当前位置:网站首页>Openstack theoretical knowledge
Openstack theoretical knowledge
2022-04-23 15:19:00 【You are my bug forever】
One 、 What is? OpenStack
Openstack It's a cloud platform management project .
OpenStack Is an open source cloud platform , It belongs to... In cloud computing IaaS,
simply : He's here to manage our hardware facilities . Put the server 、 Switch 、 Routers, storage, etc. are controlled by OpenStack Platform management .
We deploy... On the device Linux operating system , Then deploy... On the operating system OpenStack, from OpenStack Decide which virtual machines should be started on which physical computing nodes .
Two 、OpenStack Component introduction of
OpenStack It is composed of many core components , Each component is responsible for its own small piece of functionality , Such as : Responsible for providing computing services Nova, Providing network services Neutron, Each of them has its own management interface , The so-called management interface is based on HTTP Requested web service , It is mainly used to accept command-line tools or components http request .
Let's start with a brief introduction to each component , I'll explain it in detail later
- keystone Identity authentication service
- glance Image services
- nova Computing services
- Neutron Network services
- Horizon Kanban service
- Cinder Disk service
- Swift Object storage service ( Chicken ribs Generally do not use )
- Ceilometer Measurement services
- Heat Choreography Services
2.1 、keystone Identity authentication service
2.1.1 keystone summary
How Authentication works , Take the picture for example
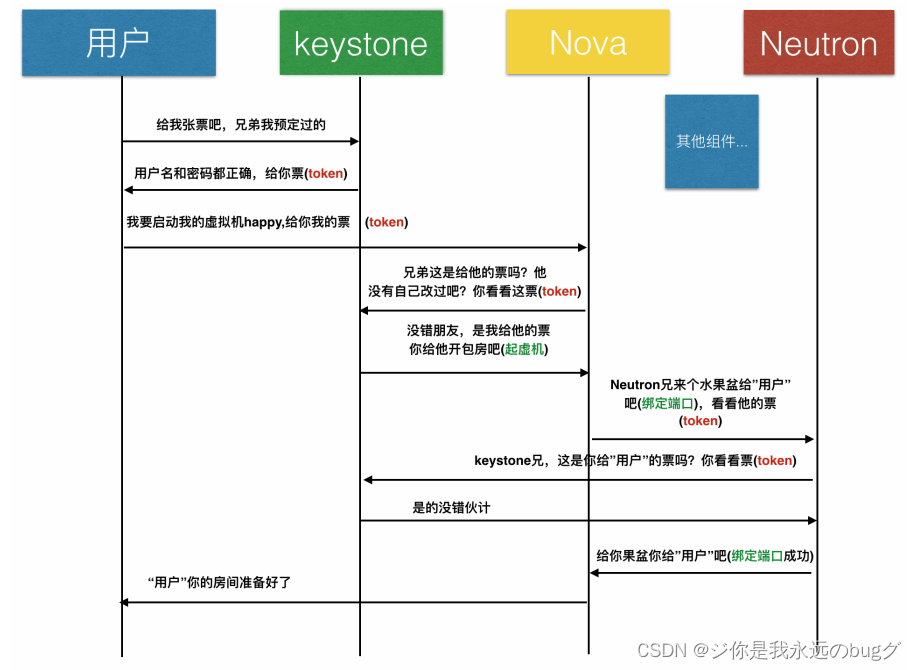
As can be seen from the figure , Before each component operates call keystone Verify your identity !
Three important concepts : user (user)、 role (role)、 Tenant (project)【 It can also be called project 】
- user : Create user , The information includes the user name 、 password 、 Email and other information , however Create users only stay Openstack Resources cannot be used in !
- Tenant :OpenStack All resources in are based on Tenants to isolate , A user must be associated with a tenant before calling resources
- role : Restrict user access to resources . Roles can only be associated with Users under tenants , also A user can have different roles under different tenants .
Tenant 、 The user's understanding : Such as The user is Company employees , A department is a tenant , Employees are assigned to departments , To work properly .
A user can have multiple tenants , The roles under different tenants can also be different
Okay , Look at the picture below , Continue analysis :
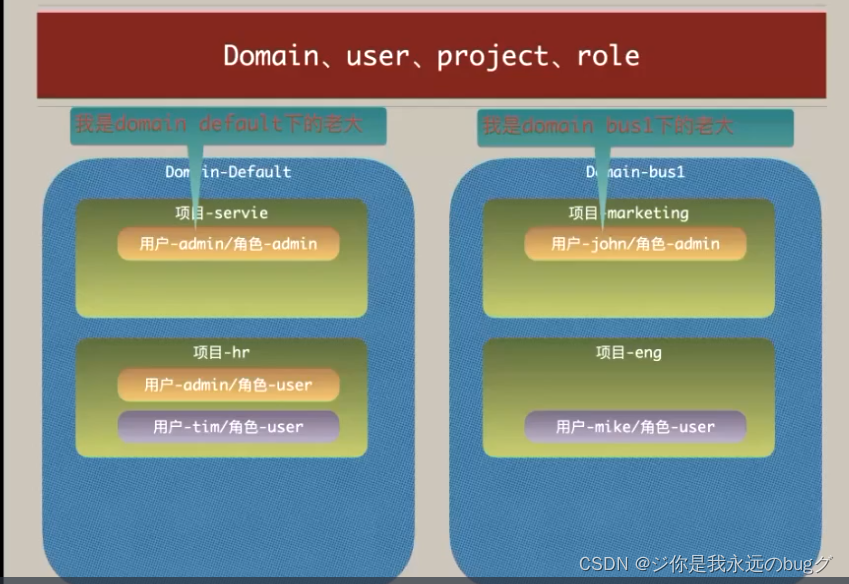
Upper figure ( Left basket ) Explain :
- OpenStack After construction , There will be a blue box , be called domin( Equivalent to the concept of database ), There are two tenants in the picture above .
- 【 user -admin/ role -admin】 Express : A user joins the tenant There must be role information ,admin by The role of super tube
- A user under different tenants , As long as the role is admin, He is Whole OpenStack Super administrator of
The problem is coming. :
The chairman is admin Does he have to take care of everything , Or to the boss of his branch admin role , Will his authority soon be the same as mine ?
Look at the basket on the right
OpenStack You can create multiple domin. Such as Domin-bus1, take A user placed under a tenant admin role , Then he just Super tube under this tenant
Enterprise private cloud is a Domin That's enough , Multiple Domin You need to activate more Domin Service for
also Some unimportant terms , Understanding can
- group Group :
Group users , Then by component 、 role , All users in the group are divided into tenants and roles ,== Take off your pants and fart , Superfluous functions - service endpoint The end of the service
Each component has a API, Yes API There will be IP Address and access method
The service endpoint is the address provided by a service, such as http://192.168.100.20:5000/v3 , So that's one
The end of the service , Service endpoints are used to provide services based on http Requested API An address of the method .
2.1.2 keystone Service for
- Identity authentication service
- Resource service
- Assign Services / Assignment Service
The above three services Namely The above said user Allocate resources according to different roles of tenants
- Bill service / Token Service
Responsible for verifying token Verification service of bills . - A directory service /Catalog Service
Responsible for service Endpoint Management of , Only registered with the correct Endpoint, The service can be called normally - Rule service /Policy Service
Service management rules , The general rules document will be in /etc/ project /Policy.json, It defines what each method needs
What role do you want to use to access .
2.2、glance Image services
Responsible for managing the openstack Online mirror warehouse , Mirror image == operating system , Store it in the object store by configuration (Swift)、ceph perhaps Gluster in
2.3、nova Computing services
2.4、Neutron Network services
2.5、Horizon Kanban service
2.6、Cinder Disk service
2.7、Swift Object storage service ( Chicken ribs Generally do not use )
2.8、Ceilometer Measurement services
Collect the use of various resources of the project
2.9、Heat Choreography Services
版权声明
本文为[You are my bug forever]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231406271638.html
边栏推荐
- Flink DataStream 类型系统 TypeInformation
- Set onedrive or Google drive as a drawing bed in upic for free
- Ffmpeg installation error: NASM / yasm not found or too old Use --disable-x86asm for a clipped build
- For 22 years, you didn't know the file contained vulnerabilities?
- js——实现点击复制功能
- SSH connects to the remote host through the springboard machine
- Hj31 word inversion
- API gateway / API gateway (II) - use of Kong - load balancing
- Leetcode153 - find the minimum value in the rotation sort array - array - binary search
- Differential privacy (background)
猜你喜欢

How to use OCR in 5 minutes
我的树莓派 Raspberry Pi Zero 2W 折腾笔记,记录一些遇到的问题和解决办法
Kubernetes详解(十一)——标签与标签选择器
T2 iCloud日历无法同步

如何设计一个良好的API接口?
Nuxt project: Global get process Env information
Set onedrive or Google drive as a drawing bed in upic for free
For 22 years, you didn't know the file contained vulnerabilities?
Sword finger offer (2) -- for Huawei
8.2 text preprocessing
随机推荐
Llvm - generate if else and pH
Analysis of common storage types and FTP active and passive modes
How to upload large files quickly?
Reptile exercises (1)
Differential privacy (background)
Difference between like and regexp
MySQL installation process (steps for successful installation)
Nacos程序连接MySQL8.0+ NullPointerException
JS - implémenter la fonction de copie par clic
Kubernetes详解(九)——资源配置清单创建Pod实战
The win10 taskbar notification area icon is missing
LeetCode151-颠倒字符串中的单词-字符串-模拟
The wechat applet optimizes the native request through the promise of ES6
Krpano panorama vtour folder and tour
Async void caused the program to crash
Compiling OpenSSL
LeetCode167-两数之和II-双指针-二分-数组-查找
8.5 concise implementation of cyclic neural network
脏读、不可重复读和幻读介绍
setcontext getcontext makecontext swapcontext