当前位置:网站首页>Research on system and software security (2)
Research on system and software security (2)
2022-04-23 08:01:00 【Xihang】
List of articles
A practical analysis of ROP attacks
arxiv 2021
( The quality of the article is not high )
background
ROP It's actually a code reuse attack , A control flow hijacking attack that does not require an attacker to inject any code , But it can trigger any behavior in the target system , Code reuse attack . Program address space (gadgets) Existing code fragments present in are linked together to perform malicious acts .
The most common one is called return oriented ROP, The other is called challenge oriented programming JOP.
ROP Use to ret Code snippet at the end of the instruction , It's like pop rip equally
In order to complete the attack target :
- Subvert the control flow of a program from its original process , The attacker needs to perform a traditional stack smash attack , For example, stack buffer overflow , And overwrite the return address of the function on the stack . Other methods such as frame pointer overlay can also be used here .
- The attacker needs to redirect the execution of the program to the code chosen by the attacker , An attacker can accomplish this task through code injection .
Modify the memory layout of a program by making the stack non executable , So as to prevent code injection of stack smashing attack . Due to code injection defense &#
版权声明
本文为[Xihang]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230625153696.html
边栏推荐
- 第七章 资产减值
- 内网渗透系列:内网隧道之dnscat2
- Série de pénétration Intranet: icmpsh du tunnel Intranet
- Idea shortcut
- TA notes of Zhuang understand (VII) < Lambert + Phong + shadow + 3evcolor + Ao >
- Research on software security based on NLP (I)
- 三分钟教你用Houdini流体>>解算粒子流体水滴
- Link to some good tutorials or notes about network security and record them
- 读书笔记
- strcat()、strcpy()、strcmp()、strlen()
猜你喜欢

linux下mysql数据库备份与恢复(全量+增量)
![[unity VFX] Introduction notes of VFX special effects - spark production](/img/bb/a6c637d025dfb8877e6b85e7f39d6b.png)
[unity VFX] Introduction notes of VFX special effects - spark production

常用Markdown语法学习

Mysql database backup and recovery under Linux (full + incremental)

内网渗透系列:内网隧道之pingtunnel
CTF-MISC学习之从开始到放弃

Towords Open World Object Detection

云计算技能大赛 -- openstack私有云环境 第一部分
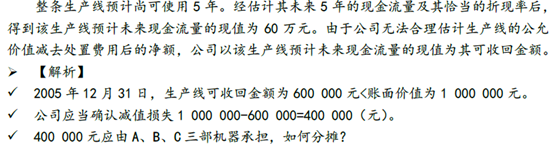
Chapter VII asset impairment

C # control the camera, rotate and drag the observation script (similar to scenes observation mode)
随机推荐
云计算技能大赛 -- openstack私有云环境 第一部分
ABAP ALV显示金额与导出金额不一致
Houdini > fluid, rigid body export, learning process notes
VBA calls SAP RFC to read & write data
第七章 资产减值
C read INI file and write data to INI file
Houdini流体>>粒子流体导出到unity笔记
BUUCTF MISC刷题
Internal network security attack and defense: a practical guide to penetration testing (5): analysis and defense of horizontal movement in the domain
Plane definition - plane equation
C # control the camera, rotate and drag the observation script (similar to scenes observation mode)
Unity gets a resource that is referenced by those resources
Sto with billing cross company inventory dump return
Houdini terrain and fluid solution (simulated debris flow)
Index locked data cannot be written to es problem handling
Houdini>建筑道路可变,学习过程笔记
The problem of exporting excel form with wireframe and internal spacing of form by using web form
Série de pénétration Intranet: icmpsh du tunnel Intranet
Enterprise wechat login free jump self built application
三分钟教你用Houdini流体>>解算粒子流体水滴