
Basic concepts of multithreading (concurrency and parallelism, threads and processes) and entry cases
Innovation training (XII) reptile
Golang select priority execution
configmap
Innovation training (VII) FBV view & CBV view
Innovation training (VI) routing
Cross border e-commerce | Facebook and instagram: which social media is more suitable for you?
SCP command details
COM in wine (2) -- basic code analysis
MySQL uses or to query SQL, and SQL execution is very slow
2022/4/22
Innovation training (10)
【数据库】MySQL单表查询
Deep learning notes - object detection and dataset + anchor box
【数据库】MySQL基本操作(基操~)
Grpc long connection keepalive