当前位置:网站首页>DOS command of Intranet penetration
DOS command of Intranet penetration
2022-04-23 20:26:00 【Huacheng bag】
Preface
- Blog home page : Huacheng bag
- Welcome to focus on the likes collection ️ Leaving a message.
- This article is included in the full stack column of hacker attack and defense technology : Intranet Security . It will be updated in the future , Coming soon !
- This column is specifically aimed at Xiaobai who wants to get started in the field of network security , Plan to finish in a month !
- One can walk very fast , A group of people can go further ! Join me and study with me !- Only by continuous learning can we not be submerged by the vast sea of people !
- If an error is found , Please leave me a message in the comment area , Thank you very much !

Catalog
- Preface
- 🥦 One 、 Permeate common DOS command
-
- 1.cd Switch the current directory
- 2.dir( List disk catalog files )
- 3.ping( Check the computer connection status )
- 4.net( Query network status and shared resources )
- 5.netstat( Display network connection information )
- 6.tracert( Check the network routing node )
- 7.tasklist( Display host process information )
- 8.sfc( Scan and fix system errors )
- 🥦 Two 、 Practice
- 🥦 3、 ... and 、 Conclusion
🥦 One 、 Permeate common DOS command
1.cd Switch the current directory
cd path :path It's the path , You can switch to the corresponding path . for example , You want to enter Program Files Catalog :
 cd . . : The last two dots indicate that you are going back to the previous Directory
cd . . : The last two dots indicate that you are going back to the previous Directory

cd /: Indicates that no matter in which directory , With this command, you can immediately return to the root directory

2.dir( List disk catalog files )
Use dir The command can list all or specified files and directories on the disk , The display contains Volume label 、 file name 、 file size 、 Document creation date and time 、 Directory name 、 Disk space left etc. . The syntax is as follows :
dir [ Disk character ] [ route ] [ file name ] [/P] [/W] [/A: attribute ]
The function of each parameter :
- /P: Pause the display when more than one screen of information is displayed , Until you press any key to continue to display .
- /W: Displays the file and directory names in a horizontal arrangement , Each row 5 individual , But the file size and creation date are not displayed .
- /A: attribute : Show only files with specified properties , Without this parameter , Show all files except system and implied files , Can be specified as the following :
- /AS: Display information about system files ;
- / AH: Show information about hidden files ;
- / AR: Displays information about read-only files ;
- / AA: Display the information of the archive ;
- / AD: Display directory information .
Specific steps :
View the file information in the current directory :

see c Directory of all files on disk :
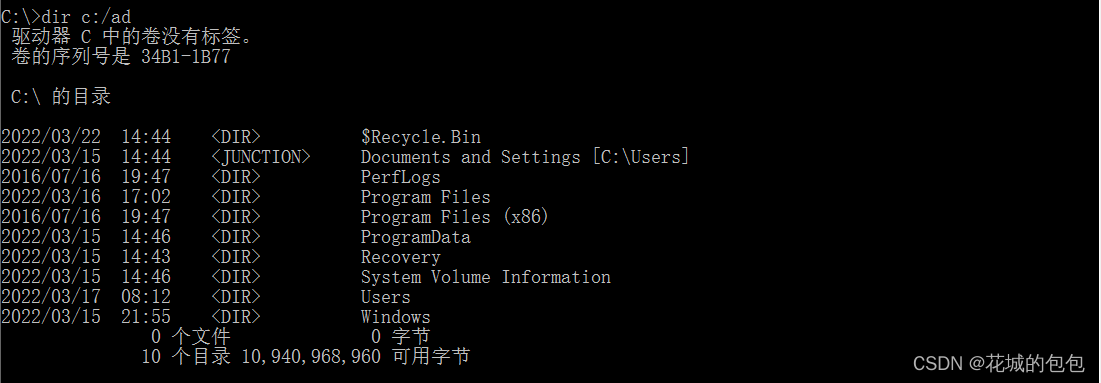
View hidden files :

Be careful :windows Case sensitive !
3.ping( Check the computer connection status )
ping The order is TCP/IP One of the most commonly used commands in , It is mainly used to check whether the network is normal or the speed of network connection .
The specific steps are as follows :
ping Command to determine the operating system type of the computer : By returning to the package TTL Value judgment of .TTL(Time To Live) When we are using ping On command , The result will be returned with TTL value . The meaning of this thing is actually Time To Live, A message that can be in a network ’ Survive ’ The limitation of . When a message is relayed over the network , Time exceeds that limit , The last routing point to receive the message ’ Will throw it away , Instead of forwarding . Later, the time limit was changed to the hop limit , When a message is relayed over the network , Every time I pass by ‘‘ Routing point ’, Just put this preset TTL Value minus 1, Until the last TTL=1 The times were thrown away , No forwarding down .
therefore TTL Field values can help us identify the type of operating system :
LINUX 64
Windows 2000/NT/XP/7/10: 64~128( But there are special circumstances , image TTL=64 Sometimes it's Linux, We should draw a conclusion in combination with other judgment methods , We'll talk about this next time )
WINDOwS series :32
UNIX series :128~255
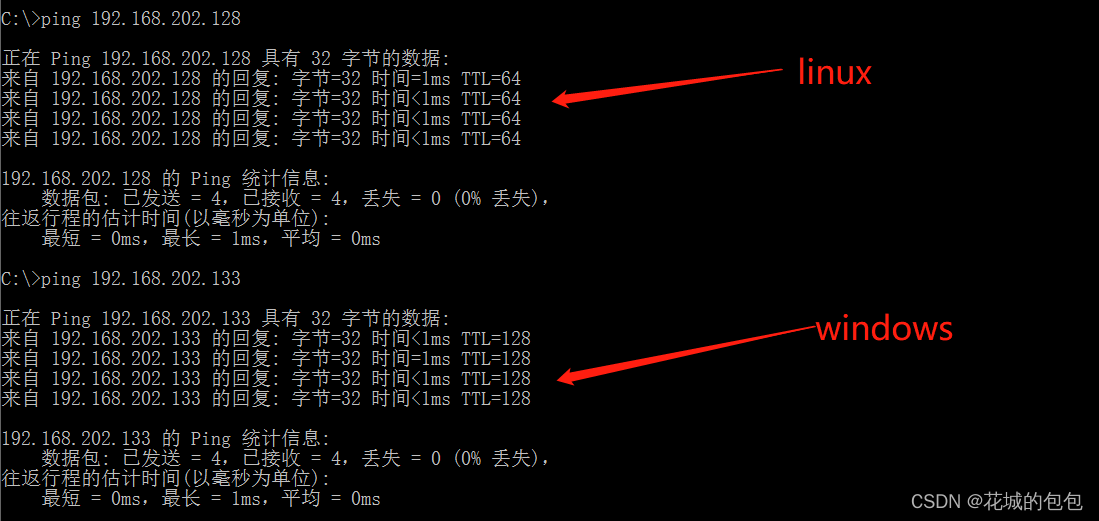
Enter... In the command prompt window ping 192.168.202.133 -t -l 128 command , It can continuously send a large number of data packets to the host :

Judge whether the computer is connected to the outside world :ping www.baidu.com

Analyze a ip The computer name of the address ping -a 192.168.202.133

4.net( Query network status and shared resources )
Query which computers are enabled on this computer windows service :net start

5.netstat( Display network connection information )
netstat The command is mainly used to display the information of network connection , Includes displaying the active TCP Connect 、 Router and network interface information , It's a monitor TCP/IP The Internet is a very useful tool , It can let users know which network connections in the system are normal at present .
netstat /?: Get help

netstat -a: Show all connections and listening ports :

netstat -r : Show routing information :

Check the rest when you need it , I won't show them one by one .
6.tracert( Check the network routing node )
Use tracert The command can view the information of routing nodes in the network , The most common use is in tracert Append a parameter after the command , Indicates to detect and view the routing nodes experienced by the current host , Suitable for large-scale network testing . The syntax format of the command is as follows :
tracert [-d][-h MaximumHops] [-j Hostlist] [-w Timeout] [TargetName]
among , The meaning of each parameter is as follows :
(1)-d: Prevent resolving the name of the target host , Can speed up the display tracert The result of the order .
(2) -h MaximumHops: Specify the maximum number of hops to search to the target address , The default is 30 Jump points .
(3) -j Hostlist: Release the source route according to the address in the host list .
(4) -W Timeout: Specify the timeout interval , The default unit is milliseconds .
(5) TargetName: Specify the target computer .
see www.baidu.com Routing and network connection of the Bureau :

7.tasklist( Display host process information )
Taklist The command is used to display all processes running on a local or remote computer , With multiple execution parameters .Tasklist The format of the command is as follows :
Tasklist [/s system [ /u username[/p[password]]]][/m [module] | /SVC / V ][/fi filter][/fo format] [/nh]
utilize Tasklist The command can view the processes in the machine and the services provided by each process :

View this machine svchost.exe Services provided :
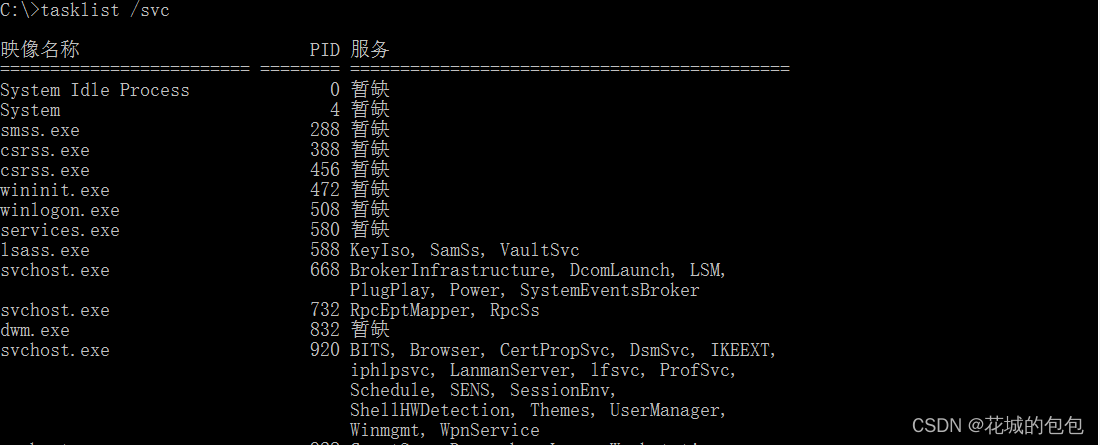
Check which processes in the local system called shell32.dll Module file :

8.sfc( Scan and fix system errors )
sfc The main function of the command is to scan all protected system files and complete the repair work . The syntax format of the command is as follows :
sfc"/scannow""Iscanonce""/scanboot""/revert""/purgecache""/cachesize=x"
among , The meaning of each parameter is as follows .
(1) /scannow: Scan all protected system files now .
(2) /scanonce: Next time it starts , Scan all protected system files .
(3) /scanboot: Every time it starts , Scan all protected system files .
(4) /revert: Return the scan to the default settings .
(5) /purgecache: Clear file cache .
(6) /cachesize- X: Set the file cache size .
Here is the most commonly used sfc/scannow For example , The specific operation steps are as follows :
Right click “ Start ” Button , Choose... From the shortcut menu that pops up “ Command prompt ( Administrators )” Options , As shown in the figure below .

Choice is , enter :

Input :sfc/scannow enter : Start automatic scanning system , It will take a little time . If a damaged system file is found, it will be repaired automatically , And display the repaired information , Here's the picture :

🥦 Two 、 Practice
1. Use the command to execute ( Clear system garbage files )
Quickly clean up the garbage files in the computer by batch processing files , Steps are as follows :
Open Notepad , Enter the code : Rename it to delete.bat
@echo off
echo Cleaning system garbage files , Please wait a moment ......
del /f /s /q %systemdrive%\*.tmp
del /f /s /q %systemdrive%\*._mp
del /f /s /q %systemdrive%\*.log
del /f /s /q %systemdrive%\*.gid
del /f /s /q %systemdrive%\*.chk
del /f /s /q %systemdrive%\*.old
del /f /s /q %systemdrive%\recycled\*.*
del /f /s /q %windir%\*.bak
del /f /s /q %windir%\prefetch\*.*
rd /s /q %windir%\temp & md %windir%\temp
del /f /q %userprofile%\cookies\*.*
del /f /q %userprofile%\recent\*.*
del /f /s /q"Suserprofile Number \LocalSettings\Temporary Internet Files\*.*"
del/f /s /q“userprofile&\LocalSettings.\Temp\* .*”
del / f /s /q "%userprofile%\recent\*.*
echo Garbage cleaning is complete !
echo. & pause
stay dos Run in the window :

2. Use shutdown command ( Realize timing shutdown )
Enter... In the command prompt window :shutdown /s /t 30


Cancel shutdown :shutdown /a

3. Turn off the computer by sliding the mouse
Press Win+R key , Enter in the input box :C:\Windows\System32\SlideToShutdown.exe

Slide the mouse down to turn off the computer , Cancel up .

🥦 3、 ... and 、 Conclusion
For you , Three thousand lights , For you , Flowers bloom all over the city , For you , invincible !
———— Huacheng bag

版权声明
本文为[Huacheng bag]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204232023284380.html
边栏推荐
- PIP installation package reports an error. Could not find a version that satisfies the requirement pymysql (from versions: none)
- CVPR 2022 | querydet: use cascaded sparse query to accelerate small target detection under high resolution
- R language uses econocrats package to create microeconomic or macroeconomic map, visualize indifference function indifference curve, customize calculation intersection, and customize the parameters of
- selenium.common.exceptions.WebDriverException: Message: ‘chromedriver‘ executable needs to be in PAT
- 2022 - Data Warehouse - [time dimension table] - year, week and holiday
- 考研英语唐叔的语法课笔记
- Identification of bolt points in aerial photography based on perception
- SQL Server Connectors By Thread Pool | DTSQLServerTP plugin instructions
- selenium. common. exceptions. WebDriverException: Message: ‘chromedriver‘ executable needs to be in PAT
- SQL Server Connectors By Thread Pool | DTSQLServerTP 插件使用说明
猜你喜欢

Latest investigation and progress of building intelligence based on sati
Numpy mathematical function & logical function
Linux64Bit下安装MySQL5.6-不能修改root密码
Commit and rollback in DCL of 16 MySQL
Plato Farm元宇宙IEO上线四大,链上交易颇高
波场DAO新物种下场,USDD如何破局稳定币市场?
![[PTA] get rid of singles](/img/ab/b5d49f336cbfbede23b3377a9314ad.png)
[PTA] get rid of singles
LeetCode 74、搜索二维矩阵
Fundamentals of network communication (LAN, Wan, IP address, port number, protocol, encapsulation and distribution)

Three. Based on ply format point cloud voxel model JS upload interface writing
随机推荐
Introduction to link database function of cadence OrCAD capture CIS replacement components, graphic tutorial and video demonstration
Es error: request contains unrecognized parameter [ignore_throttled]
ArcGIS JS version military landmark drawing (dovetail arrow, pincer arrow, assembly area) fan and other custom graphics
SQL Server connectors by thread pool 𞓜 instructions for dtsqlservertp plug-in
【PTA】L2-011 玩转二叉树
Shanghai a répondu que « le site officiel de la farine est illégal »: l'exploitation et l'entretien négligents ont été « noirs » et la police a déposé une plainte
Three. Based on ply format point cloud voxel model JS upload interface writing
論文寫作 19: 會議論文與期刊論文的區別
How does onlyoffice solve no route to host
上海回應“面粉官網是非法網站”:疏於運維被“黑”,警方已立案
Es index (document name) fuzzy query method (database name fuzzy query method)
Zdns was invited to attend the annual conference of Tencent cloud basic resources and share the 2020 domain name industry development report
内网渗透之DOS命令
16MySQL之DCL 中 COMMIT和ROllBACK
Investigate why close is required after sqlsession is used in mybatties
Use the rolling division method to find the maximum common divisor of two numbers
PCL点云处理之计算两平面交线(五十一)
Devexpress 14.1 installation record
How to do product innovation—— Exploration of product innovation methodology I
Analysis of the relationship between generalized Bim and CAD under the current background