当前位置:网站首页>CTF online encryption and decryption and common tools
CTF online encryption and decryption and common tools
2022-08-09 17:18:00 【AHlien】
In the beginning of CTF, finding tools is the most annoying and the easiest part to dispel our enthusiasm. I share some encryption and decryption, coding, CTF tools, algorithms, etc. that I have used and recorded before.To everyone, I hope to be helpful to everyone, and jointly contribute to the network security of the motherland!
Binary to text site
http://www.txttool.com/t/?id=NDE5
Knight CMSstrong>
https://www.74cms.com/
Convert Unicode encoding to characters
https://www.runoob.com/jsref/jsref-fromcharcode.html
Convert Unicode to Chinese
https://www.bejson.com/convert/unicode_chinese/
Audio morse decoding
https://morsecode.world/international/decoder/audio-decoder-adaptive.html
DES/TripleDes/AES/RSA/SM2/SM3/SM4 encryption and decryption
https://the-x.cn/en-us/cryptography/TripleDes.aspx
CTF encryption and decryption collection
http://ctf.ssleye.com/
ROT5/13/18/47 encodingConvert
https://www.qqxiuzi.cn/bianma/ROT5-13-18-47.php
CTF Repository
https://www.ctftools.com/
Encryption and decryption with Buddhism and Zen
https://www.keyfc.net/bbs/tools/tudoucode.aspx
The large collection of CTF encryption and decryption contains the online encryption and decryption tools we often use, as well as encoding, CTF algorithms, CTF miscellaneous, etc.
The CTF resource library contains the CTF tools we often use
Can only be used for learning, illegal use at your own risk!
边栏推荐
- Hold face (hugging face) tutorial - Chinese translation - task summary
- PE格式系列_0x05:输出表和重定位表(.reloc)
- 图像质量指标:峰值信噪比PSNR和结构相似性SSIM
- 【力扣】617. 合并二叉树
- 【学习笔记】win10报0xc0000221错误无法开机
- 【深度学习】SVM解决线性不可分情况(八)
- QNX 7.1 交叉编译 boost 1.76
- Photoshop CS6的使用心得
- hugging face tutorial-Chinese translation-pipeline-based reasoning
- 【 graduate work weekly 】 (10 weeks)
猜你喜欢
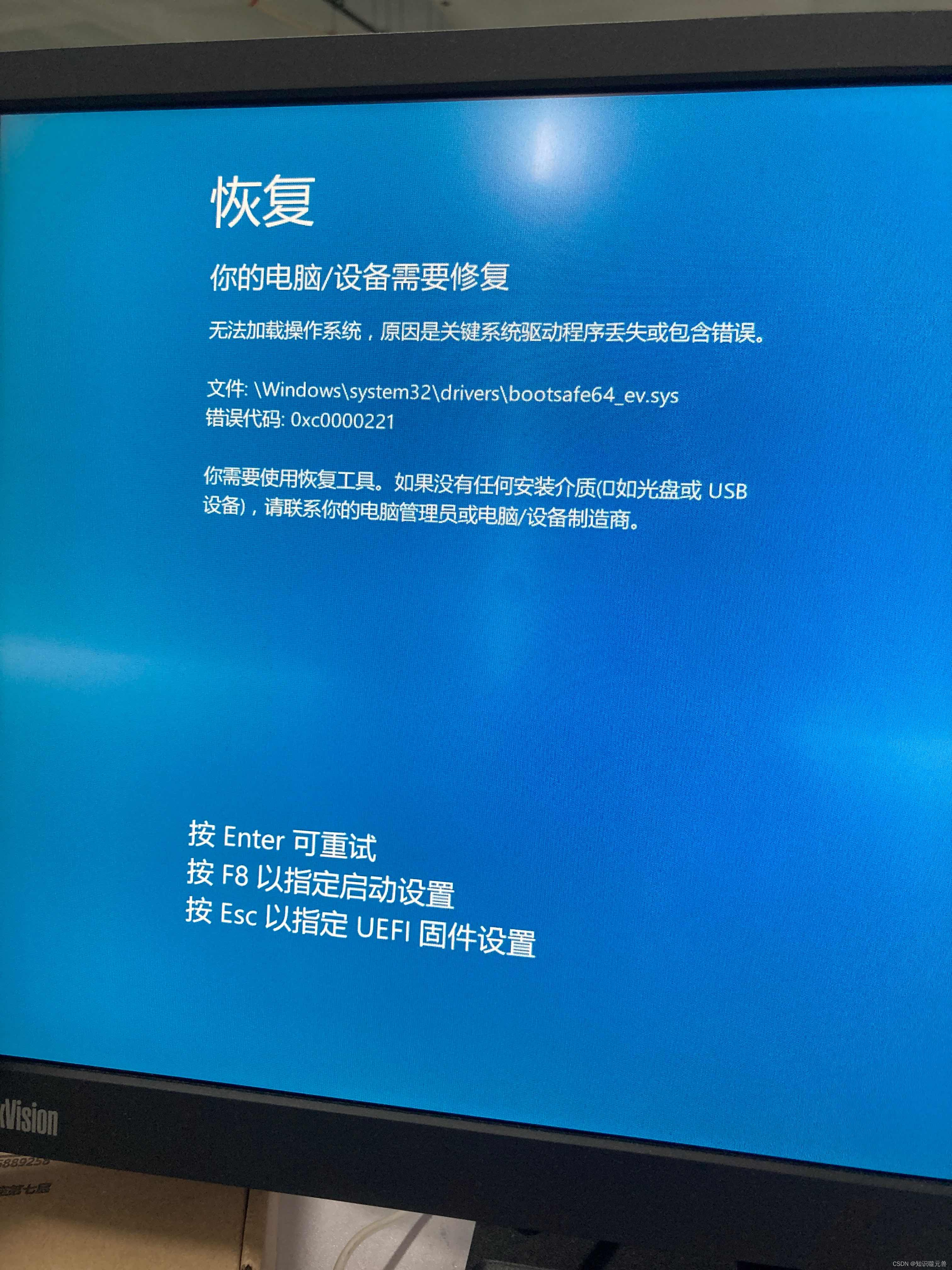
【学习笔记】win10报0xc0000221错误无法开机

Vim实用技巧_5.在文件间和文件内快速移动

【Postgraduate Work Weekly】(Week 8)

【Postgraduate Work Weekly】(The third week)

配置 vscode 让它变得更好用
交叉编译 OpenSSL
【更新中7/31】NTIRE 2022 ESR(efficient super-resolution) 方案与结果

R-CNN Fast R-CNN Faster R-CNN总结

【Postgraduate Work Weekly】(Week 12)

【Postgraduate Work Weekly】(Week 7)
随机推荐
时间序列分析
Photoshop CS6的使用心得
【Postgraduate Work Weekly】(Week 7)
堆(heap)系列_0x05:一张图剖析堆块分配和FreeLists的联系
数据拟合方法 MATLAB在数学建模中的应用(第二版)
软件安全基本概念
【工具使用】Modscan32软件使用详解
Stetman读paper小记:Backdoor Learning: A Survey(Yiming Li, Yong Jiang, Zhifeng Li, Shu-Tao Xia)
Hold face (hugging face) tutorial - Chinese translation - task summary
Visio画神经网络卷积层
AlexNet pytorch实现
【The sword refers to Offer II 091. Paint the house】
【深度学习】前向传播和反向传播(四)
将类指针强制转换为void*指针进行传参的使用方法
【论文阅读】Deep Learning for Image Super-resolution: A Survey(DL超分辨率最新综述)
交叉编译 Crypto++
【力扣】207. 课程表
深入浅出最优化(6) 最小二乘问题的特殊方法
蓝桥杯嵌入式第十三届模拟题做题笔记
【学习笔记】win10报0xc0000221错误无法开机
