当前位置:网站首页>Daily CISSP certification common mistakes (April 12, 2022)
Daily CISSP certification common mistakes (April 12, 2022)
2022-04-23 18:17:00 【Tang Junfei - Mingxue Online】
CISSP Certification is often wrong ( From Mingxue online test platform :https://www.maxstu.com/page/1773704)
【 The answer is analyzed after the question 】
subject 1
Q:Kim Want to create a key that enforces database referential integrity . What type of key does she need to create ?
Kim would like to create a key that enforces referential integrity for the database. What type of key does she need to create?
A、 Primary key
Primary key
B、 Foreign keys
Foreign key
C、 Candidate key
Candidate key
D、 Master key
Master key
subject 2
Q:Amanda Want to use existing Gmail Contacts in the account , New users of her app already have these contacts . Which of the following protocols is used for such use by many cloud providers , Provide secure delegate access ?
Amanda wants to use contacts from the existing Gmail accounts that new users for her application already have. What protocol from the following options is used to provide secure delegated access for this type of use by many cloud providers?
A、OpenID
B、Kerberos
C、OAuth
D、SAML
subject 3
Q:Jill Is purchasing new network hardware for her organization . She found a gray market supplier who imported hardware from abroad at a lower price . What is the most important security issue of the hardware obtained in this way ?
Jill is working to procure new network hardware for her organization. She finds a gray market supplier that is importing the hardware from outside the country at a much lower price. What security concern is the most significant for hardware acquired this way?
A、 Security of hardware and firmware
The security of the hardware and firmware
B、 Availability of hardware and software support
Availability of support for the hardware and software
C、 Whether the hardware is the legal product of the actual supplier
Whether the hardware is a legitimate product of the actual vendor
D、 Age of hardware
The age of the hardware
---------------
There are more free online security certification test questions and wechat learning discussion groups , You can add Mingxue online assistant vx:maxstu_com, Get and join .
---------------
subject 1
answer :B
analysis : Integrity references ensure that records are referenced by foreign keys in other tables , The record exists in the secondary table . Foreign keys are mechanisms used to strictly guarantee referential integrity .
B. Foreign keys are used to create relationships between tables in a database. The data- base enforces referential integrity by ensuring that the foreign key used in a table has a corresponding record with that value as the primary key in the referenced table.
subject 2
answer :C
analysis :OAuth Used to provide secure delegated access in scenarios like this .OpenID Credentials used to log in from other service providers , For example, when you use Google When logging into other websites .SAML Or security assertion markup language , Used to make security assertions , Allow authentication and authorization between identity providers and service providers .Kerberos Mainly used within the organization , Not in a union , And this is the focus of this question .
OAuth is used to provide secure delegated access in scenarios exactly like this. OpenID is used to sign in using credentials from an identity provider to other services, such as when you log in with Google to other sites. SAML, or Security Assertion Markup Language, is used to make security assertions allowing authentication and authorizations between identity providers and service providers. Kerberos is mostly used inside of organizations instead of for federation, as this question focuses on.
subject 3
answer :A
analysis : Each of these answers can be a question , But the most important security issue is whether the hardware and firmware can be trusted or may have been modified . Original equipment manufacturer (OEM) There are commercial reasons to ensure the safety of its products , But third parties in the supply chain may not feel the same pressure . The availability of support and the legality of hardware are also issues , But it's not a direct security issue . Last , The hardware may be older than expected , Or maybe it's used 、 Refurbished or not new .
Each of these answers may be a concern, but the overriding security concern is if the hardware and firmware can be trusted or may have been modified. Original equipment manufacturers (OEMs) have business reasons to ensure the security of their product, but third parties in the supply chain may not feel the same pressure. Both availability of support and whether the hardware is legitimate are also concerns, but less immediate security concerns. Finally, hardware may be older than expected, or may be used, refurbished, or other- wise not new.
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610263917.html
边栏推荐
- Crawler for querying nicknames and avatars based on qqwebapi
- 消费者灰度实现思路
- Stm32mp157 wm8960 audio driver debugging notes
- Format problems encountered in word typesetting
- JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
- Error reported when running tensorboard: valueerror: duplicate plugins for name projector, solution
- Docker 安裝 Redis
- In shell programming, the shell file with relative path is referenced
- Test post and login function
- Matlab tips (6) comparison of seven filtering methods
猜你喜欢
QT add external font ttf
Dock installation redis
Vulnérabilité d'exécution de la commande de fond du panneau de commande JD - freefuck
![[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (2)](/img/91/3272d5ad04cd1d8476c739546f4356.png)
[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (2)
【ACM】509. Fibonacci number (DP Trilogy)
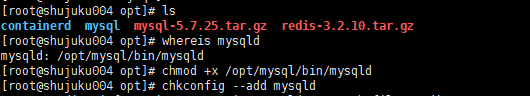
mysql自动启动设置用Systemctl start mysqld启动
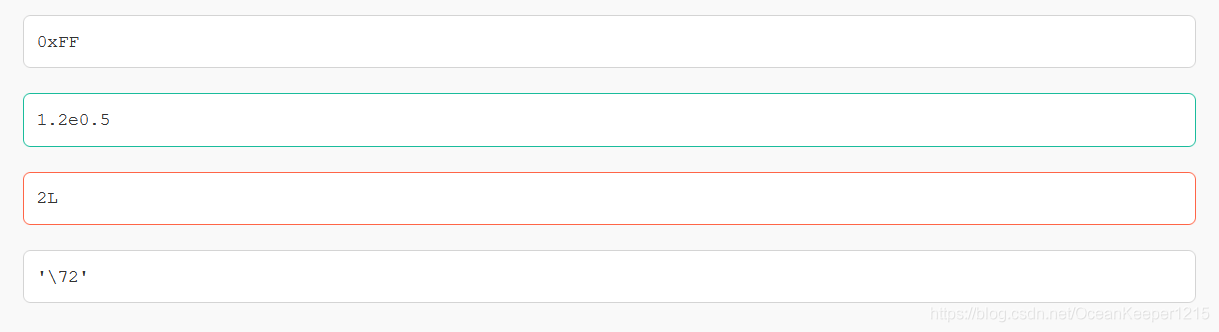
7-21 wrong questions involve knowledge points.
Hard core parsing promise object (do you know these seven common APIs and seven key questions?)

JD-FreeFuck 京東薅羊毛控制面板 後臺命令執行漏洞
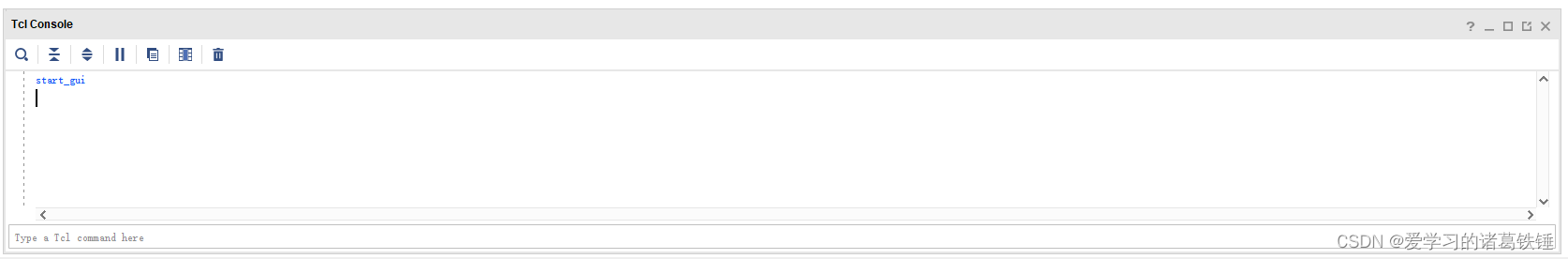
The vivado project corresponding to the board is generated by TCL script
随机推荐
Gson fastjason Jackson of object to JSON difference modifies the field name
[UDS unified diagnostic service] (Supplement) v. detailed explanation of ECU bootloader development points (2)
C [file operation] read TXT text by line
Qt读写XML文件(含源码+注释)
Crawl the product data of cicada mother data platform
Resolve the error Max virtual memory areas VM max_ map_ count [65530] is too low, increase to at least [262144]
How to install jsonpath package
Reptile efficiency improvement method
QT add external font ttf
From source code to executable file
powerdesigner各种字体设置;preview字体设置;sql字体设置
mysql自动启动设置用Systemctl start mysqld启动
Rust: how to match a string?
MATLAB从入门到精通(二)
Resolves the interface method that allows annotation requests to be written in postman
Batch export ArcGIS attribute table
MySQL auto start settings start with systemctl start mysqld
Solution to Chinese garbled code after reg file is imported into the registry
【ACM】376. Swing sequence
MATLAB小技巧(6)七种滤波方法比较