当前位置:网站首页>Differential privacy (background)
Differential privacy (background)
2022-04-23 15:07:00 【White horse is not a horse·】
This article mainly aims at B Stand on Teacher Zhang Xiaojian , A summary of the lecture on differential privacy theory and Application , Promoting learning by writing ,B Station video link and PPT It will be put after the text .
1. Differential privacy
1.1 Data release privacy disclosure
Today, , We are in an era of big data . By mastering some of our data , Can optimize the program , Design better products , Improve our quality of life , meanwhile , We also want our data to be used , Can keep privacy from being revealed ( That is, some or some attributes of a particular individual ), This requires a method of privacy protection .
If the data is not treated with privacy protection , Or if the method is too simple , There is a high probability of privacy disclosure , And then damage your personal life :
- Carnegie Mellon university LatanyaSweeney Will be anonymous GIC database ( Include the date of birth of each patient 、 Gender and zip code ) When linked to the voter registration record , You can find the medical records of the governor of Massachusetts .
- 2018 Cambridge analytics “ manipulation ” US election Events , Through illegal acquisition 8700 ten thousand Facebook User data , Build psychoanalytic models , Analyze the personality characteristics of Internet users , And then targeted the implementation of false advertising .
1.2 Privacy protection methods
There are current methods to protect privacy , Mainly add the first and third :
- K- anonymous (K-Anonymous)
- K- Anonymous variant (L-diversity,T-Closeness)
- Differential privacy (differential Privacy)
1.2.1 K- anonymous

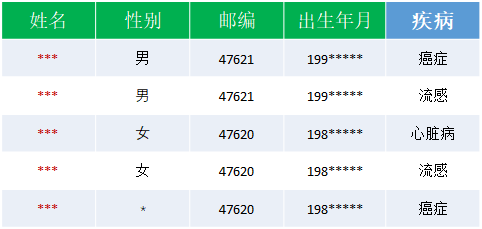
The figure above shows the data to be published , It contains three types of data : Identification data , Quasi identification data and sensitive data
- Identification data : full name , Data that can uniquely identify the user's identity
- Quasi identification data : Gender , Zip code , date of birth , Quasi identification data refers to some attributes between identification data and sensitive attributes , These attributes are combined with other data tables ( Link Attack ), It can also identify the specific information of the patient .
- sensitive data : disease , The core information of publishing data .
K- Anonymity mechanism : Data before release , First erase the identification data , Secondly, align the identification data for processing , Make each data at least K-1 Data cannot be distinguished .
The following is an example of 2- Anonymous data , First delete the name , Then on “ Gender , Zip code and date of birth ” Wait for information to be anonymous . As can be seen from the table , Any piece of data cannot be distinguished from at least one other piece of data .
Link Attack : It refers to the operation of the attacker to obtain and publish data through other channels , To infer private data , Thus causing privacy disclosure , It is equivalent to an expansion of the dimension of personal information .
CDP And LDP The practical application of
版权声明
本文为[White horse is not a horse·]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231407525411.html
边栏推荐
- Brute force of DVWA low -- > High
- 8.3 language model and data set
- SQLSERVER事物与锁的问题
- 分布式事务Seata介绍
- Openfaas practice 4: template operation
- adobe illustrator 菜单中英文对照
- January 1, 1990 is Monday. Define the function date_ to_ Week (year, month, day), which realizes the function of returning the day of the week after inputting the year, month and day, such as date_ to
- tcp_ Diag kernel related implementation 1 call hierarchy
- Explanation and example application of the principle of logistic regression in machine learning
- TLS / SSL protocol details (28) differences between TLS 1.0, TLS 1.1 and TLS 1.2
猜你喜欢

LeetCode151-颠倒字符串中的单词-字符串-模拟
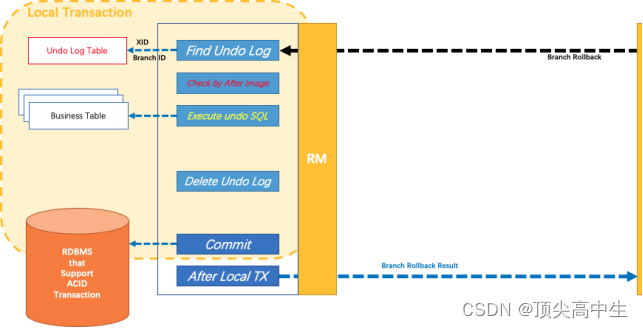
分布式事务Seata介绍

How to upload large files quickly?
Tun model of flannel principle
eolink 如何助力遠程辦公
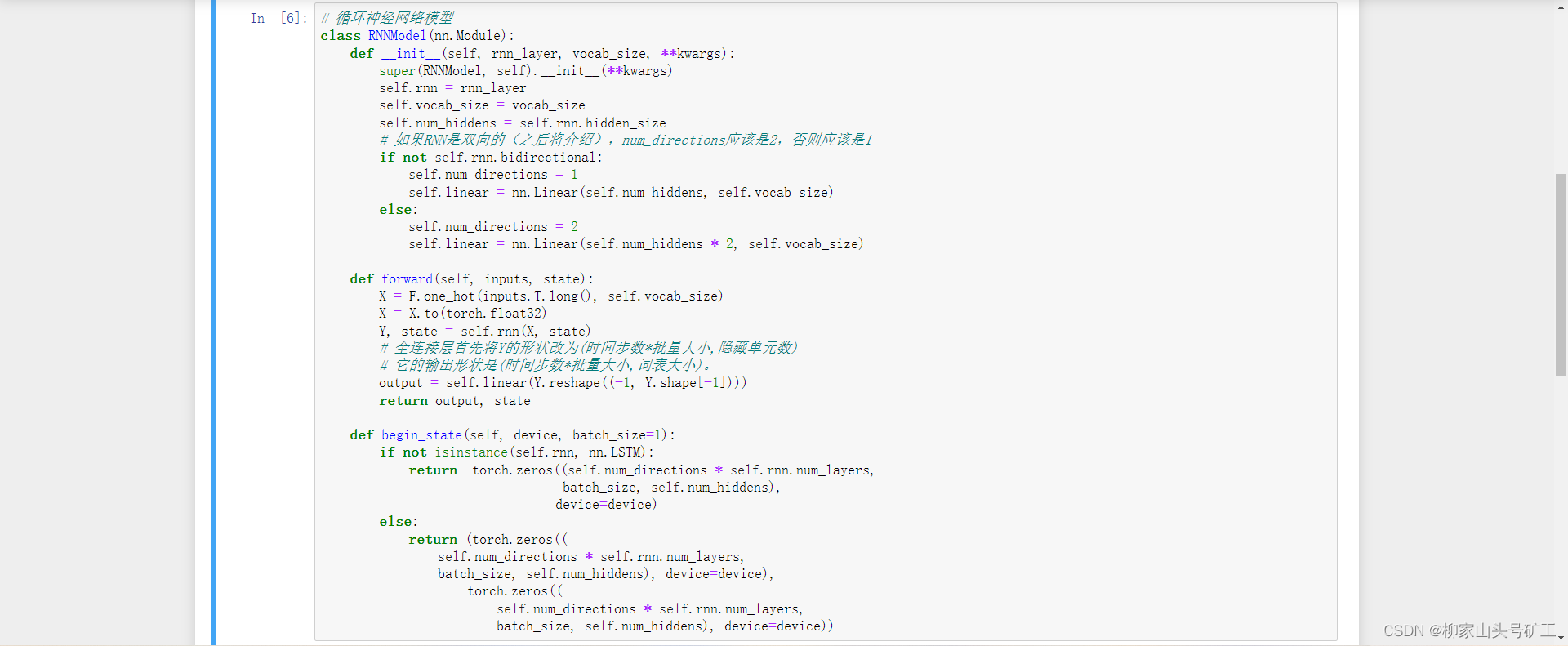
8.5 concise implementation of cyclic neural network

如何设计一个良好的API接口?
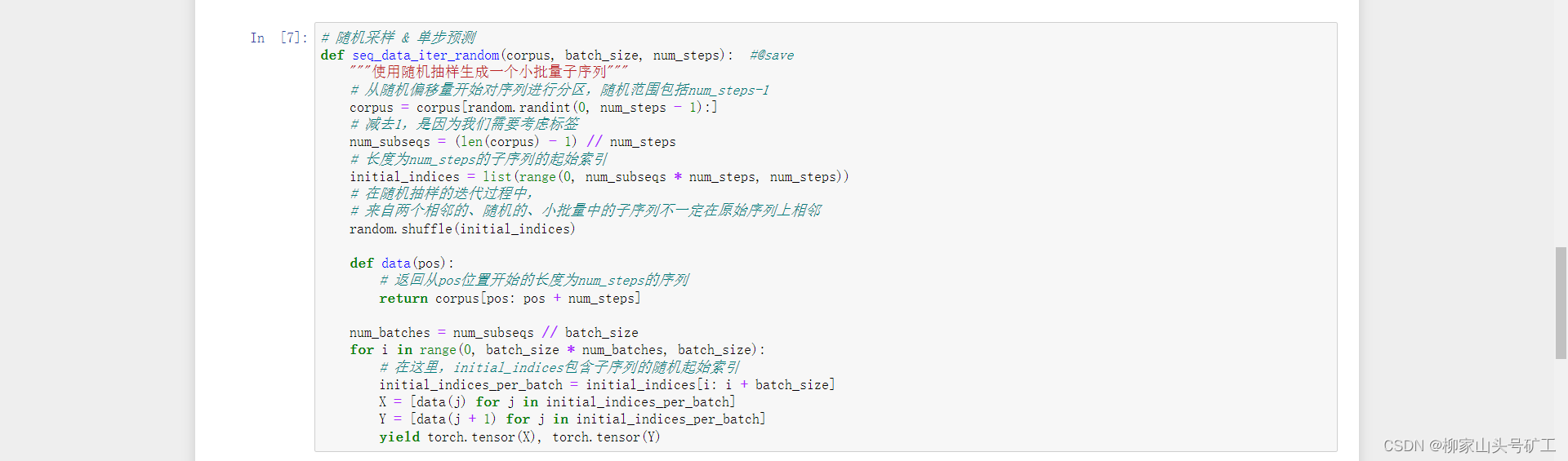
8.3 language model and data set
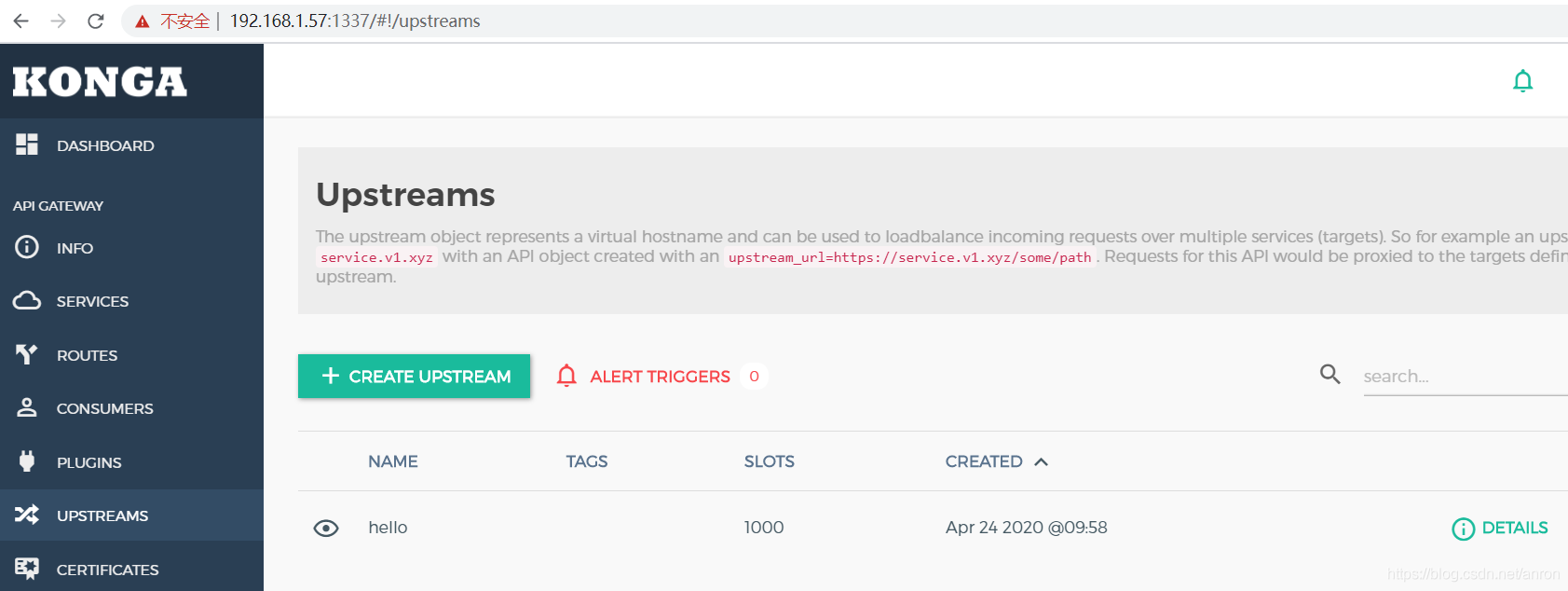
API gateway / API gateway (II) - use of Kong - load balancing
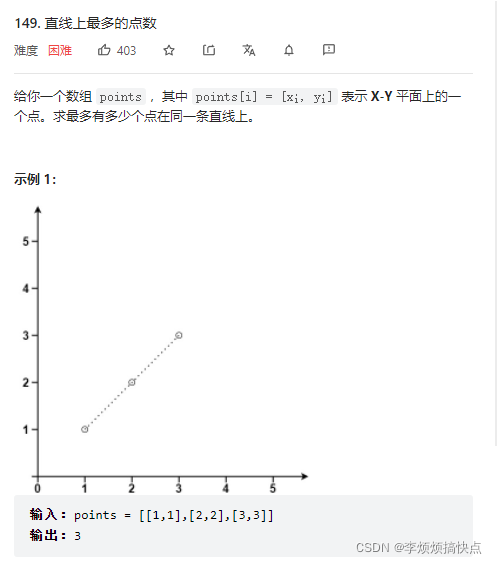
Leetcode149 - maximum number of points on a line - Math - hash table
随机推荐
封面和标题中的关键词怎么写?做自媒体为什么视频没有播放量
Leetcode exercise - 396 Rotation function
January 1, 1990 is Monday. Define the function date_ to_ Week (year, month, day), which realizes the function of returning the day of the week after inputting the year, month and day, such as date_ to
Swift - literal, literal protocol, conversion between basic data types and dictionary / array
Openfaas practice 4: template operation
ffmpeg安装遇错:nasm/yasm not found or too old. Use --disable-x86asm for a crippled build.
UML学习_day2
Have you really learned the operation of sequence table?
Brute force of DVWA low -- > High
C语言超全学习路线(收藏让你少走弯路)
About UDP receiving ICMP port unreachable
Llvm - generate if else and pH
8.5 concise implementation of cyclic neural network
Unity_ Code mode add binding button click event
setcontext getcontext makecontext swapcontext
Mds55-16-asemi rectifier module mds55-16
PSYNC synchronization of redis source code analysis
Subnet division of flannel principle
JS -- realize click Copy function
中富金石财富班29800效果如何?与专业投资者同行让投资更简单