当前位置:网站首页>Remote code execution in Win 11 using wpad / PAC and JScript
Remote code execution in Win 11 using wpad / PAC and JScript
2022-04-23 20:05:00 【franket】
Introduce
In hindsight , Many widely deployed technologies seem to be a strange or unnecessary risk-taking idea .IT Engineering decisions in are usually made under incomplete information and time pressure ,IT Some of the strangest things about the stack “ It seemed like a good idea ” To explain . In the personal views of some of the authors of this article ,WPAD(“Web Proxy Auto Discovery Protocol”—— More specifically “Proxy Auto-Config”) Is one of them .
stay Internet Some early moment ——1996 Years ago ——Netscape According to the engineer of JavaScript Is a good language for writing configuration files . The result is PAC—— A configuration file format , It works as follows : The browser connects to a preconfigured server , download PAC file , And perform specific Javascript Function to determine the correct proxy configuration . Why not? ? It's definitely better than ( For example )XML More expressive and less verbose , And it seems to be a reasonable way to provide configuration to many clients .
PAC Itself and a called WPAD Combination of protocols —— The protocol eliminates the need for browsers to connect to pre configured servers . contrary ,WPAD Allows the computer to query the local network to determine where to load PAC File server .
somehow , This technology eventually became 1999 Due in IETF The draft , And now , stay 2017 year , Each station Windows The machine will ask the local network :“ well , Where can I find what to do Javascript file ?”. This can happen through a variety of mechanisms :DNS、WINS, but —— Maybe the most interesting thing is ——DHCP.
In recent years , Browser vulnerability exploitation has been mainly aimed at DOM Change to directly target Javascript engine , So just mention that we can execute through the network without a browser Javascript It's very attractive . Preliminary investigation shows that , Responsible for executing these configuration files JS Engine is jscript.dll - Also support IE7 and IE8 Old version of JS engine ( If you use the appropriate script attributes , stay IE7/8 Compatibility mode can still be used in IE11 Medium visit ). It's good and bad - One side , This means that not everyone Chakra Errors will automatically become local network remote attacks , But on the other hand , This means that some fairly old code will be responsible for executing our Javascript.
Researchers have previously warned about safety too WPAD Of dangerous . however , As far as we know , This is the first proof against WPAD Your attack will lead to WPAD Complete intrusion of user machines .
Windows Certainly not the only way to achieve WPAD Software for . The same is true for other operating systems and Applications . for example ,Google Chrome There is also a WPAD Realization , But in Chrome Under the circumstances , assessment PAC In the document JavaScript The code takes place in the sandbox . And other support WPAD Your operating system does not enable it by default . That's why Windows At present, it is the most interesting target of this kind of attack .
Web Agent auto discovery
As mentioned above ,WPAD Will query DHCP and DNS( In this order ) To get the to connect URL - If not from DNS Response , Obviously, you can also use LLMNR and Netbios.WPAD-over-DNS Some features of can lead to surprising attack vectors .
Attack scenarios : adopt DHCP Local network
In the most common case , The machine will use the option code 252 Query local DHCP The server .DHCP The server replies with a string - for example “ http://server.domain/proxyconfig.pac ”, It specifies the configuration URL Should get the file . Then the client continues to get the file , And use the content as Javascript perform .
In the local network , An attacker can simply impersonate DHCP The server - adopt ARP Legal by game or competition DHCP. then , An attacker can provide hosting malicious Javascript Of documents URL.
Attack scenarios : Through privileged locations and DNS Remote access Internet
In addition to local cyber attack scenarios ,WPAD Your search may also be through DNS happen , This creates a secondary attack scenario . Many users configure their computers for public use 、 Globally visible DNS One of the servers ( for example 8.8.8.8、8.8.4.4、208.67.222.222 and 208.67.220.220) perform DNS lookup . under these circumstances , The machine will DNS Inquire about ( for example wpad.local) Send to a server located outside the local network . An attacker in a privileged position on the network ( For example, gateway or any other upstream host ) Can monitor DNS Query and cheat reply , So as to guide the client to download and execute malicious Javascript file .
Settings like this seem common - according to This Wikipedia entry ,DNS A large part of the traffic seen by the root server is .local request .
Attack scenarios : Through malice wpad.tld Remote on the Internet
WPAD A particular oddity of is that it recursively traverses the local machine name to find the domain to query . If a machine is called “laptop01.us.division.company.com”, Then query the following fields in order :
- wpad.us.division.company.com
- wpad.division.company.com
- wpad.company.com
- wpad.com
this ( according to this Wikipedia entry ) It used to cause people to register wpad.co.uk And redirect traffic to online auction sites . Further reference to this entry :
adopt WPAD file , Attackers can point users' browsers to their own agents , And intercept and modify all WWW Traffic . Although in 2005 In, it was applied for Windows WPAD Simple fix for handling , But it only fixes .com The problem of domain .Kiwicon A speech by showed that , The rest of the world is still very vulnerable to this security breach , A sample domain registered in New Zealand for testing purposes , Receive proxy requests from all over the country at a rate of several per second . some wpad.tld domain name ( Include COM、NET、ORG and US) Now point to the client loopback address , To help prevent this vulnerability , But there are still some names registered (wpad.co.uk).
therefore , Administrators should ensure that users can trust all users in the organization DHCP The server , And all the possible of the organization wpad The domains are under control . Besides , If not configured for the organization wpad Domain , Then the user will go to the next... In the domain hierarchy wpad Any external location of the site , And use it for its configuration . This allows in a particular country / Regional registration wpad Anyone in a subdomain can set themselves as agents for all traffic or sites of interest , For the country / Most of the region Internet Flow execution Man-in-the-middle attack .
On the other hand ,IETF The draft clearly requires customers to only allow “ standard ”( For example, non top-level domains ). We haven't investigated the extent to which customers have achieved this , Or secondary domain ( for example .co.uk) Is it the culprit of historical traffic redirection cases .
Either way : If a person tries to work for a given organization TLD register wpad.$TLD, ... under consideration Javascript Errors in the engine can be exploited remotely via the Internet , The premise is that TLD Not explicitly blacklisted by the client implementation . Whereas 1999 Year of IETF The draft cites 1994 Year of TLD list ( RFC1591 ), It is unlikely that the client has been updated to reflect the new TLD The spread of .
We work for all kinds of TLD register wpad.co.$TLD Attempts to ( not yet ) success .
error
We spent some time looking for jscript.dll Mistakes in , Manual analysis and fuzzy test are adopted .JScript Initially, some challenges were posed , Because many are used to trigger JavaScript Errors in the engine “ function ” Can't be in JScript Use in , Just because it's too old to support them . for example :
- No more than one array type (int Array 、float Array etc. ). therefore , It is impossible to confuse one array type with another .
- No updates 、 Faster JavaScript So much optimization of the engine (“ Fast path ”). These fast paths are often the source of errors .
- Cannot be used in general JavaScript Define... On the object getter/setter. You can call defineProperty But only those that don't work for us DOM object , because WPAD There won't be... In the process DOM. Even if there is , many JScript Function in DOM When called on an object, it will also simply fail , And display the message “JScript object expected”.
- Once the prototype of an object is created, it cannot be changed ( That is, no “__proto__” attribute ).
however ,JScript There are more “ old-fashioned ” Vulnerability categories , for example use-after-free. This old article MSDN article Described in JScript The garbage collector . JScript Use non generational tagging and scavenging garbage collectors . Essentially , Whenever garbage collection is triggered , It will mark all JScript object . Then it's from a group “ root ” object ( Sometimes it's also called “ The sweeper ”) Start scanning them , And clear the tags of all objects it encounters . All objects that are still marked will be deleted . A recurring problem is that local variables on the stack are not added to the root object list by default , This means that programmers need to remember to add them to the root list of the garbage collector , Especially if the objects referenced by these variables can be deleted within the life cycle of the function .
Other possible vulnerability types include buffer overflow 、 Uninitialized variables, etc .
For fuzzy testing , We used a grammar based approach to Domato Fuzzy test engine , And specifically for JScript Write a new grammar . By looking at various JScript Object's EnsureBuiltin Method , We identified interesting built-in properties and functions to add to the syntax .JScript Syntax has been added to Domato The repository in .
Between fuzzy testing and manual analysis , We found seven security vulnerabilities . They are summarized in the table below :
|
Vulnerability level |
influence IE8 Pattern vulnerabilities |
influence IE7 model A loophole |
|---|---|---|
|
Use after free |
1340 , 1376 , 1381 |
1376 |
|
Heap overflow |
1369 , 1383 |
1369 , 1383 |
|
Uninitialized variables |
1378 |
1378 |
|
Crossing the line read |
1382 |
1382 |
|
All of the |
7 |
5 |
When posting this blog post , All errors have been fixed by Microsoft .
The table subdivides vulnerabilities according to the classes and compatibility modes required to trigger vulnerabilities .WPAD Medium JScript Equivalent to the IE7 Run the script in compatibility mode , It means , Although we found 7 A loophole , But in WPAD in “ only ” It can trigger 5 individual . however , When a malicious web page enters IE8 In compatibility mode , Other vulnerabilities can still be used to attack Internet Explorer( Include IE11).
版权声明
本文为[franket]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231947044677.html
边栏推荐
- Kubernetes introduction to mastery - ktconnect (full name: kubernetes toolkit connect) is a small tool based on kubernetes environment to improve the efficiency of local test joint debugging.
- LeetCode异或运算
- Introduction to electron Tutorial 4 - switching application topics
- Design of library management database system
- Golang timer
- 渤海期货这家公司怎么样。期货开户办理安全?
- MySQL 进阶 锁 -- MySQL锁概述、MySQL锁的分类:全局锁(数据备份)、表级锁(表共享读锁、表独占写锁、元数据锁、意向锁)、行级锁(行锁、间隙锁、临键锁)
- Design of warehouse management database system
- Class loading mechanism
- Unity general steps for creating a hyper realistic 3D scene
猜你喜欢

Understanding various team patterns in scrum patterns

@Mapperscan and @ mapper
Class loading process of JVM
Project training of Software College of Shandong University - Innovation Training - network security shooting range experimental platform (6)
Kubernetes入门到精通-裸机LoadBalence 80 443 端口暴露注意事项
![[transfer] summary of new features of js-es6 (one picture)](/img/45/76dba32e4fa7ed44a42e5f98ea8207.jpg)
[transfer] summary of new features of js-es6 (one picture)
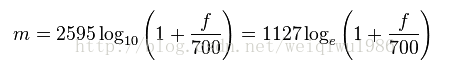
MFCC: Mel频率倒谱系数计算感知频率和实际频率转换
Command - sudo
PHP reference manual string (7.2000 words)
精简CUDA教程——CUDA Driver API
随机推荐
Kubernetes getting started to proficient - install openelb on kubernetes
还在用 ListView?使用 AnimatedList 让列表元素动起来
[numerical prediction case] (3) LSTM time series electricity quantity prediction, with tensorflow complete code attached
The difference between underline and dot of golang import package
MySQL lock
图书管理数据库系统设计
Unity general steps for creating a hyper realistic 3D scene
Kubernetes入门到精通-裸机LoadBalence 80 443 端口暴露注意事项
C6748 software simulation and hardware test - with detailed FFT hardware measurement time
Openharmony open source developer growth plan, looking for new open source forces that change the world!
Physical meaning of FFT: 1024 point FFT is 1024 real numbers. The actual input to FFT is 1024 complex numbers (imaginary part is 0), and the output is also 1024 complex numbers. The effective data is
MFCC: Mel频率倒谱系数计算感知频率和实际频率转换
Shanda Wangan shooting range experimental platform project - personal record (V)
Scrum Patterns之理解各种团队模式
Project training of Software College of Shandong University - Innovation Training - network security shooting range experimental platform (V)
@Mapperscan and @ mapper
Why is the hexadecimal printf output of C language sometimes with 0xff and sometimes not
仓库管理数据库系统设计
Lpc1768 optimization comparison of delay time and different levels
Possible root causes include a too low setting for -Xss and illegal cyclic inheritance dependencies