当前位置:网站首页>SSL / TLS application example
SSL / TLS application example
2022-04-23 07:23:00 【dotphoenix】
1、SSL/TLS brief introduction
Agreement is Web Browser and Web A protocol for the secure exchange of information between servers , Provide two basic security services : Identification and confidentiality .
1.1、 effect
Don't use SSL/TLS Of HTTP signal communication , It's communication without encryption . All information is transmitted in plain text , There are three risks .
- The risk of eavesdropping (eavesdropping): The third party can know the content of the communication .
- Risk of tampering (tampering): The third party can modify the content of the communication .
- Pretend to be a risk (pretending): The third party can participate in the communication as others .
SSL/TLS The agreement is designed to address these three risks , Hope to achieve :
- A secret : After the session key is defined in the handshake protocol , All messages are encrypted .
- To identify : Optional client authentication , And forced server-side Authentication .
- integrity : Messages sent include message integrity checks ( Use MAC).
1.2、 working principle
1.2.1、 Basic concepts
-
Key:Key It's a bit (bit) character string , Used to encrypt and decrypt data , It's like a key to unlock .
-
Symmetric algorithm (symmetric cryptography): It requires both sides to use the same key To encrypt and decrypt messages , Common key algorithms are Data Encryption Standard(DES)、triple-strength DES(3DES)、Rivest Cipher 2 (RC2) and Rivest Cipher 4(RC4). Because the efficiency of symmetric algorithm is relatively high , therefore SSL The sensitive data in the session is encrypted by the key algorithm .
-
Asymmetric algorithm (asymmetric cryptography): Namely key Is composed of a public key and a private key pair (key-pair), Pass the public key to the other party and keep the private key by yourself . The public and private key algorithms are mutually inverse , One for encryption , The other can decrypt . Common algorithms are Rivest Shamir Adleman(RSA)、Diffie-Hellman(DH). The asymmetric algorithm has a large amount of computation and is relatively slow , Therefore, it is only suitable for a small amount of data encryption , Such as encrypting the key , It is not suitable for communication encryption of a large amount of data .
-
Public key certificate (public key certificate): Public key certificates are similar to digital passports , Issued by a trusted institution . The trusted organization's public key certificate is certificate authority(CA). Multiple certificates can be connected into a certificate string , The sender is the first , The next is the entity that issued the certificate , Up to root certificate is a trusted organization worldwide , Include VeriSign, Entrust, and GTE CyberTrust. Public key certificate makes the public key transmission of asymmetric algorithm more secure , Can avoid identity forgery , such as C Created public and private keys , Yes, and pretend to be A Pass the public key to B, such C And B Communication between will make B Mistaken identity A And B Communication between .
-
Encrypted hash function (Cryptographic Hash Functions): Encryption hash function and checksum Functions are similar . The difference is ,checksum It is used to detect unexpected data changes, while the former is used to detect intentional data tampering . The data is hashed to produce a small string of bits , Small data changes will lead to changes in the hash string . When sending encrypted data ,SSL Will use the encrypted hash function to ensure data consistency , Used to prevent third parties from damaging the integrity of communication data .SSL Commonly used hash algorithms are Message Digest 5(MD5) and Secure Hash Algorithm(SHA).
-
Message authentication code (Message Authentication Code): The message authentication code is similar to the encryption hash function , Except that it needs to be key based . The combination of the key information and the data generated by the encryption hash function is the hash message authentication code (HMAC). If A Make sure you give B Messages sent are not C Tampering , He should follow the following steps --A First, we have to calculate a HMAC value , Add it to the original message . use A And B The key of communication between encrypts the message body , And send it to B.B After receiving the message, decrypt it with the key , Then recalculate a HMAC, To determine whether the message has been tampered with in transmission .SSL use HMAC To ensure the security of data transmission .
-
digital signature (Digital Signature): After the encrypted hash of a message is created , The hash value is encrypted with the sender's private key , The result of encryption is called digital signature .
1.2.2、 Authentication type :
- One way Authentication : That is, there is only one-sided authentication between the user and the server , That is, the client will authenticate the server-side identity , The server side will not authenticate the client's identity . First , Client initiates handshake request , After the server receives the handshake request , Will choose the protocol version and encryption method suitable for both parties . then , Then send the negotiation result to the client together with the public key of the server . The client uses the public key of the server , Encrypt the data to be sent , And send it to the server . When the server receives it , The local private key will be used to decrypt the received encrypted data of the client . then , Both sides of the communication will use this data to generate the encryption key for communication between the two sides . Next , The two sides can start the secure communication process .
- Two-way authentication : Is that both sides will authenticate each other , That is, certificates will be exchanged between the two . The basic process is exactly the same as one-way Authentication , Just a few more steps in the negotiation stage . After the server sends the negotiation result to the client together with the server's public key , Will request the client's certificate , The client will send the certificate to the server . then , After the client sends encrypted data to the server , The client will send the digital signature generated by the private key to the server . The server side will use the public key in the client certificate to verify the legitimacy of the digital signature . After the handshake is established, the process is completely consistent with one-way communication .
1.2.3、 handshake protocol (Handshake protocol)
Handshake process :
Handshake process .png
step 1:ClientHello – The client sends the supported SSL/TLS The highest protocol version number and the set of encryption algorithms and compression methods supported are sent to the server .
step 2.:ServerHello – After the server receives the client information , Choose what both sides can support SSL/TLS Protocol version, encryption method and compression method , Return to the client .
step 3.:SendCertificate( Optional ) – The server sends the server certificate to the client .
step 4: RequestCertificate( Optional ) – If you choose two-way authentication , The server requests the client certificate from the client .
step 5.:ServerHelloDone – The server notifies the client that the initial negotiation is over .
step 6.:ResponseCertificate( Optional ) – If you choose two-way authentication , The client sends the client certificate to the server .
step 7.:ClientKeyExchange – The client uses the public key of the server , Encrypt the client's public key and key seed , Send to the server .
step 8:CertificateVerify( Optional ) – If you choose two-way authentication , Client generates digital signature with local private key , And send it to the server , Let it authenticate through the received client public key .
step 9: CreateSecretKey – The communication parties generate the communication key based on the key seed and other information .
step 10: ChangeCipherSpec – The client informs the server that the communication mode has been switched to encryption mode .
step 11:Finished – The client is ready for encrypted communication .
step 12:ChangeCipherSpec – The server informs the client that the communication mode has been switched to encryption mode .
step 13:Finished – The server is ready for encrypted communication .
step 14:Encrypted/DecryptedData – Both parties use the client key , The communication content is encrypted by symmetric encryption algorithm .
step 15:ClosedConnection – After communication , Either party sends a disconnection SSL Connected messages .
1.2.4、 Record agreements (Record protocol)
The recording protocol is used after the client and server shake hands successfully , That is, after the client and server identify each other and determine the algorithm used for security information exchange , Get into SSL Record agreements , Record agreement to SSL The connection provides two services :
- confidentiality : Use the secret key defined by handshake protocol to realize
- integrity : Handshake protocol defines MAC, Used to ensure message integrity
Record the process of the agreement :
Record the process of the agreement .png
1.2.5、 Alarm protocol (Alert protocol)
When clients and servers find errors , Send an alert message to the other party . If it's a fatal error , The algorithm is closed immediately SSL Connect , Both parties will first delete the relevant session number , Secrets and keys . A total of... Per alert message 2 Bytes , The first 1 Bytes indicate the error type , If it's an alarm , Then the value is 1, If it's a fatal error , Then the value is 2; The first 2 Bytes to specify the actual error type .
1.2.6、 Secret key generation process
In this way, the handshake agreement is completed , Let's take a look at what is the prepared master key , How the master key is generated . In order to ensure the integrity and confidentiality of information ,SSL Need to have six encryption secrets : Four keys and two IV. For the credibility of information , The client needs a key (HMAC), In order to encrypt, you need to have a key , For packet encryption, we need a IV, So is the service .SSL The required key is one-way , Unlike those keys in other directions . If there is an attack in one direction , This attack has no effect in other directions . The generation process is as follows :
Calculate the master key from the prepared master key .png
Calculate the secret key material from the master secret key .png
Extract the encryption key from the secret key material .png
Reference blog :
http://www.ruanyifeng.com/blog/2014/02/ssl_tls.html
https://segmentfault.com/a/1190000002554673
https://www.ibm.com/developerworks/cn/java/j-lo-ssltls/index.html
https://www.cnblogs.com/zhuqil/archive/2012/10/06/ssl_detail.html
https://www.cnblogs.com/zhuqil/archive/2012/10/06/ssl_detail.html
2、keytool brief introduction
Java Self contained keytool The tool is a key and certificate management tool . It allows users to manage their own public keys / Private key pair and related certificates , be used for ( By digital signature ) Self certification ( Users to other users / Service certification itself ) Or data integrity and authentication services . It also allows users to store the public keys of their communication peers ( In the form of a certificate ). keytool Store keys and certificates in a so-called key warehouse (keystore) in . The default keystore implementation implements the keystore as a file . It uses a password to protect the private key .
2.1、Java KeyStore The type of
- JKS and JCEKS yes Java Keystore (KeyStore) Two more common types of ( All I know is 5 Kind of ,JKS, JCEKS, PKCS12, BKS,UBER).
- JKS Of Provider yes SUN, In each version JDK There are ,JCEKS Of Provider yes SUNJCE,1.4 After that, we can all use it directly .
- JCEKS In terms of security level, it is better than JKS strong , The use of Provider yes JCEKS( recommend ), Especially in protecting KeyStore On the private key in ( Use TripleDes).
- PKCS#12 Is the public key encryption standard , It specifies that all private keys can be included 、 Public keys and certificates . It's stored in binary format , Also known as PFX file , stay windows Can be directly imported into the key area , Be careful ,PKCS#12 The keystore protection password is also used to protect Key.
- BKS come from BouncyCastle Provider, It also uses TripleDES To protect... In the keystore Key, It can prevent the certificate library from being accidentally modified (Keystore Of keyentry Get rid of 1 individual bit There will be mistakes ),BKS To be able to talk to JKS interoperability , Readers can use Keytool Go to TryTry.
- UBER More special , When the password is provided through the command line , It can only follow keytool Interaction . Whole keystore It's through PBE/SHA1/Twofish encryption , therefore keystore It can prevent being changed by mistake 、 Check and verify . before ,Sun JDK( Provided by SUN) Allows you to load a without providing a password Keystore, similar cacerts,UBER This is not allowed .
2.2、keytool The order of
- -genkey: Create a default file in the user's home directory ".keystore", There will be one more mykey Another name for ,mykey Contains the user's public key 、 Private key and certificate ,( By default ,keystore The user system default directory will exist , Such as :win System , Will be generated in C:\Documents and Settings\ user name \ The file named “.keystore”);
- -keystore: Specify the name of the keystore ( The generated information will not be available .keystore In file );
- -keyalg: The algorithm that specifies the key ( Such as RSA、DSA,default:DSA);
- -validity: Specifies how many days the certificate created is valid (default:90);
- -keysize: Specify key length (default:1024, Range :512 ~ 2048);
- -storepass: Specifies the password for the keystore ( obtain keystore The password for the information );
- -keypass: Specifies the password for the alias entry ( The password for the private key );
- -dname: Specify certificate owner information . for example : "CN= First and last names ,OU= Organization name ,O= Organization name ,L= City or area name ,ST= State or province name ,C= The two-letter country code for the unit ";
- -list: Displays certificate information in the keystore .keytool -list -v -keystore Appoint keystore -storepass password -v Displays the certificate details in the keystore ;
- -export: Export the certificate specified by the alias to the file .keytool -export -alias Alias to export -keystore Appoint keystore -file Specify the location and name of the exported Certificate -storepass password ;
- -delete: Deletes an entry from the keystore .keytool -delete -alias Specify the to be deleted keystore Alias -keystore Appoint keystore -storepass password ;
- -printcert: View the exported certificate information .keytool -printcert -file yushan.crt;
- -keypasswd: Changes the password for the specified entry in the keystore .keytool -keypasswd -alias Alias to modify -keypass Old password -new New password -storepass keystore password -keystore sage;
- -storepasswd: modify keystore password .keytool -storepasswd -keystore e:\yushan.keystore( You need to change your password keystore) -storepass 123456( The original password ) -new yushan( New password );
- -import: Imports the signed digital certificate into the keystore .keytool -import -alias Alias -keystore Appoint keystore -file Certificate to import ;
2.3、keytool Examples of use
2.3.1、keystone Generation
Phased generation :
command :
keytool -genkey -alias zhaozhou -keypass zhaozhou -keyalg RSA -keysize 1024 -validity 365 -keystore testStore.keystore -storepass 666666
What is your first and last name ?
[Unknown]: zhaozhou
What is the name of your organizational unit ?
[Unknown]: jd
What is the name of your organization ?
[Unknown]: jd
What is the name of your city or area ?
[Unknown]: beijing
Your province / City / What is the name of the Autonomous Region ?
[Unknown]: beijing
The unit's two letter country / What is the area code ?
[Unknown]: ch
CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch Whether it is right ?
[ no ]: y
One time generation :
command :
keytool -genkey -alias zhaozhou -keypass zhaozhou -keyalg RSA -keysize 1024 -validity 365 -keystore testStore.keystore -storepass 666666 -dname "CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch"
2.3.2、keystore Information viewing
command :
keytool -list -v -keystore testStore.keystore -storepass 666666
Output :
Keystore type : JKS
Keystore provider : SUN
Your keystore contains 1 Entries
Alias : zhaozhou
Date of creation : 2019-1-5
Item type : PrivateKeyEntry
Certificate chain length : 1
certificate [1]:
owner : CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch
Publisher : CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch
Serial number : ab89854
Date of expiry : Sat Jan 05 14:59:54 CST 2019, Closing date : Sun Jan 05 14:59:54 CST
2020
Certificate fingerprint :
MD5: 9D:F0:98:56:3F:F7:9C:38:58:FC:30:3C:2B:28:24:2E
SHA1: AC:74:9E:A5:41:AD:D6:F7:E1:6E:5E:F9:FD:96:49:FD:E4:E0:D9:C5
SHA256: CE:77:51:60:00:CB:DF:D5:AE:EA:5D:4F:5C:85:47:14:D9:5A:56:72:66:
F1:A8:E8:8D:1D:E9:50:CC:3B:81:1A
Signature algorithm name : SHA256withRSA
edition : 3
Expand :
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 19 0A A6 EB 67 E9 B8 5B F5 58 03 2D B9 5D E8 93 ....g..[.X.-.]..
0010: CD 4B B1 98 .K..
]
]
*******************************************
*******************************************
2.3.3、 Certificate export
command :
keytool -export -alias zhaozhou -keystore testStore.keystore -storepass 666666 -file testStore.cer
Output :
Store in file <testStore.cer> The certificate
2.3.4、 Certificate confirmation
command :
keytool -printcert -file testStore.cer
Output :
owner : CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch
Publisher : CN=zhaozhou, OU=jd, O=jd, L=beijing, ST=beijing, C=ch
Serial number : ab89854
Date of expiry : Sat Jan 05 14:59:54 CST 2019, Closing date : Sun Jan 05 14:59:54 CST
2020
Certificate fingerprint :
MD5: 9D:F0:98:56:3F:F7:9C:38:58:FC:30:3C:2B:28:24:2E
SHA1: AC:74:9E:A5:41:AD:D6:F7:E1:6E:5E:F9:FD:96:49:FD:E4:E0:D9:C5
SHA256: CE:77:51:60:00:CB:DF:D5:AE:EA:5D:4F:5C:85:47:14:D9:5A:56:72:66:
F1:A8:E8:8D:1D:E9:50:CC:3B:81:1A
Signature algorithm name : SHA256withRSA
edition : 3
Expand :
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 19 0A A6 EB 67 E9 B8 5B F5 58 03 2D B9 5D E8 93 ....g..[.X.-.]..
0010: CD 4B B1 98 .K..
]
]
2.3.5、 Certificate import
command :
keytool -import -alias client -file client.cer -keystore testStore.keystore -storepass 666666 -keypass 666666
Output :
owner : CN=localhost
Publisher : CN=localhost
Serial number : 5b1bd334
Date of expiry : Fri Jan 04 20:26:42 CST 2019, Closing date : Sat Jan 04 20:26:42 CST
2020
Certificate fingerprint :
MD5: A1:F3:B4:96:42:E9:62:2B:8C:FB:83:3B:E2:EE:A3:29
SHA1: 33:01:EA:A6:12:EF:E3:8E:4C:CA:11:EF:D9:4D:DF:3D:85:93:7D:29
SHA256: 1F:EE:BF:D3:15:78:E2:34:F5:53:0E:49:43:58:0E:BB:3E:A5:EE:22:0E:
D1:82:42:95:CD:19:FA:B1:03:7D:74
Signature algorithm name : SHA256withRSA
edition : 3
Expand :
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 23 9D 32 A9 0F C6 C1 1B 95 57 16 88 20 3E B7 0C #.2......W.. >..
0010: 2B 8D 21 59 +.!Y
]
]
Do you trust this certificate ? [ no ]: y
Certificate added to keystore
2.3.6、 Delete certificate
command :
keytool -delete -alias zhaozhou -keystore testStore.keystore -storepass 666666
Output :
Reference blog :
http://tutorials.jenkov.com/java-cryptography/keystore.html
https://www.cnblogs.com/littleatp/p/5922362.html
https://czj4451.iteye.com/blog/1487684
https://my.oschina.net/suyewanwan/blog/164108
https://my.oschina.net/u/2502527/blog/596425
https://my.oschina.net/xinxingegeya/blog/264635
https://www.chinassl.net/ssltools/keytool-commands.html
http://www.cnblogs.com/xdp-gacl/p/3750965.html
https://blog.csdn.net/liumiaocn/article/details/61921014
3、Netty+TLS Encrypted communication
3.1、 One way Authentication
3.1.1、 Secret key and signature certificate generation
(1) Generate Netty Server public key 、 Private key and certificate warehouse :
keytool -genkey -alias server -keysize 2048 -validity 3650 -keyalg RSA -dname "CN=localhost" -keypass nettyDemo -storepass nettyDemo -keystore serverStore.jks
explain :
-alias server: The alias associated with the server certificate warehouse is
-keypass nettyDemo: Server private key password
-storepass nettyDemo: Server keystore password
-keystore serverStore.jks: The file name of the server keystore ( It is placed in the user's home directory by default )
(2) export Netty Server signing certificate :
keytool -export -alias server -keystore serverStore.jks -storepass nettyDemo -file server.cer
(3) Generate Netty The public key of the client 、 Private key and certificate warehouse :
keytool -genkey -alias client -keysize 2048 -validity 3650 -keyalg RSA -dname "CN=localhost" -keypass nettyDemo -storepass nettyDemo -keystore clientStore.jks
explain :
-alias client: The alias associated with the client certificate repository ;
-keypass nettyDemo: Client private key password ;
-storepass nettyDemo: Client keystore password
-keystore clientStore.jks: The file name of the client key store ( It is placed in the user's home directory by default )
(4) take Netty The certificate of the server is imported into the certificate warehouse of the client :
keytool -import -trustcacerts -alias server -file server.cer -storepass nettyDemo -keystore clientStore.jks
The final generation file :
- conf/oneway/clientStore.jks: The certificate warehouse of the client ( Include public key 、 Private key 、 Trusted certificate warehouse ( Server certificate ))
- conf/oneway/serverStore.jks: The certificate warehouse of the server ( Include public key 、 Private key 、 Trusted certificate warehouse ( No certificate ))
- conf/oneway/server.cer: Export file of server side word signature certificate
3.1.2、 Source code example
(1)、 Code directory
Source directory .png
clientStore.jks For the client's secret key store ,serverStore.jks It is the secret key library of the server ,server.cer Is the public key of the server ;
One way authentication example source code :https://github.com/zhaozhou11/netty-demo.git
(2)、 Server side SSLContext Generate
public static SSLContext getServerContext(String pkPath){
if(SERVER_CONTEXT!=null) return SERVER_CONTEXT;
InputStream in =null;
try{
// Key manager
KeyManagerFactory kmf = null;
if(pkPath!=null){
// Keystore KeyStore
KeyStore ks = KeyStore.getInstance("JKS");
// Load server certificate
in = new FileInputStream(pkPath);
// Load the server KeyStore ;sNetty Is the password set when generating the warehouse , Password used to check the integrity of the keystore
ks.load(in, "nettyDemo".toCharArray());
kmf = KeyManagerFactory.getInstance("SunX509");
// Initialize the key manager
kmf.init(ks, "nettyDemo".toCharArray());
}
// Get secure socket protocol (TLS agreement ) The object of
SERVER_CONTEXT= SSLContext.getInstance(PROTOCOL);
// Initialize this context
// Parameter one : Authentication key Parameter two : Peer to peer trust authentication Parameter 3 : Pseudo random number generator . Due to one-way Authentication , The server does not need to verify the client , So the second parameter is null
SERVER_CONTEXT.init(kmf.getKeyManagers(), null, null);
}catch(Exception e){
throw new Error("Failed to initialize the server-side SSLContext", e);
}finally{
if(in !=null){
try {
in.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
return SERVER_CONTEXT;
}
(3)、 client SSLContext Generate :
public static SSLContext getClientContext(String caPath){
if(CLIENT_CONTEXT!=null) return CLIENT_CONTEXT;
InputStream tIN = null;
try{
// Truststore
TrustManagerFactory tf = null;
if (caPath != null) {
// Keystore KeyStore
KeyStore tks = KeyStore.getInstance("JKS");
// Load client certificate
tIN = new FileInputStream(caPath);
tks.load(tIN, "nettyDemo".toCharArray());
tf = TrustManagerFactory.getInstance("SunX509");
// Initialize the truststore
tf.init(tks);
}
CLIENT_CONTEXT = SSLContext.getInstance(PROTOCOL);
// Set up the trust certificate
CLIENT_CONTEXT.init(null,tf == null ? null : tf.getTrustManagers(), null);
}catch(Exception e){
throw new Error("Failed to initialize the client-side SSLContext");
}finally{
if(tIN !=null){
try {
tIN.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
return CLIENT_CONTEXT;
}
(4) Server side ChannelHandler initialization :
ChannelPipeline pipeline = sc.pipeline();
String sChatPath = (System.getProperty("user.dir")+ "/src/main/java/com/zhaozhou/netty/demo/ssl/conf/oneway/serverStore.jks");
SSLEngine engine = SslOneWayContextFactory.getServerContext(sChatPath).createSSLEngine();
engine.setUseClientMode(false);// Set to server mode
//engine.setNeedClientAuth(false);// No client authentication required , The default is false, So you don't need to write this line .
pipeline.addLast("ssl", new SslHandler(engine));
// On top of the SSL handler, add the text line codec.
pipeline.addLast("framer", new LineBasedFrameDecoder(1024, false, false));
pipeline.addLast("decoder", new StringDecoder());
pipeline.addLast("encoder", new StringEncoder());
// and then business logic.
pipeline.addLast("handler", new SslOneWayServerHandler());
(5)、 Server side ChannelHandler initialization :
ChannelPipeline pipeline = ch.pipeline();
String cChatPath = System.getProperty("user.dir")+"/src/main/java/com/zhaozhou/netty/demo/ssl/conf/oneway/clientStore.jks";
SSLEngine engine = SslOneWayContextFactory.getClientContext(cChatPath)
.createSSLEngine();// establish SSLEngine
engine.setUseClientMode(true);// Client side model
pipeline.addLast("ssl", new SslHandler(engine));
// On top of the SSL handler, add the text line codec.
pipeline.addLast("framer", new LineBasedFrameDecoder(1024, false, false));
pipeline.addLast("decoder", new StringDecoder());
pipeline.addLast("encoder", new StringEncoder());
// and then business logic.
pipeline.addLast("handler", new SslOneWayClientHandler());
(6)、 Test output
Server output :

Client output :

3.2、 Two-way authentication
3.2.1、 Secret key and signature certificate generation
In front of two-way authentication 4 The step is the same as that of one-way authentication , Two more steps for two-way authentication , You need to export the client public key and import the client public key into the certificate warehouse of the server :
(5)、 export Netty Self signed certificate of the client :
keytool -export -alias client -keystore clientStore.jks -storepass nettyDemo -file client.cer
(6)、 Import the self signed certificate of the client into the certificate warehouse of the server :
keytool -import -trustcacerts -alias client -file client.cer -storepass nettyDemo -keystore serverStore.jks
3.2.2、 Source code example
The source code example of two-way authentication is basically the same as that of one-way authentication , I won't go into more details here .
Two way authentication example source code :https://github.com/zhaozhou11/netty-demo.git
3.2.3、 Test output
Server output :

Client output :

author : Bridgehead cowherd
link :https://www.jianshu.com/p/710f70a99cbc
source : Simple books
The copyright belongs to the author . Commercial reprint please contact the author for authorization , Non-commercial reprint please indicate the source .
版权声明
本文为[dotphoenix]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230609059267.html
边栏推荐
- Pytorch model pruning example tutorial III. multi parameter and global pruning
- SSL/TLS应用示例
- 面试总结之特征工程
- Easyui combobox 判断输入项是否存在于下拉列表中
- Face_ Recognition face detection
- 三子棋小游戏
- C# EF mysql更新datetime字段报错Modifying a column with the ‘Identity‘ pattern is not supported
- Unable to determine the device handle for GPU 0000:02:00.0: GPU is lost.
- Visual Studio 2019安装与使用
- 【指标】Precision、Recall
猜你喜欢

图像分类白盒对抗攻击技术总结

Machine learning III: classification prediction based on logistic regression

Summary of image classification white box anti attack technology
![[recommendation of new books in 2021] practical IOT hacking](/img/9a/13ea1e7df14a53088d4777d21ab1f6.png)
[recommendation of new books in 2021] practical IOT hacking
![[point cloud series] sg-gan: advantageous self attention GCN for point cloud topological parts generation](/img/1d/92aa044130d8bd86b9ea6c57dc8305.png)
[point cloud series] sg-gan: advantageous self attention GCN for point cloud topological parts generation
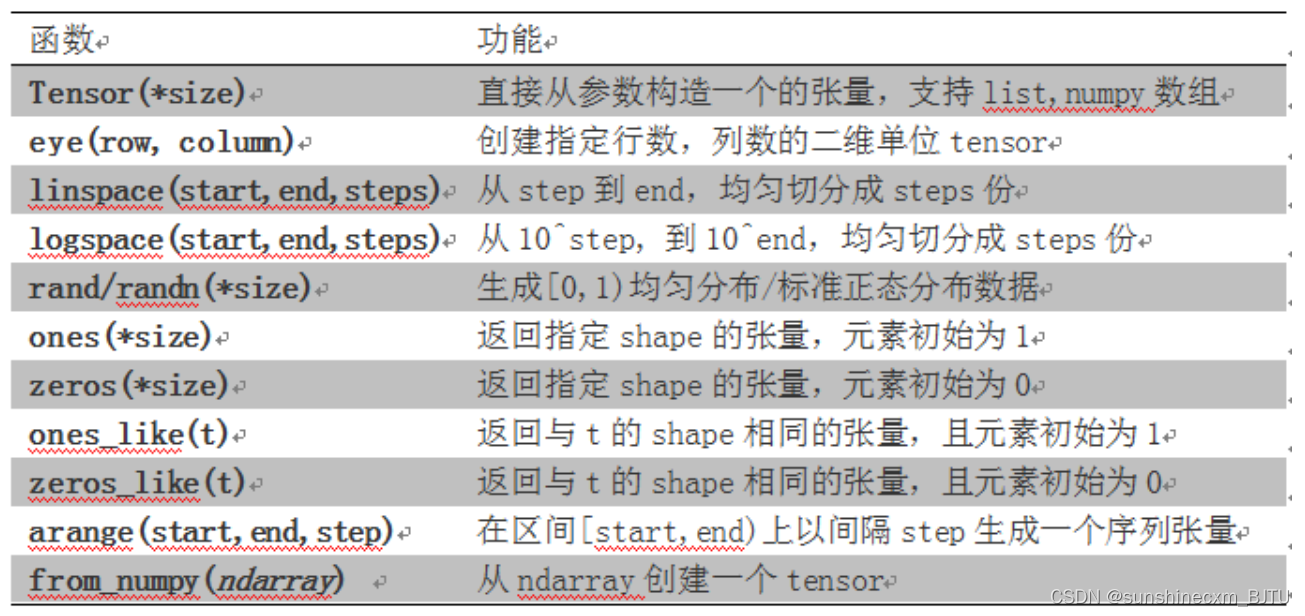
Chapter 2 pytoch foundation 1
Chapter 2 pytoch foundation 2

C language, a number guessing game
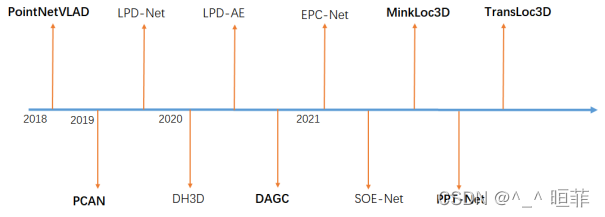
【点云系列】 场景识别类导读

【点云系列】 A Rotation-Invariant Framework for Deep Point Cloud Analysis
随机推荐
红外传感器控制开关
1.2 初试PyTorch神经网络
Chapter 2 pytoch foundation 2
rearrange 和 einsum 真的优雅吗
unhandled system error, NCCL version 2.7.8
Data class of kotlin journey
【点云系列】Neural Opacity Point Cloud(NOPC)
Pytoch model saving and loading (example)
Easyui combobox 判断输入项是否存在于下拉列表中
torch.where能否传递梯度
torch.where能否传递梯度
第5 章 机器学习基础
The Cora dataset was trained and tested using the official torch GCN
PyTorch 21. PyTorch中nn.Embedding模块
Gee configuring local development environment
PyTorch 20. PyTorch技巧(持续更新)
[dynamic programming] longest increasing subsequence
Pytorch trains the basic process of a network in five steps
PyTorch 17. GPU并发
三子棋小游戏